User authentication method having strengthened integrity and security
A user authentication and user technology, which is applied in the field of user authentication with enhanced integrity and security, and can solve the problems of inconvenient management, inconvenience, and the inability of users to arbitrarily replace OTP devices.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
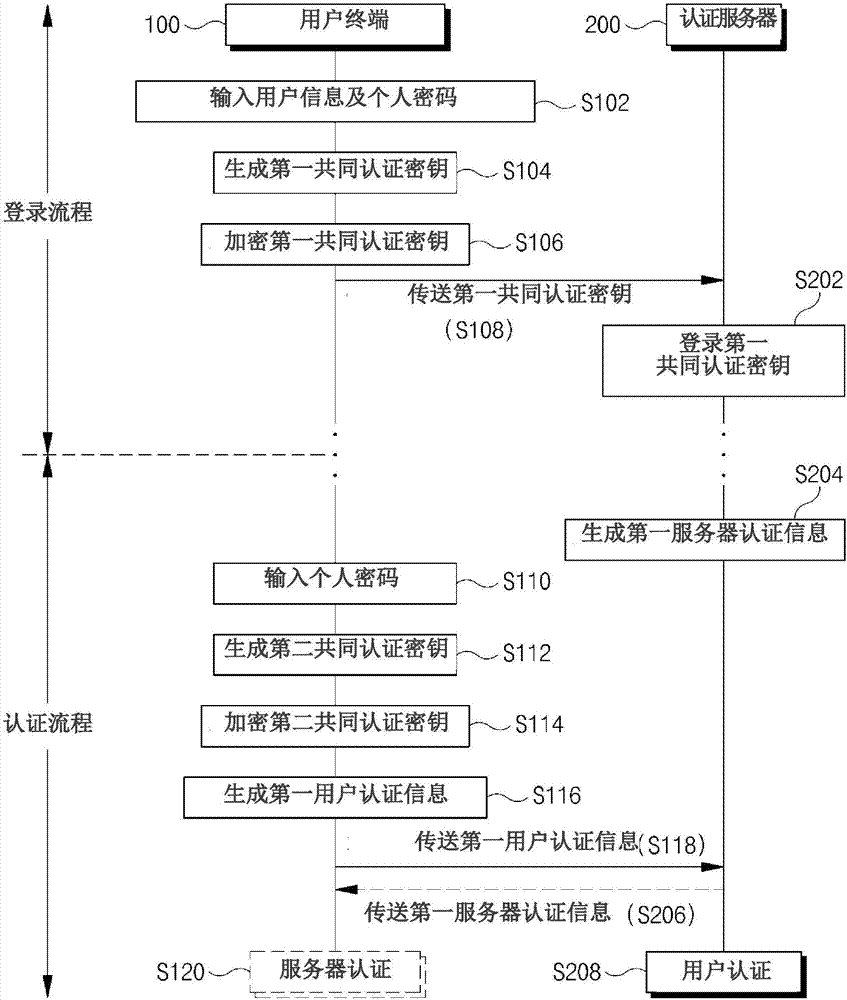
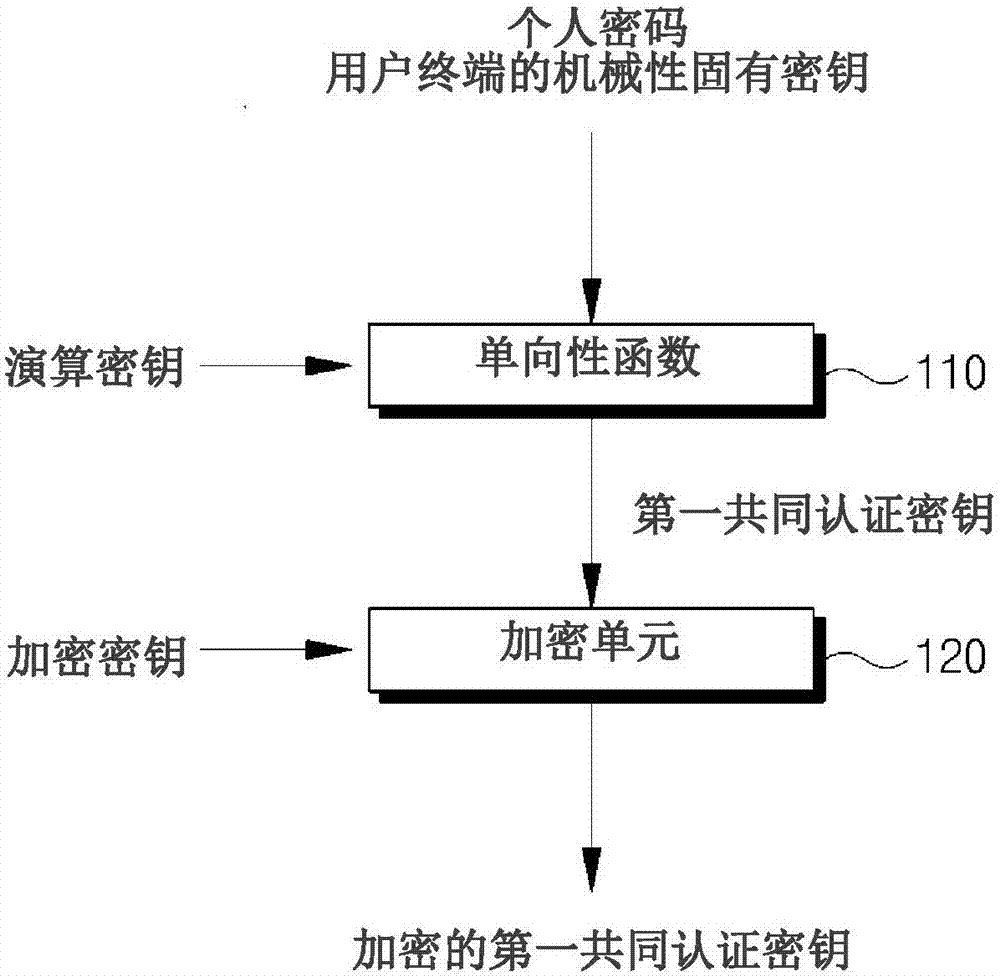
[0098] In the case of the first embodiment of the present invention, in the same manner as the first common authentication key is generated, the personal password input by the user may be added as a constituent element required for generating the second common authentication key.
[0099] That is, the personal password and the mechanical unique key of the user terminal 100 are combined, and the first transformation using the one-way function 110 is performed to generate a second common authentication key S112.
[0100] The one-way function 110 can use the same function as the one-way function for generating the first common authentication key, can be applied in the same way.
[0101] The second common authentication key may be generated in the same way as the first common authentication key, and by using the personal password and the mechanical inherent key of the user terminal 100 as constituent elements, according to a predetermined The calculation key generated based on the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com