Method for obfuscation of code using return oriented programming
A code and return address technology, applied in the direction of program/content distribution protection, platform integrity maintenance, etc., can solve problems such as limitations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] Many specific details are set forth in the following description for a thorough understanding of various embodiments of the present invention. However, those skilled in the art will understand that the embodiments of the present invention may be practiced without some or all of these specific details. In other cases, in order not to unnecessarily obscure relevant aspects of the described embodiments, well-known process operations are not described in detail. In the drawings, the same reference numerals refer to the same or similar functionality or features throughout several views.
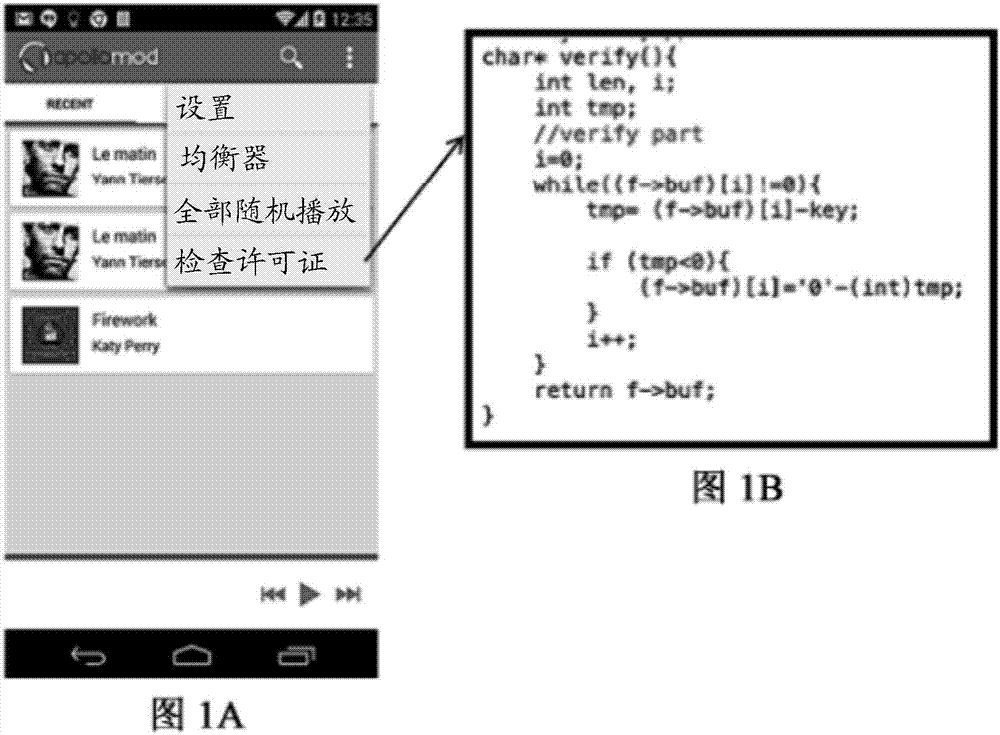
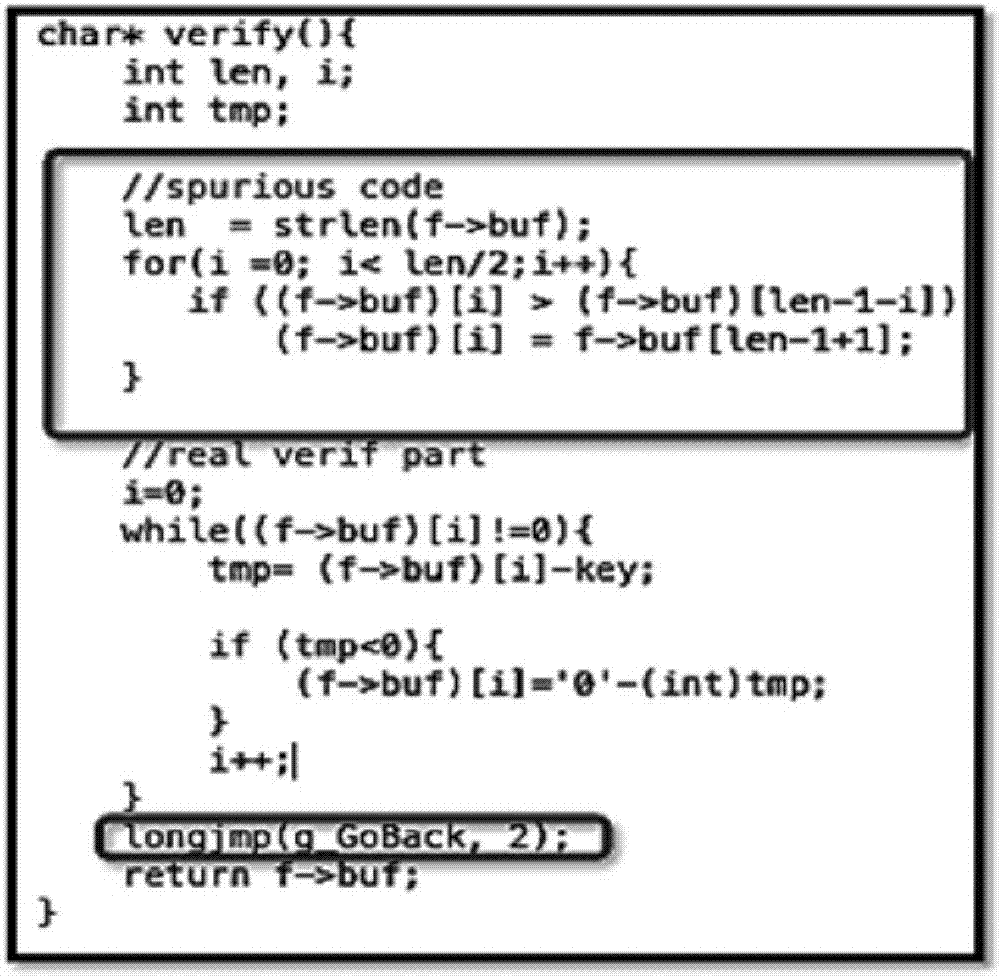
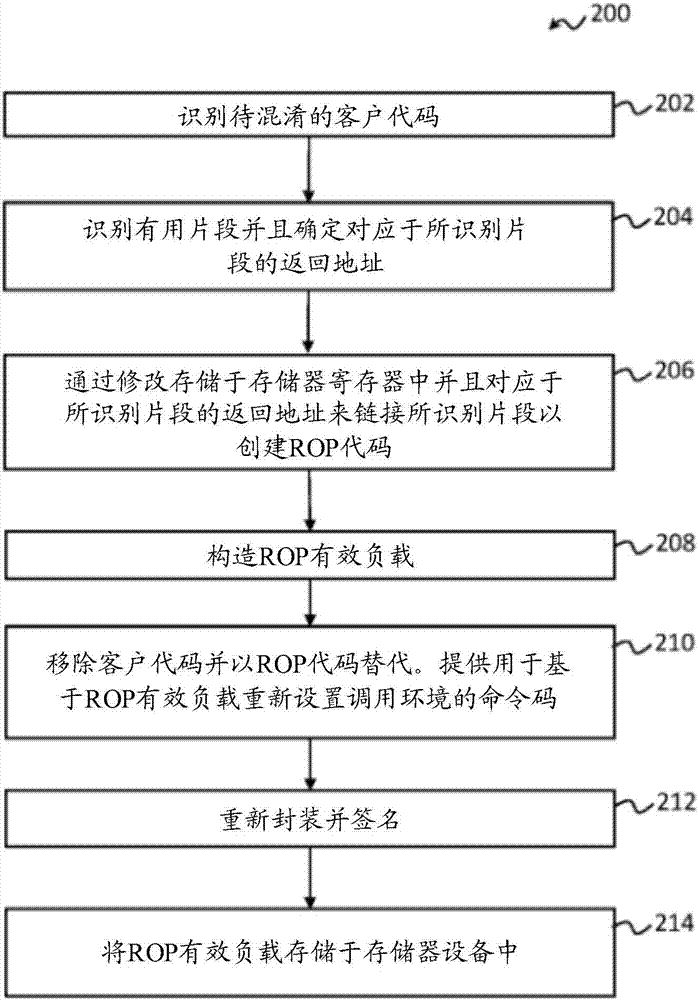
[0034] The embodiment of the present invention discloses a new obfuscation technique using Return Oriented Programming (ROP).
[0035] In recent years, ROP has become one of the most effective runtime attack techniques. Attackers using ROP usually identify fragments from valid code sequences as the first step. A fragment can be referred to as a small fragment of a valid code sequence, and mor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com