Dynamic switching method for VoIP audio-video encryption keys
An encryption key, audio and video technology, applied in the field of network communication, can solve problems such as interruption and low security of the scheme, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
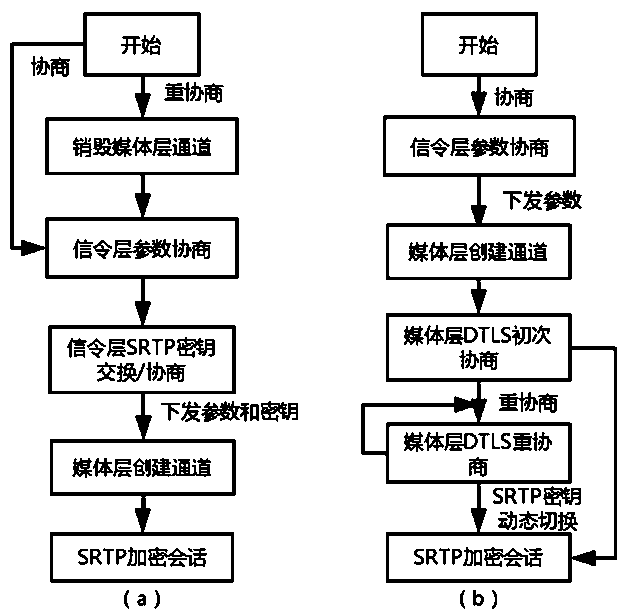
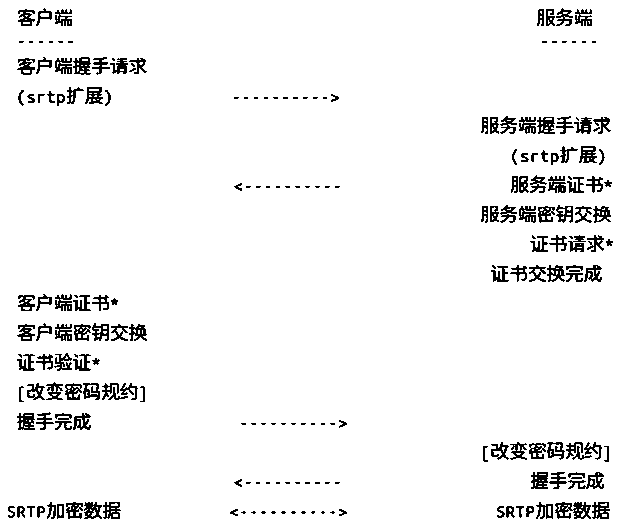
[0024] The basic principles of the present invention are as follows: This solution completes the dynamic switching of audio and video encryption keys based on the DTLS protocol at the media layer, uses the security of the DLTS protocol to ensure that the encryption key is not easily leaked, and the session is not interrupted when the key is dynamically switched. The overall structure of this solution consists of three parts, which are initial negotiation, SRTP encrypted transmission and re-negotiation. The main negotiation process is completed at the media transport layer and has little correlation with the signaling layer.
[0025] In order to make the purpose, technical solutions and advantages of the present invention clearer, examples are given below. It should be understood that the specific embodiments described here are only used to explain the present invention, and are not intended to limit the present invention.
[0026] figure 1 It is a schematic diagram of the comm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com