Extraction and identification technology of infringement picture content by deep learning and hash coding
A hash coding and deep learning technology, which is applied in character and pattern recognition, instruments, biological neural network models, etc., can solve the problems of automatic judgment, webpage content cannot be monitored, and detection business is passive, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
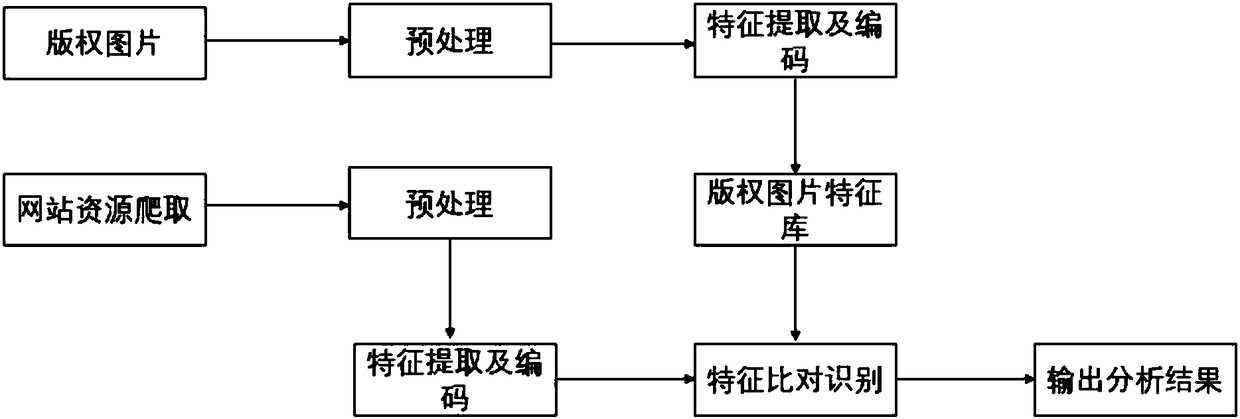
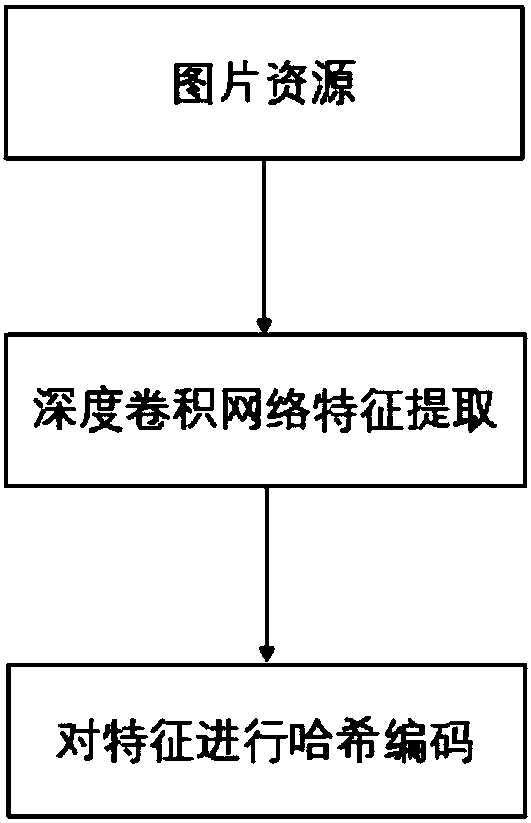
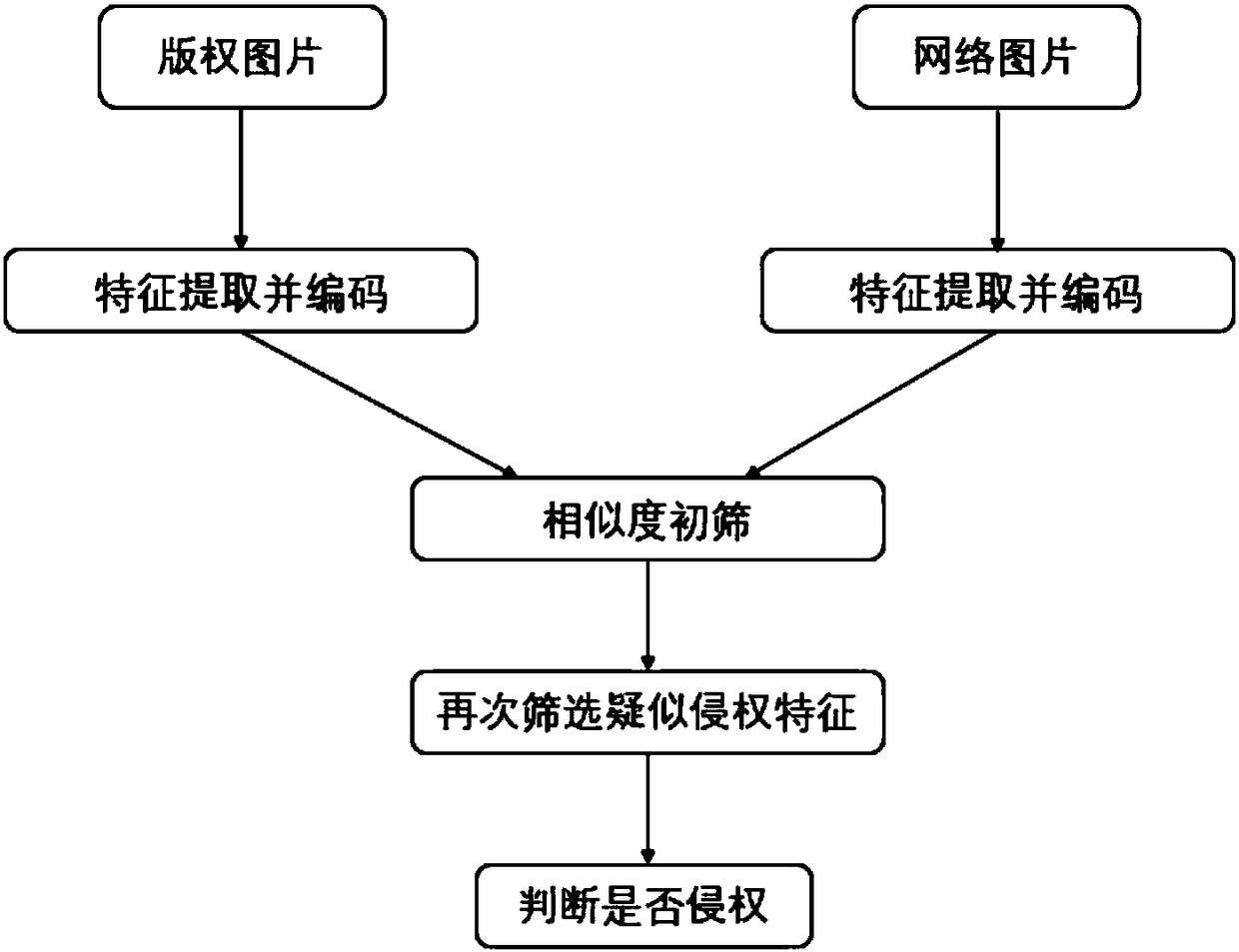
[0024] This example implements the identification technology of infringing content, which consists of three parts:
[0025] Step 1. Acquisition of image resources. Search for resources with a high matching degree on the website according to image keywords, search scope, and upload time of search resources. Before searching for content involving image copyright infringement, in the face of massive image information on the Internet, searching without purpose is like finding a needle in a haystack. Therefore, in order to achieve this goal, it is first necessary to filter the content of the retrieved pictures. The screening conditions include keywords related to the content of the pictures, resource retrieval (crawling) scope limitation, resource upload time and other key screening conditions. The main objects of resource retrieval are large and medium-sized portal websites. Crawler technology is used to crawl resources with high matching degree involving image copyright infringe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com