Video conference terminal registration method, terminal and gatekeeper
A video conference and terminal technology, applied in the field of security authentication, can solve the problem of lack of certain guarantee of video conference security, achieve the effect of simple and fast judgment process and improve registration efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
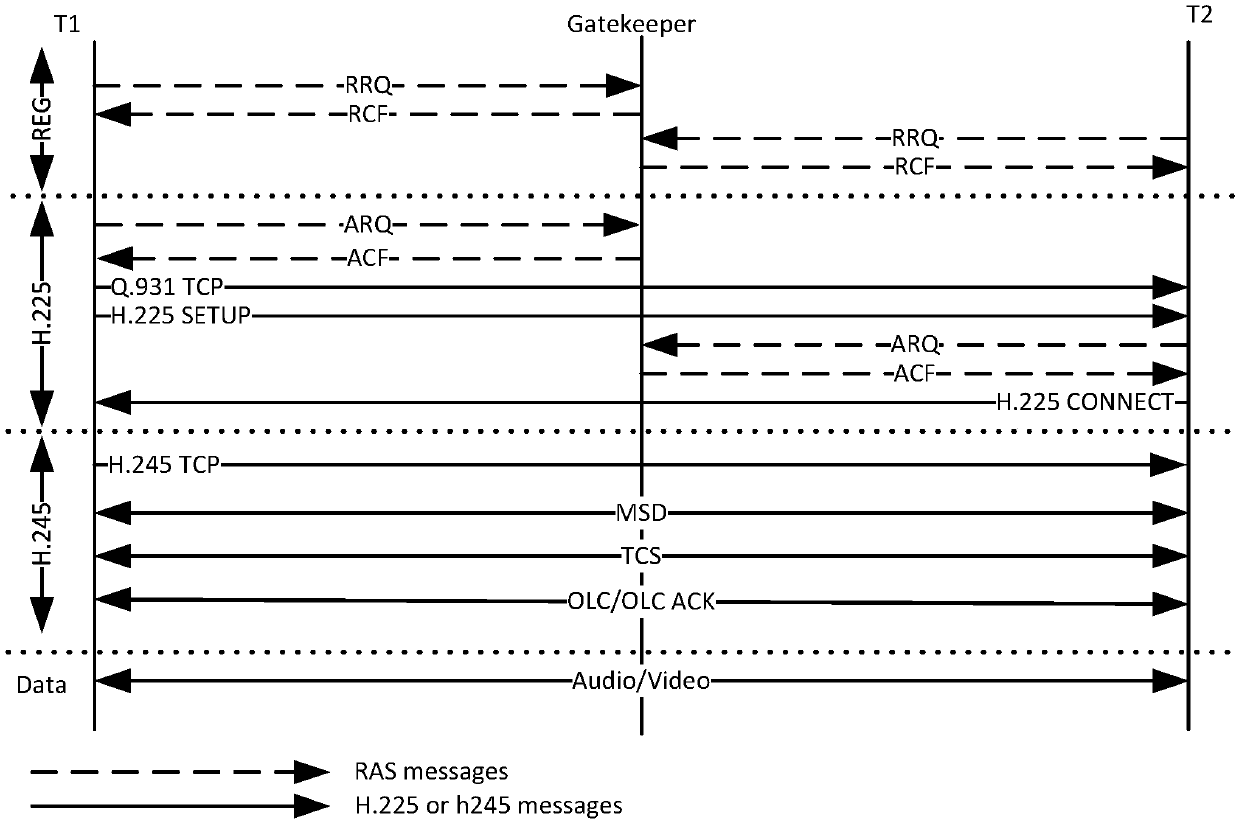
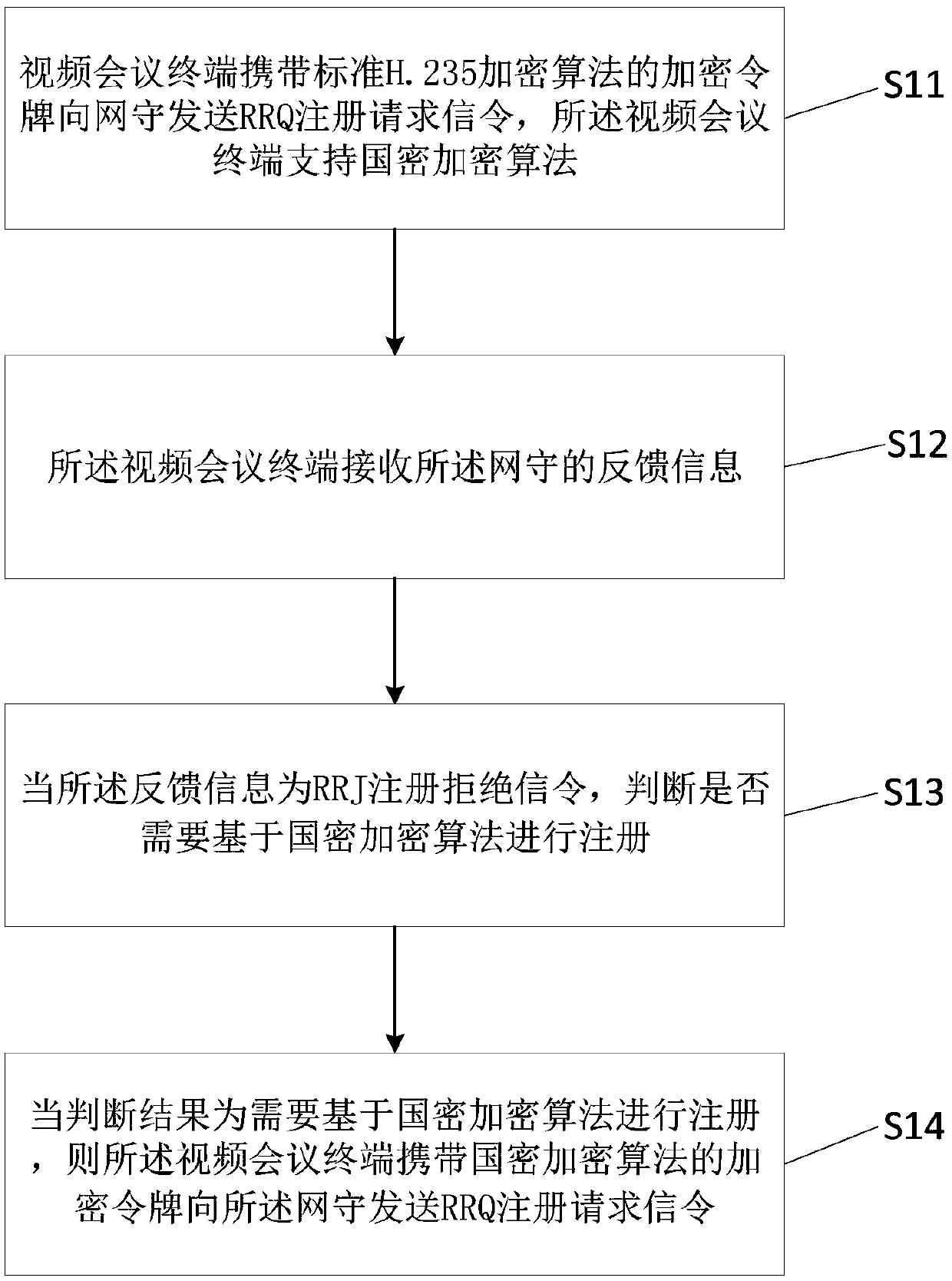
[0070] This embodiment provides a video conferencing terminal registration method, the execution subject is figure 1 Any video conferencing terminal in T1 or T2. Such as figure 2 shown, including the following steps:
[0071] Step S11 , the video conferencing terminal carries an encryption token of the standard H.235 encryption algorithm and sends RRQ registration request signaling to the gatekeeper, and the video conferencing terminal supports the national secret encryption algorithm.
[0072] Step S12, the video conference terminal receives the feedback information from the gatekeeper. Wherein, the feedback information of the gatekeeper is generally RCF registration confirmation signaling or RRJ registration rejection signaling.
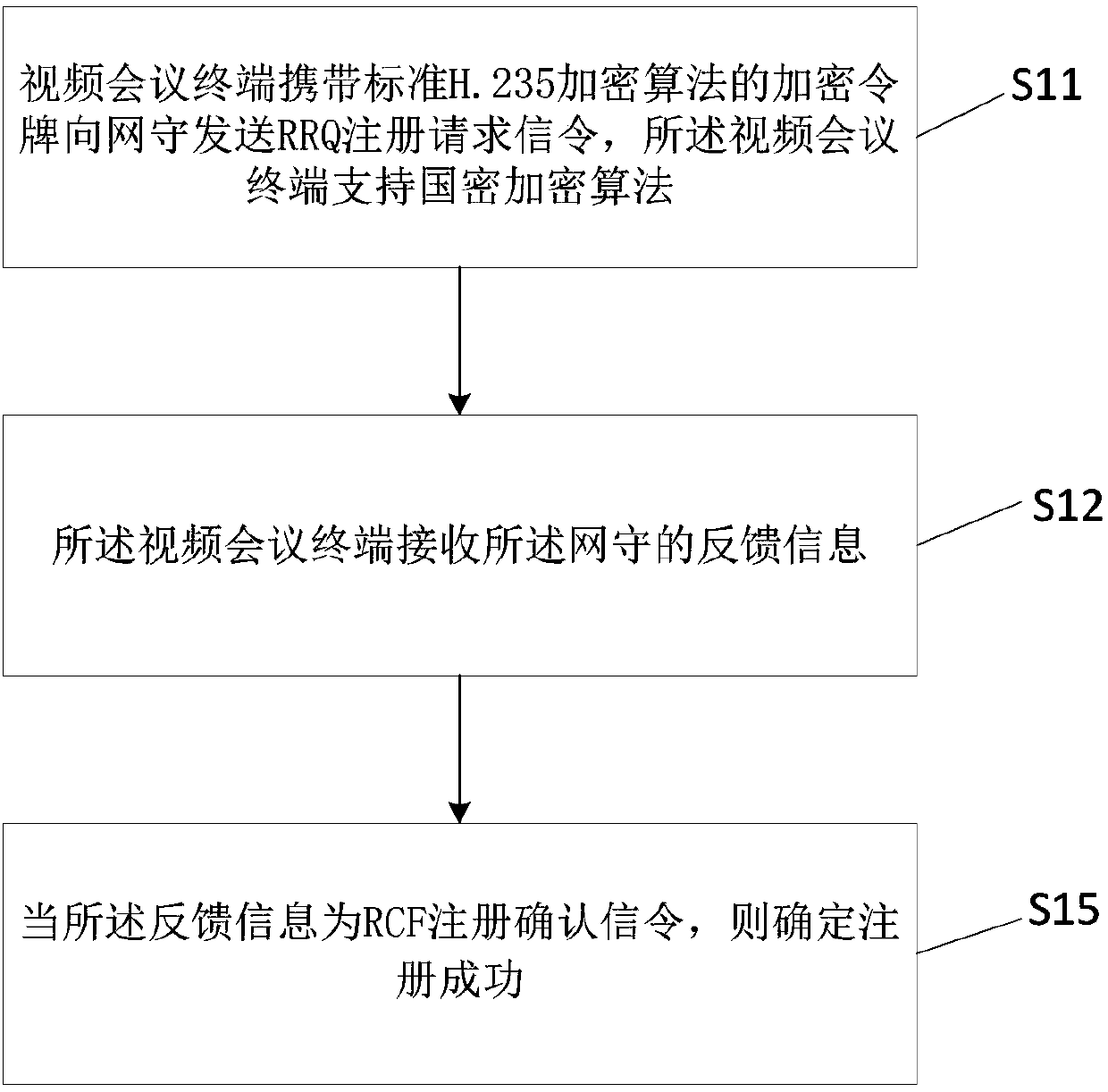
[0073] Step S13 , when the feedback information is the RRJ registration rejection signaling, it is judged whether registration based on the national secret encryption algorithm is required. Otherwise, if image 3 As shown, step S15 is execute...
Embodiment 2
[0107] This embodiment provides a video conferencing terminal registration method, the execution subject is figure 1 The target gatekeeper in . Such as Figure 8 shown, including the following steps:
[0108] Step S21, receiving the RRQ registration request signaling sent by the video conference terminal carrying the encryption token of the national secret encryption algorithm.
[0109]Step S22. Obtain the second ciphertext by using the same national secret encryption algorithm as that of the video conferencing terminal.
[0110] Wherein, the method for obtaining the second ciphertext is the same as the method for obtaining the first ciphertext by the video conferencing terminal in Embodiment 1. The only difference is that information such as passwords and E.164 aliases on the gatekeeper side are obtained from the server side by the gatekeeper side. obtained from the database.
[0111] Step S23, when the second ciphertext is the same as the first ciphertext in the encrypte...
Embodiment 3
[0120] This embodiment provides a specific implementation manner of the method for registering a video conference terminal in Embodiment 1 above. Include the following steps:
[0121] 1) The video conference terminal carries an encryption token of the standard H.235 encryption algorithm to initiate RRQ registration request signaling to the gatekeeper.
[0122] 2) The video conferencing terminal receives the feedback information from the gatekeeper. When the feedback information is the RCF registration confirmation signaling, the registration is successful with the authentication mode of the standard H.235 encryption algorithm; when the feedback information is the RRJ registration rejection signaling, then perform step 3 ).
[0123] 3) Determine whether the reason for the registration refusal is "genericDataReason", and determine whether the specific reason for the refusal of the logo is the need for national secret SM3 encryption.
[0124] 4) When the judgment result is that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com