Method and device for determining security diagnosability of stochastic discrete event system
A discrete event and system security technology, applied in general control systems, control/regulation systems, test/monitoring control systems, etc., can solve problems such as increasing the complexity of safety fault diagnosis and affecting the applicability and efficiency of safety fault diagnosis methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 2
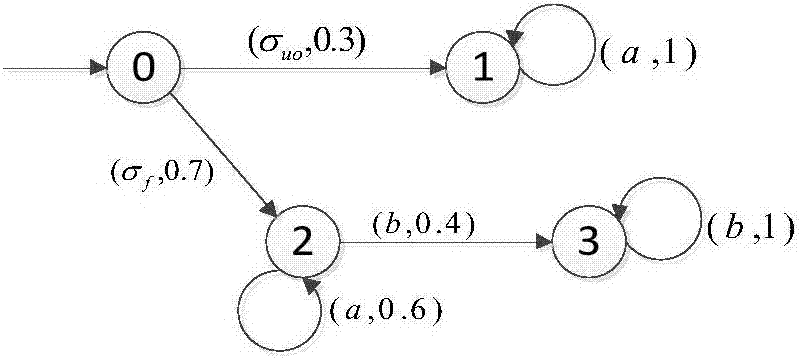
[0176] Example 2: For the convenience of comparison, the random discrete event system G in Example 1 is still used below 1 =(X,Σ,η G ,x 0 )(Such as figure 1 shown) as an example. In Example 1, the system G has been obtained by using the safety diagnostic method 1 Not a safe and diagnosable conclusion. Next, use the safety verifier-based safety diagnosability determination method proposed in the embodiment of the present invention to test the system G 1 authenticating.
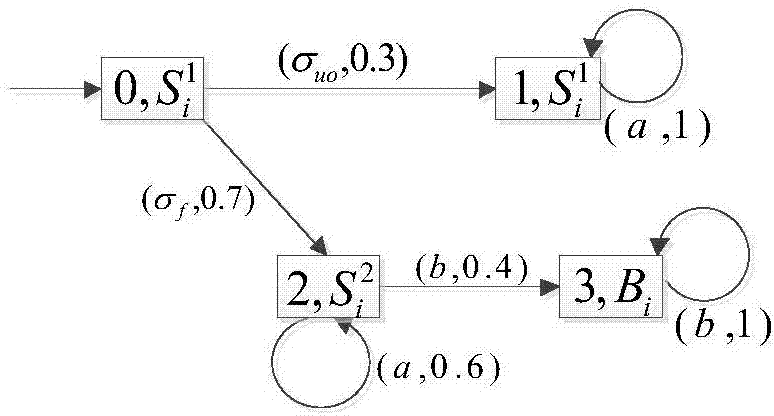
[0177] According to the above step S22, the construction system G 1 The error-free automaton H 1 ,Such as Figure 6 shown. According to step S23 again, construct illegal language recognizer G r1 ,Such as Figure 7 shown.
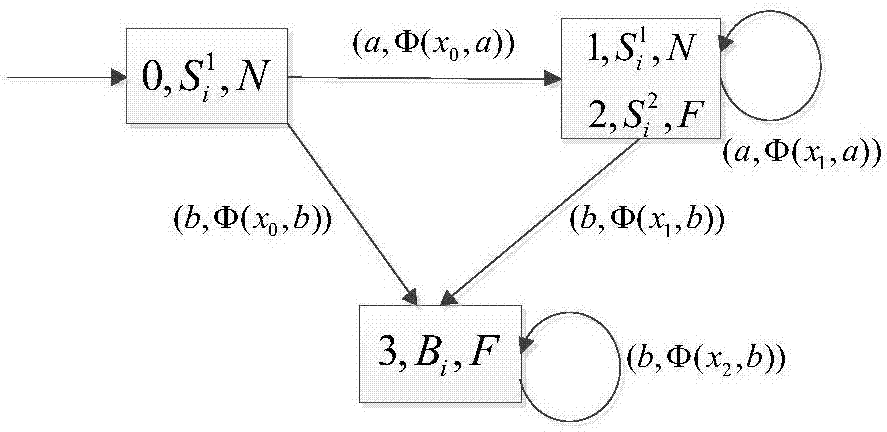
[0178] Then, according to step S24, construct system G 1 The security verifier G v1 ,Such as Figure 8 As shown, it can be seen that in G v1 The following transitions exist in:
[0179] δ v ((0,N,0),b)=(3,B,E),δ v ((3,B,E),b)=(3,B,E)),
[0180] And, δ v ((2,F,1),b)=(3,B,E...
example 3
[0181] Example 3: Consider a random discrete event system G 2 =(X,Σ,η G ,x0 ),Such as Figure 9 Shown, where X={0,1,2}, Σ={a,b,c,σ f}, Σ 0 ={a,b,c}, And the forbidden event cluster is Γ i ={c}.
[0182] Next, use the safety verifier-based safety diagnosability determination method proposed in the present invention to system G 2 Implement security troubleshooting. Construct G according to the above step S22 2 The error-free automaton H 2 ,Such as Figure 10 shown. Then according to above-mentioned step S23 structure illegal language recognizer G r2 ,Such as Figure 11 shown.
[0183] Then, construct system G according to step S24 2 The security verifier G v2 ,Such as Figure 12 shown. due to Figure 12 The security verifier G v2 The transfer in the necessary and sufficient conditions satisfying the above step S24 cannot be found in , so it can be obtained that the random discrete event system G 2 is safe and diagnosable.
[0184] Correspondingly, the embod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com