Method for detecting privacy leakage on basis of context information
A privacy leakage and detection method technology, applied in the direction of instrument, platform integrity maintenance, digital data protection, etc., can solve the problems of repackaging failure, increased system overhead, difficulty of development, and large software impact, etc., to achieve small modification, Ease of Deployment, Efforts to Mitigate Challenges
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
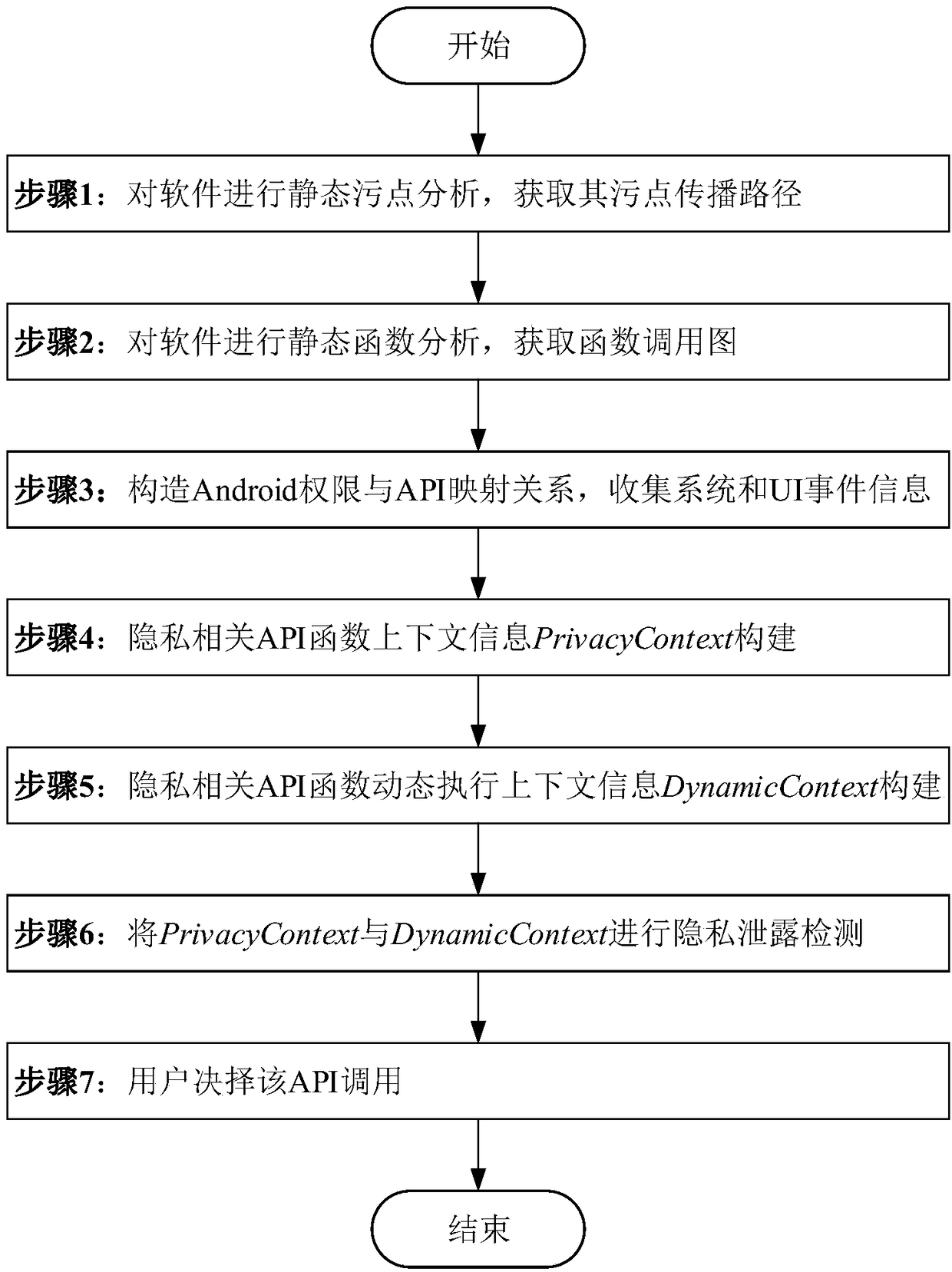
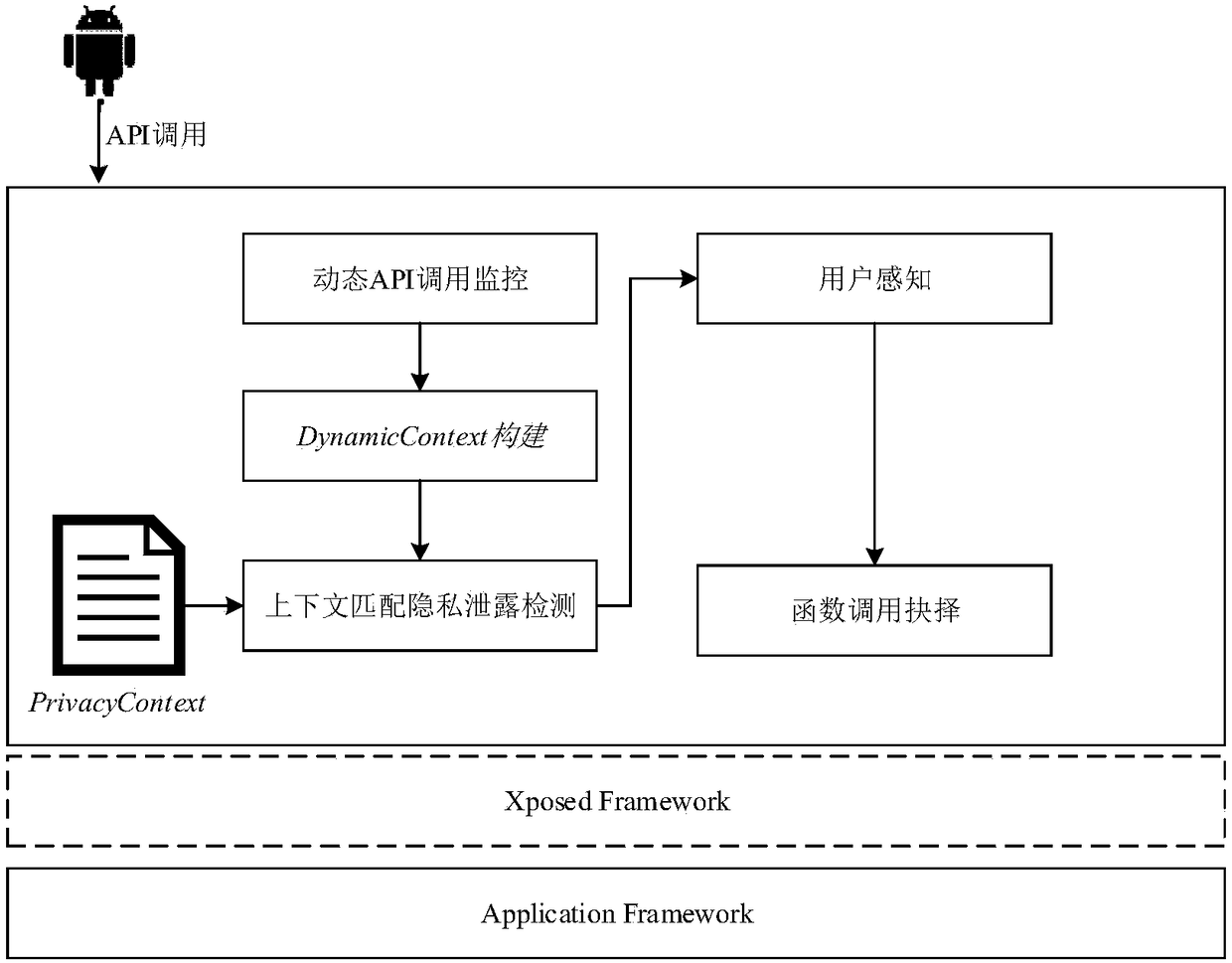
[0049] The privacy leakage detection method based on context information includes the following contents:
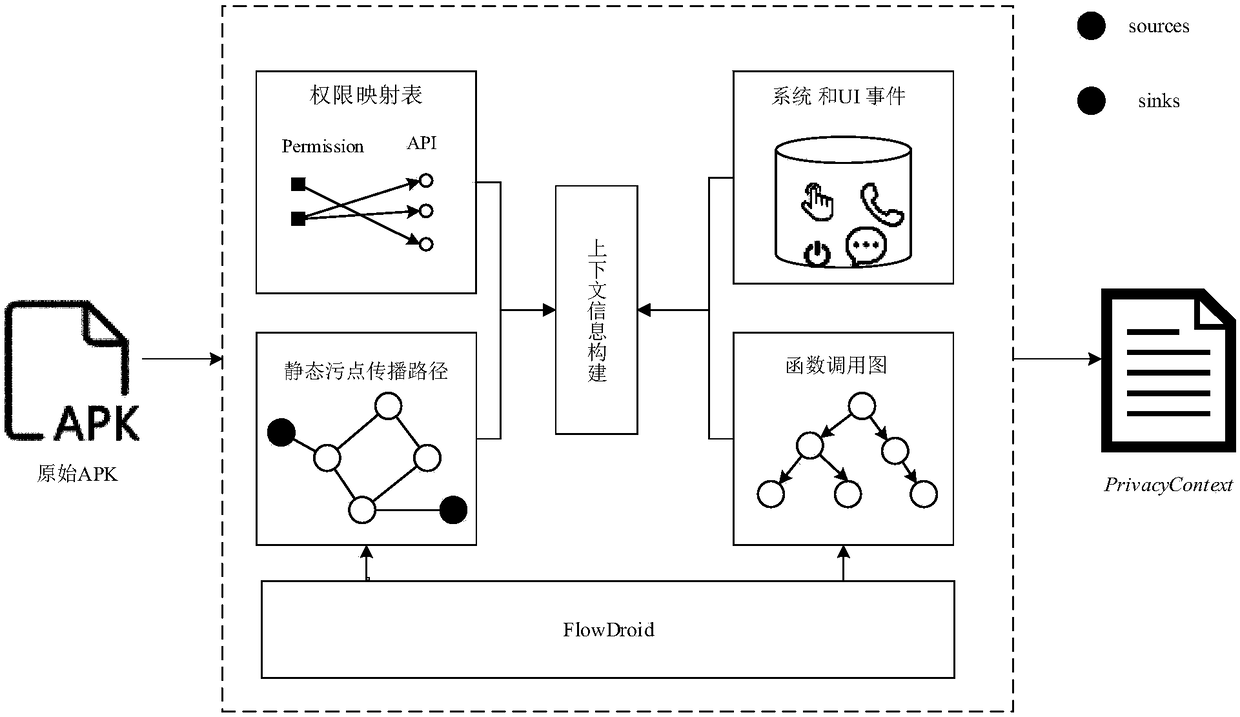
[0050] 1. Acquisition of software taint propagation path
[0051] Configure the source and anchor functions, and then obtain the taint propagation path through the FlowDroid static taint analysis platform.
[0052] 2. Acquisition of software function call graph
[0053] Decompile the software installation package to generate Java code, and then use the Soot framework to obtain its function call graph from the decompiled Java code.
[0054] 3. Construction of Android permission and API mapping relationship
[0055] The mapping relationship between permissions and APIs reflects the relevant permissions required for an API call. In order to cover a larger area of API functions, we use the data provided in the PScout project.
[0056] 4. Collection of system and UI event information
[0057] The information we collect includes system events commonly u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com