A location privacy protection method based on p2p structure
A privacy protection and location information technology, applied in transmission systems, electrical components, etc., can solve the problems of high query overhead and communication overhead, reduce query overhead and communication overhead, improve privacy protection, and reduce query overhead and communication overhead Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
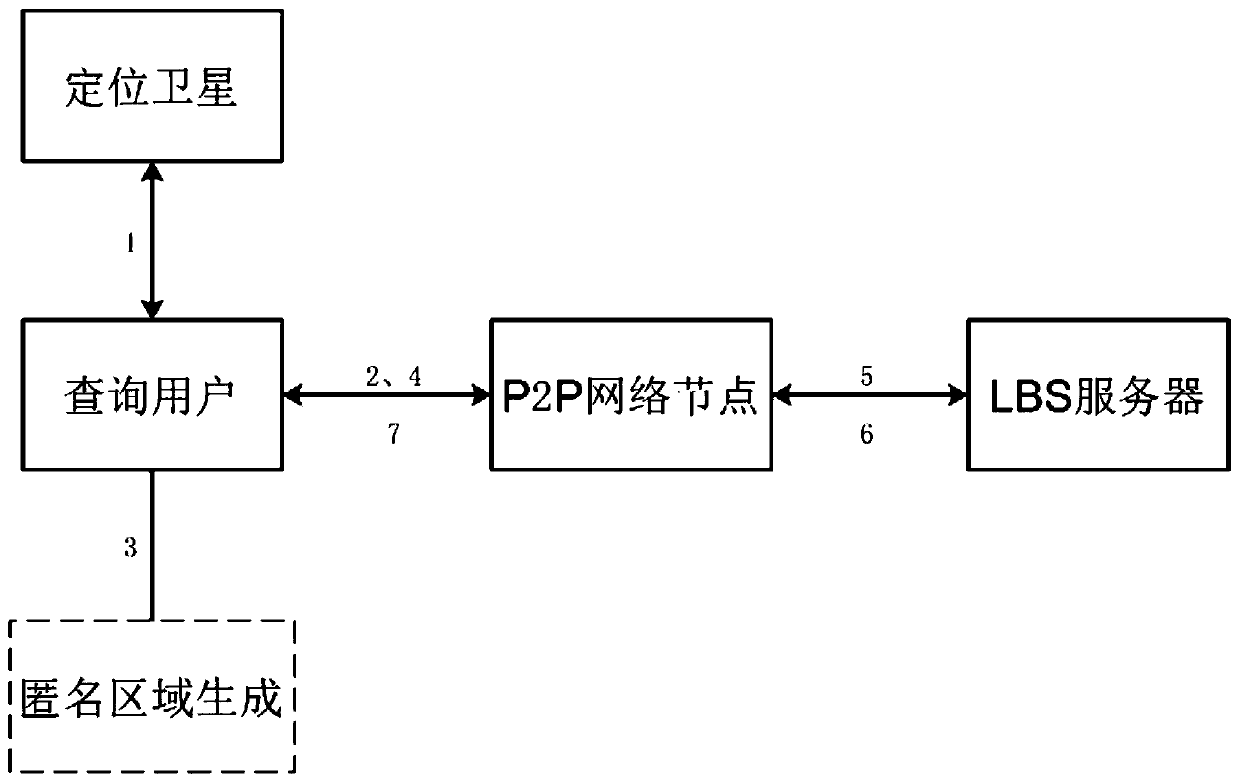
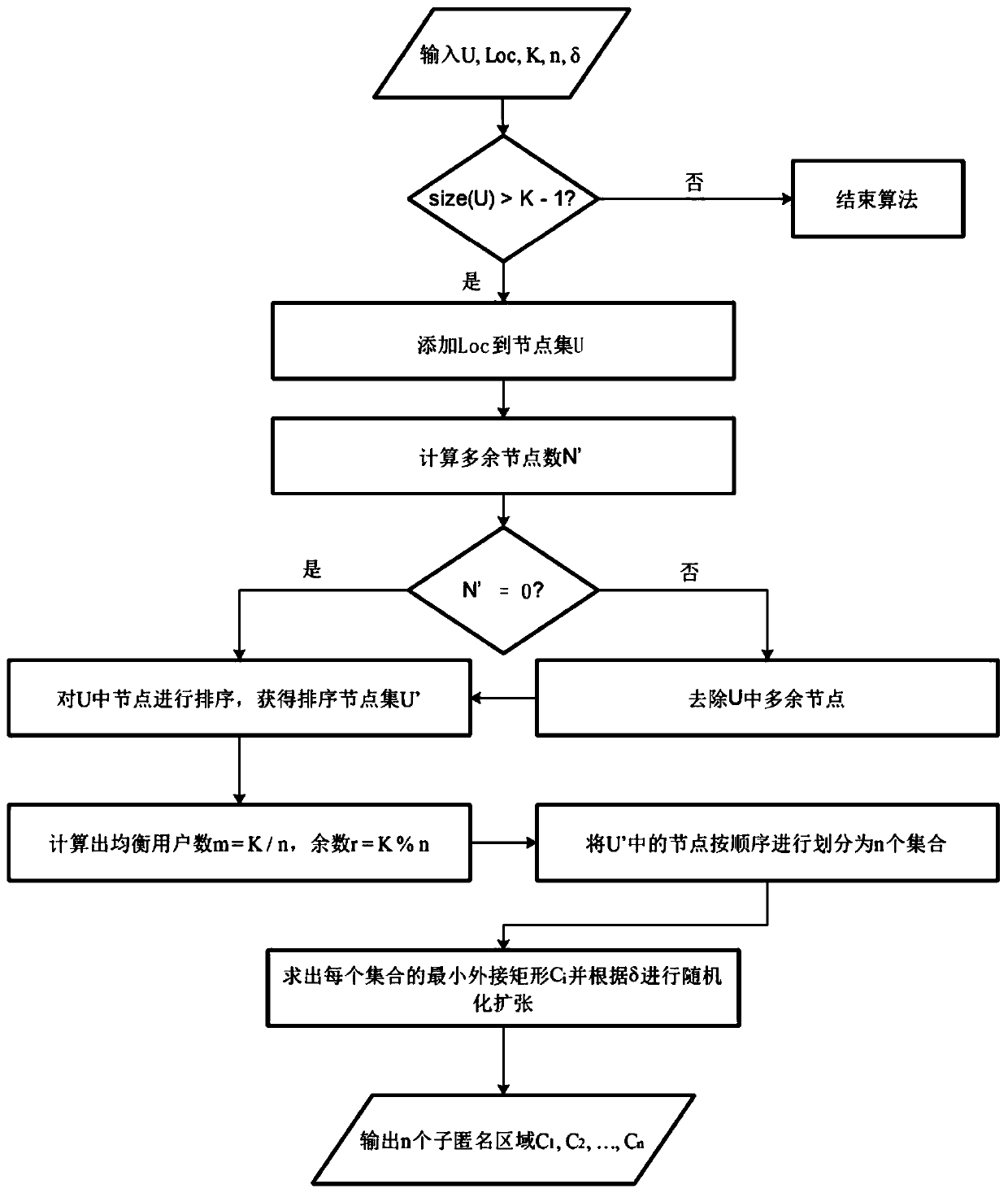
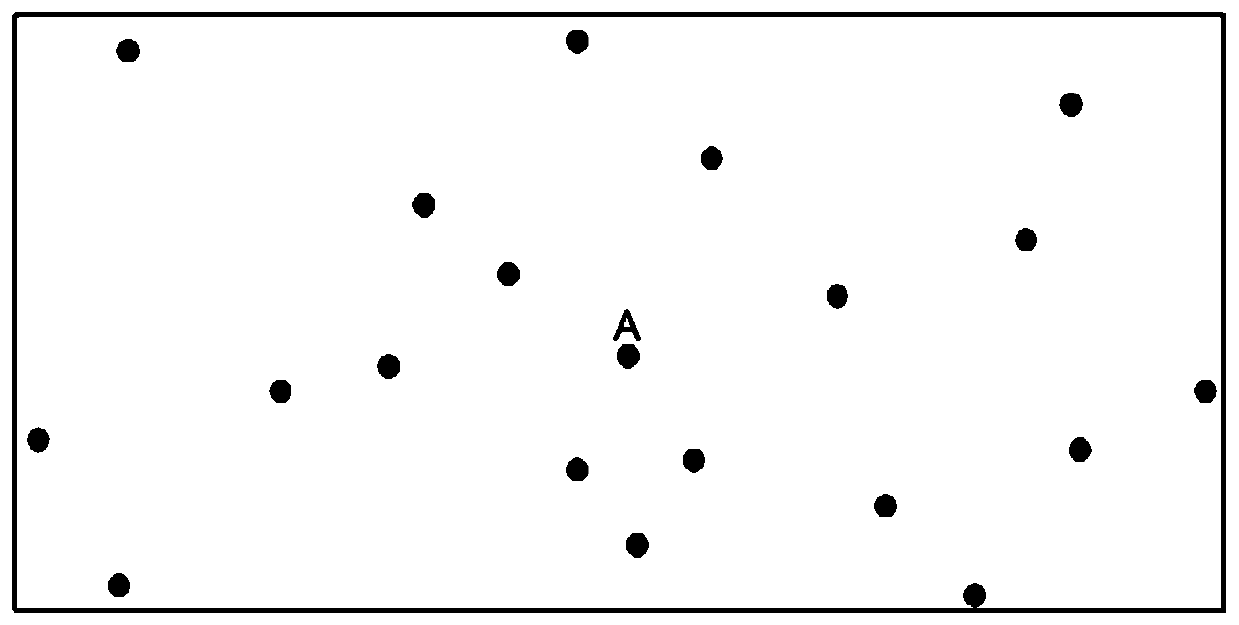
[0049] The present invention is mainly deployed on the user's equipment, and there are three main tasks that the user needs to complete: 1) Locating and initiating to find the information of the assisting node; 2) Generate multiple sub-anonymous areas according to the node information, and send them to each sub-area Random user node; 3) Obtain the result set returned in each sub-area, filter and refine it to obtain the appropriate query result. Among them, the present invention is mainly aimed at the anonymous region generation work in the second step, and the third step also has a corresponding design. The algorithm goal of the present invention is to generate multiple sub-anonymous regions to meet 1) user K’s anonymity requirements; 2) region offset to resist central point attack; 3) regions have similarity and resist location homogeneity attacks; 4) each region The number of users in the network is evenly distributed, resisting the collusion attack of malicious user nodes. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com