A method of attack defense, network equipment and computer storage medium
A network equipment and equipment technology, applied in the field of network communication, can solve the problems of inability to filter attack packets, maintenance difficulties, network abnormalities, etc., and achieve the effect of improving attack defense capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The invention provides an attack defense method and network equipment, which are used to improve the attack defense capability of the network equipment.
[0056] The technical solution in the embodiment of the present application is to solve the above-mentioned technical problems, and the general idea is as follows:
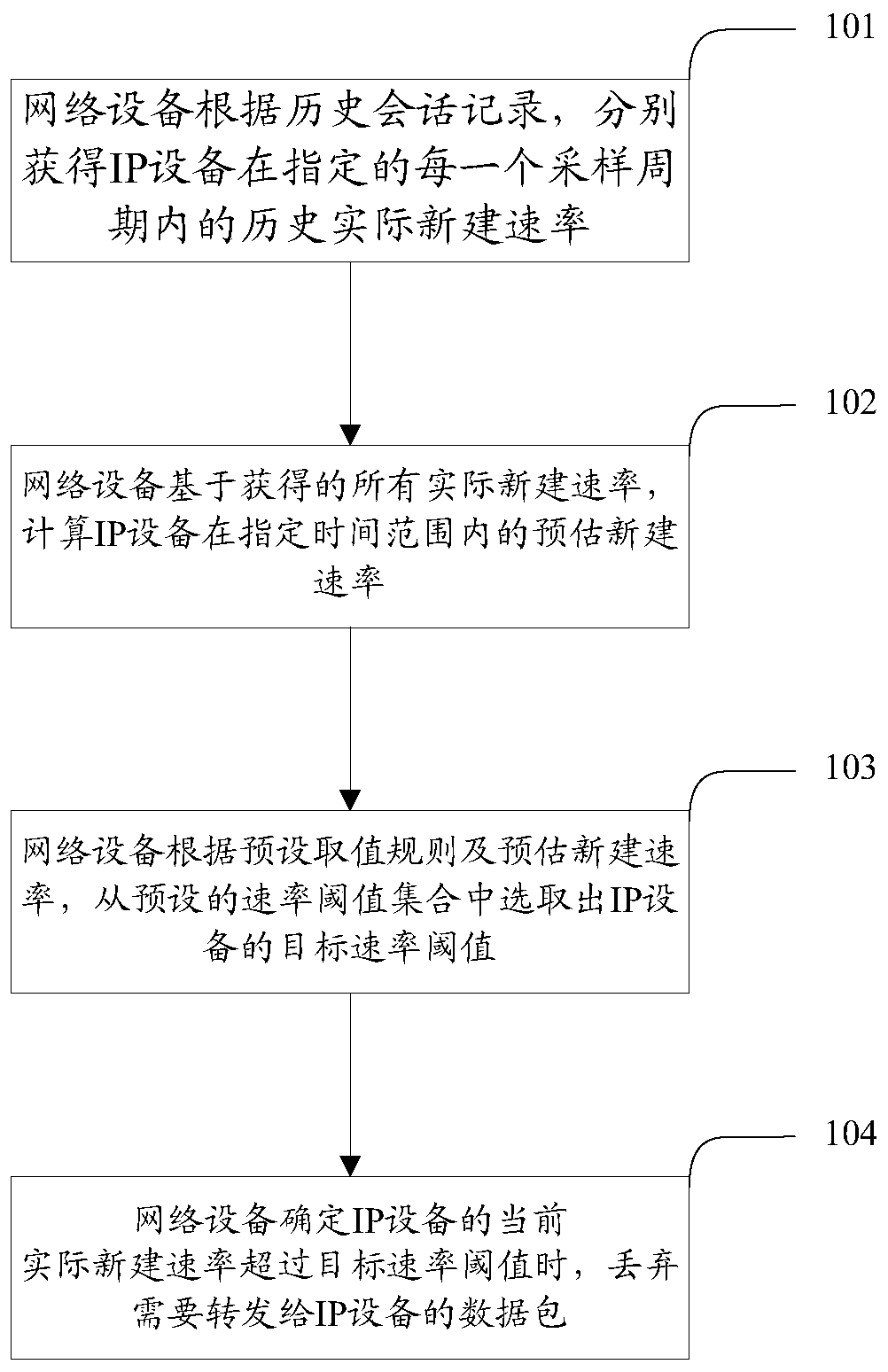
[0057] An attack defense method is provided, which is applied to network devices, including: the network device obtains the historical actual new rate of IP devices in each specified sampling period according to historical session records; wherein, the historical actual new rate in a sampling period The rate is the number of new sessions between the network device and the IP device within a sampling period; the network device calculates the estimated new rate of the IP device within the specified time range based on all the actual new rates obtained; the network device calculates the estimated new rate of the IP device according to the preset value rules an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com