A method and device for converting program code into data constraints
A technology of data constraints and program codes, which is applied in the fields of electrical digital data processing, computer security devices, instruments, etc., can solve the problems of high complexity of intermediate instructions and difficult extraction of data constraints, and achieve the effect of facilitating constraint extraction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
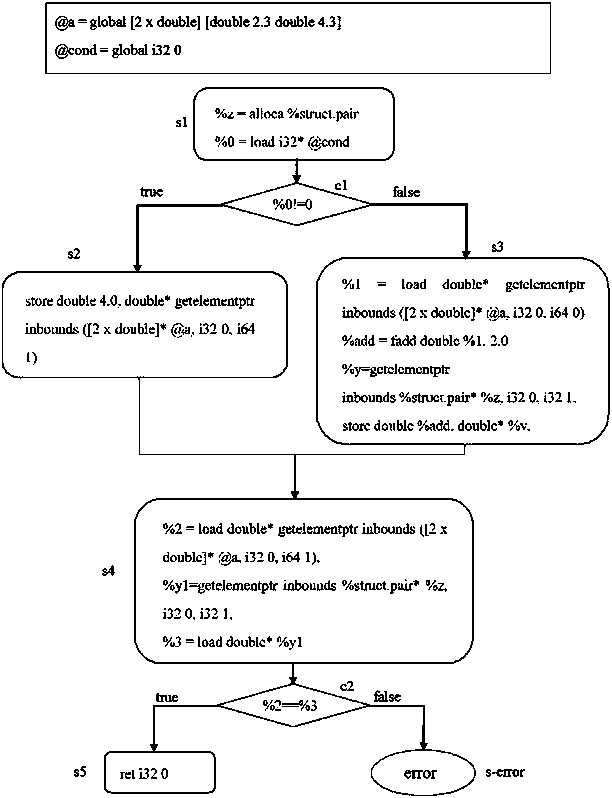
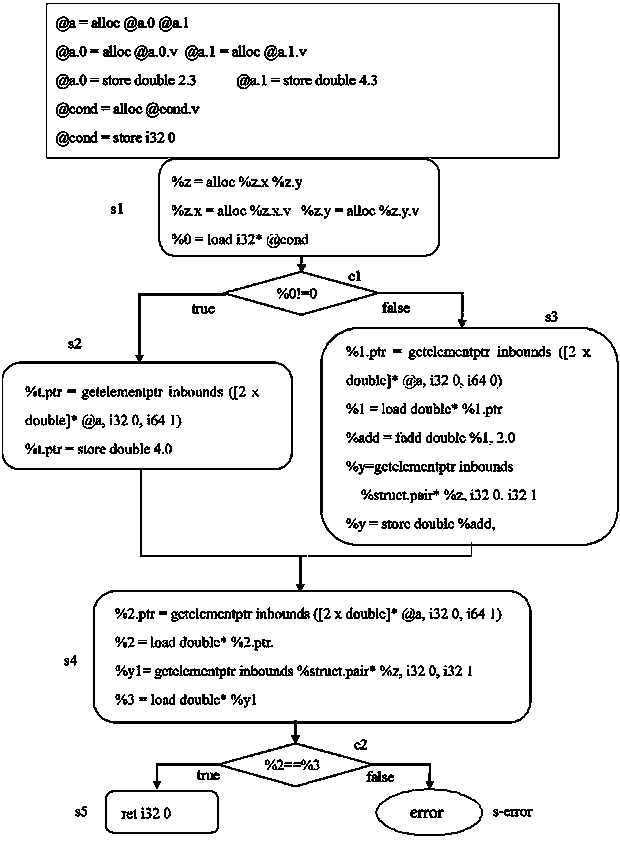
[0032] The present invention will be described in further detail below in conjunction with the accompanying drawings.
[0033] The method for converting program codes into data constraints of the present invention includes two steps: a step of converting source codes into intermediate instruction sets and a step of processing the intermediate instruction sets to extract data constraints. Wherein, the former is the aforementioned step S1, converting the source code input by the user into an intermediate instruction set; the latter is the aforementioned steps S2, S3, S4 and S5.
[0034] The process of step S1 can be implemented by a general front-end compiler. Those skilled in the art understand that under the framework of existing compiler theory, a compiler generally consists of a front-end compiler, an optimization module and a back-end compiler. The front-end compiler is used to convert source codes in different languages into intermediate instruction sets, then the optim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com