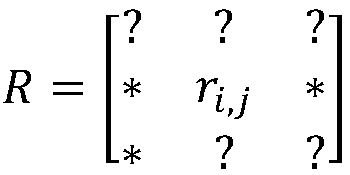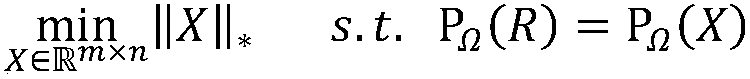Shilling attack resistance recommendation algorithm based on matrix completion
A technology of matrix completion and recommendation algorithm, applied in the field of information security in the field of computer technology, and can solve problems such as trust attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
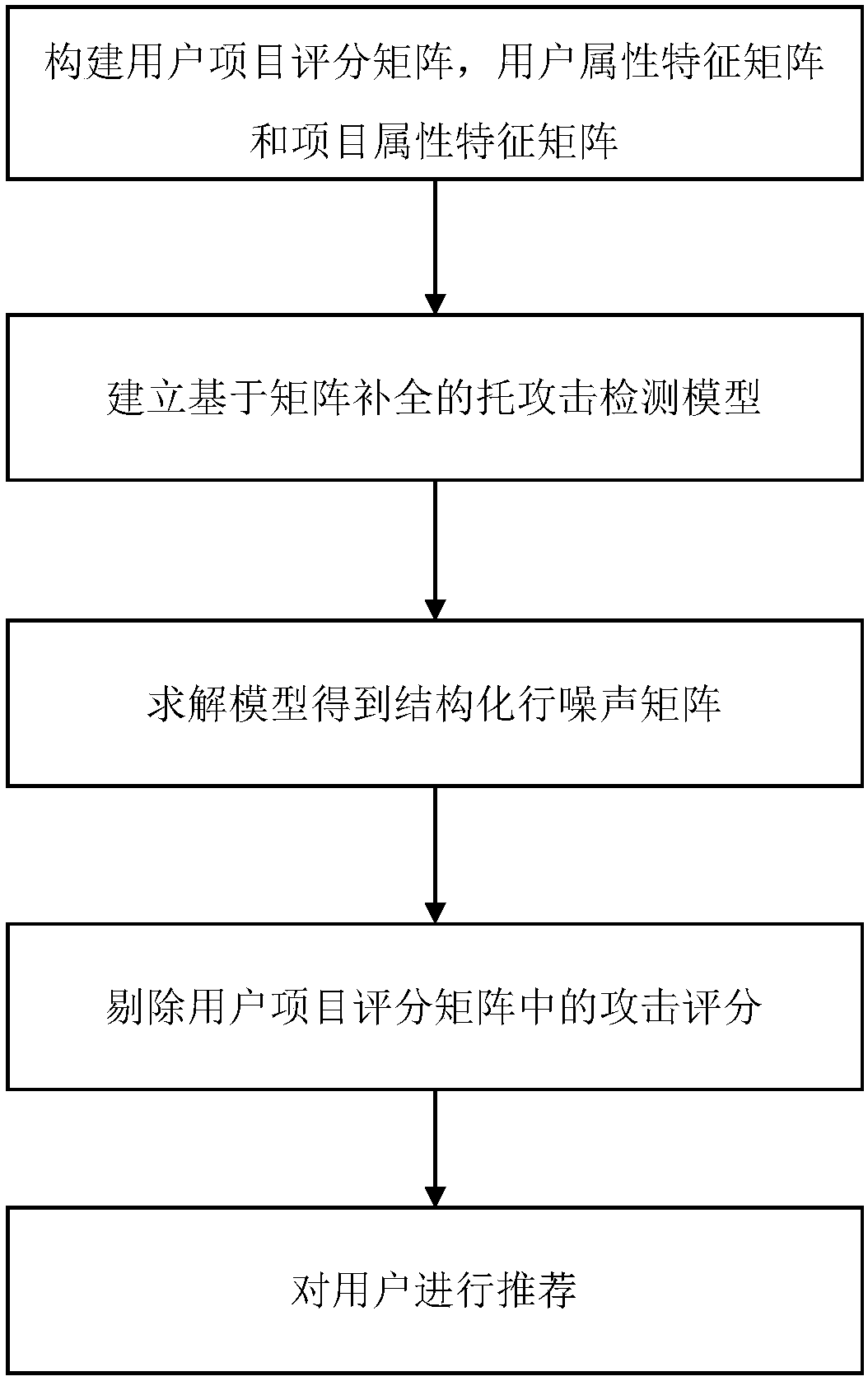
[0082] A matrix-completion-based anti-trust attack recommendation algorithm includes the following steps:
[0083] 1) Establish user-item rating matrix:
[0084] m users form user set U={u 1 , u 2 ,...u m}, n items constitute the item collection I={i 1 ,i 2 ,…i n}, the user-item rating matrix can be expressed as
[0085]
[0086] Among them, the rating of user u on item i is denoted as r i,j , "*" indicates a known score, and "?" indicates an unknown score.
[0087] 2) Establish a recommendation system model:
[0088] For recommendation system problems, low-rank matrix completion techniques can be used for score prediction. Using R to represent the currently observed scoring matrix, the recommendation system problem can be modeled as:
[0089]
[0090] Among them, the Ω set represents the set of element subscripts that have received ratings in the scoring matrix, The X matrix is a low-dimensional unknown matrix, σ i is the matrix kernel norm, σ i is t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com