Systems and methods for identifiying compromised devices within industrial control systems
A technology for industrial control systems and industrial equipment, applied in general control systems, control/regulation systems, comprehensive factory control, etc., to solve problems such as inability to meaningfully monitor network traffic, leaks, and systems vulnerable to attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
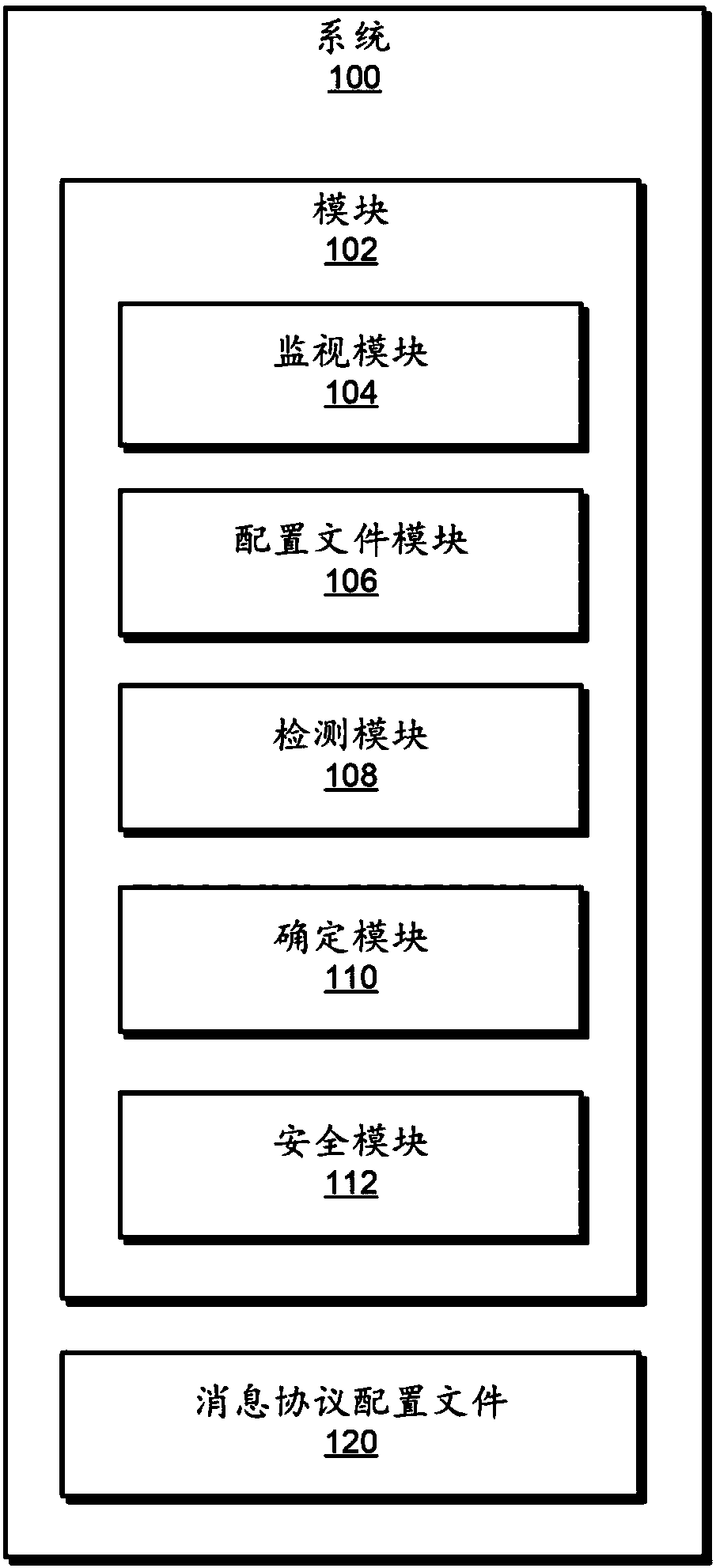
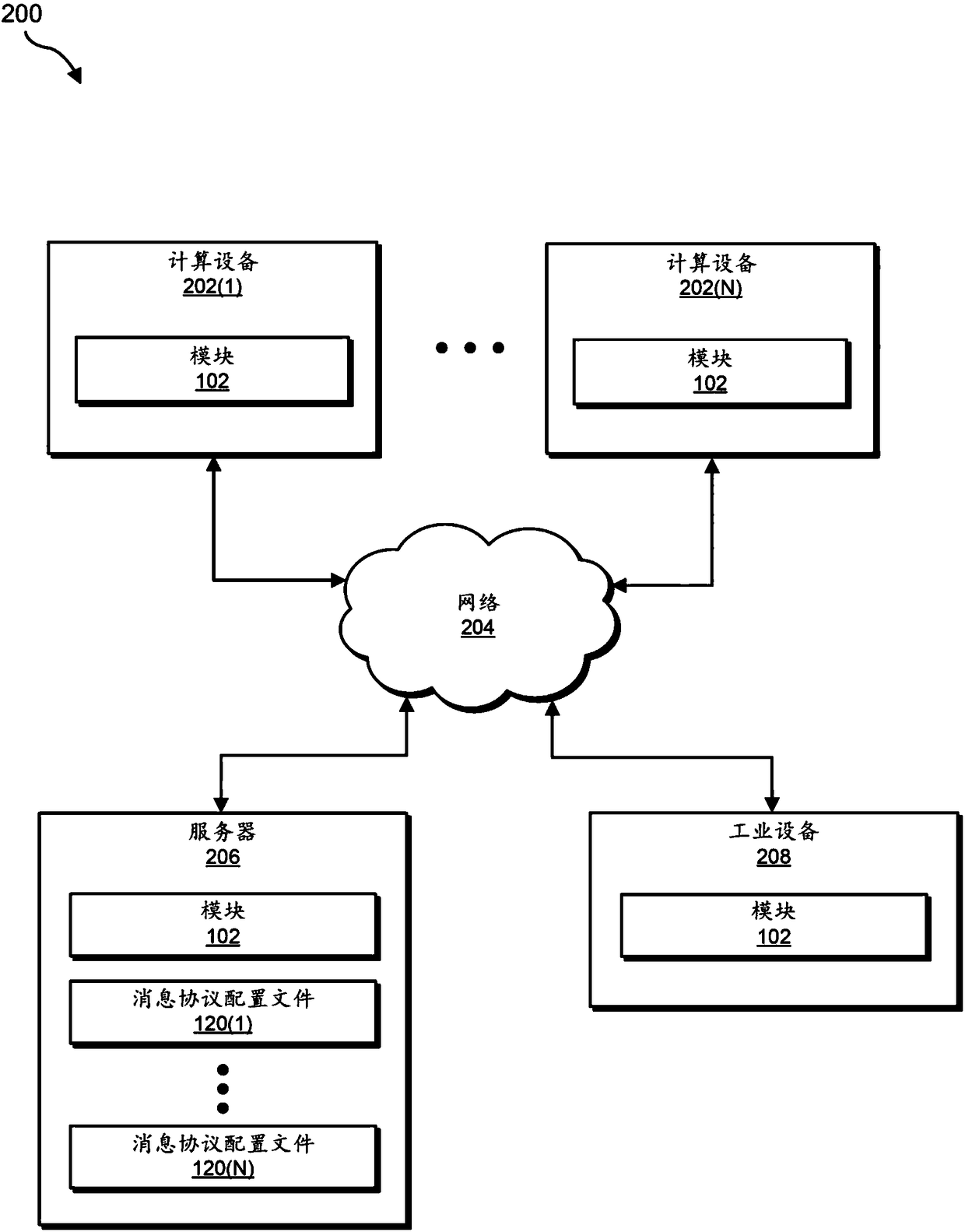
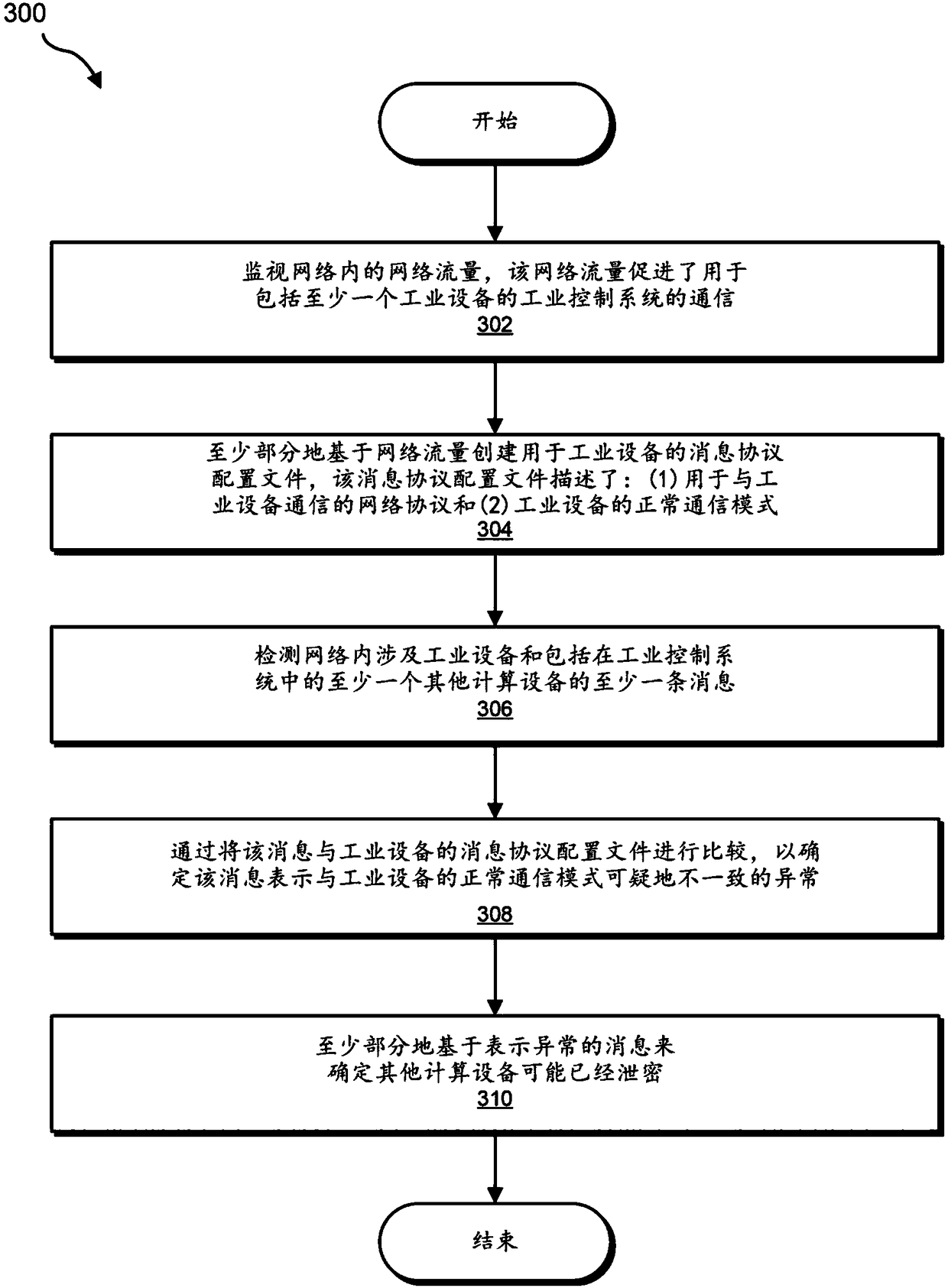
[0021] The present invention generally relates to systems and methods for identifying compromised devices within industrial control systems. As will be explained in more detail below, by monitoring network traffic within an industrial network, the various systems and methods described herein enable the monitoring of industrial networks communicating via an industrial network even if the communication protocol is undocumented and / or not available to the public. Study and / or reverse engineer the communication protocols used by the control system. When communication protocols are learned and / or reverse engineered in this manner, the various systems and methods described herein can group similar traffic into groups of messages that share certain characteristics (e.g., same communication protocol, same purpose Internet Protocol (IP) address and / or the same destination port number). These systems and methods can then build a message protocol profile that describes the normal commun...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com