Method for generating master node for preventing injection of false data into Lin bus
A technology of false data and generation method, which is applied in the direction of bus network, data exchange network, data exchange through path configuration, etc., and can solve problems such as injection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
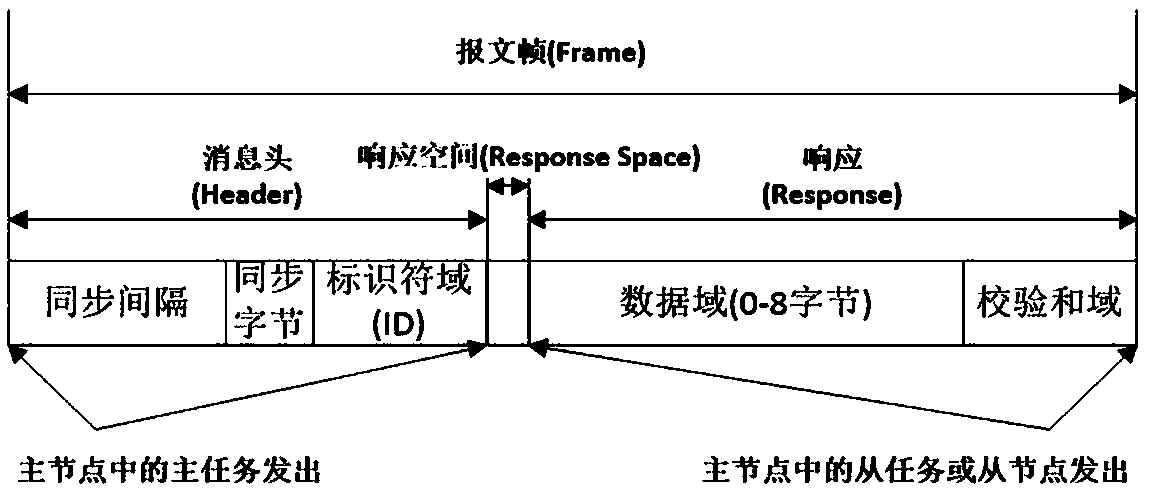
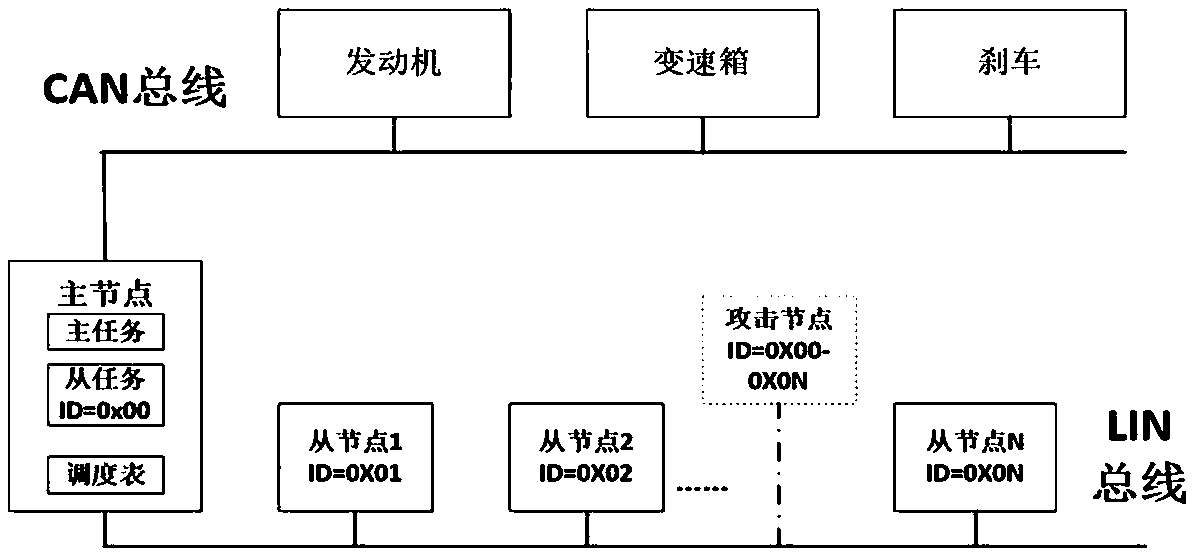
[0040] 1. Modify the software of the existing LIN master node so that it has the function of monitoring the message header and response data on the bus;
[0041] 2. In a safe environment, the master node obtains the Max of the data generated by each slave node i 、Min i and D i , where 2≤i≤15, P i The initial value is 0;
[0042] 3. For the attack node pretending to be a slave node to send a false message response, the slave task in the master node obtains the value V of each slave node i according to the schedule cycle i , and the Max of node i i 、Min i ,P i and D i Compare and replace P i , the alarm condition is: V i >Max i or V i i or |V i -P i |>D i ;
[0043] 4. The master task in the master node regularly sends the header of the data sent by itself to the bus, and the slave task sends data and monitors the bus. If a data conflict is detected, there must be false data injection (all normal slave nodes will not respond data), an alarm is issued.
[0044] 5...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com