Automatic information leakage monitoring method and system based on internet big data
A technology of information leakage and automatic monitoring, applied in the field of information security, can solve the problems of low threshold for information outflow, threat of information confidentiality control, etc., and achieve the effect of avoiding information leakage incidents
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
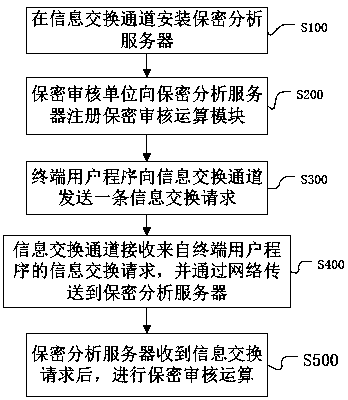
[0032] Such as figure 1 As shown, the automatic monitoring method for information leakage based on Internet big data includes the following steps:
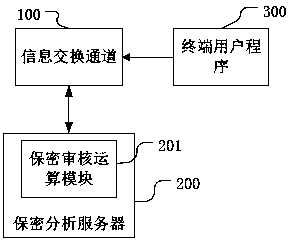
[0033] S100. Install a security analysis server on the information exchange channel to provide basic services for information security review;
[0034] The security analysis server of the present invention has a network connection with the information exchange channel, and the ownership of the security analysis server belongs to the information exchange channel, and the information exchange channel mainly refers to online information such as various portal websites, mail services, instant messaging services, and blog services. outgoing channels.
[0035] Through the design of separating the information exchange channel and the confidential analysis server, the changes to the existing website are minor, and commercial development and application can be carried out, which improves the enthusiasm of the online information distributi...
Embodiment 2
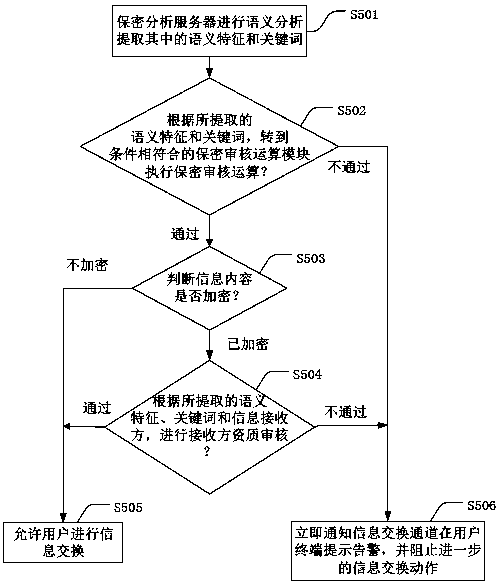
[0051] In a more preferred embodiment, S501 semantic analysis also includes text extraction and scene recognition for images, voices and videos in the information exchange request, and then the process of extracting semantic features and keywords.
[0052] The confidential review of image, voice and video-related information needs to first extract the text, and then obtain the semantic features and keywords. The subsequent steps are like S502, S503, and S504.
Embodiment 3
[0054] In another embodiment, the registration process at S200 also includes a payment process by the confidential review unit to the information exchange channel.
[0055] By paying for the confidentiality review operation process, and making the operators of the information exchange channel provide socialized paid confidentiality review services for the registered confidentiality review operation modules according to the agreement, the cooperation between the information exchange channel and the commercial confidentiality review unit is achieved. Win-win and balance of interests.
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap