Query result set sensitivity-based data leakage detection method
A technology for query results and detection methods, applied in the field of data security, can solve the problems of lack of consideration of the relationship between data objects and the inability to assess the degree of data sensitivity, and achieve the effect of efficient data leakage detection methods, reduced intervention, and reasonable calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
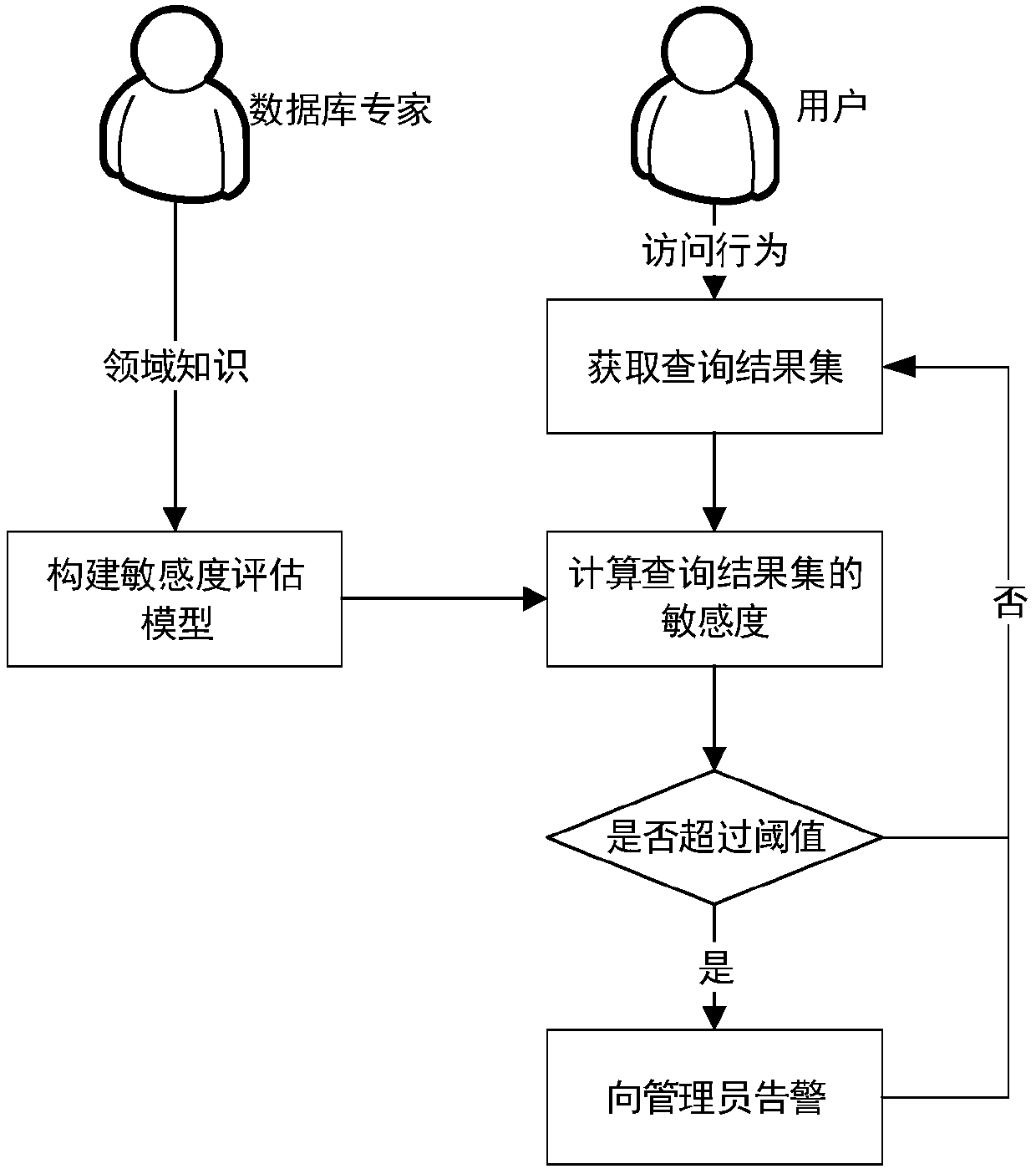
[0038] figure 1 It is a schematic flow chart of the data leakage detection method of the present invention.
[0039] This embodiment provides a data leakage detection method based on the sensitivity of the query result set, including the following steps:
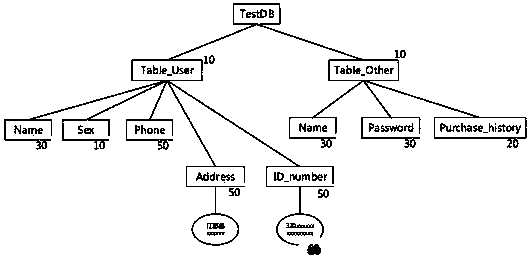
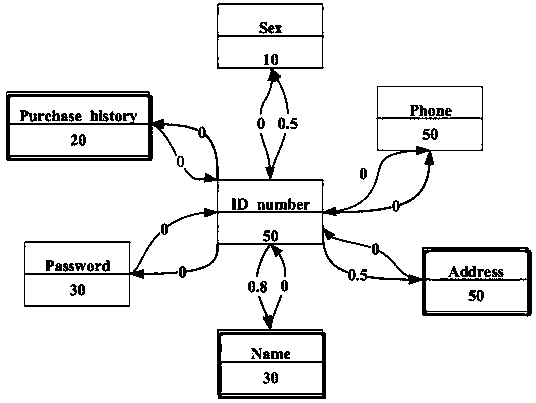
[0040] Step 1. Construct a sensitivity assessment model, which includes not only the sensitivity and inheritance relationship of tables and attributes in the database, but also the relationship between attributes;
[0041] Step 2. Obtain the returned result set of the interactive query request between the user and the database; calculate the sensitivity of the query result set according to the sensitivity evaluation model;
[0042] Step 3: accumulating the sensitivities of multiple query result sets of the user within a certain time window, and sending an alarm to the administrator if the threshold value of the user (user role) is exceeded.
[0043] Step 1. Establish a sensitivity assessment model based on the domain knowl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com