User authorization multi-party monitoring sharing method and system
A user authorization and sharing system technology, applied in the computer field, can solve the problems of inconvenient query monitoring, the query subject and the authorized subject have not been effectively verified, and the data transfer cannot be effectively monitored, etc., to achieve the effect of convenient supervision.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
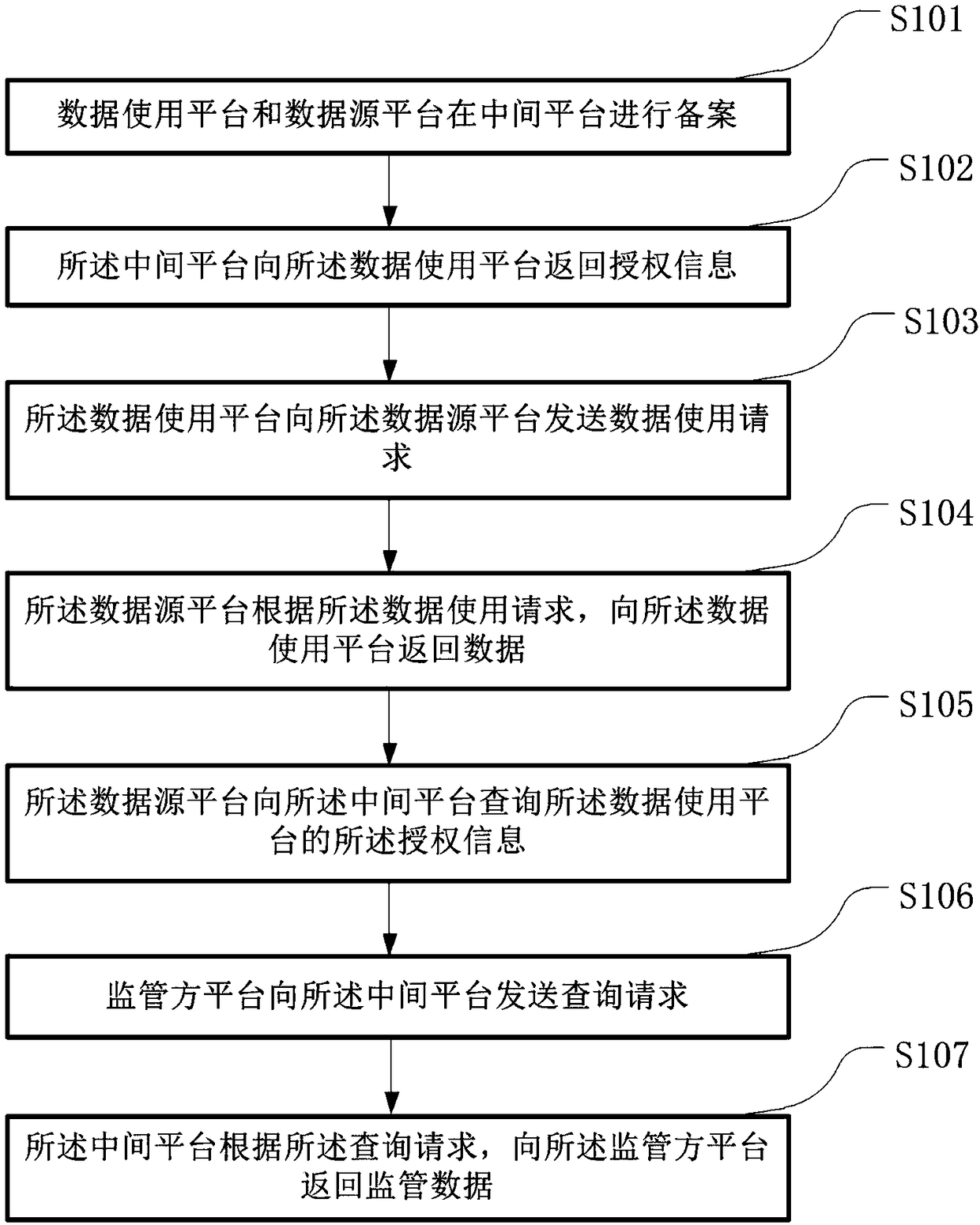
[0048] figure 1 It is a schematic flow diagram of the user authorization multi-party monitoring and sharing method in Embodiment 1 of the present invention, as shown in figure 1 As shown, the user authorizes multi-party monitoring and sharing methods including:
[0049] In step S101, the data usage platform and the data source platform are filed on the intermediate platform.
[0050] The filing information includes: data usage authorization agreement information, and identity information of the data usage platform and the data source platform.
[0051] The data usage authorization agreement is formulated on the data source side, and the end user must read and agree to it when using it. The data source provider may formulate an authorization agreement for all data services provided, and may also formulate an authorization agreement for each function or API (Application Program Interface, Application Program Interface) in the data service. A data source can have multiple auth...
Embodiment 2
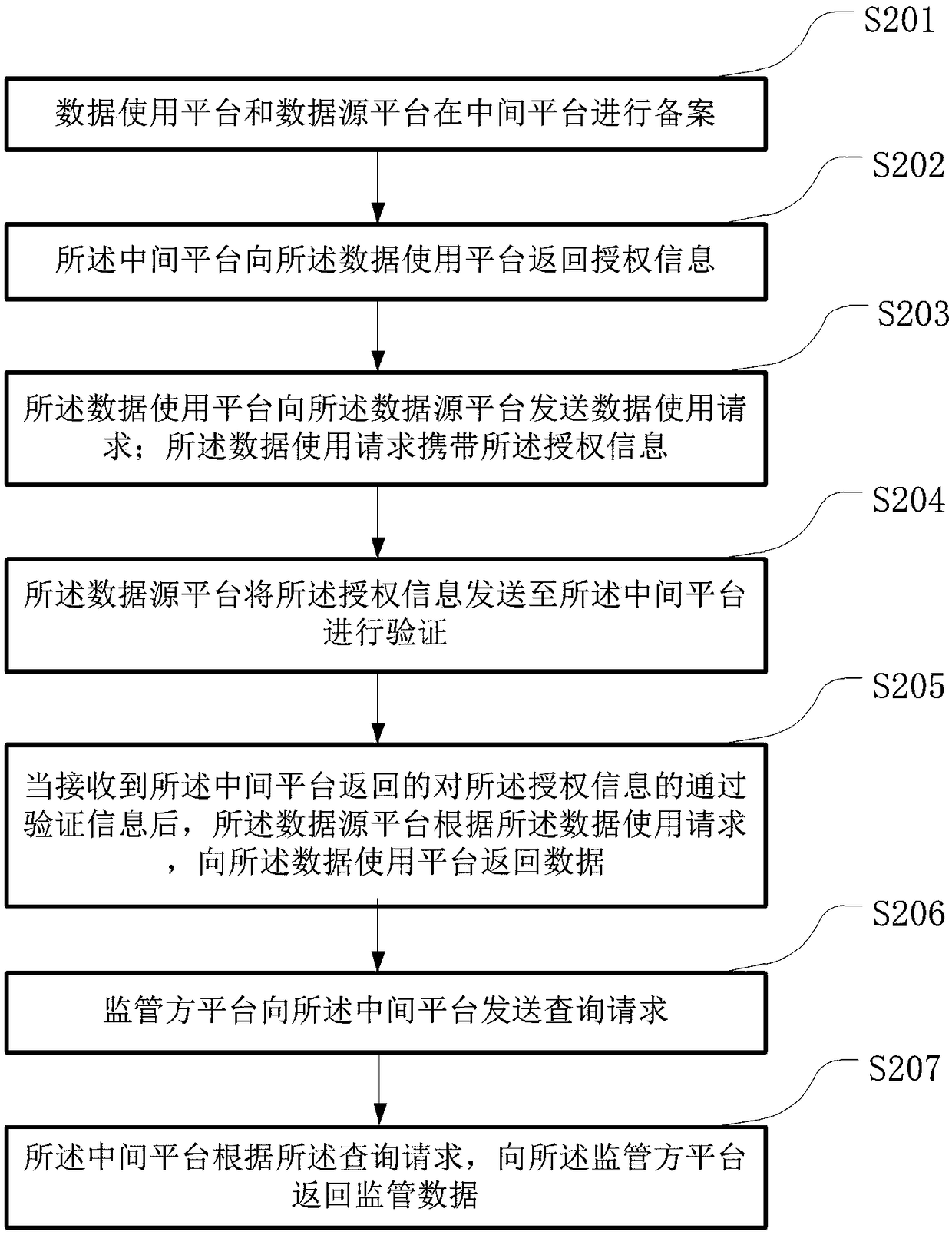
[0067] figure 2 It is a schematic flow diagram of the user authorization multi-party monitoring and sharing method in Embodiment 1 of the present invention, as shown in figure 2 As shown, the user authorizes multi-party monitoring and sharing methods including:
[0068] In step S201, the data usage platform and the data source platform are filed on the intermediate platform.
[0069] The filing information recorded by the intermediate platform includes: data usage authorization agreement information, and identity information of the data usage platform and the data source platform.
[0070] Step S202, the intermediate platform returns authorization information to the data usage platform.
[0071] For example, if an e-commerce company wants to use the personal portrait query service of the Jinlian database, the e-commerce company first sends an authorization filing request to the intermediate platform through the data usage platform, and the intermediate platform queries the...
Embodiment 3
[0082] image 3 It is a schematic structural diagram of a user-authorized multi-party monitoring and sharing system in Embodiment 3 of the present invention, as shown in image 3 As shown, the user-authorized multi-party monitoring and sharing system 30 in Embodiment 3 of the present invention includes: a data usage platform 31 , an intermediate platform 32 and a data source platform 33 .
[0083] The intermediate platform 32 is used for filing with the data usage platform 31 and the data source platform 33 , and returns authorization information to the data usage platform 31 . The filing information recorded by the intermediate platform includes: data usage authorization agreement information, and identity information of the data usage platform and the data source platform.
[0084] The data usage platform 31 is configured to send a data usage request to the data source platform 33 .
[0085] The data source platform 33 is configured to return data to the data usage platfor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com