A method and device for implementing roaming between wireless controllers AC
A technology of a wireless controller and an implementation method, applied in the field of data communication, can solve the problems of no backup of security entries and poor user experience, and achieve the effect of improving the roaming experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
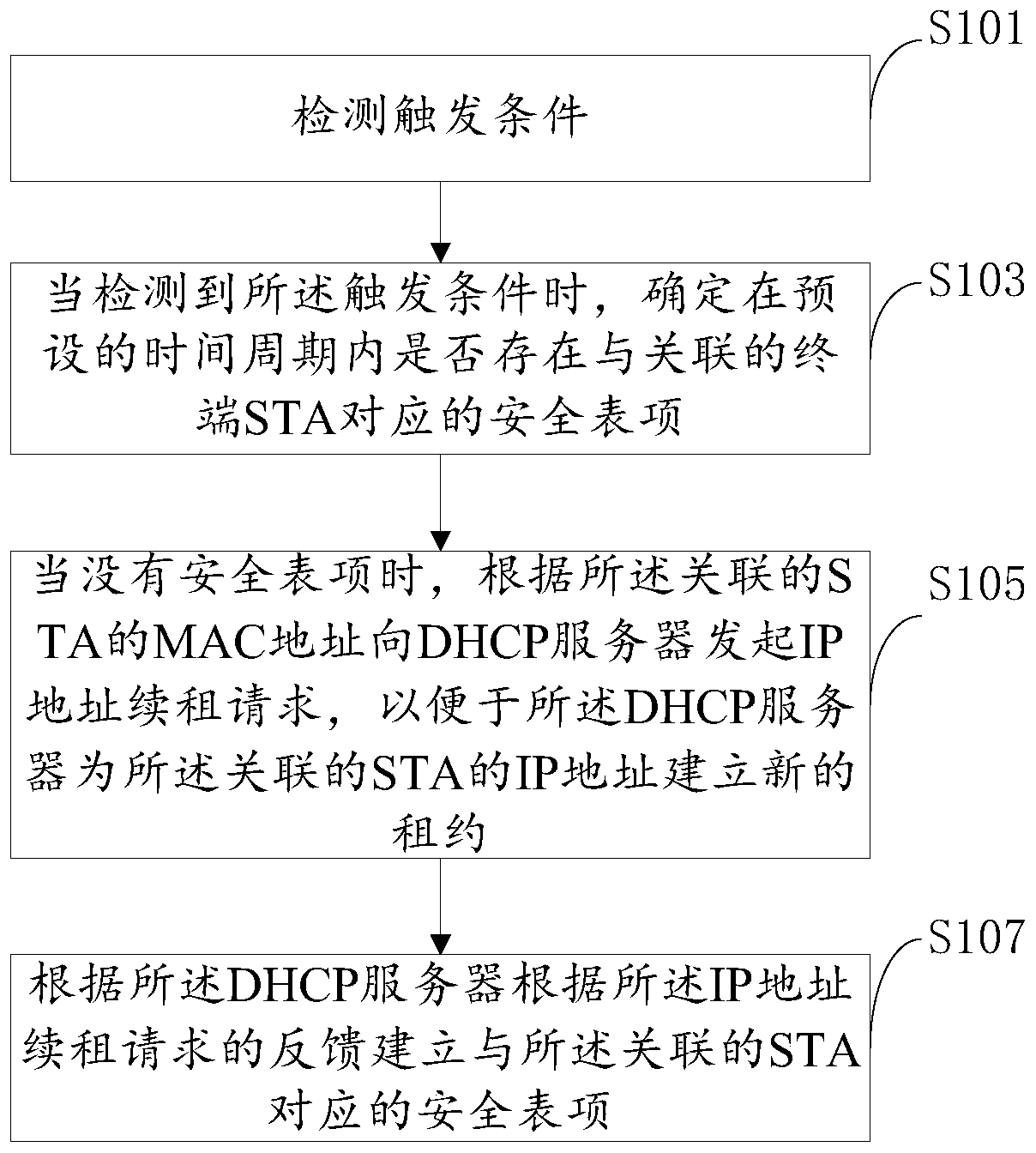
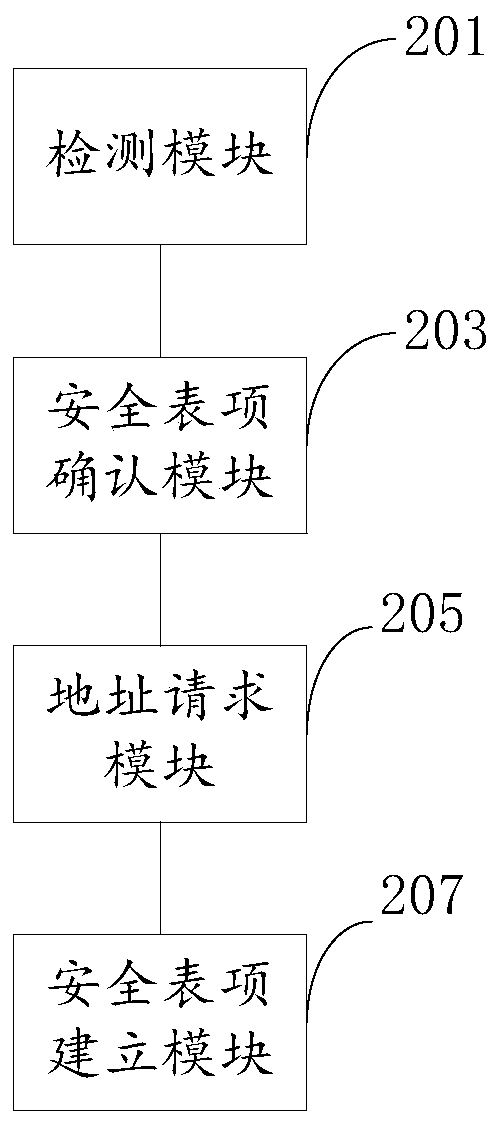
[0057] Optionally, based on the first embodiment of the present invention, in the second embodiment of the present invention, the trigger conditions include:
[0058] The STA is associated with the first access device, wherein the STA roams to the first access device after the second access device associates with the second AC corresponding to the second access device and acquires an IP address. An access device and the STA of the first AC corresponding to the first access device.
[0059] Optionally, based on the first embodiment of the present invention, in the third embodiment of the present invention, the trigger conditions include:
[0060] The security entry corresponding to the STA ages out, wherein the STA establishes an association with the first AC corresponding to the first access device and acquires an IP address on the first access device Roaming to the second access device and the second AC corresponding to the second access device after the security entry, reac...
no. 4 example
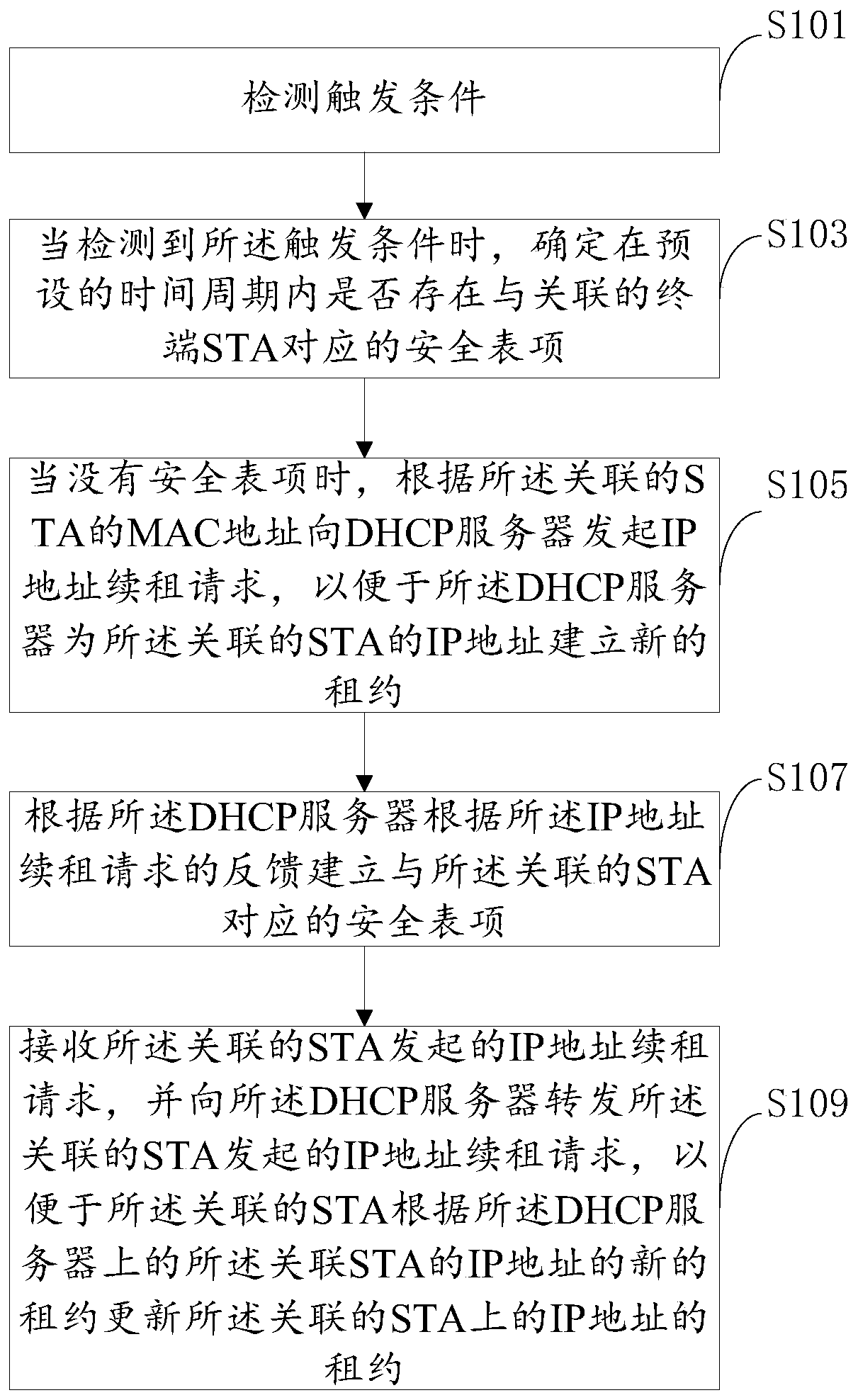
[0064] Optionally, based on the fourth embodiment of the present invention, in the fifth embodiment of the present invention, the step S109 specifically includes: when receiving the lease of the IP address of the associated STA on the associated STA reaches a set threshold An IP address renewal request is initiated, so that the associated STA renews the lease of the IP address of the associated STA according to the new lease of the IP address of the associated STA on the DHCP server.
[0065] Since the IP address allocated by the DHCP server after the STA renews the lease remains unchanged, DHCPSnooping on the access device AP sniffs the DHCP to obtain the IP address and learns security entries. The access device AP initiates DHCP to obtain the IP address instead of the STA. transparent. At this time, the leases of DHCP Server and Snooping will be refreshed, the STA’s lease remains the original one, and the STA’s communication is normal. Afterwards, when the STA reaches the 1 / ...
no. 6 example
[0072] Optionally, based on the sixth embodiment of the present invention, in the seventh embodiment of the present invention, the trigger conditions include:
[0073] The STA is associated with the first access device, wherein the STA roams to the first access device after the second access device associates with the second AC corresponding to the second access device and acquires an IP address. An access device and the STA of the first AC corresponding to the first access device.
[0074] Optionally, based on the sixth embodiment of the present invention, in the eighth embodiment of the present invention, the trigger conditions include:
[0075] The security entry corresponding to the STA ages out, wherein the STA establishes an association with the first AC corresponding to the first access device and acquires an IP address on the first access device Roaming to the second access device and the second AC corresponding to the second access device after the security entry, re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com