Cipher card key protection device, cipher card and encryption system
A technology of key protection and encryption system, applied in the field of password card and encryption system, password card key protection device, can solve the problems of important information leakage, user loss, key leakage and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
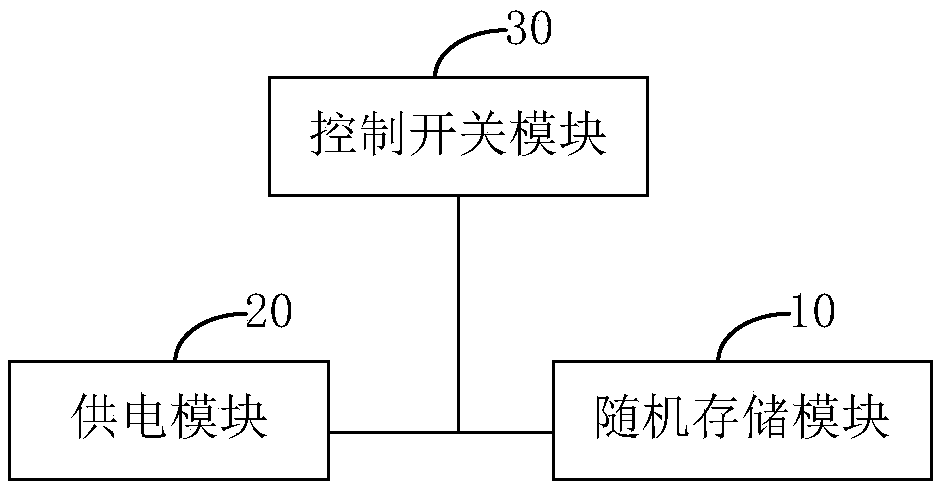
[0037] figure 1 It is a schematic diagram of a cipher card key protection device provided by an embodiment of the present invention.
[0038] Such as figure 1 As shown, the cipher card key protection device provided in this embodiment includes a random storage module 10, a power supply module 20 and a control switch module 30 arranged on the cipher card;
[0039] Random storage module 10, used for storing key;
[0040] The power supply module 20 is used to supply power to the random storage module;
[0041] The control switch module 30 is used to cut off the power supply module when the password card is triggered, so that the key in the random storage module is lost.
[0042] The key of the password card is stored in the random storage module, which is volatile when power off. When the password card is triggered (that is, pulled out), the control switch module cuts off the power supply of the random storage module, so that the key therein is lost. In this way, it is possib...
Embodiment 2
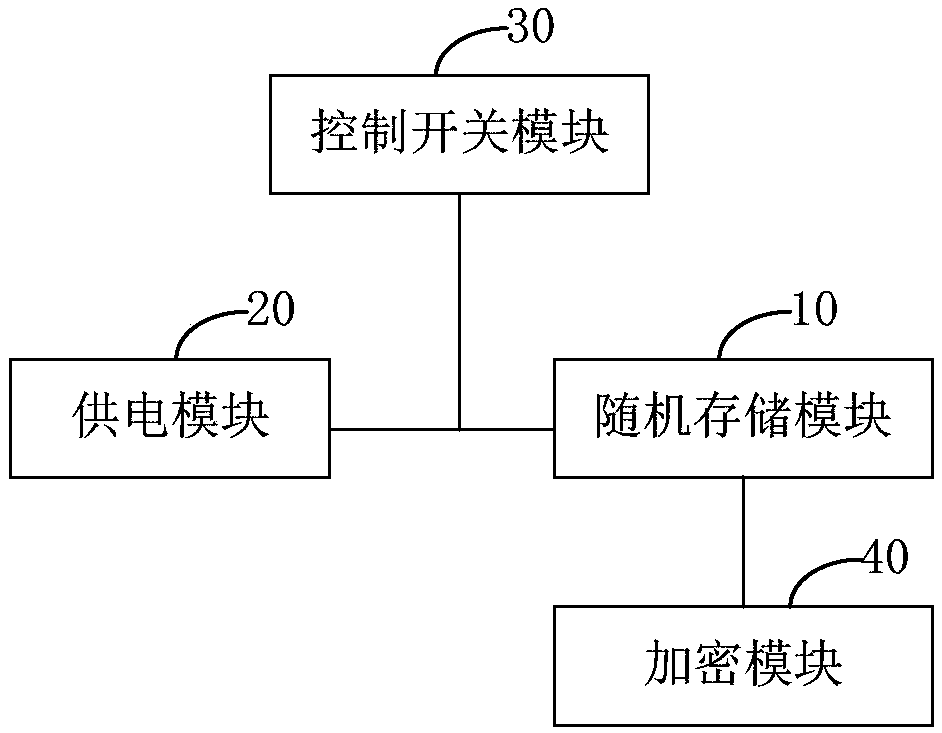
[0046] figure 2 A schematic diagram of a password card provided by an embodiment of the present invention.
[0047] Such as figure 2 As shown, the encryption card provided by this embodiment includes the encryption card key protection device of the above embodiment, and also includes an encryption module 40, which is used to obtain the key in the random storage module to encrypt data to obtain encrypted data.
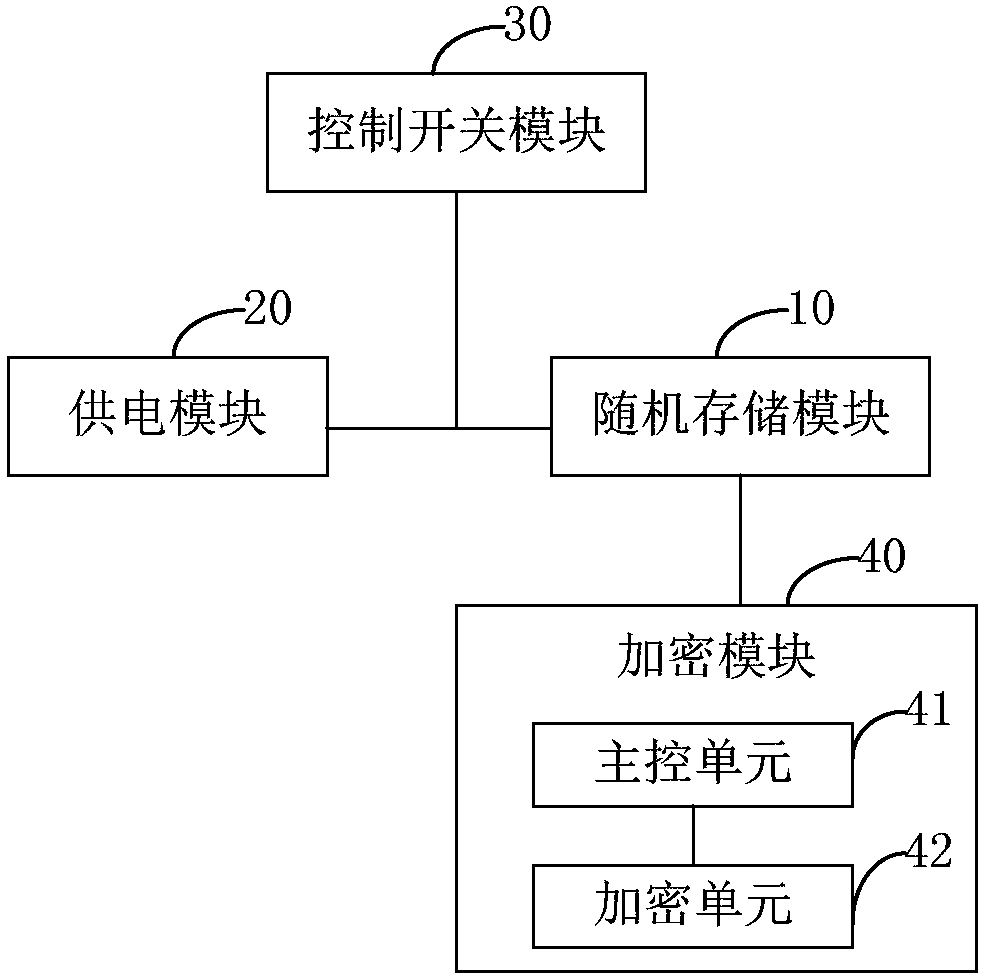
[0048] Such as image 3 As shown, the encryption module 40 includes a main control unit 41 and an encryption unit 42; the main control unit 41 can use a main control chip, and the encryption unit 42 can use an encryption chip;
[0049] The main control unit 41 is used to obtain the data to be encrypted and the key, and send the data to be encrypted and the key to the encryption unit;
[0050] The encryption unit 42 is configured to use a key to perform encryption operations on the data to be encrypted.
[0051] In addition, since the encryption key in the encrypti...
Embodiment 3
[0054] Figure 4 It is a schematic diagram of the encryption system provided by the embodiment of the present invention.
[0055] Such as Figure 4 As shown, the encryption system provided by this embodiment includes the encryption card 100 of the above embodiment, and also includes a data processing device 200, and the encryption card 100 is inserted into the data processing device 200;
[0056] The data processing device 200 is used to send the data to be encrypted to the password card;
[0057] The encryption card 100 is used for performing encryption operations on data to be encrypted using a key.
[0058] In this embodiment, after the encryption card 100 is inserted into the data processing device 200, the data processing device 200 provides power for the encryption card when it is turned on; when the data processing device 200 is in a closed state, the power supply module of the encryption card 100 is Provide power. Once the encryption card 100 is pulled out, its pow...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com