Method and device of accessing restriction on resource and terminal equipment
A resource limitation and resource technology, applied in the Internet field, can solve problems such as low system operation efficiency and usage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
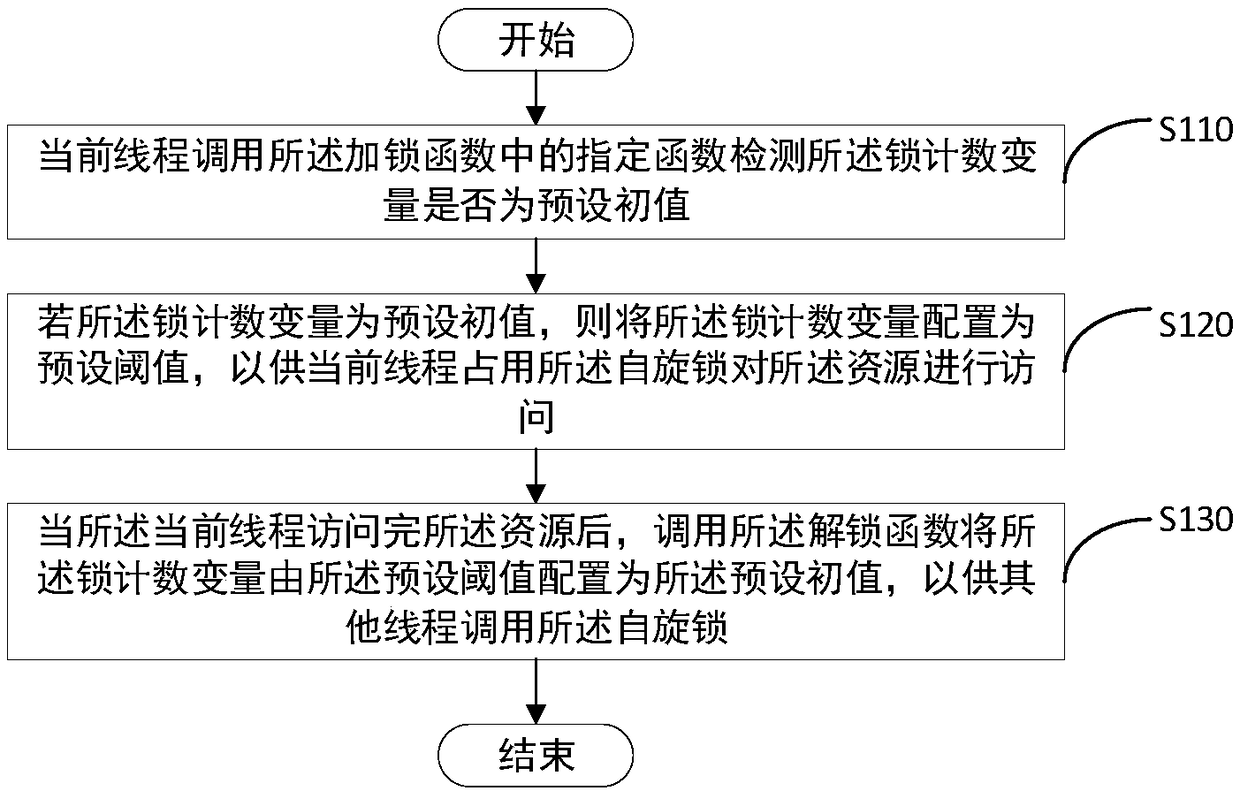
[0036] Create a spin lock through class SpinLock, which includes a constructor, a locking function lock, and an unlocking function unlock. Wherein, the lock count variable is defined in the constructor, and the initial value of the lock count variable is 0, which means that the spin lock is an idle spin lock not occupied by other threads. The locking function lock is placed in the while loop. In the body of the while loop, the lock count variable is read and written through the InterlockedCompareExchange system function (specified function). The InterlockedCompareExchange system function is an atomic operation function provided by the Windows platform. Among them, the while loop body of the locking function is:
[0037]
[0038] It can be seen that, by int old=InterlockedCompareExchange((volatile long*)&m_spin, 1,0); three parameters of the interlockedCompareExchange system function are defined, and these three parameters are respectively the lock count variable, the first ...
no. 2 example
[0041] In the first embodiment, two atomic API operation functions, InterlockedCompareExchange and InterlockedExchange, are used. These two operation functions are atomic operation functions provided by the Windows platform, and cannot be transplanted to systems such as Linux, Mac / OSX, Android, and iOS. Therefore, in order to realize the cross-platform spin lock method, the atomic atomic operation template class in the C++11 standard is used to realize the cross-platform use of the spin lock method. Specifically, the spin lock includes a constructor, a lock function lock and an unlock function unlock. Wherein, the constructor defines the initial value of the lock count variable m_spin as 0, which indicates that the lock count variable is an idle spin lock not occupied by other threads.
[0042] The locking function lock is placed in a while loop body. In the loop body, the read and write operations on the lock count variable are realized through the compare_exchage_strong func...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com