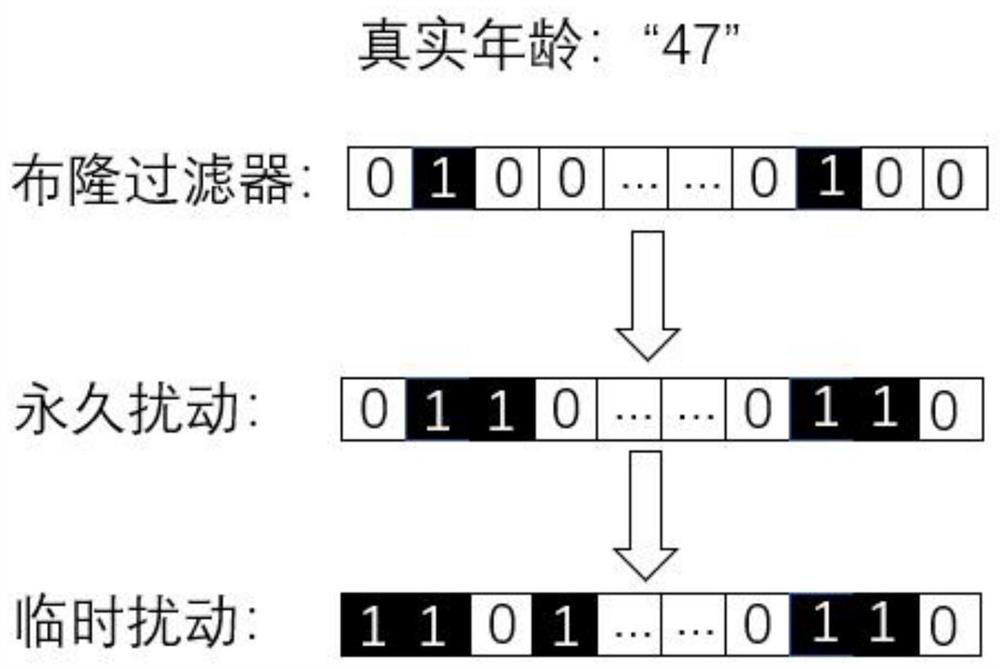
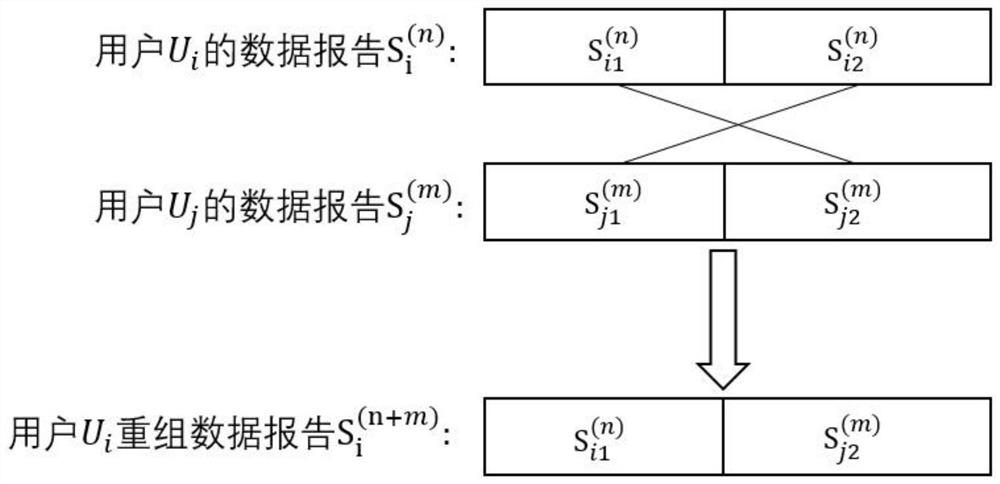
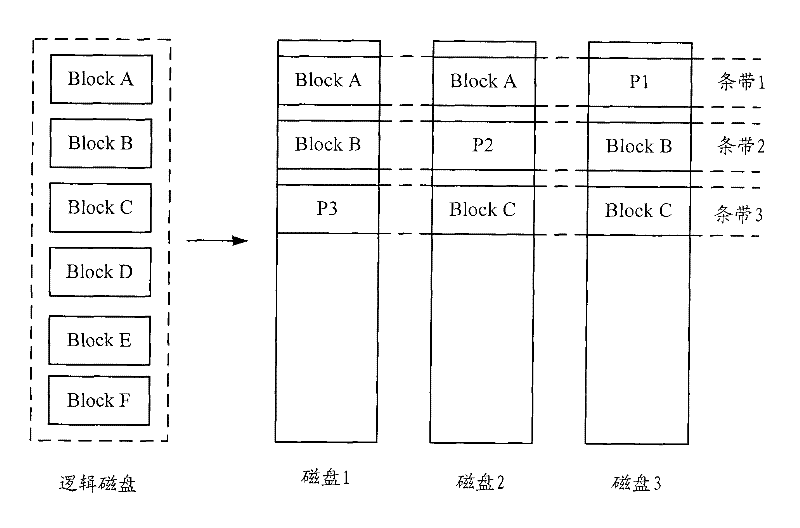
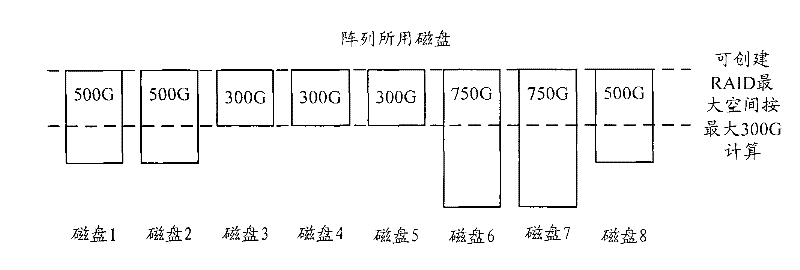
Patents
Literature
30results about How to "Does not affect availability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
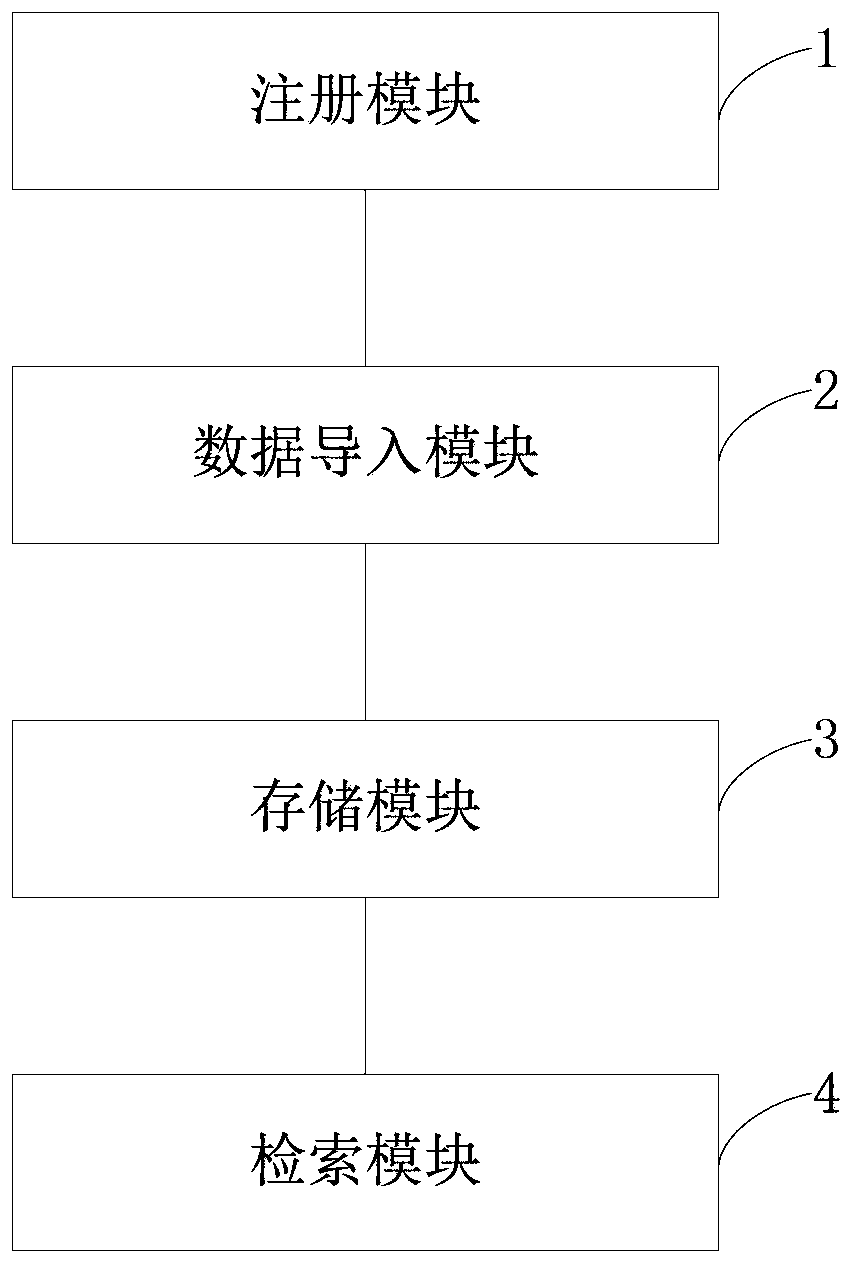
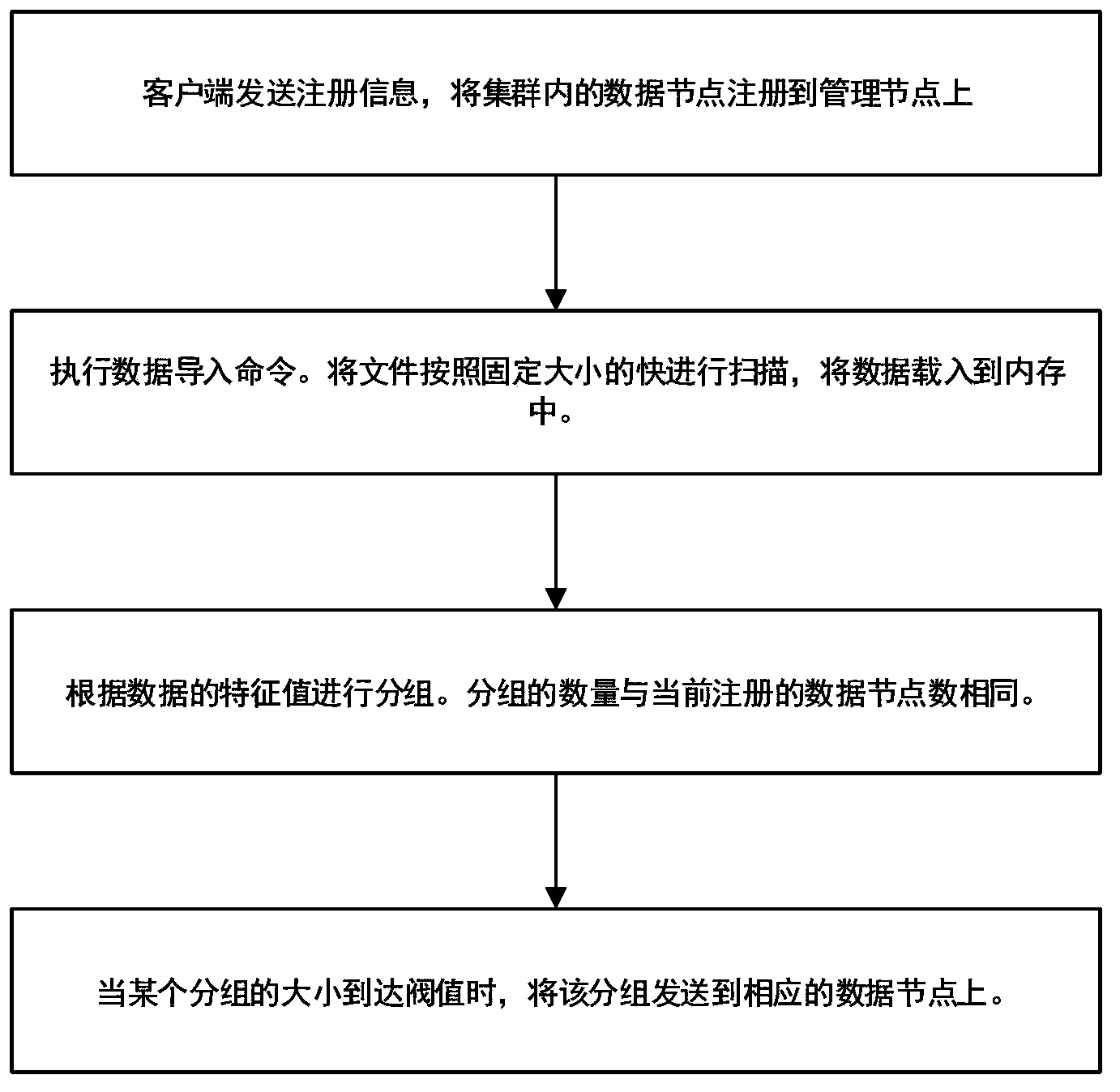
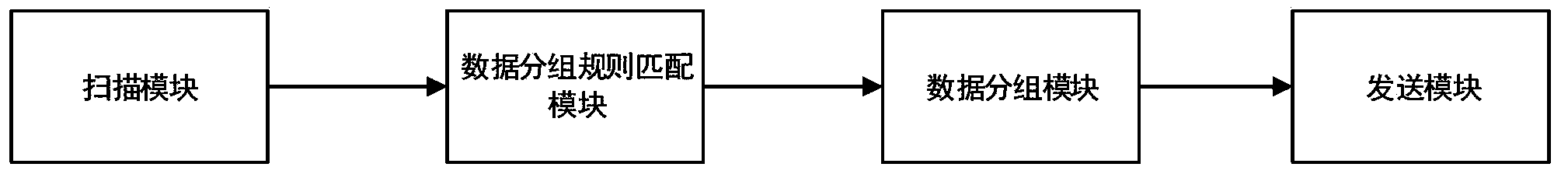
Data distributed storage system and method
InactiveCN104123300AImplement real-time transaction processingEnsure safetySpecial data processing applicationsNode clusteringComputer module
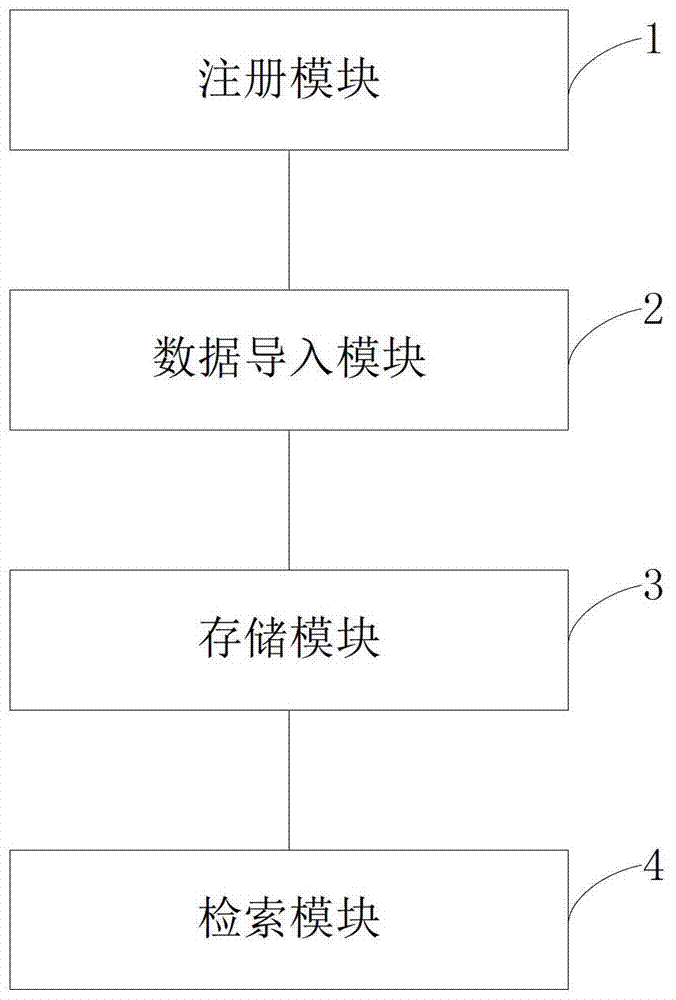
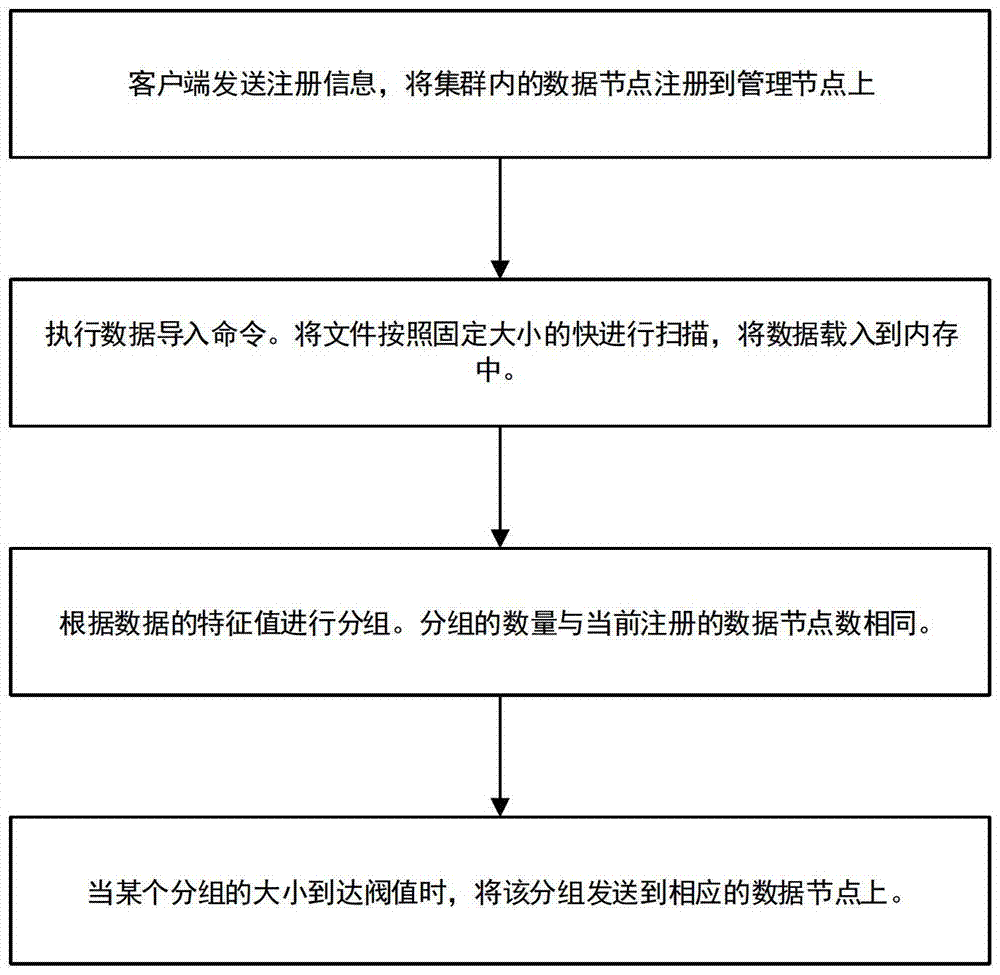
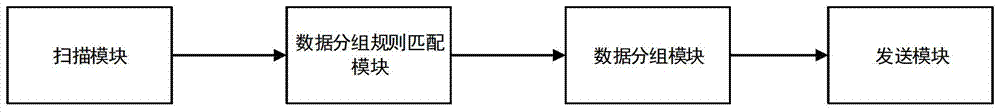
The invention discloses a data distributed storage system and method. The system comprises a node cluster module, a data import module and a storage module. The node cluster module is used for connecting data nodes in a cluster with corresponding management nodes; the data import module is used for scanning input data according to data blocks with sizes set and loading the input data into a memory, data in the memory are grouped according to characteristic values of the data, and the grouped data are sent to the corresponding data nodes; the storage module is used for storing data fragmentations in the memory after the data nodes receive file fragmentations, and the data nodes output logs to a hard disk; whether the data in the memory exceed a set threshold value or not is judged, if the data in the memory exceed the set threshold value, the data are reorganized and compressed and then written into the hard disk, and corresponding log files restored through user memory data are deleted. According to the system and method, the cluster based on memory computing power can be accelerated; real-time loading and processing capacity for large-scale data can be improved, and response time of the system is shortened.
Owner:SHANGHAI PEOPLEYUN INFORMATION TECH CO LTD
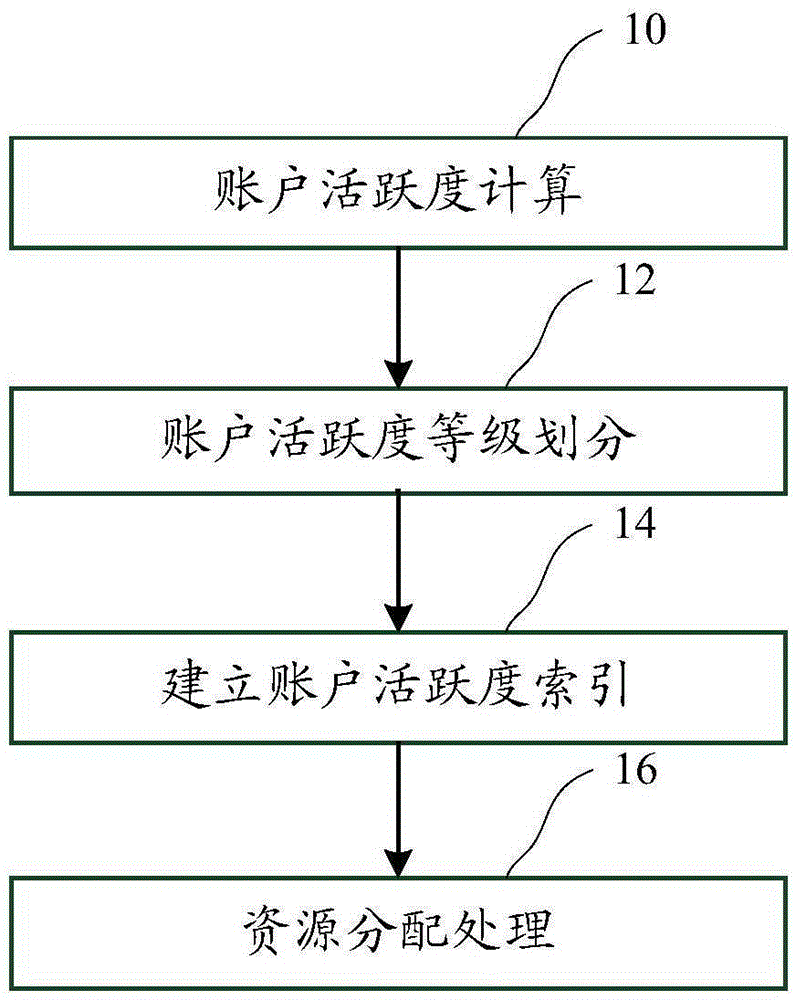
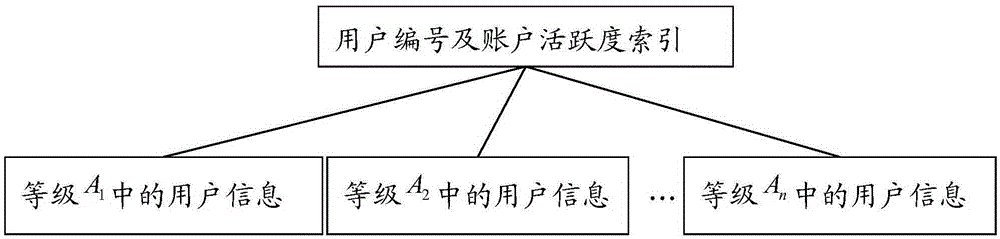
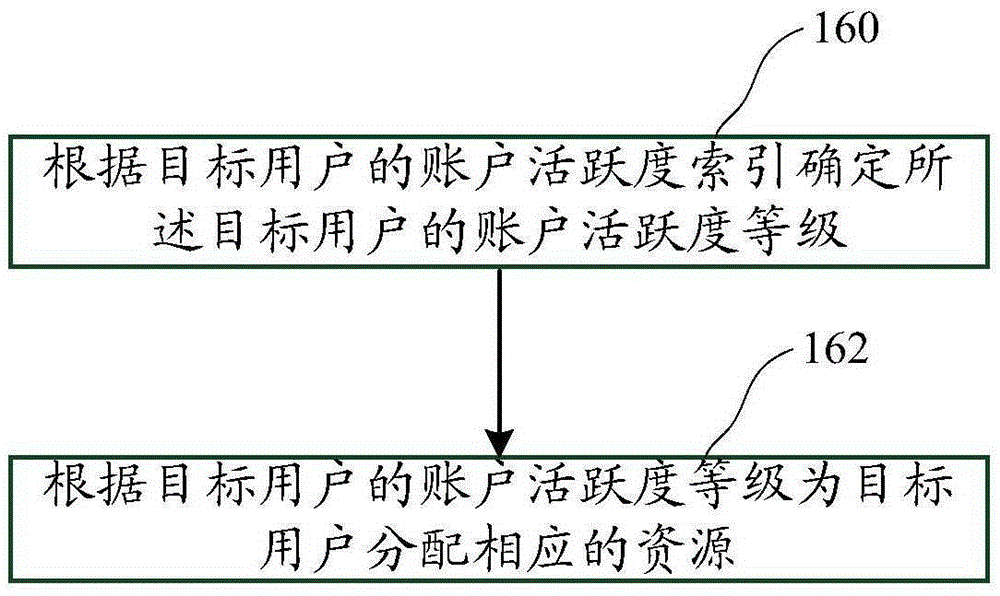
Account activeness-based system resource allocation method and device
InactiveCN105391654AQuick responseReduce management costsProgram controlResourcesDistribution methodResource use
The invention discloses an account activeness-based system resource allocation method and device. The method includes the steps of: obtaining account activeness parameters of users and calculating the account activeness of each user according to the account activeness parameter of each user; according to the account activeness of each user and a preset account activeness grade division method, determining the account activeness grade of each user; according to a user serial number, the account activeness and the account activeness grade of each user, establishing an account activeness index of each user; and when information processing is performed on a target user, allocating system resources used for performing information processing for the target user according to the account activeness index of the target user. By adoption of the account activeness-based system resource allocation method, appropriate system resources can be allocated for users with different activeness in a targeted mode, thereby improving overall use efficiency of system resources, reducing management cost, and improving user experience.
Owner:CHINA CONSTRUCTION BANK
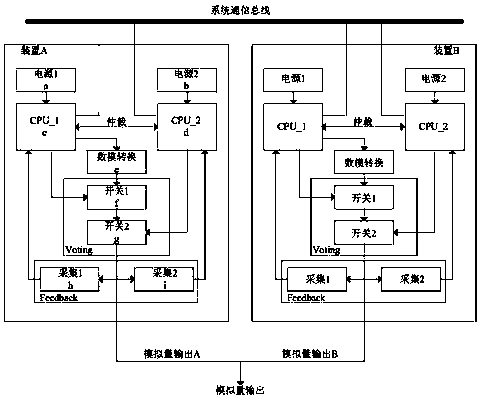
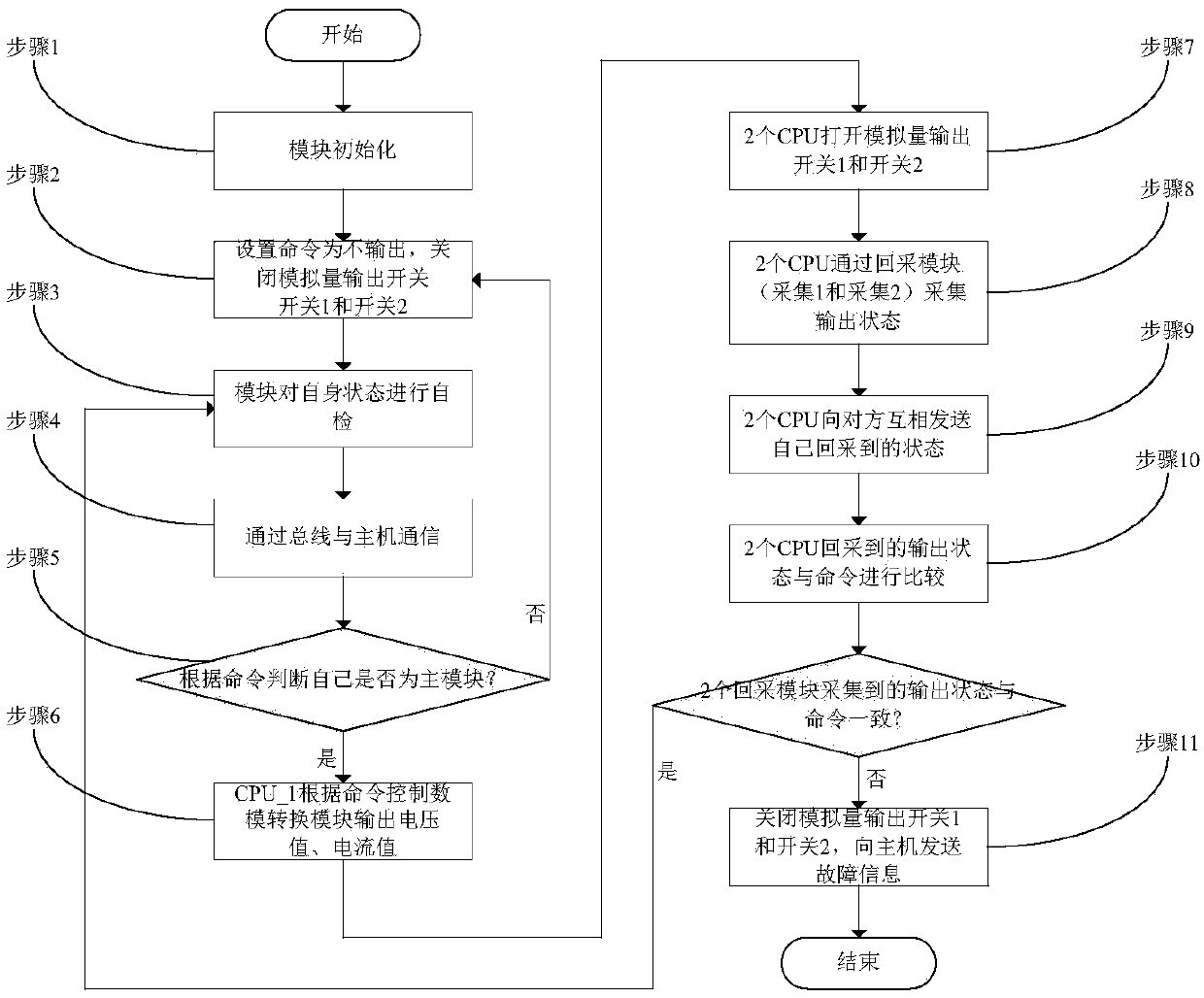
Analog quantity redundancy output devices and method with high reliability
PendingCN107942820ALow costImprove reliabilityProgramme controlComputer controlCommunications systemOutput device
The invention relates to analog quantity redundancy output devices and method with high reliability. The devices include a device A and a device B, the device A and the device B are connected with a host through a system communication bus to communicate, the device and the device B are mutually redundant and identical, one of the devices A and B is a main device and works in a main output state, the other device is a standby device and works in a standby state, when a fault of the main device occurs, reliable switching to the standby device is carried out, and the main device works in the standby state; and the original standby device is immediately switched into a main device to continue to output, and works in a main output state. Compared with the prior art, the analog quantity redundancy output devices with high reliability have the advantages of reducing cost and improving system reliability.
Owner:CASCO SIGNAL
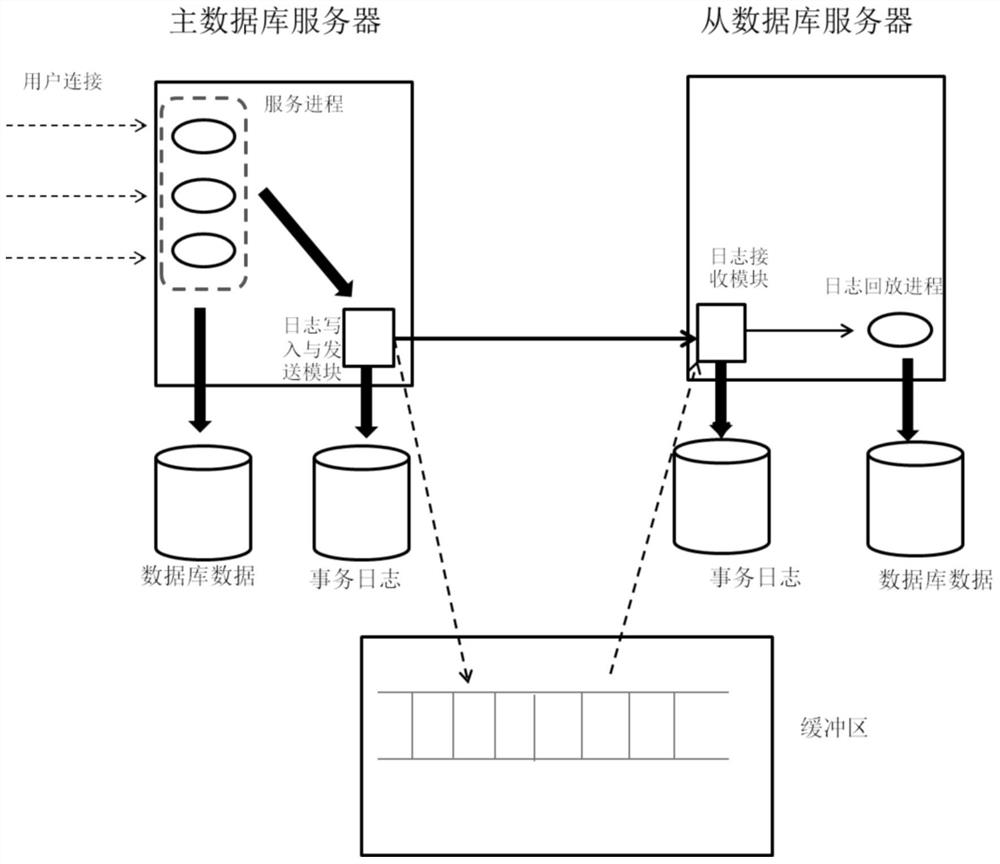
Service providing method for database and database system
ActiveCN106897288AGuaranteed not to loseImprove performanceError preventionSpecial data processing applicationsService provisionNetwork connection
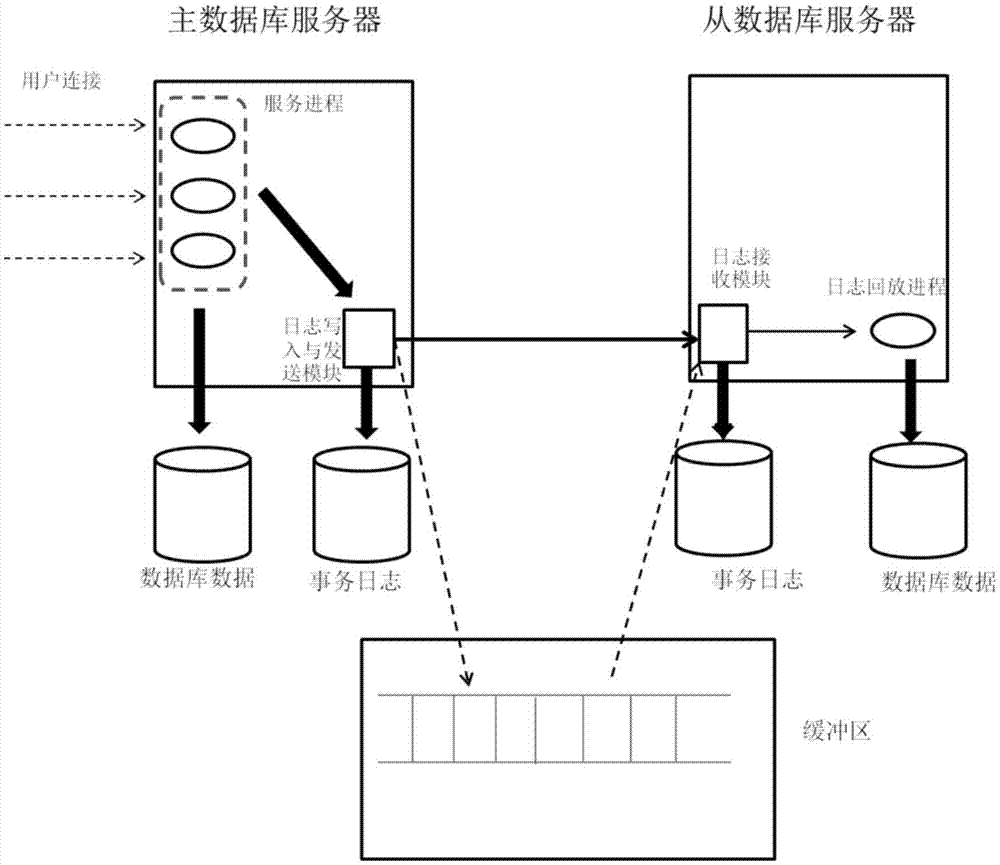
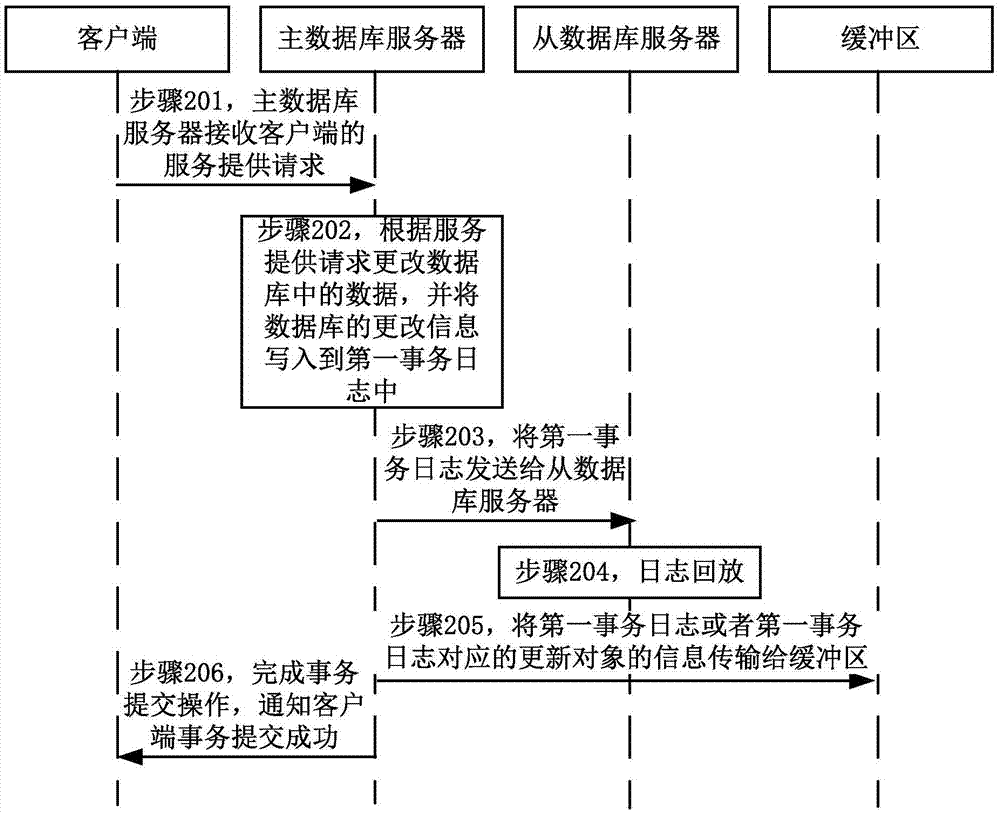
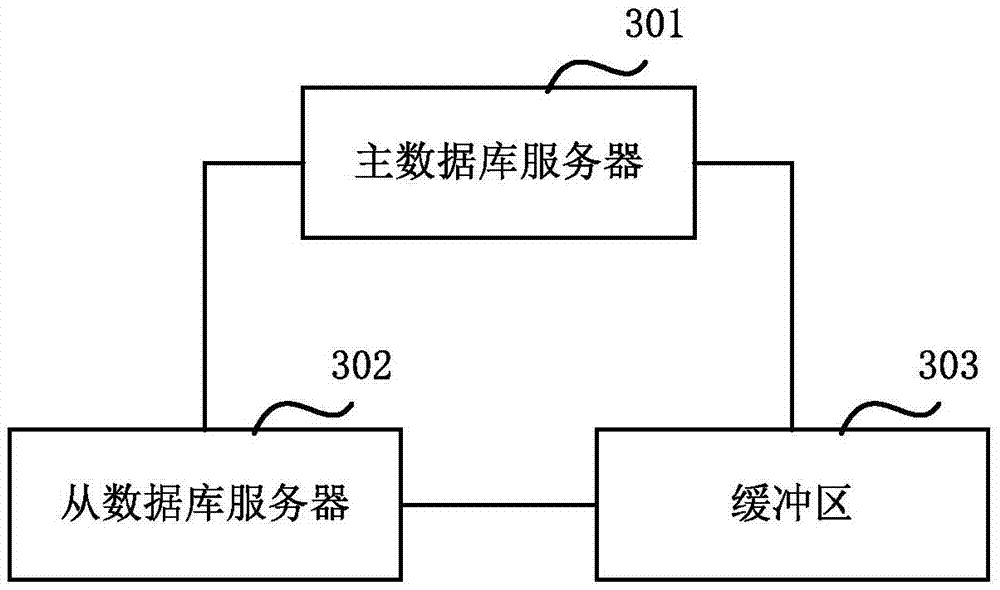
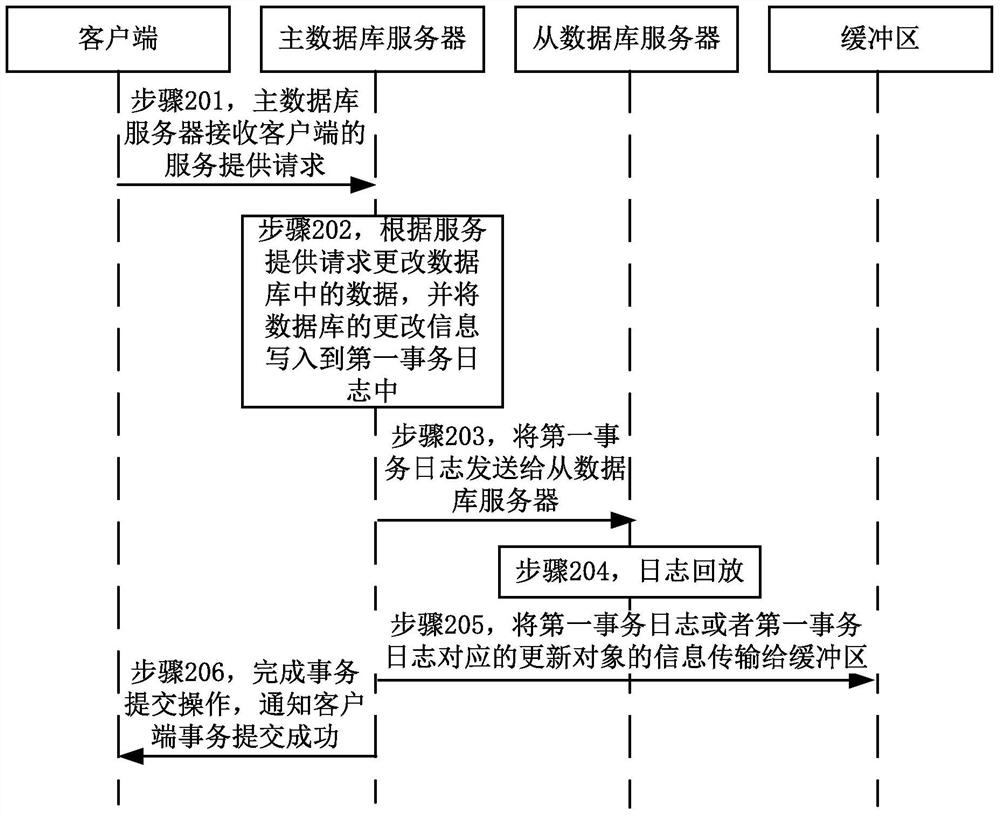
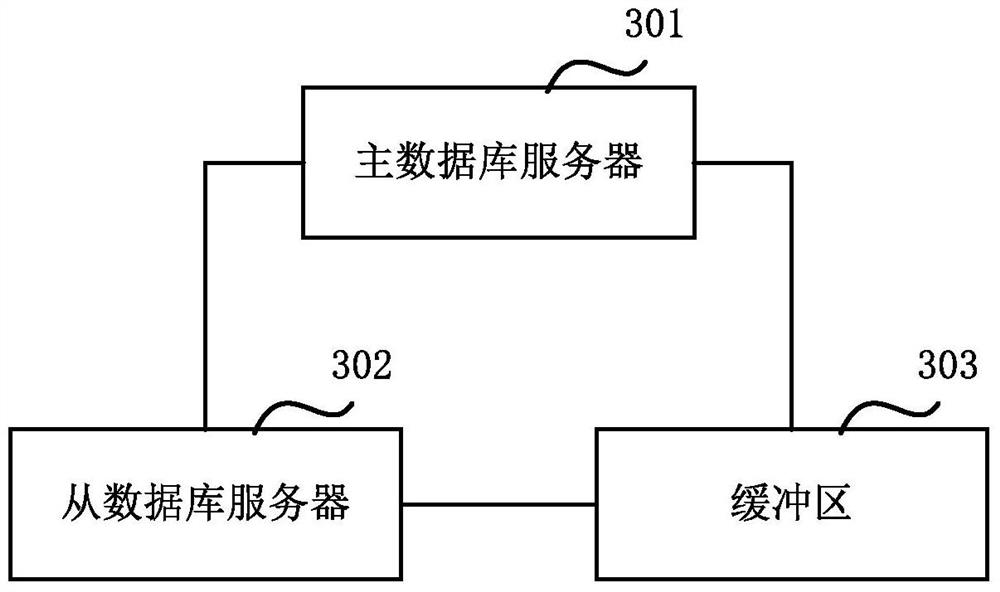
The embodiment of the invention relates to a service providing method of a data base, and a database system. The service providing method includes: when a master database server receives a service providing request of a client, the master database server changes data in a database according to the service providing request, writes change information of the database into a first transaction log, and sends the first transaction log to a slave database server; and when a network connection between the master database server and the slave database server is disconnected or time-out, or when the number of accumulated transaction logs which are not sent successively exceeds a preset number value in the master database server, or when the sending time of the first transaction log exceeds the preset time, the master database server transmits the first transaction log or information of an update object corresponding to the first transaction log to a buffer zone. In the embodiment of the invention, when a backup database cannot receive logs temporarily, the master database sends the logs to the buffer zone, and then the logs will not be lost.
Owner:ALIBABA GRP HLDG LTD
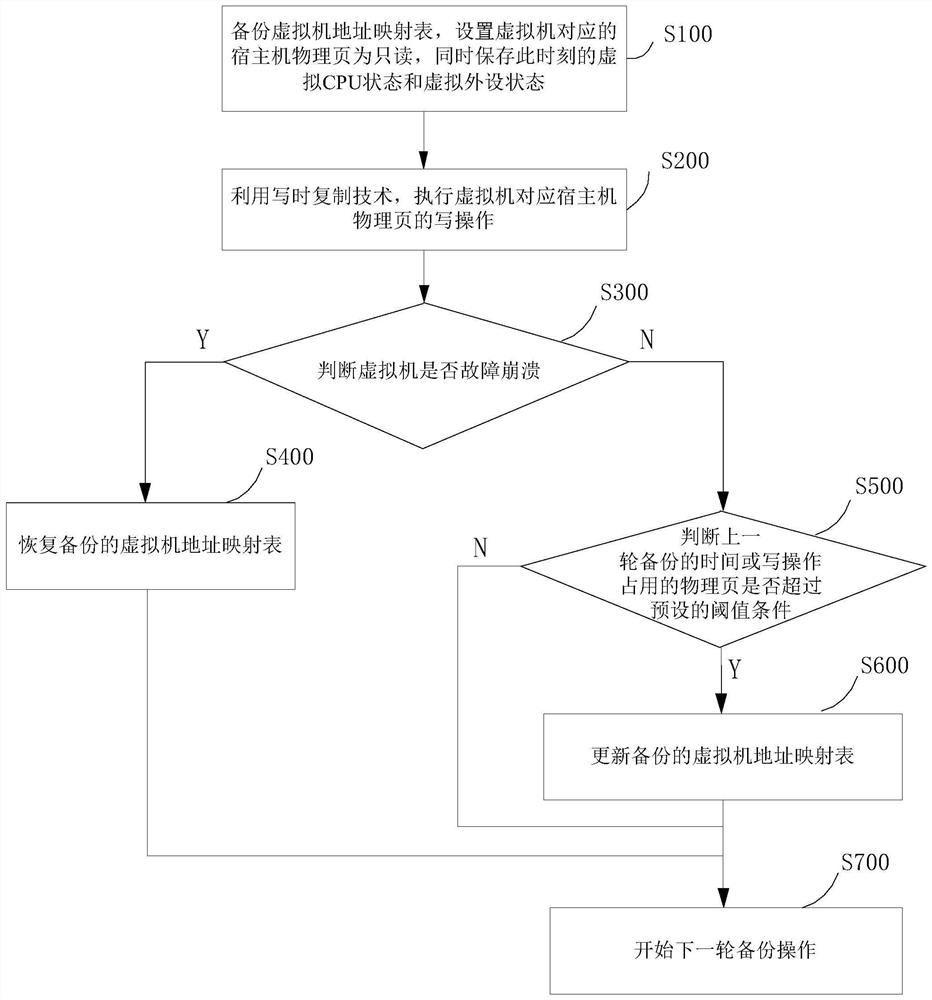
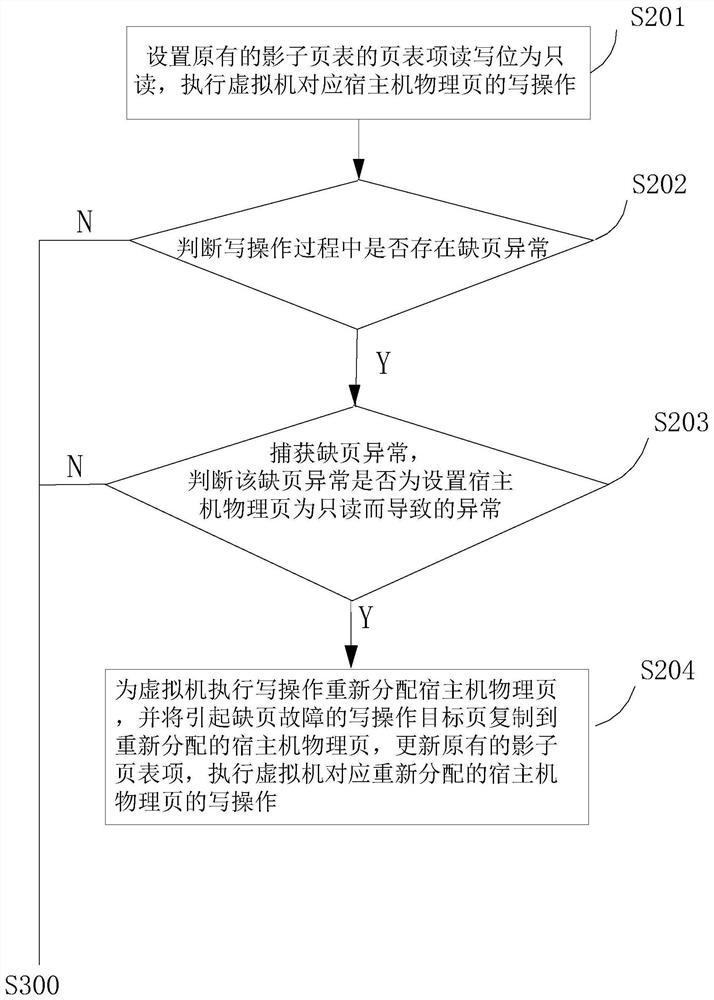
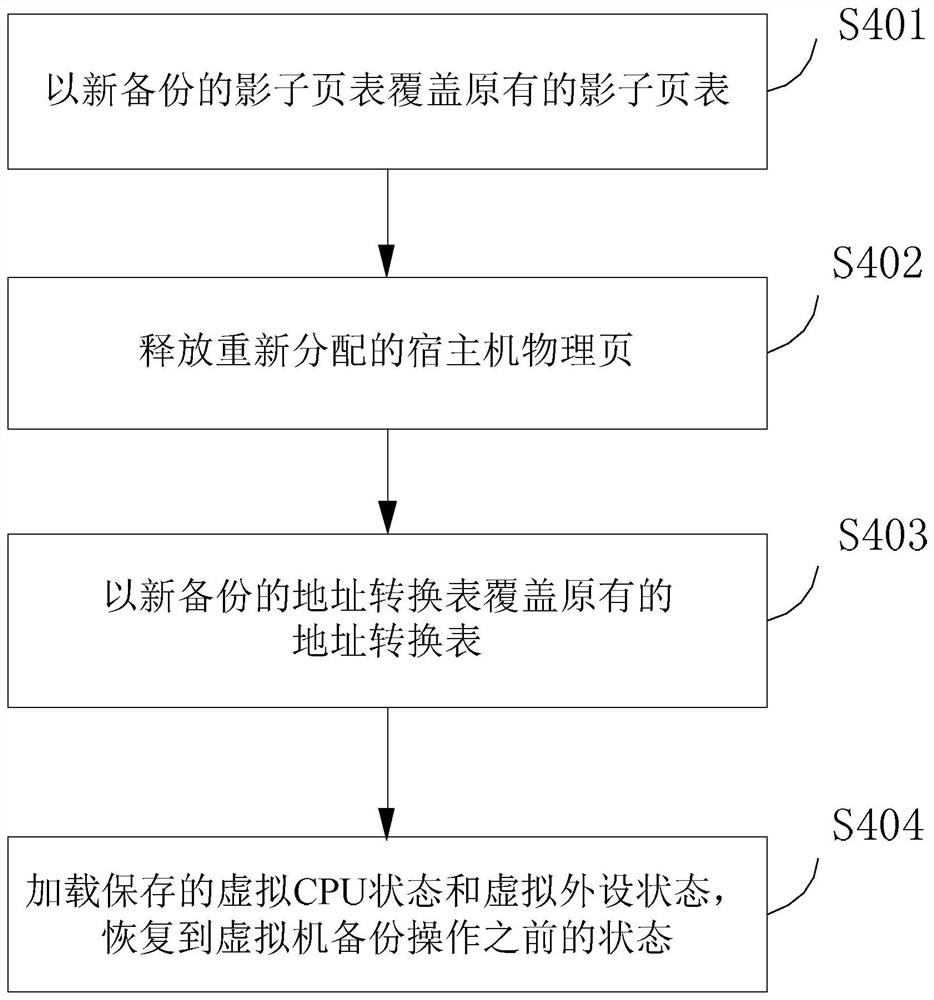
Virtual machine fault rapid recovery method and system
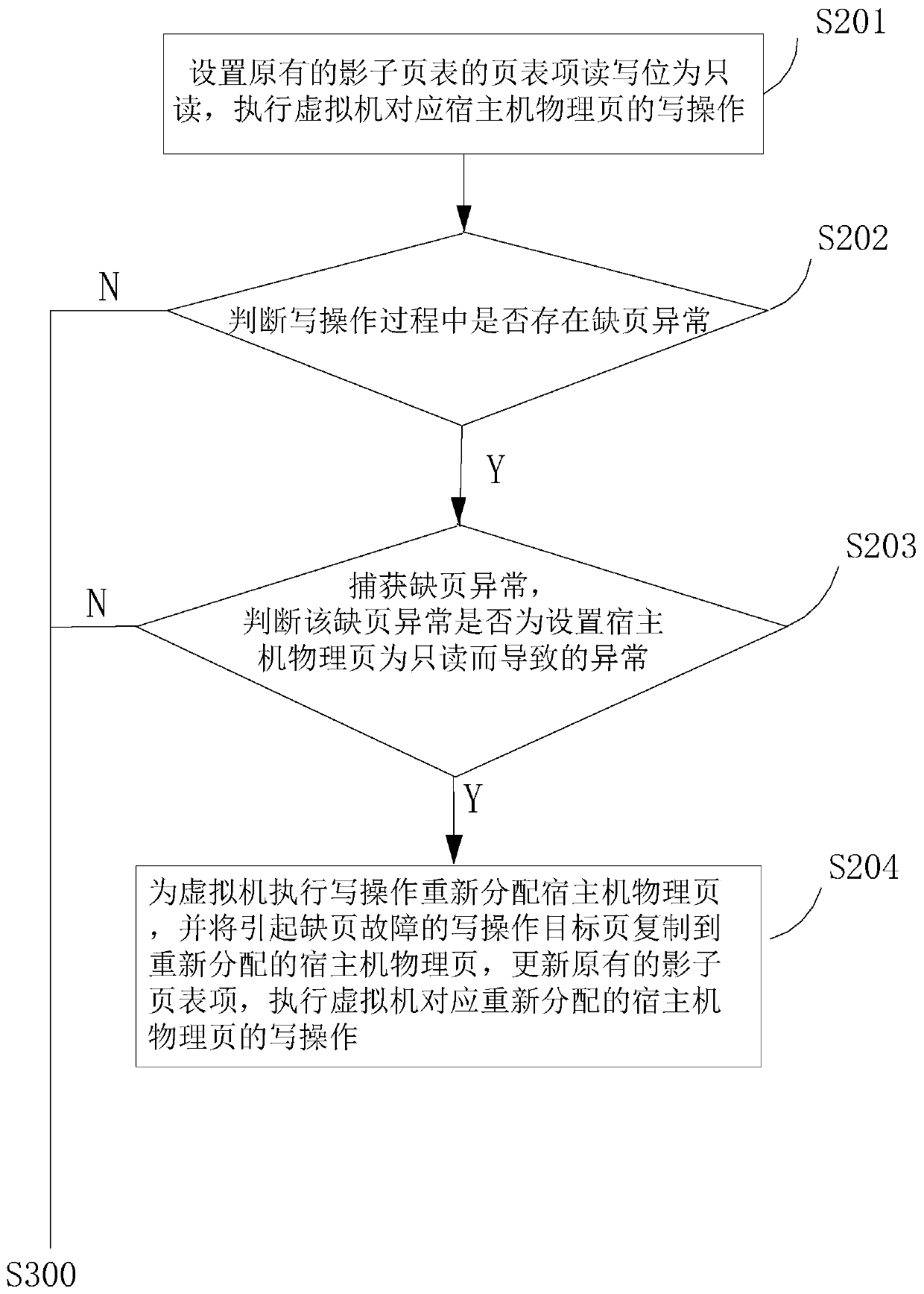
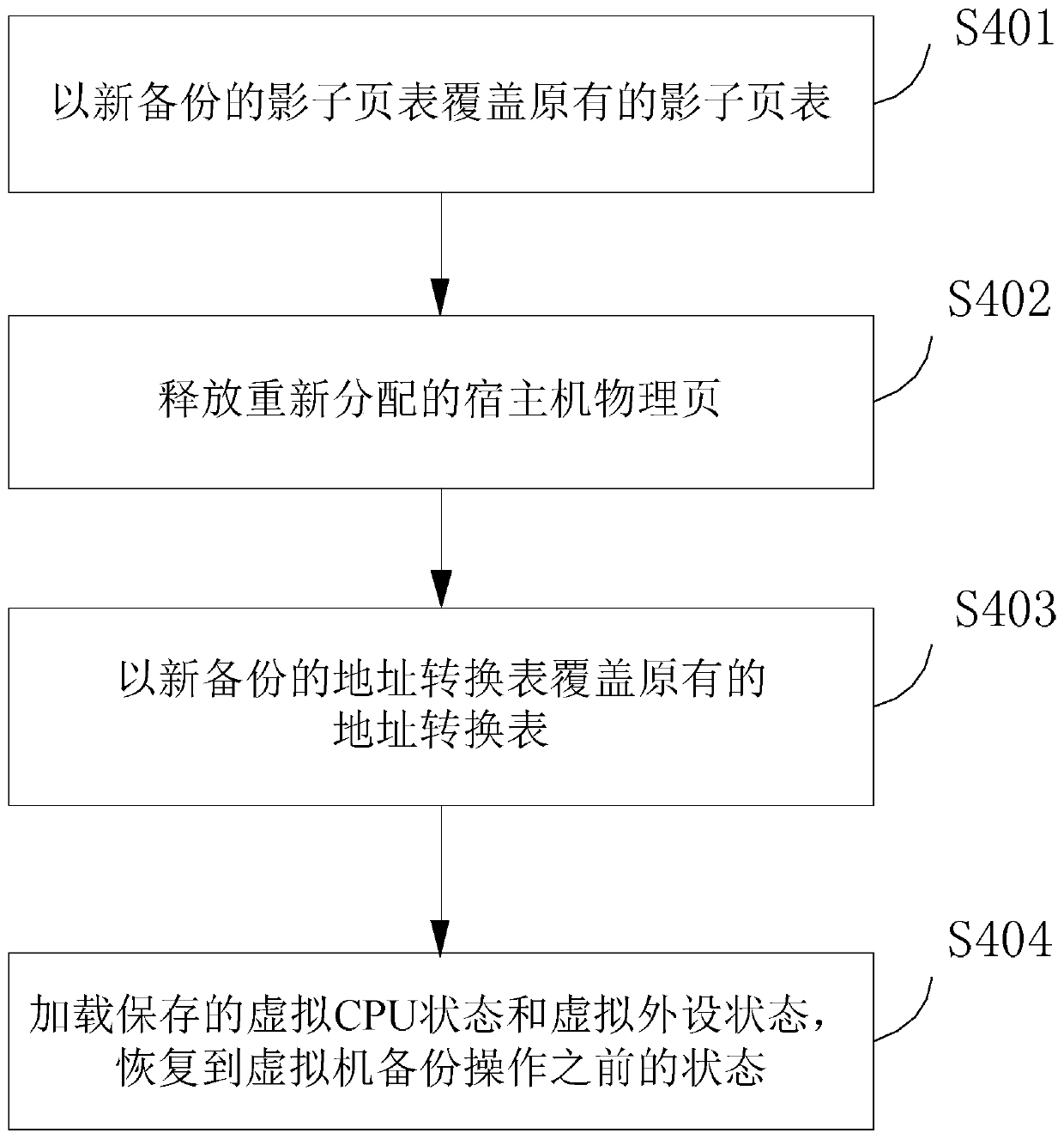
ActiveCN110018881AGuaranteed uptimeShort downtimeSoftware simulation/interpretation/emulationRedundant operation error correctionRecovery methodAddress mapping
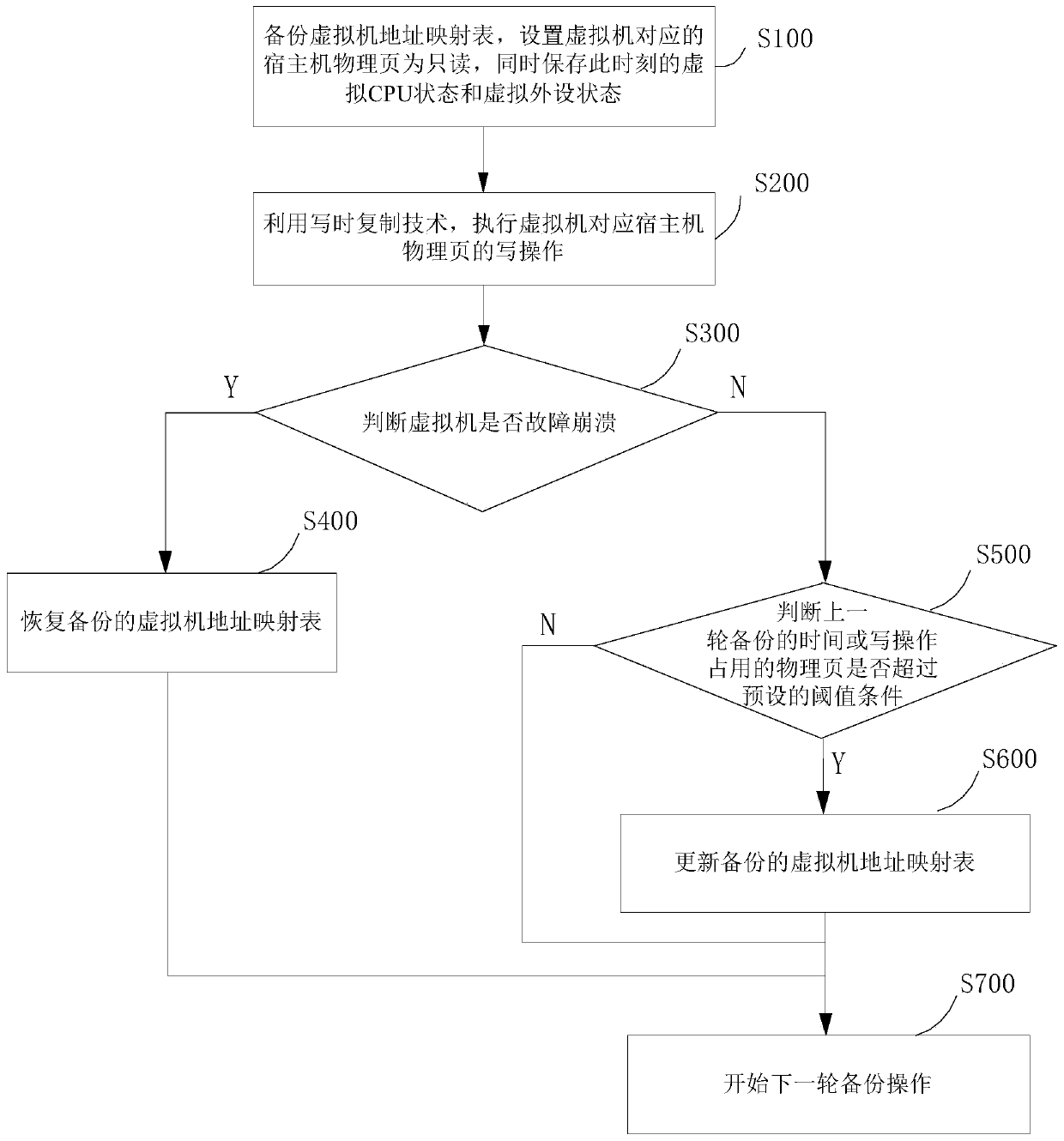
The invention discloses a virtual machine fault rapid recovery method and system. A virtual machine address mapping table is backed up, a host machine physical page corresponding to the virtual machine is set to be read-only, protection of host machine physical memory content corresponding to the virtual machine is achieved through the write-time copying technology, and after the virtual machine breaks down, the previous backup state of the virtual machine can be rapidly recovered. The method has the advantages of being small in backup data size, high in backup and recovery speed and the like,and reliable operation of the virtual machine is guaranteed.
Owner:XI AN JIAOTONG UNIV +1
Monitoring system utilizing power grid intelligent videos
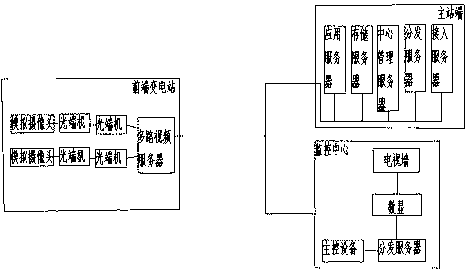
InactiveCN103297763ARealize monitoringAchieve intelligent video surveillanceClosed circuit television systemsTransmissionTransformerPower grid
The invention discloses a monitoring system utilizing power grid intelligent videos. The monitoring system utilizing power grid intelligent videos comprises a front-end transformer substation, a main station end and a monitoring center which are connected through a power data network. The front-end transformer substation comprises a multi-channel video server, optical transmitter-receiver and a simulation camera. The main station end comprises multiple communicated servers. The monitoring center comprises a television wall, a digital displayer, a server and a main control device which are connected in sequence. By adopting the structure, the power grid intelligent videos and environment cluster monitoring are combined well, the flexibility is high, and the availability of the system is not influenced by adding or omitting of a vidicon and the servers.
Owner:SICHUAN YOUMEI INFORMATION TECH
Virtual shared storage in a cluster
InactiveCN103546529ADoes not affect availabilityInput/output to record carriersError detection/correctionVirtual hostingNamespace
The present invention minimizes the cost of establishing a cluster that utilizes shared storage by creating a storage namespace within the cluster that makes each storage device, which is physically connected to any of the nodes in the cluster, appear to be physically connected to all nodes in the cluster. A virtual host bus adapter (VHBA) is executed on each node, and is used to create the storage namespace. Each VHBA determines which storage devices are physically connected to the node on which the VHBA executes, as well as each storage device that is physically connected to each of the other nodes. All storage devices determined in this manner are aggregated into the storage namespace which is then presented to the operating system on each node so as to provide the illusion that all storage devices in the storage namespace are physically connected to each node.
Owner:MICROSOFT TECH LICENSING LLC
Behavior analysis method and device of target object, electronic equipment and storage medium
PendingCN113486777AImprove accuracySolve the excessive alarm rateImage enhancementImage analysisEngineeringAction prediction
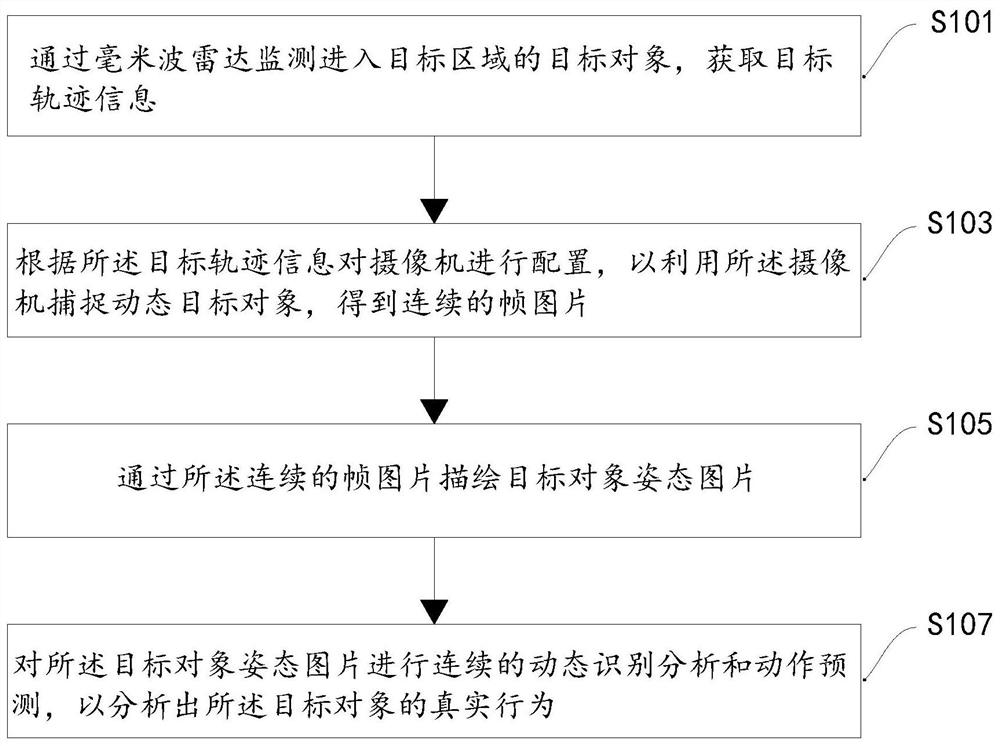
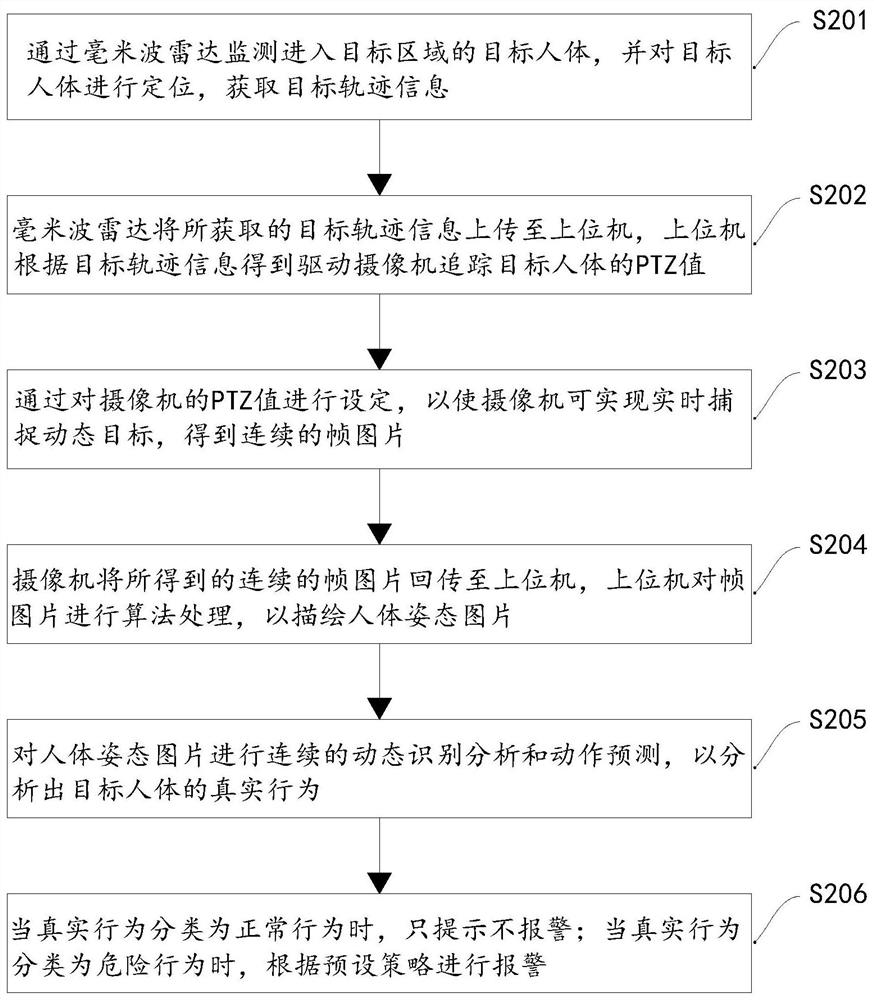
The embodiment of the invention discloses a behavior analysis method and device for a target object, electronic equipment and a storage medium, and the method comprises the steps of monitoring a target object entering a target region through a millimeter-wave radar, and obtaining target track information; configuring a camera according to the target track information so as to capture a dynamic target object by using the camera to obtain continuous frame pictures; describing a target object posture picture through the continuous frame pictures; and carrying out continuous dynamic identification analysis and action prediction on the target object posture picture so as to analyze the real behavior of the target object.
Owner:北京一维大成科技有限公司
Privacy protection query language PQL and system thereof
InactiveCN112162998AEnsure safetyDoes not affect availabilityDigital data information retrievalDigital data protectionError checkLexical analysis
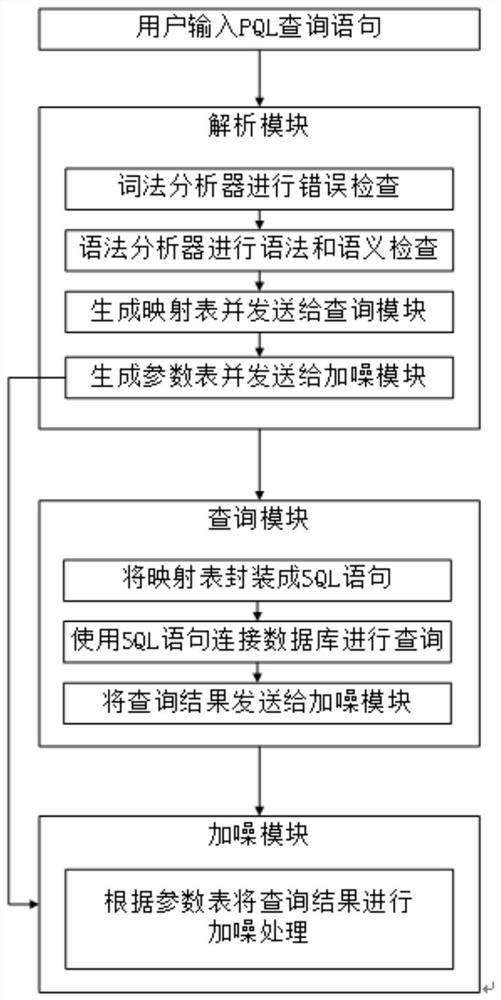
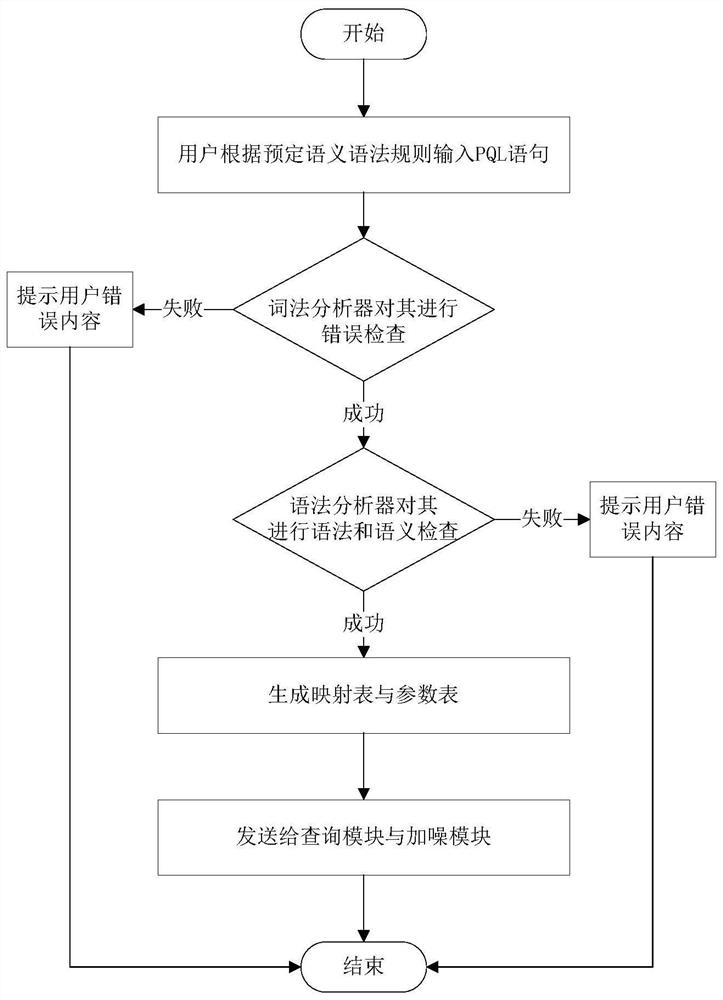
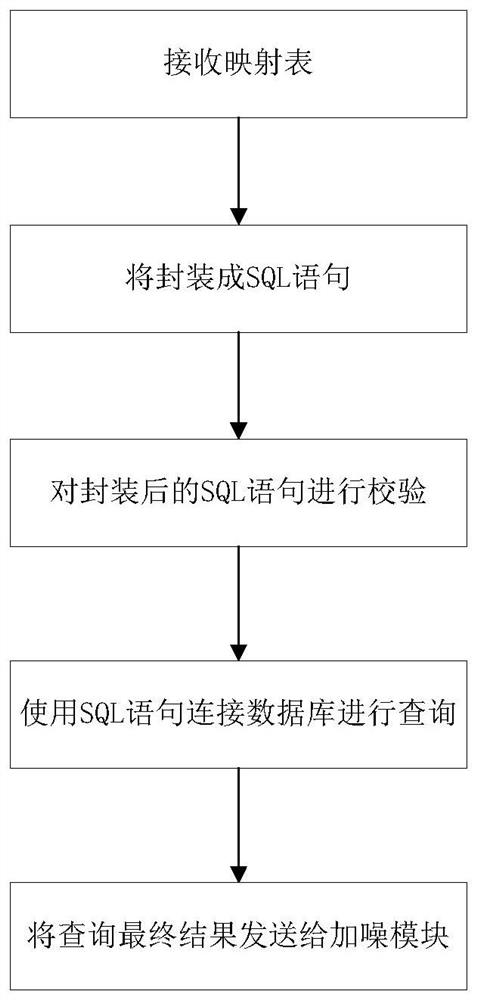
The invention discloses a privacy protection query language PQL and a system thereof; the system comprises a PQL statement and a system, and the system comprises an analysis module, a query module anda noise adding module; the analysis module comprises a lexical analyzer and a syntactic analyzer; a user inputs a PQL statement according to a preset semantic grammar rule, and after receiving the PQL statement, an analysis module performs error check on the PQL statement through a lexical analyzer and sends a correct result to a grammar analyzer; performing grammar and semantic check on the PQLstatement by a grammar analyzer, and generating a mapping table and a parameter table according to a correct result; the query module encapsulates the mapping table into an SQL statement after receiving the mapping table, and verifies the encapsulated SQL statement; the noise adding module acquires a final query result of the query module and calculates noise adding sensitivity according to the parameter table; according to the invention, the security of data privacy is ensured, and the availability of the data is not influenced by the added noise.
Owner:XUZHOU MEDICAL UNIV +1
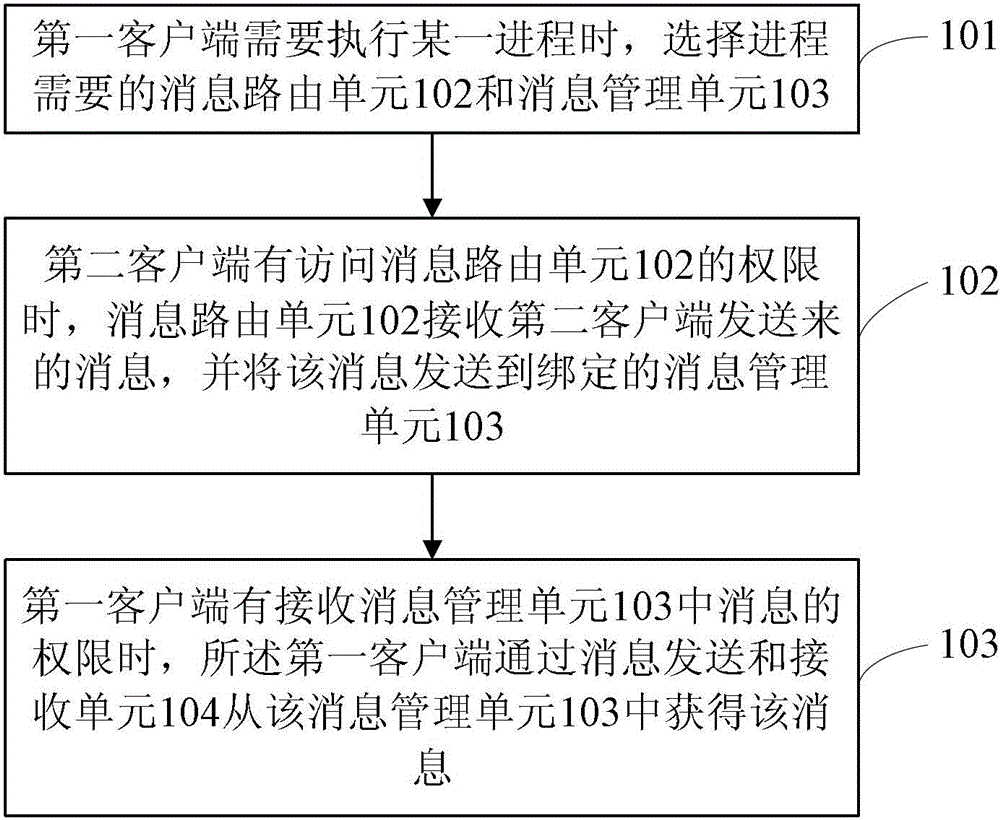
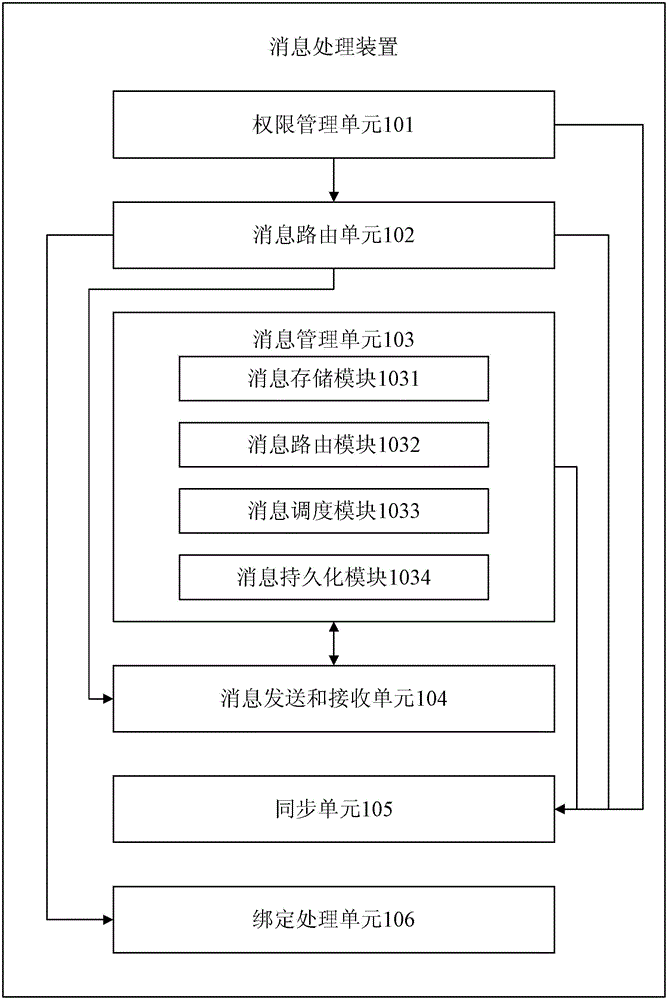
Method and device for message processing
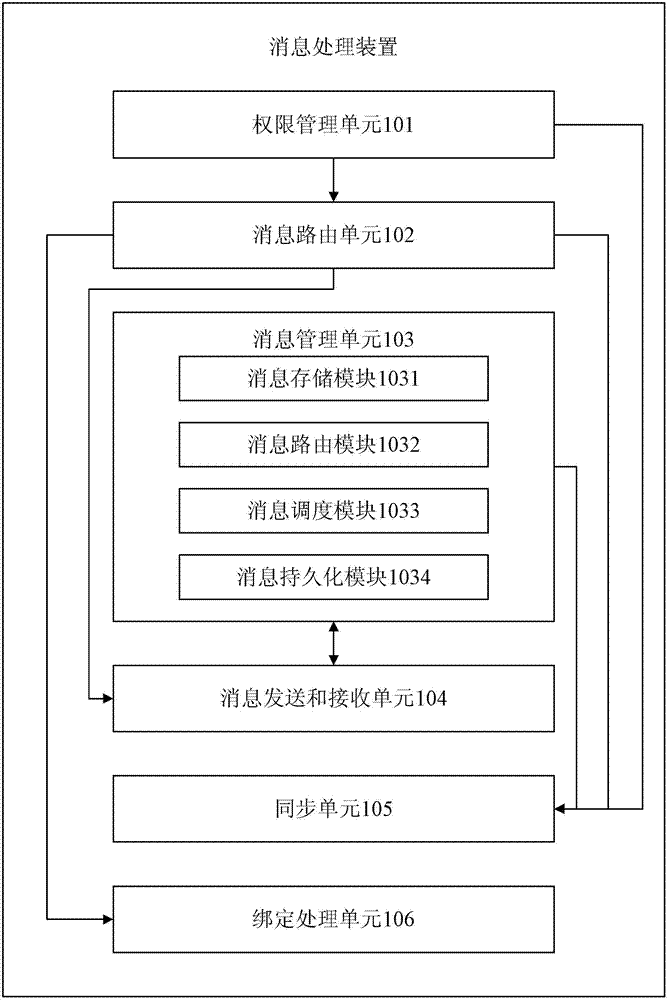
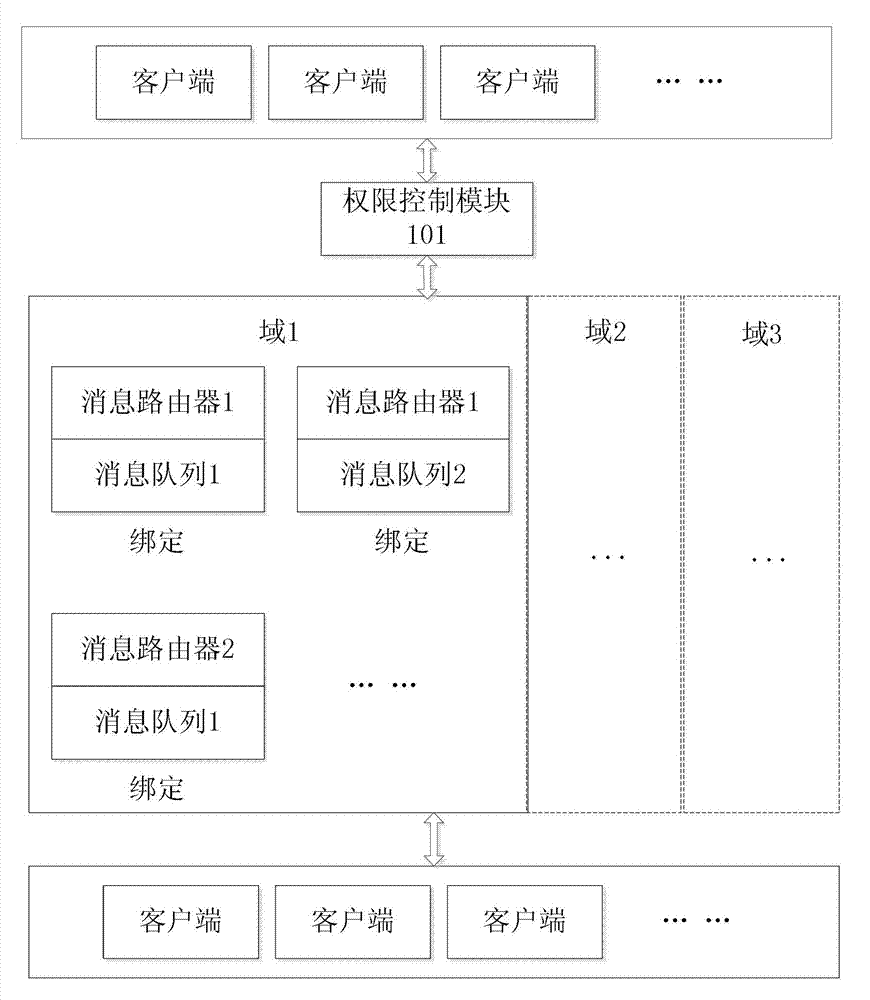
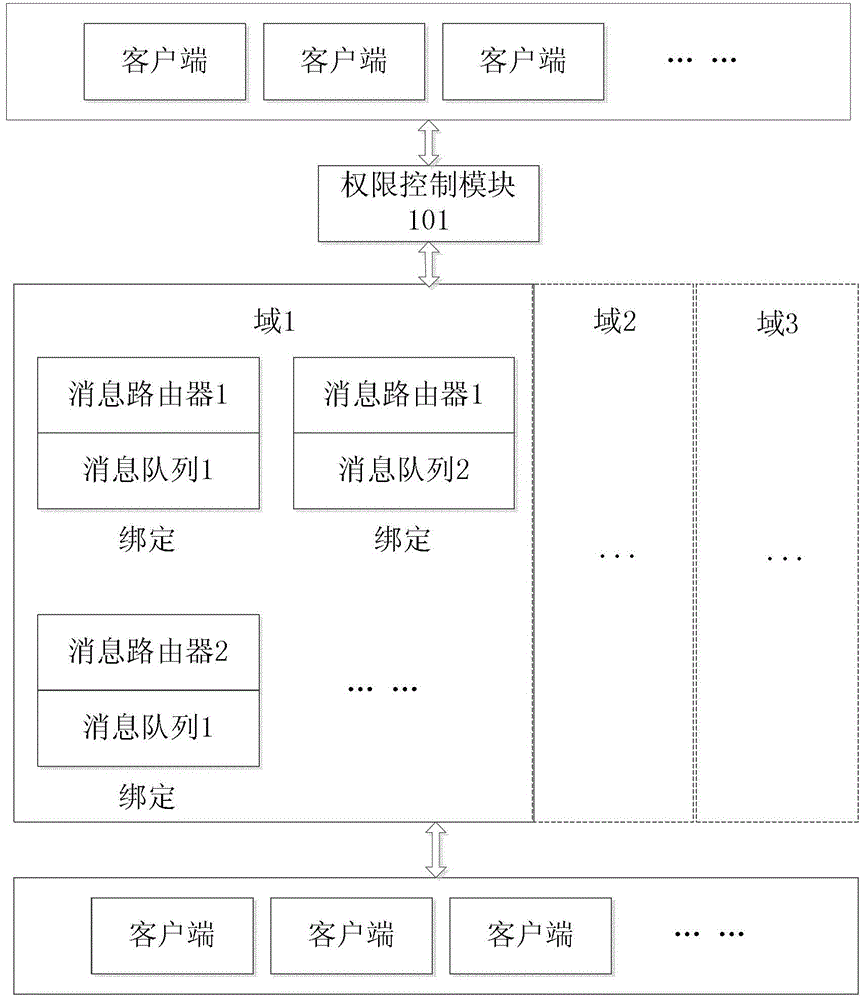
ActiveCN102868594AAchieve isolationAvoid mutual interferenceData switching networksManagement unitPassword
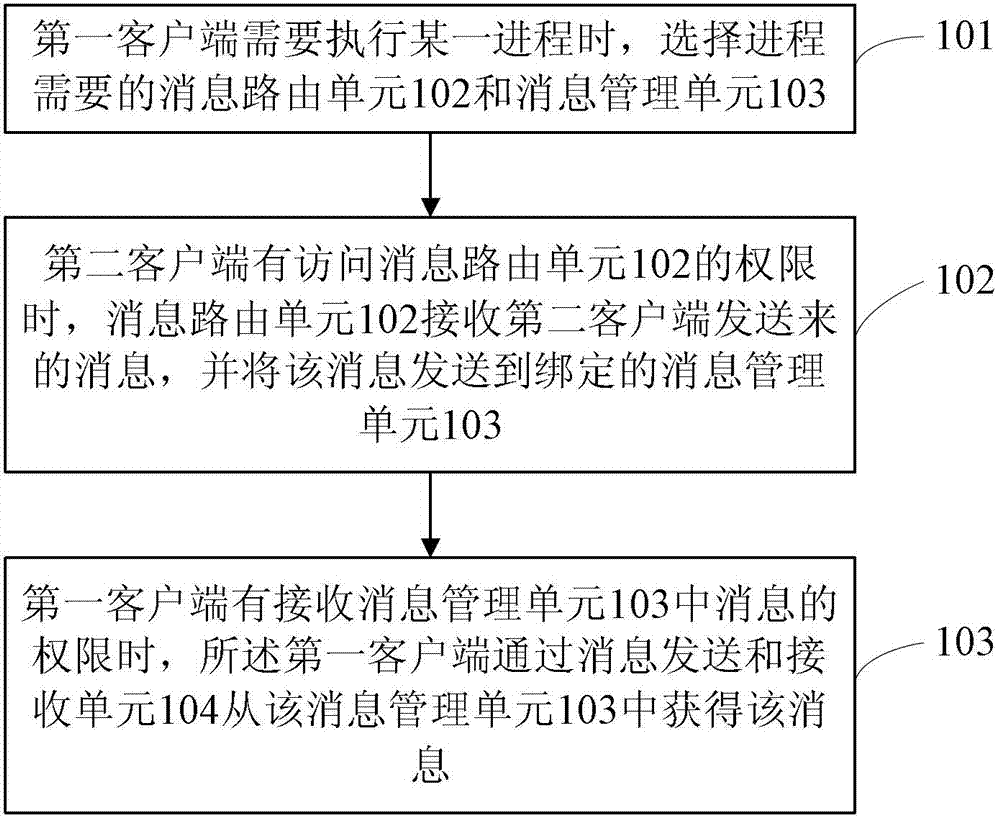
The invention relates to a method and a device for message processing. The device comprises an authority management unit, a message routing unit, a message management unit and a message transmitting and receiving unit. When one process needs to be implemented by a first client side, an application is sent to the message processing device, whether the first client side has the authority of access to a domain established by the authority management unit is judged by the authority management unit according to a username and a password input by the first client side, and if the first client side has the authority of access to the domain established by the authority management unit, a message routing unit and a message management unit required for the process are selected from message routing units and message management units specified by the domain with a process corresponding to the username and the password input by the client side, a corresponding relationship to the process is established, and the selected message routing unit and the selected message management unit are bound by set binding rules. The method and the device have the advantages of good universality and portability.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Continuous casting system particularly for long steel products, and a method for continuous casting
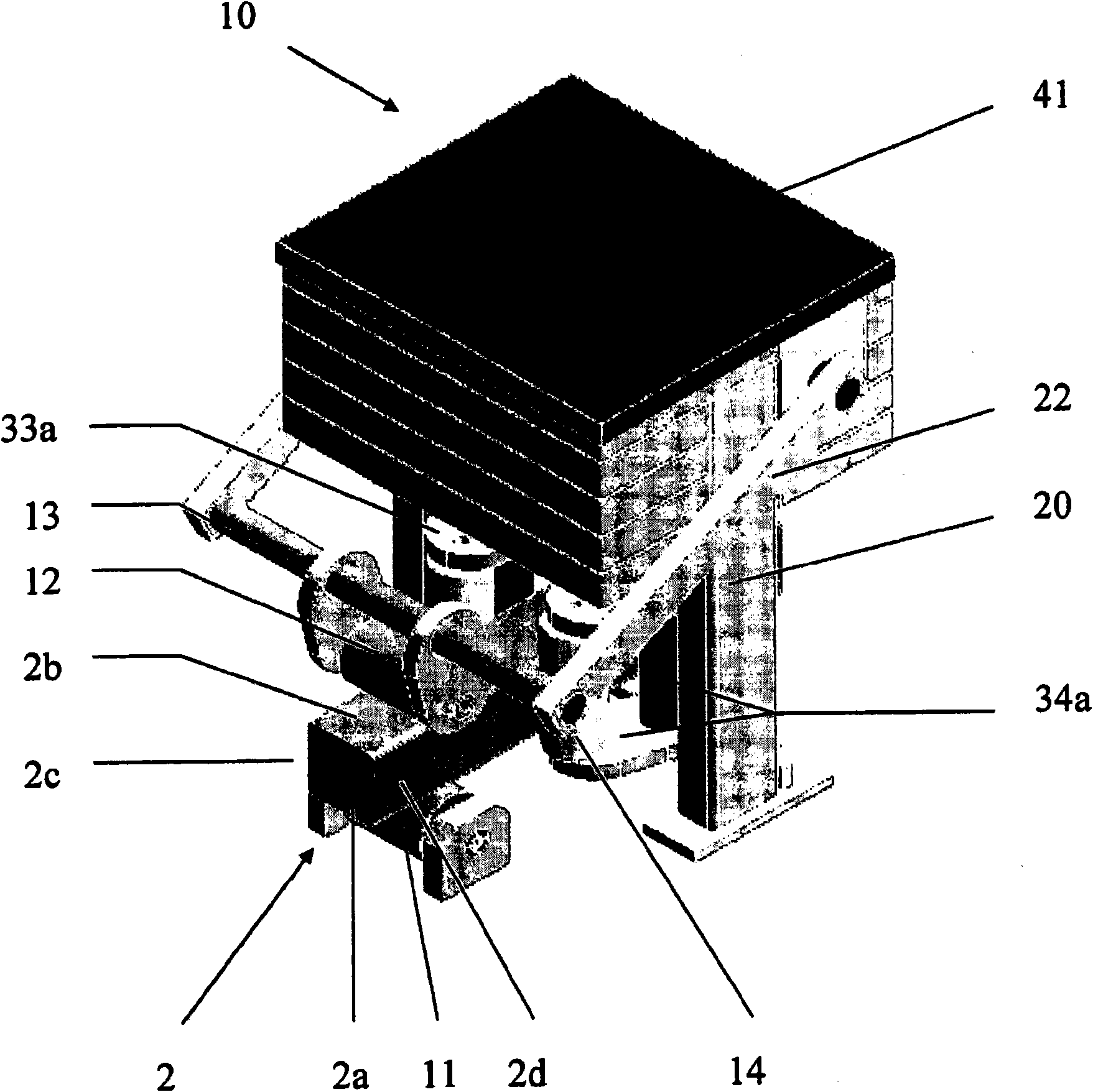
InactiveCN101970151AReduced risk of strand surface damageGuaranteed symmetrical coolingGravitationMetallurgy
The invention relates to a continuous casting system, particularly for long steel products, having a gravity die wherefrom a cast slab (2) is continuously cast. The cast slab (2) is formed along a guide track formed by guide rollers disposed one after the other (11, 12, 13, 14), particularly a curved guide track, and substantially fed into a cooling chamber having spray heads. The guide rollers (12, 13, 14) and / or the spray heads are present in a plurality of centering modules (10) or spray modules (3) disposed one after the other, and can be adjusted substantially concentrically to the target axis of the cast slab. The risk of thermal overload of the rollers and of damage to the slab surface is thereby significantly reduced, and the symmetrical cooling is also ensured.
Owner:SMS CONCAST
Cross-road-network location anonymization method keeping statistical characteristics unchanged
ActiveCN107682817AAvoid gettingStatistical characteristics do not changeLocation information based serviceSecurity arrangementUser privacyRoad networks
The invention discloses a cross-road-network location anonymization method keeping statistical characteristics unchanged. First, road networks are extracted according to the road distribution in a target area, and road network areas are obtained through partitioning; then, a location anonymization candidate set meeting the protection requirements is constructed according to an actually needed scope of protection and the center-of-mass location of each road network area; and finally, a location anonymized road network area is determined according to the location point number difference, center-of-mass point distance and other parameters between a to-be-protected road network area and the road network areas in the candidate set, and cross-road-network location anonymization is carried out through location exchange. Road network areas are obtained through partitioning using road networks, and location anonymization is carried out between different road network areas, which can prevent attackers from acquiring user privacy by making use of the background knowledge of the location-territory relationship. In the invention, location anonymization is carried out through location exchange,which can keep the statistical characteristics of the overall data unchanged and does not affect the availability of data after privacy protection.
Owner:XI AN JIAOTONG UNIV
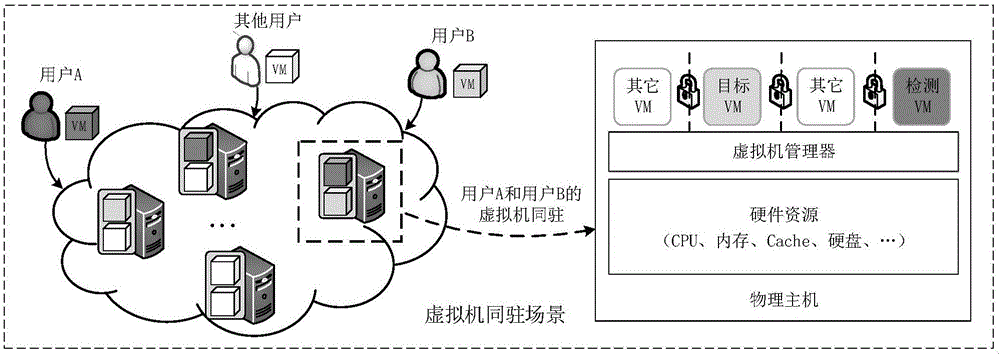
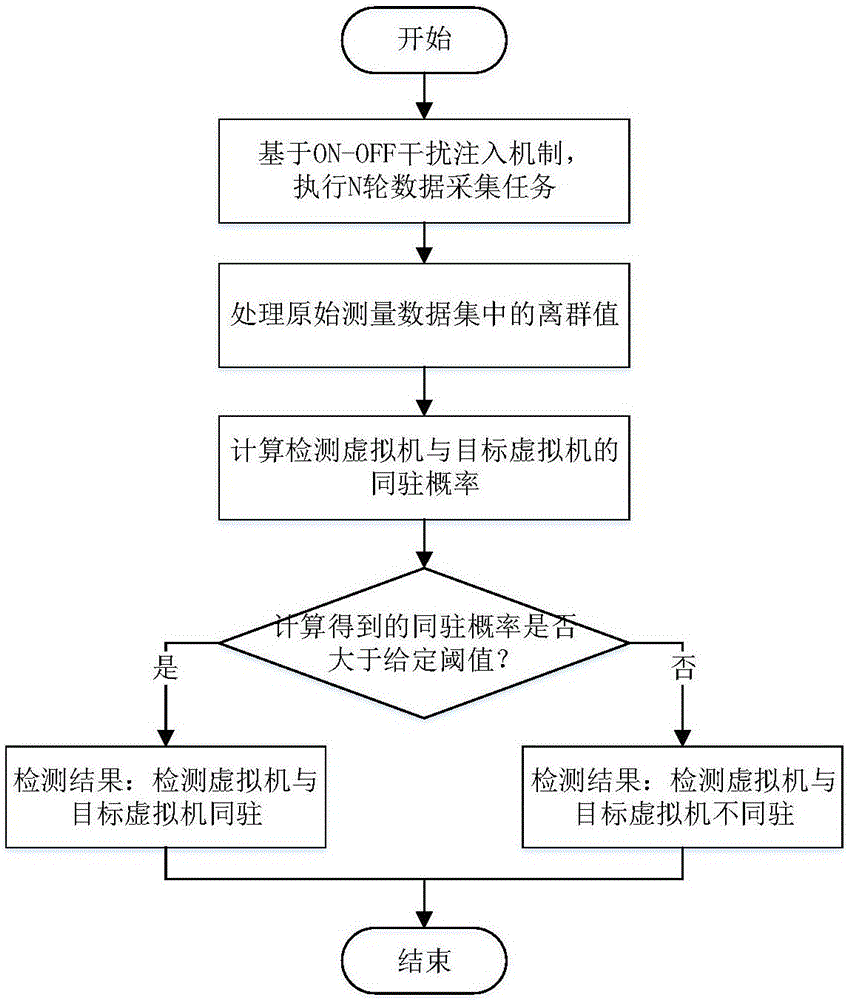
Virtual machine co-residency detection method based on response time sequence data analysis
ActiveCN106656678ADoes not affect availabilityDoes not affect effectivenessData switching networksSoftware simulation/interpretation/emulationCloud dropletDependability
The invention discloses a virtual machine co-residency detection method based on response time sequence data analysis. The method comprises the following steps of 1), performing real-time acquisition of a response time sequence of a target virtual machine based on an ON-OFF interference injection mechanism, and then respectively extracting response time sequences of the target virtual machine in an interference condition and a normal condition; 2), processing abnormal values in acquired data; 3), calculating a co-residency probability; and 4), determining a detection result. According to the method of the invention, according to a characteristic of sharing a multi-tenancy resource of a cloud computing platform, the service response time sequences of the target virtual machine in the normal condition and the interference condition are acquired; through defining deviation degree between cloud models, the co-residency between a detecting virtual machine and the target virtual machine is calculated, thereby quantitatively describing the co-residency possibility between the detecting virtual machine and the target virtual machine. The virtual machine co-residency detection method ensures high accuracy and high reliability of a co-residency detection result and furthermore has high adaptability and high practical value.
Owner:XI AN JIAOTONG UNIV
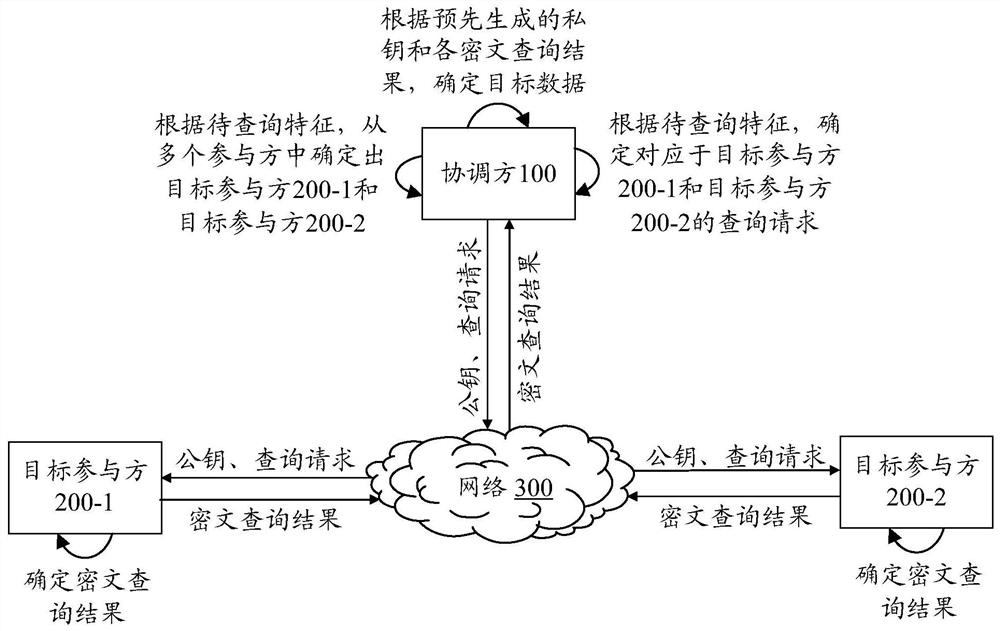
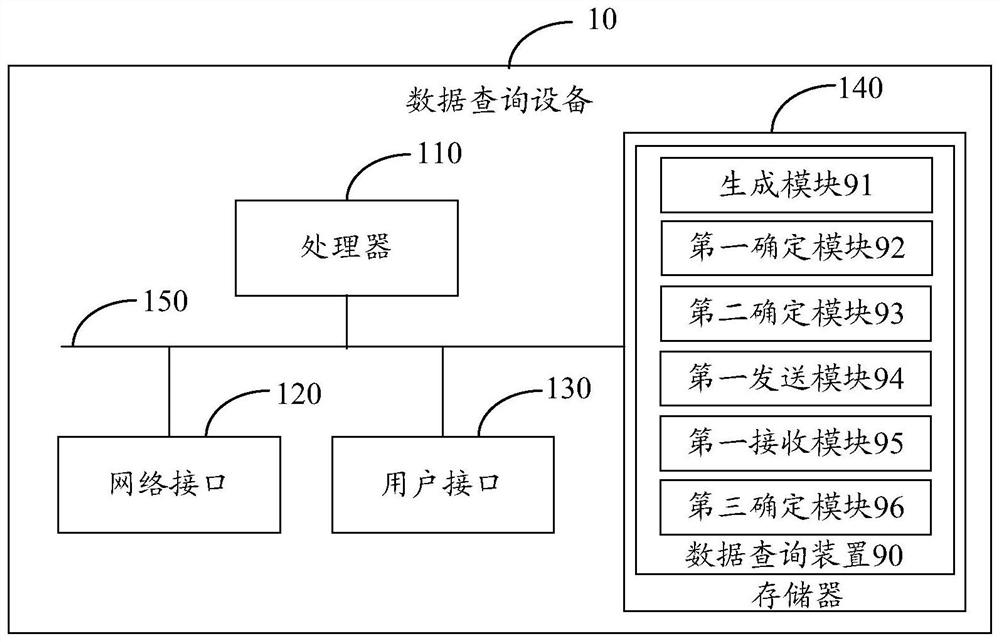
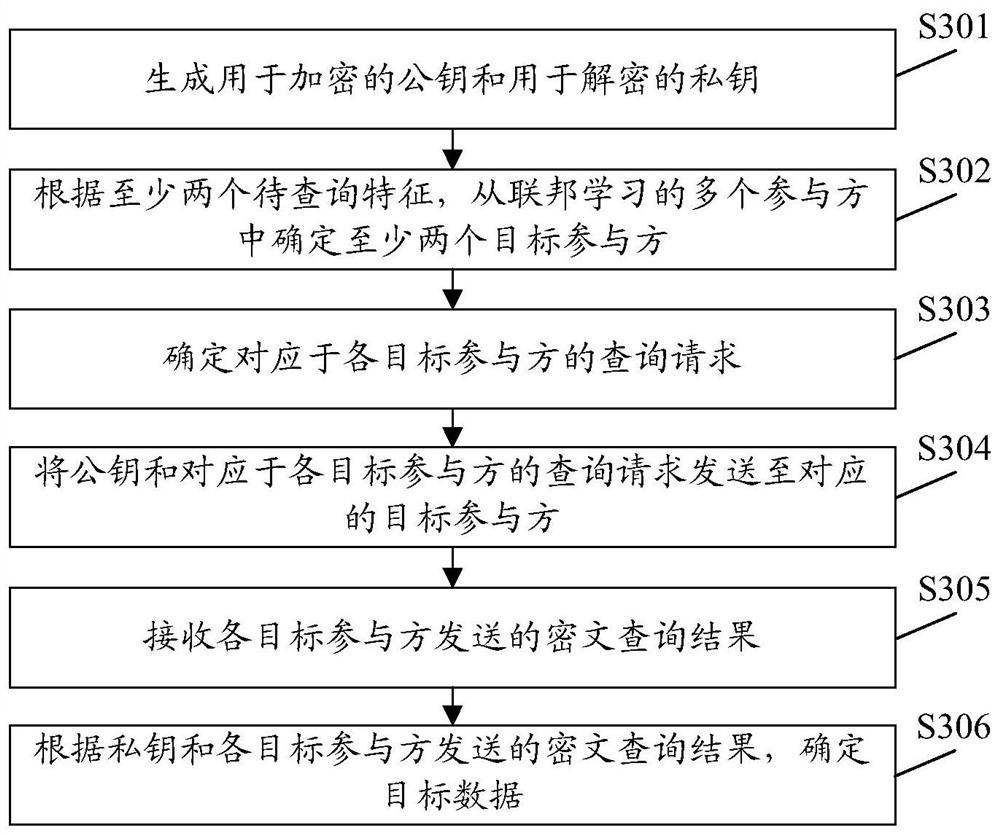
Data query method and device, equipment, storage medium and program product
PendingCN113239395ARealize cross-table queryPrivacy protectionDigital data protectionMachine learningCiphertextFeature data
The invention provides a data query method and device, equipment, a storage medium and a program product. The method comprises the steps that a coordinator generates a public key for encryption and a private key for decryption; at least two target participants are determined according to the at least two to-be-queried features, query requests corresponding to the target participants are determined, and feature data of part of the to-be-queried features are stored in the target participants; sending the public key and a query request corresponding to each target participant to the corresponding target participant; receiving a ciphertext query result sent by each target participant, wherein the ciphertext query result is determined by each target participant based on the public key and the query request received by each target participant; and determining target data according to the private key and the ciphertext query result sent by each target participant. The cross-table query of the data is realized on the premise of ensuring that the data is not out of the local of each participant, so that the data privacy can be protected, the data leakage is prevented, and the availability of the queried target data is not influenced.
Owner:WEBANK (CHINA)
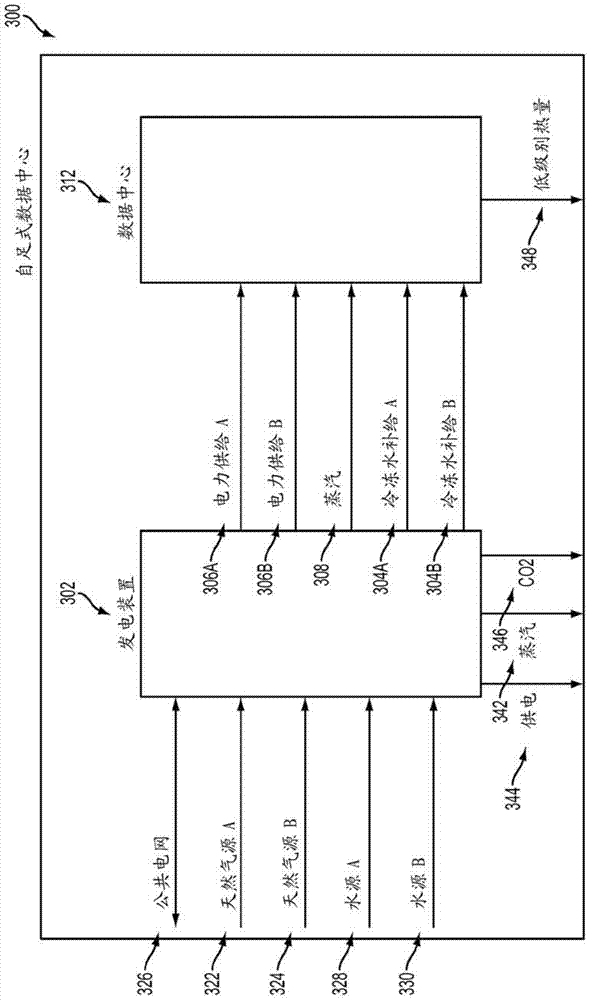
Integrated power plant and data center
InactiveCN104508932AReduce or eliminate storageReduce transmissionElectric signal transmission systemsSteam useElectricityData center
A power plant, in the form of a combined heat and power (CHP) plant, may be co-located with a data center to provide redundant electrical power. The CHP plant and the data center may operate as an island, separate from the local electrical-utility grid. The CHP plant may have a redundant fuel source connection to reduce unavailability of fuel for the CHP and increase the uptime of the data center. The CHP plant may include turbines and engines to manage variable loads within the data center. The power plant may include multiple distributions busses in high-availability configurations to provide highly-reliable and high-quality electricity to the data center. The positioning of these elements in the power plant design provides economies of scale and eliminates single points of failure commonly found in data center configurations, increasing the reliability of the data center.
Owner:K2IP HLDG LLC
Multistage-mapping-based large-scale multi-copy distributed storage system and application method thereof
ActiveCN102571991BImprove storage utilizationImprove scalabilityTransmissionNode clusteringDistributed computing
The invention discloses an application method of a multistage-mapping-based large-scale multi-copy distributed storage system. The problems of data hash imbalance, incapability of supporting copies and node weights, great difficulty in management and the like of the large-scale distributed storage system in the prior art are solved. The multistage-mapping-based large-scale multi-copy distributed storage system comprises a storage node cluster, a management node, a client and a regular node cluster, wherein the storage node cluster is used for storing resources; the management node and the client are connected with the storage node cluster respectively; the management node manages the storage node cluster; the client acquires the storage positions of the resources according to a hash mechanism; and the regular node cluster is connected with the management node and the client and managed by the management node, and provides hash mapping rules for the client.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
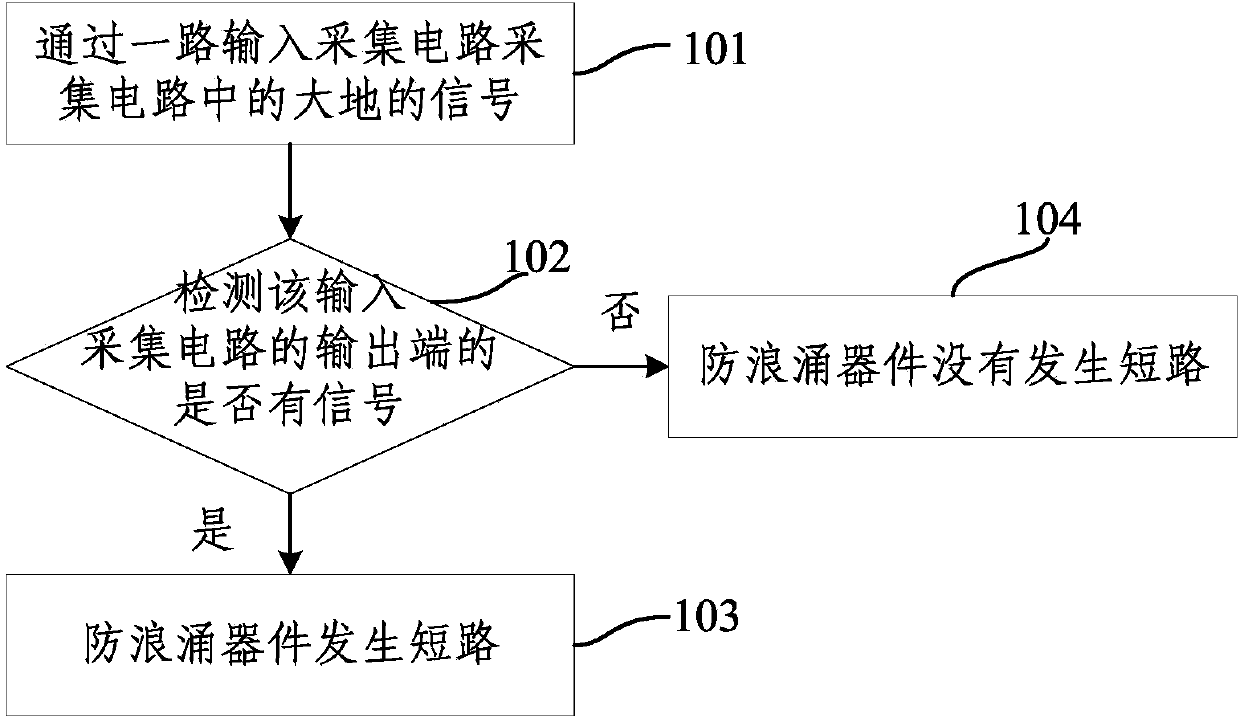
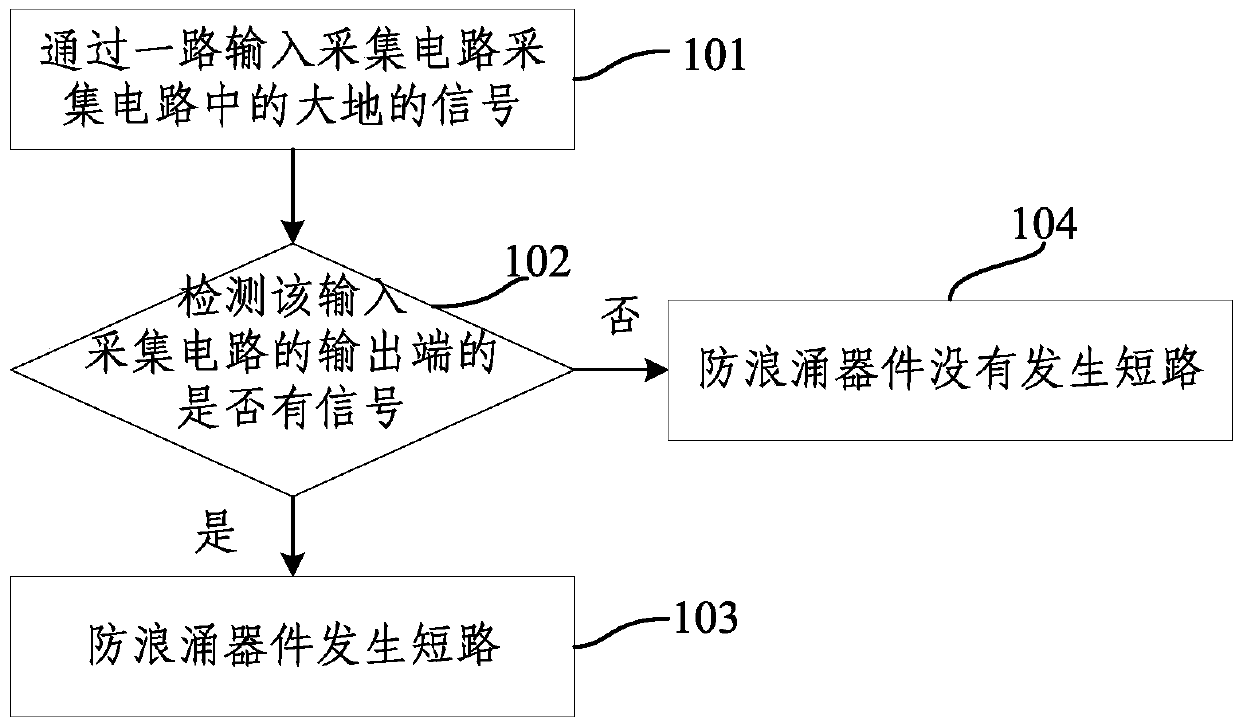
Method for detecting fault of anti-surge device in train automatic control system
ActiveCN103743990ADoes not affect availabilityNo external mixingElectrical testingAutomatic train controlAutomatic control
The invention provides a method for detecting faults of an anti-surge device in a train automatic control system. The method comprises that an input acquiring circuit acquires a ground signal in a circuit and detects whether a signal is outputted by the output end of the input acquiring circuit; if a signal is outputted, it is determined that short circuit occurs to the anti-surge device; and that if no signal is outputted, it is determined that short circuit does not occur to the anti-surge device. According to the method for detecting faults of an anti-surge device in a train automatic control system, fault detection on the anti-surge device using the input acquiring circuit in the train automatic control system does not need additional components and parts, does not influence the availability of the train automatic control system, and does not generate external wire tangle.
Owner:TRAFFIC CONTROL TECH CO LTD
Distributed parallel high-speed read-write system and method based on IPFS
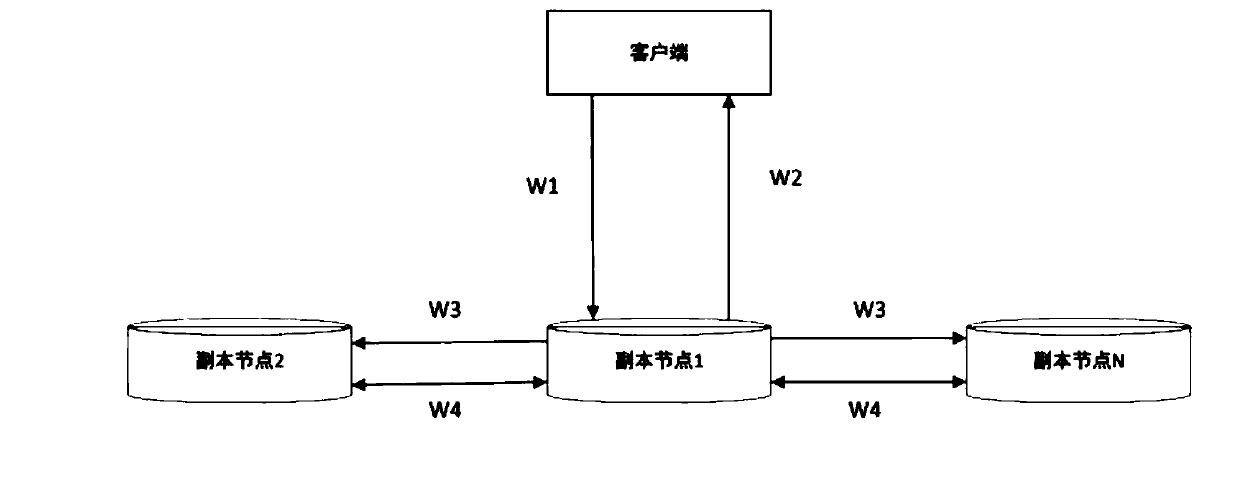
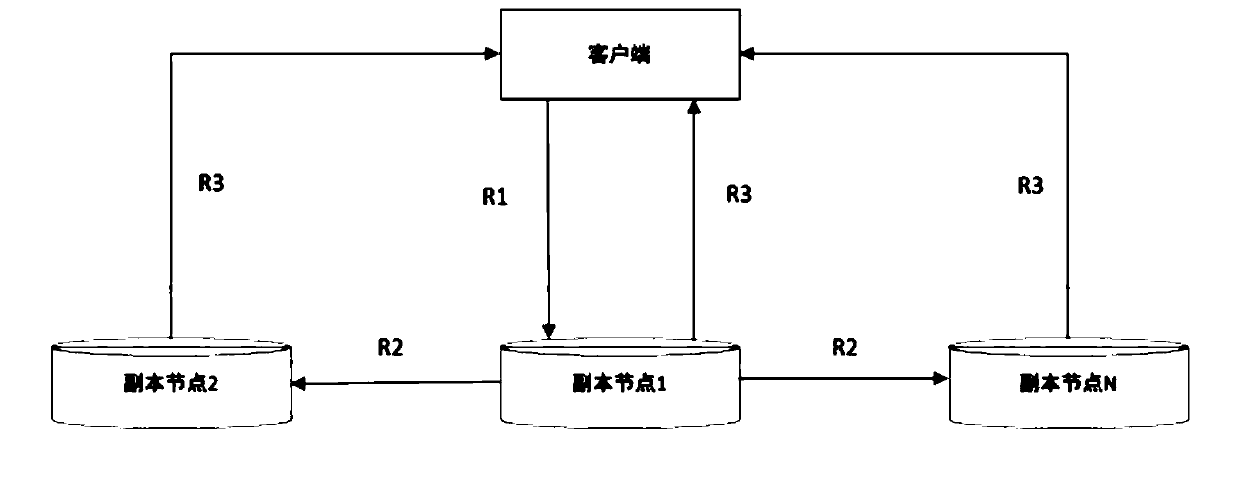
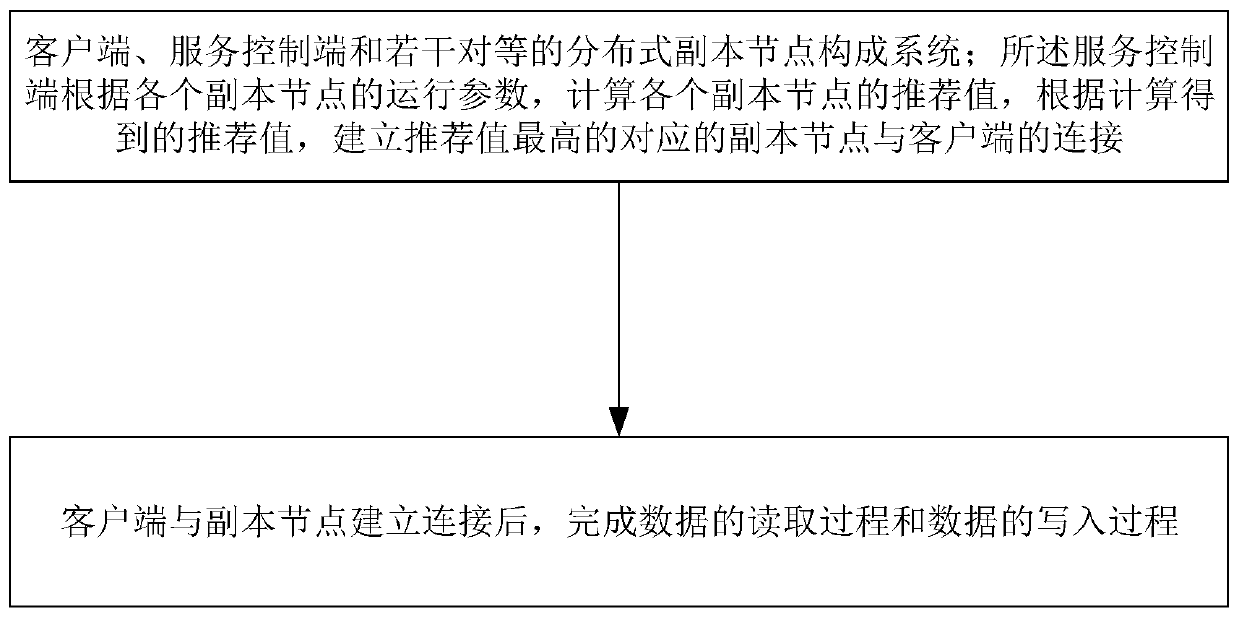
PendingCN111274222ALoad balancingDoes not affect availabilityFile access structuresSpecial data processing applicationsService controlParallel computing
The invention belongs to the technical field of distributed storage, and particularly relates to a distributed parallel high-speed read-write system and method based on an IPFS, and the system comprises a client, a service control end, and a plurality of peer-to-peer distributed replica nodes. The service control terminal calculates a recommendation value of each copy node according to the operation parameter of each copy node, and establishes connection between the corresponding copy node with the highest recommendation value and the client according to the calculated recommendation value; completing a data reading process and a data writing process after the connection between the client and the copy node is established; the system has the advantages of being high in intelligent degree,high in efficiency and high in safety.
Owner:廊坊嘉杨鸣科技有限公司
A method and system for protecting user privacy information against vertical attacks
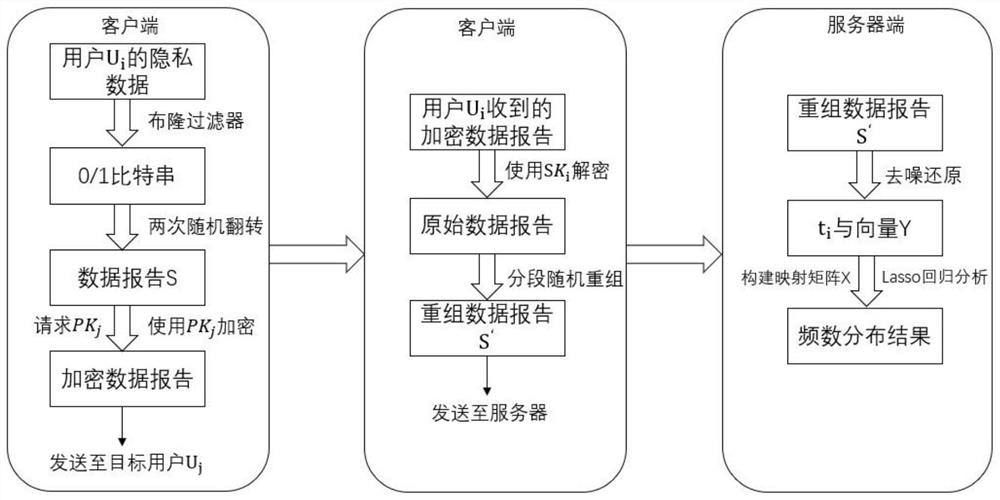
ActiveCN110866263BDoes not affect availabilitySolve the vertical attack problemDigital data protectionAttackPrivacy protection
The present invention provides a method and system for protecting user privacy information against vertical attacks, which is suitable for a network system composed of an information collection terminal and several information providing terminals. , after denoising, the information provided by each information provider is obtained. The present invention realizes that when the overall data frequency information is counted, the collector cannot directly obtain the user's private information through the data report sent by a single information provider, and cannot obtain the user's private information by repeatedly collecting the data report of a certain user by using a vertical attack method User privacy; after all data reports must be aggregated, user privacy information must be counted through methods such as denoising and regression analysis, so as to take into account privacy protection and data availability, and improve privacy protection while increasing data availability.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Method and apparatus for creating redundancy array in disc RAID
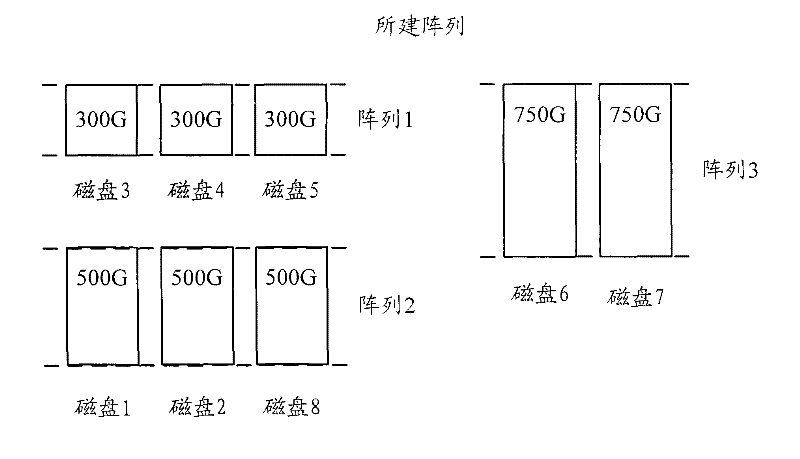
ActiveCN101620518BImprove effective space utilizationDoes not affect availabilityInput/output to record carriersRAIDMagnetic disks
Owner:NEW H3C TECH CO LTD
Data distributed storage system and method
InactiveCN104123300BImplement real-time transaction processingEnsure safetySpecial data processing applicationsNode clusteringData node
The invention discloses a data distributed storage system and method. The system comprises a node cluster module, a data import module and a storage module. The node cluster module is used for connecting data nodes in a cluster with corresponding management nodes; the data import module is used for scanning input data according to data blocks with sizes set and loading the input data into a memory, data in the memory are grouped according to characteristic values of the data, and the grouped data are sent to the corresponding data nodes; the storage module is used for storing data fragmentations in the memory after the data nodes receive file fragmentations, and the data nodes output logs to a hard disk; whether the data in the memory exceed a set threshold value or not is judged, if the data in the memory exceed the set threshold value, the data are reorganized and compressed and then written into the hard disk, and corresponding log files restored through user memory data are deleted. According to the system and method, the cluster based on memory computing power can be accelerated; real-time loading and processing capacity for large-scale data can be improved, and response time of the system is shortened.
Owner:SHANGHAI PEOPLEYUN INFORMATION TECH CO LTD
A method and system for quickly recovering from a virtual machine fault
ActiveCN110018881BGuaranteed uptimeShort downtimeSoftware simulation/interpretation/emulationRedundant operation error correctionTerm memoryAddress mapping
Owner:XI AN JIAOTONG UNIV +1
Database service providing method and system
ActiveCN106897288BGuaranteed not to loseImprove performanceDatabase updatingError preventionNetwork connectionDatabase server
A service providing method and system for a database. The method comprises: when a master database server (301) receives a service providing request of a client, changing data in a database according to the service providing request, writing change information about the database into a first transaction log, and sending the first transaction log to a slave database server (302); and when a network connection between the master database server (301) and the slave database server (302) is disconnected or times out, or when the number of accumulated transaction logs, failing to be successfully sent, in the master database server (301) exceeds a pre-set value, or when the sending time of the first transaction log exceeds a pre-set time, the master database server (301) transmitting the first transaction log or information about an update object corresponding to the first transaction log to a buffer region (303). It can be seen therefrom that when a standby database temporarily cannot receive a log, a master database sends the log to the buffer region (303) so as to prevent the log from being lost.
Owner:ALIBABA GRP HLDG LTD
A multi-tenant-oriented cloud network system
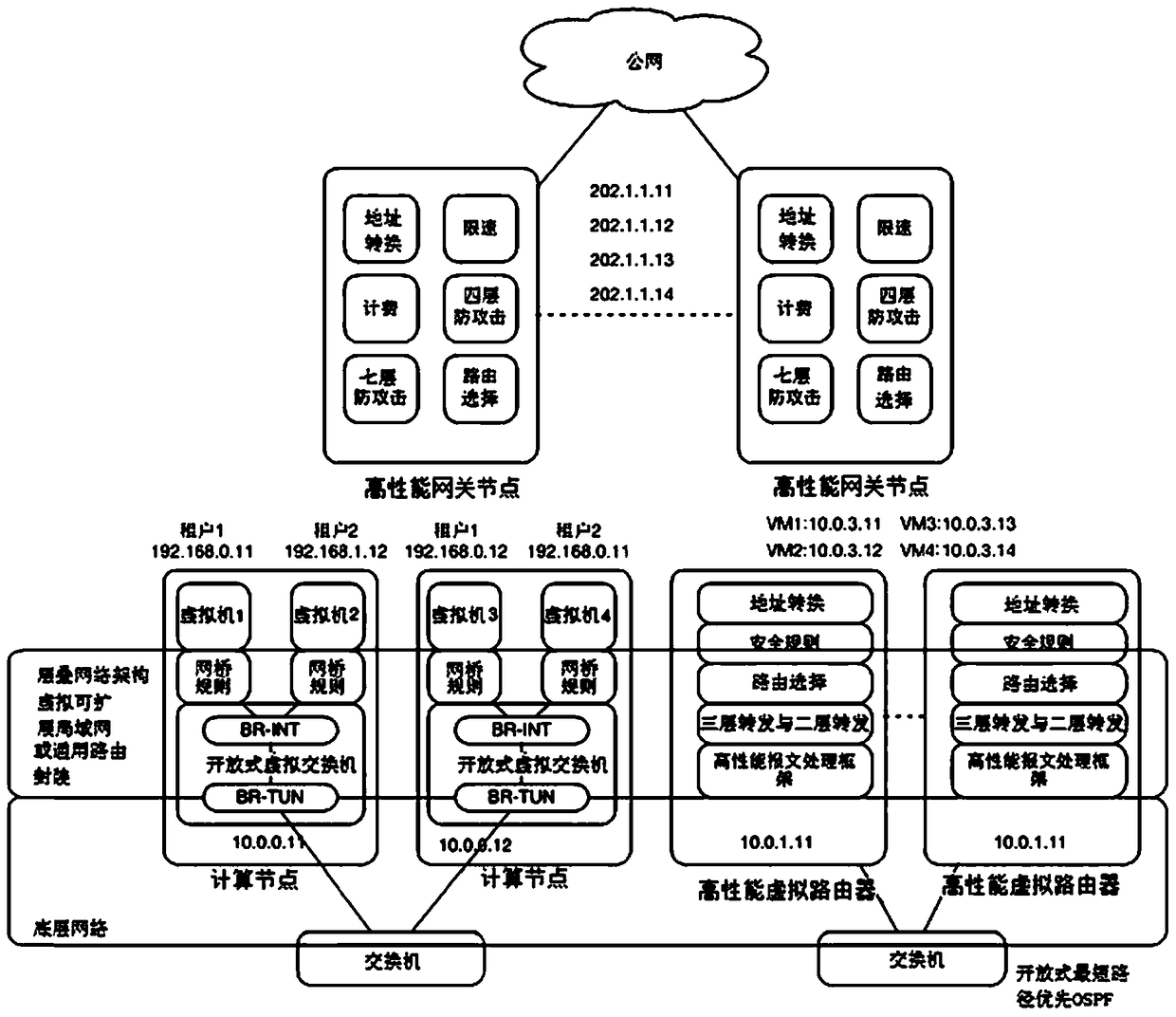
ActiveCN105391771BDoes not affect availabilityImprove performanceData switching networksIp addressPrivate network
The invention discloses a multi-tenant-oriented cloud network system. The cloud network system includes: a computing node, a virtual router cluster, and a cloud gateway. The virtual machine included in the computing node exchanges messages with the public server in the private network through the virtual router cluster; and, the virtual machine communicates with the virtual router cluster and The cloud gateway realizes message exchange with the public network; wherein, the virtual router cluster includes at least two virtual routers, and each of the virtual routers issues the same IP address to the private network switch; the cloud gateway includes at least two gateway nodes, each The gateway node publishes an equivalent default route to the private network switch, and each of the gateway nodes publishes the same floating IP address to the public network router or public network switch, so as to realize the cluster expansion of the cloud network system, and avoid the problem caused by a single node Failures affect the availability of the entire network, improving the network's attack defense capabilities.
Owner:北京云启志新科技股份有限公司
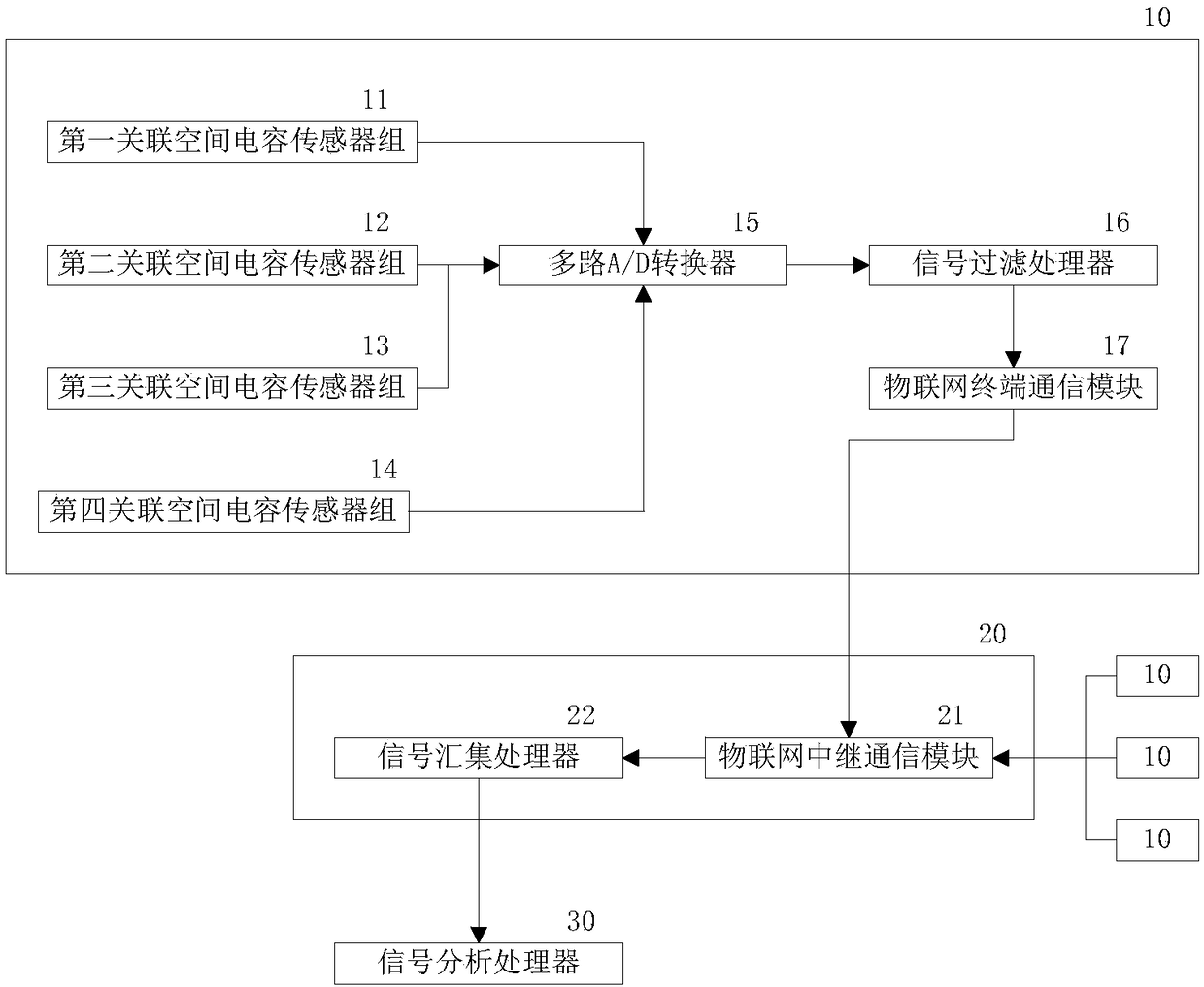
A Perimeter Vibration Alarm System Based on Internet of Things
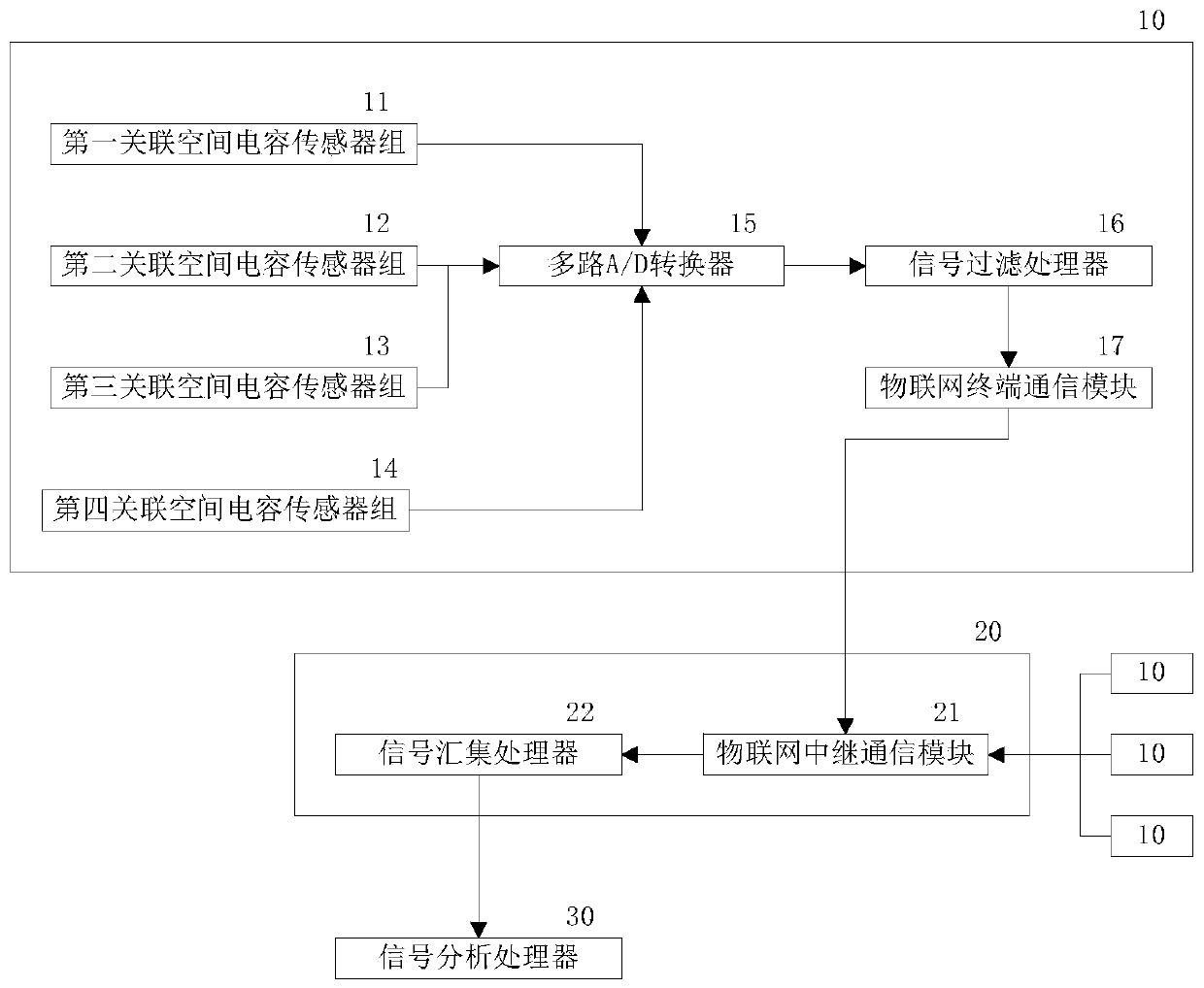
ActiveCN108833596BLess distracting factorsReduce consumptionRadio transmissionBurglar alarmVibration measurementSystem maintenance
The invention provides an IoT-based perimeter vibration alarm system to solve the low overall processing efficiency of a conventional alarm system due to the sensor structure in the conventional alarmsystem. The IoT-based perimeter vibration alarm system includes a vibration sensor for forming vibration measurement signals in associated directions in an associated enclosed space; and a data repeater for providing a re-routable data transmission link for the vibration measurement signals. The enclosed space reduces the interference factors of an acquisition environment. Forming a plurality ofassociated acquisition directions for vibration states in the enclosed space can comprehensively acquire the vibration states in all directions, so that the acquired signals of respective associated acquisition directions include the associated vibration information in the same vibration direction that can be quantified, thereby providing additional associated vibration information for subsequentsignal processing, and reducing the computational resource consumption of association analysis between vibration signals. Further, by the re-routable data transmission links, the increase or decreaseof the sensors does not affect the availability of the transmission link, thereby reducing system maintenance cost.
Owner:北京吉宝通科技发展有限公司
Face feature collaborative protection safety certification system under public network
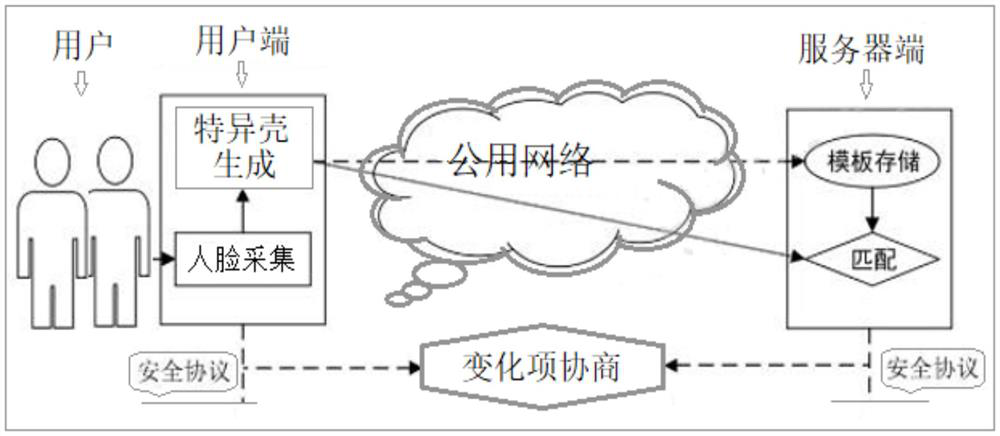
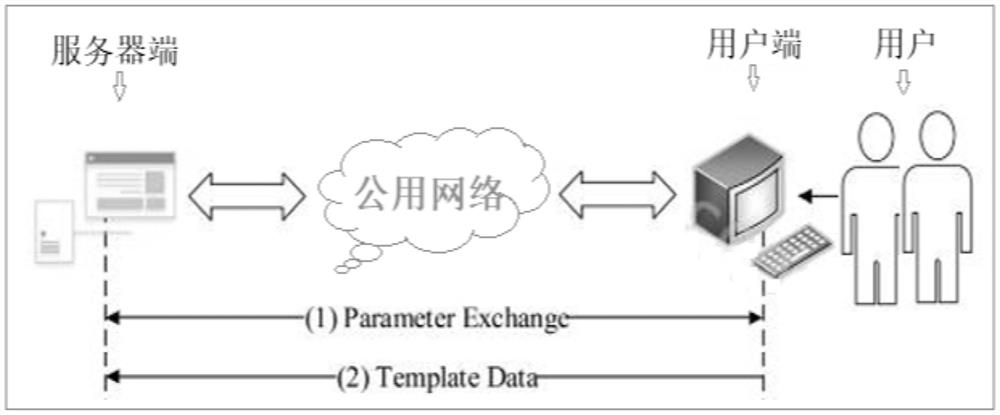
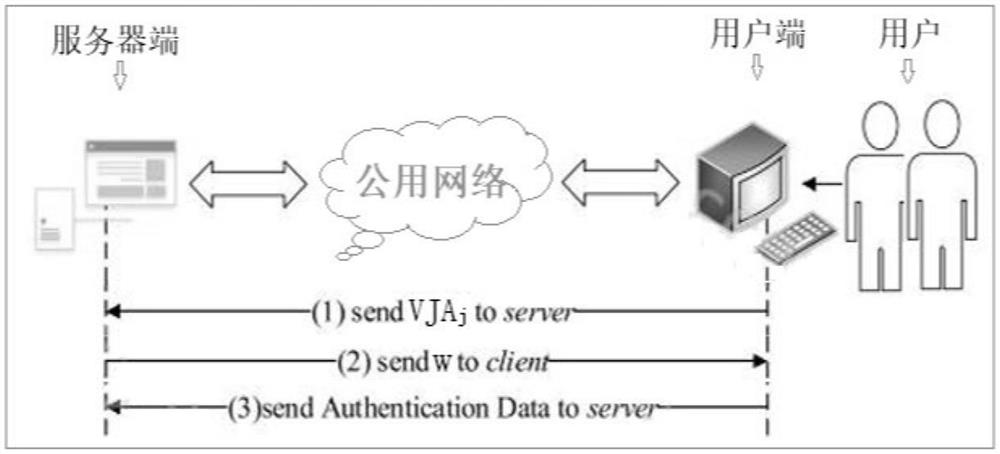
PendingCN114036485ASecurity fully consideredMeet security needsDigital data protectionDigital data authenticationEngineeringSecurity authentication
A security authentication model based on biological feature protection in a public network environment is constructed from two aspects of a security authentication protocol of face feature collaborative protection and a security authentication system of face feature collaborative protection, and the feature of biological feature identity authentication and an authentication interaction process in the public network environment are combined to obtain a task that a server undertakes face feature storage and feature matching completion, so cross-terminal identity authentication based on biological features is realized. A security authentication architecture based on face feature collaborative protection and suitable for two parties to participate in a cross-terminal application scene is provided, a feature collaborative protection algorithm based on a transformation technology is abstracted, the security of a feature specific shell and authentication data is concerned, a security guarantee on a face identity authentication interaction process is provided, the interaction process from a bottom layer processing module to protocol authentication is realized, the security requirement of biological feature identity authentication in a public network environment is met, and an authentication protocol with unified availability and security is constructed.
Owner:郭灵玉
A location anonymity method across road networks while maintaining statistical characteristics
ActiveCN107682817BAvoid gettingStatistical characteristics do not changeLocation information based serviceSecurity arrangementRoad networksPrivacy protection
The invention discloses a cross-road-network location anonymization method keeping statistical characteristics unchanged. First, road networks are extracted according to the road distribution in a target area, and road network areas are obtained through partitioning; then, a location anonymization candidate set meeting the protection requirements is constructed according to an actually needed scope of protection and the center-of-mass location of each road network area; and finally, a location anonymized road network area is determined according to the location point number difference, center-of-mass point distance and other parameters between a to-be-protected road network area and the road network areas in the candidate set, and cross-road-network location anonymization is carried out through location exchange. Road network areas are obtained through partitioning using road networks, and location anonymization is carried out between different road network areas, which can prevent attackers from acquiring user privacy by making use of the background knowledge of the location-territory relationship. In the invention, location anonymization is carried out through location exchange,which can keep the statistical characteristics of the overall data unchanged and does not affect the availability of data after privacy protection.
Owner:XI AN JIAOTONG UNIV
Method and device for message processing
ActiveCN102868594BAchieve isolationAvoid mutual interferenceData switching networksManagement unitPassword
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
IoT-based perimeter vibration alarm system
ActiveCN108833596ALess distracting factorsReduce consumptionRadio transmissionBurglar alarmVibration measurementSystem maintenance
The invention provides an IoT-based perimeter vibration alarm system to solve the low overall processing efficiency of a conventional alarm system due to the sensor structure in the conventional alarmsystem. The IoT-based perimeter vibration alarm system includes a vibration sensor for forming vibration measurement signals in associated directions in an associated enclosed space; and a data repeater for providing a re-routable data transmission link for the vibration measurement signals. The enclosed space reduces the interference factors of an acquisition environment. Forming a plurality ofassociated acquisition directions for vibration states in the enclosed space can comprehensively acquire the vibration states in all directions, so that the acquired signals of respective associated acquisition directions include the associated vibration information in the same vibration direction that can be quantified, thereby providing additional associated vibration information for subsequentsignal processing, and reducing the computational resource consumption of association analysis between vibration signals. Further, by the re-routable data transmission links, the increase or decreaseof the sensors does not affect the availability of the transmission link, thereby reducing system maintenance cost.
Owner:北京吉宝通科技发展有限公司
Fault detection method for anti-surge device in a train automatic control system
ActiveCN103743990BDoes not affect availabilityNo external mixingElectrical testingAutomatic train controlAutomatic control
Owner:TRAFFIC CONTROL TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com