Identity authentication method and device
An identity authentication and identity technology, applied in the field of identity authentication methods and devices, can solve problems such as inconvenience of use, and achieve the effect of alleviating the inconvenience of use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
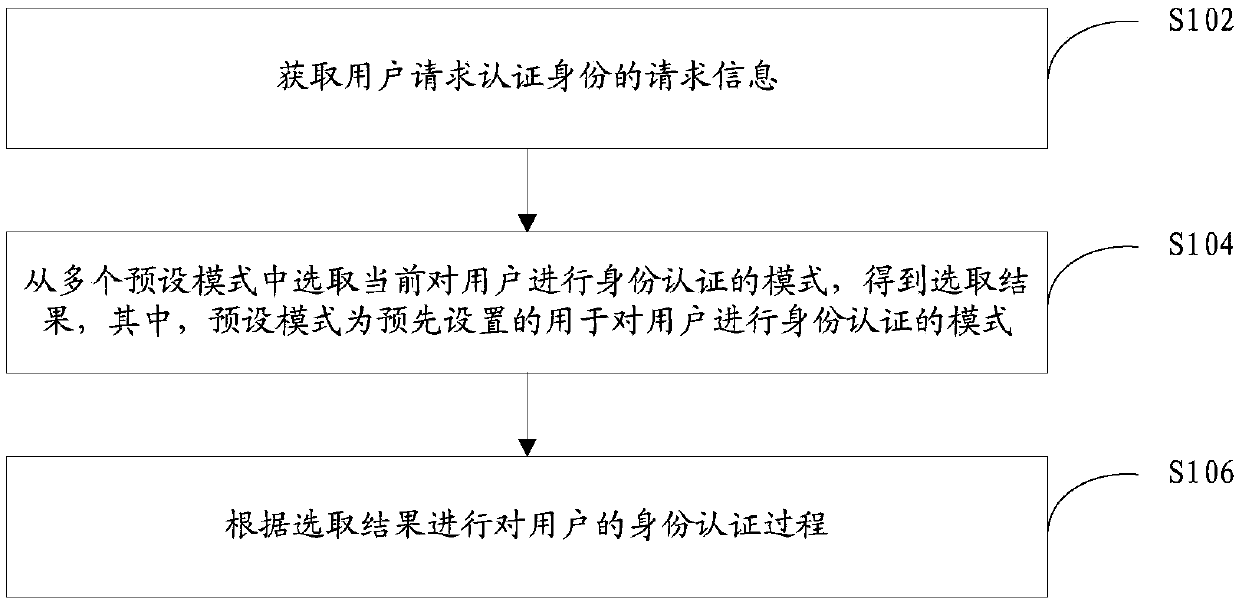
[0050] An identity authentication method provided by an embodiment of the present invention, such as figure 1 shown, including:
[0051] Step S102, obtaining the request information of the user requesting the authentication identity;
[0052]Step S104, selecting the current mode for user identity authentication from a plurality of preset modes to obtain a selection result, wherein the preset mode is a preset mode for user identity authentication;
[0053] Step S106, according to the selection result, the user's identity authentication process is performed.
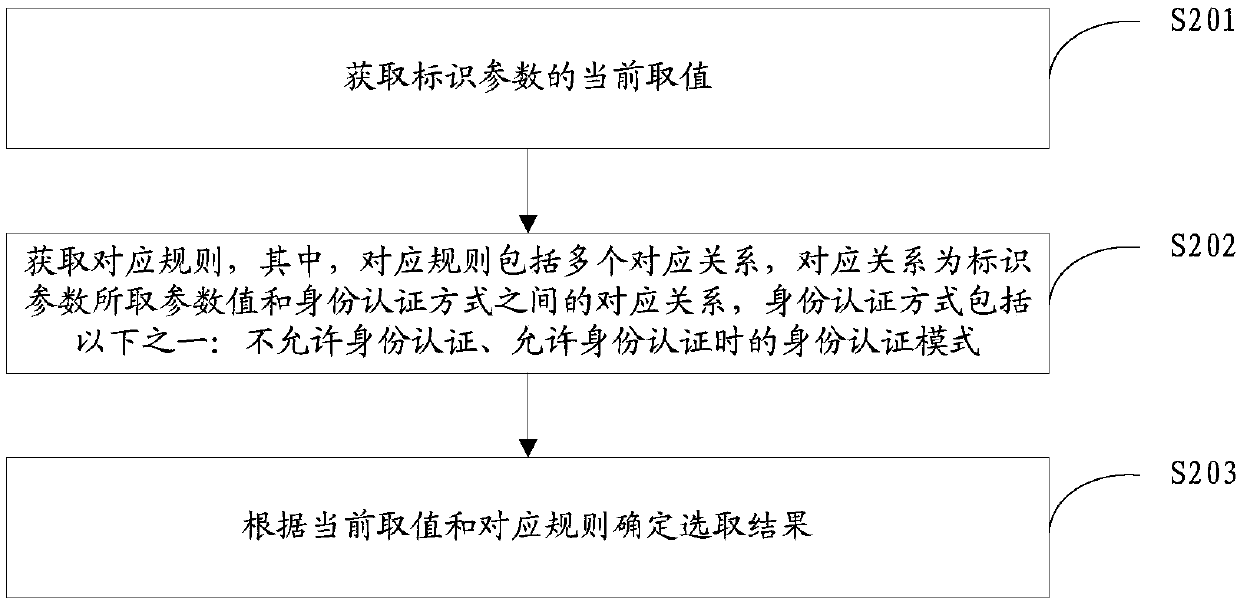
[0054] Specifically, the identity authentication method is applied to a device for authenticating a user, so as to realize the identity authentication for the user. It should be emphasized that the request information is the information that the user requests to authenticate the identity, and obtaining the request information can be obtained from the request information sent by the user using the client, or from some req...
Embodiment 2
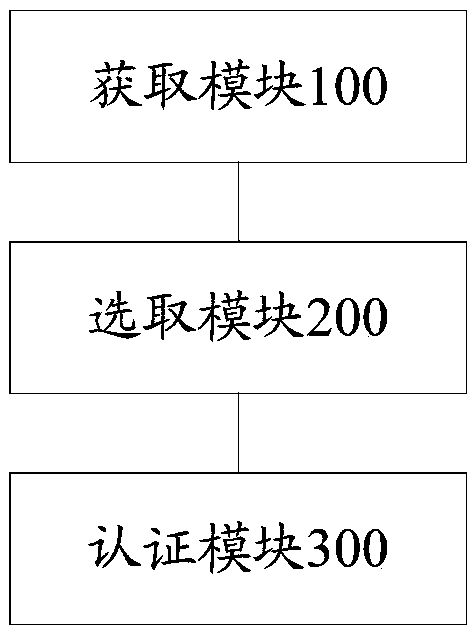
[0093] An identity authentication device provided by an embodiment of the present invention, such as image 3 shown, including:
[0094] Obtaining module 100, for obtaining the request information of user request authentication identity;
[0095] The selection module 200 is used to select a mode that currently authenticates the user from a plurality of preset modes to obtain a selection result, wherein the preset mode is a preset mode for authenticating the user;
[0096] The authentication module 300 is configured to perform an identity authentication process for the user according to the selection result.
[0097] In the embodiment of the present invention, the obtaining module 100 obtains the request information of the user requesting the authentication identity; the selecting module 200 selects the current mode for user identity authentication from a plurality of preset modes, and obtains the selection result, wherein the preset mode is the preset mode The set mode for a...
Embodiment 3
[0125] An embodiment of the present invention provides a computer-readable medium having a non-volatile program code executable by a processor, and the program code causes the processor to execute the identity authentication method of Embodiment 1.
[0126] Specifically, the storage medium includes: a USB flash drive, a mobile hard disk, a read-only memory (ROM, Read-Only Memory), a random access memory (RAM, Random Access Memory), a magnetic disk or an optical disk, and other media that can store program codes. .
[0127] In the embodiment of the present invention, the program code causes the processor to execute the identity authentication method of the first embodiment, that is, to obtain the request information of the user requesting the authentication identity; to select the current mode of identity authentication for the user from a plurality of preset modes, and obtain the selected As a result, the preset mode is a preset mode for authenticating the user; the identity a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com