D2D heterogeneous cellular secure transmission method based on QoS guarantee counting
A secure transmission and cellular technology, applied in security devices, machine-to-machine/machine-type communication services, network traffic/resource management, etc., can solve difficult to describe delay-sensitive security requirements, transmission rate reduction, legitimate users Issues such as lost launch opportunities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The present invention will be further described in detail below in conjunction with specific embodiments, which are explanations of the present invention rather than limitations.
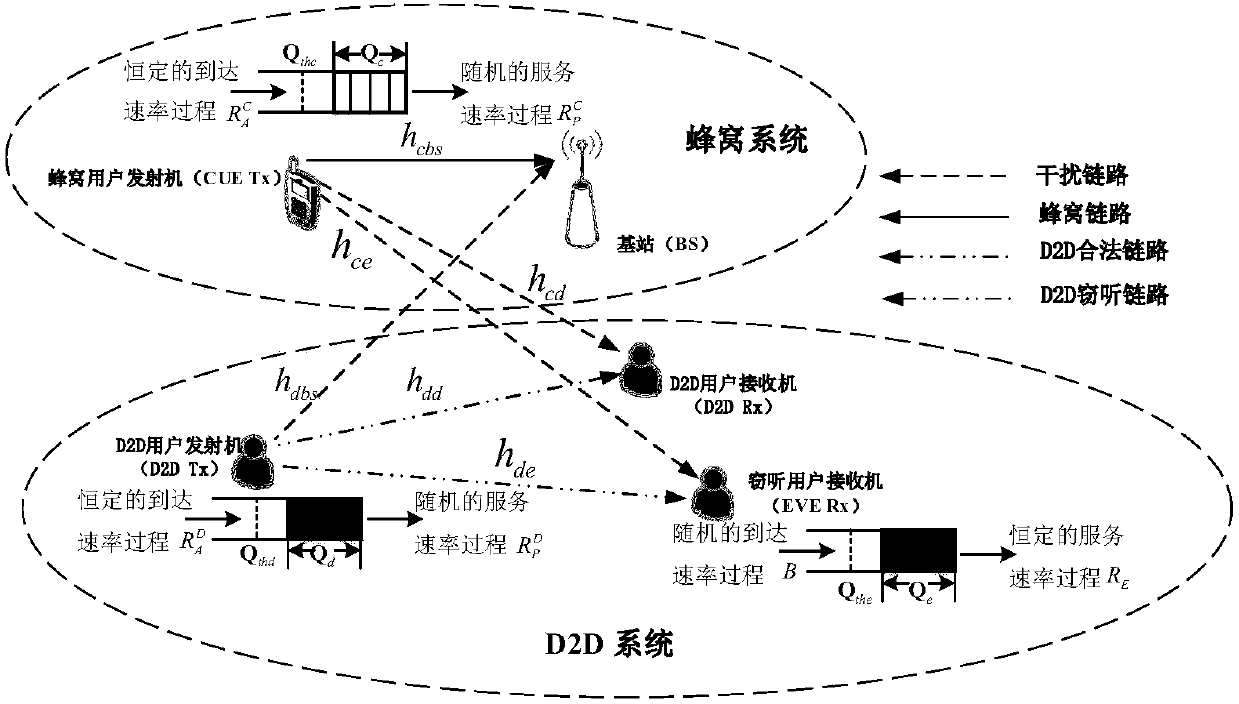
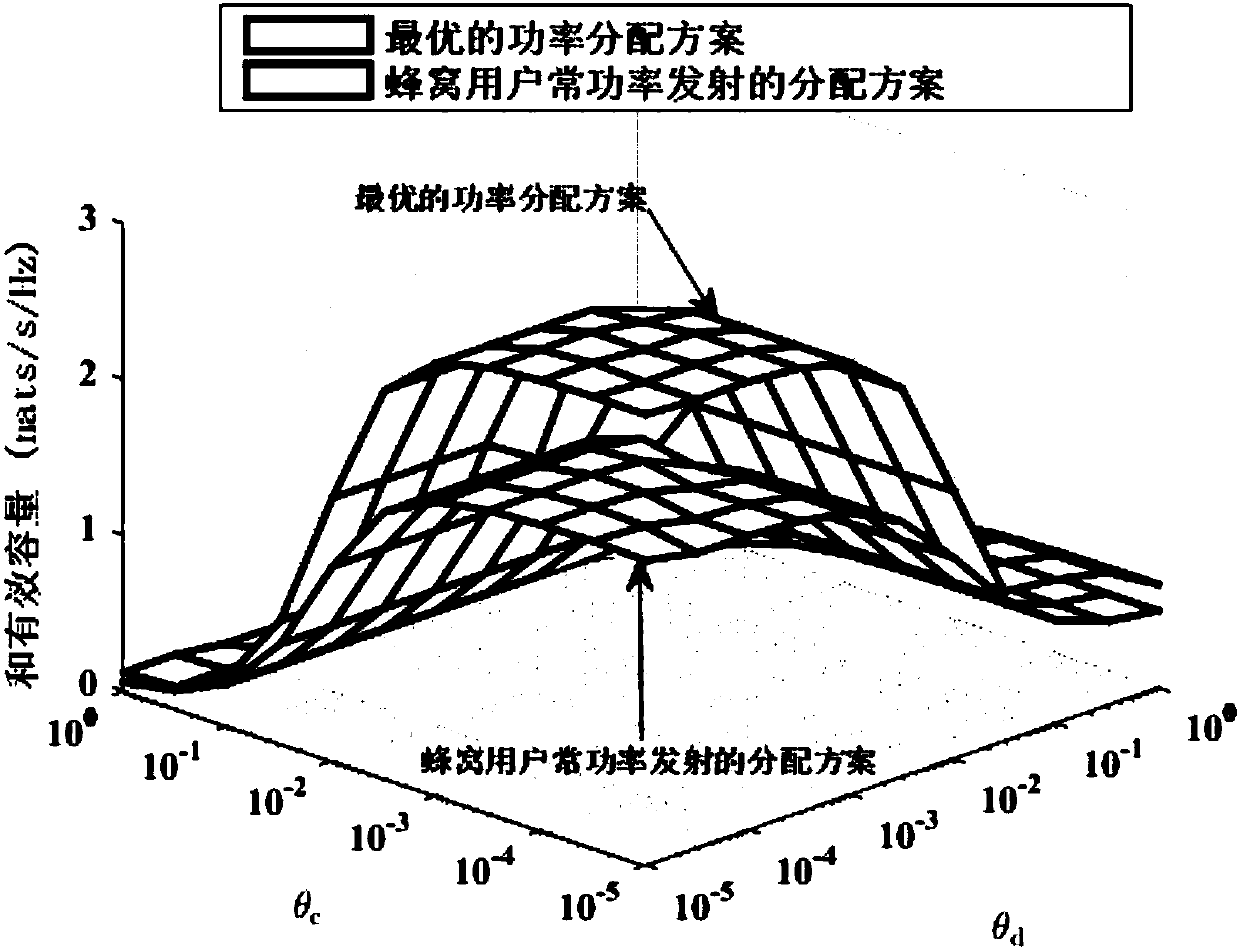
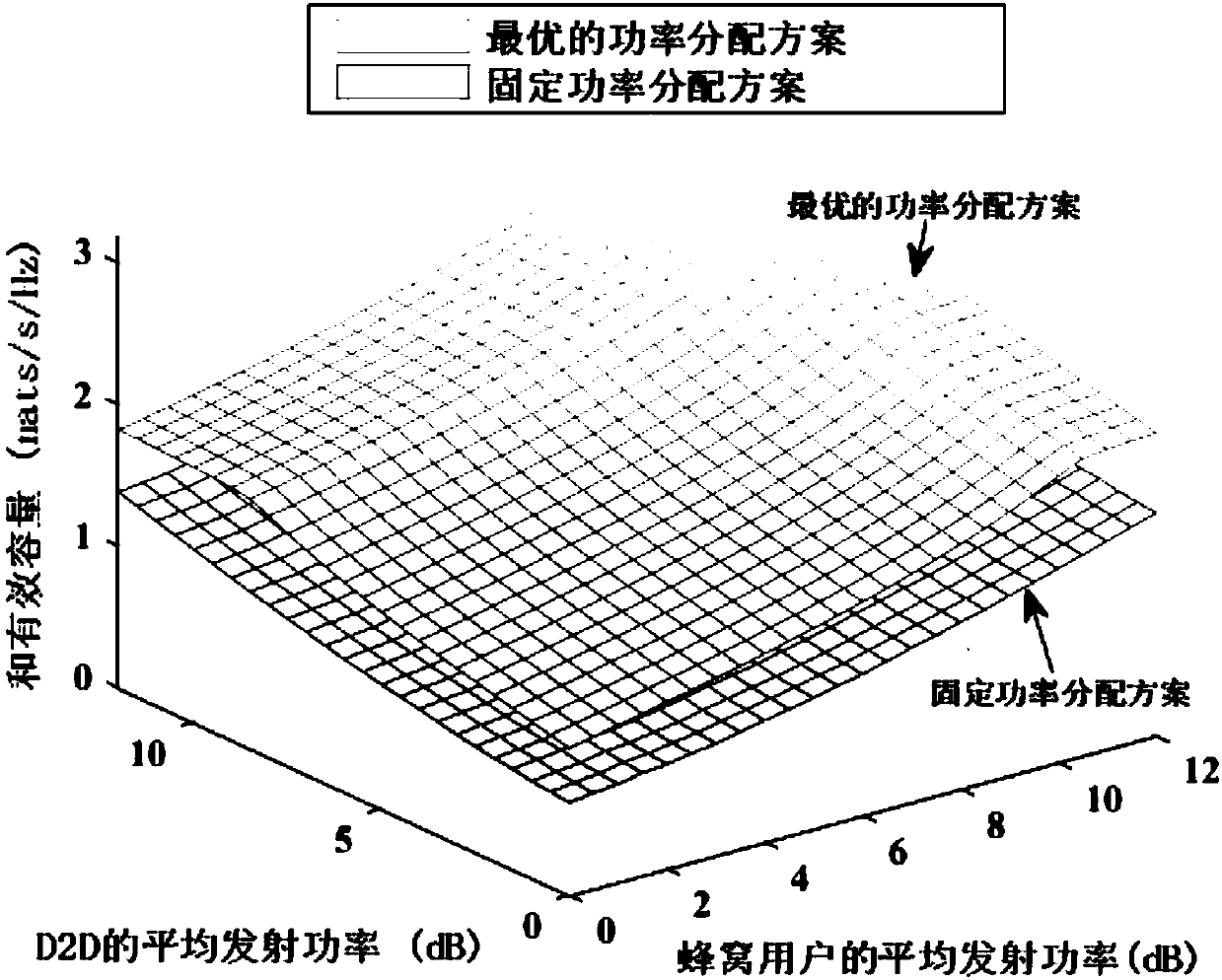
[0018] In the present invention, we use statistical queue analysis theory to protect different statistical delay QoS and D2D delay-sensitive security guarantees for uplink spectrum resource communication protection of D2D multiplexing cellular network in 5G network. Specifically, based on the statistical queue analysis theory, the statistical delay QoS and delay-sensitive security requirements can be described by the queue length threshold violation probability. By using the theory of effective capacity and effective bandwidth, we can further transform the violation probability constraint of the transmission data queue length threshold of all users into an equivalent maximum reachable rate requirement, and transform the eavesdropping data queue length threshold violation probability constraint...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com