A ddos attack defense method and defense system of sdn controller
A controller, purpose technology, applied in the field of network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
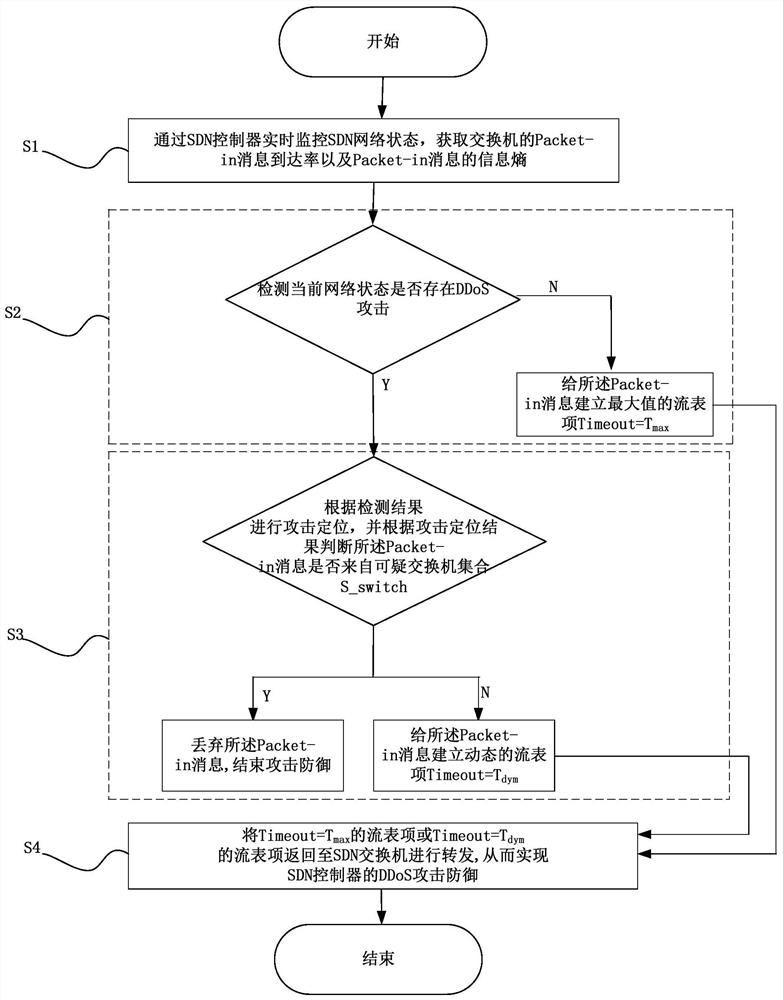
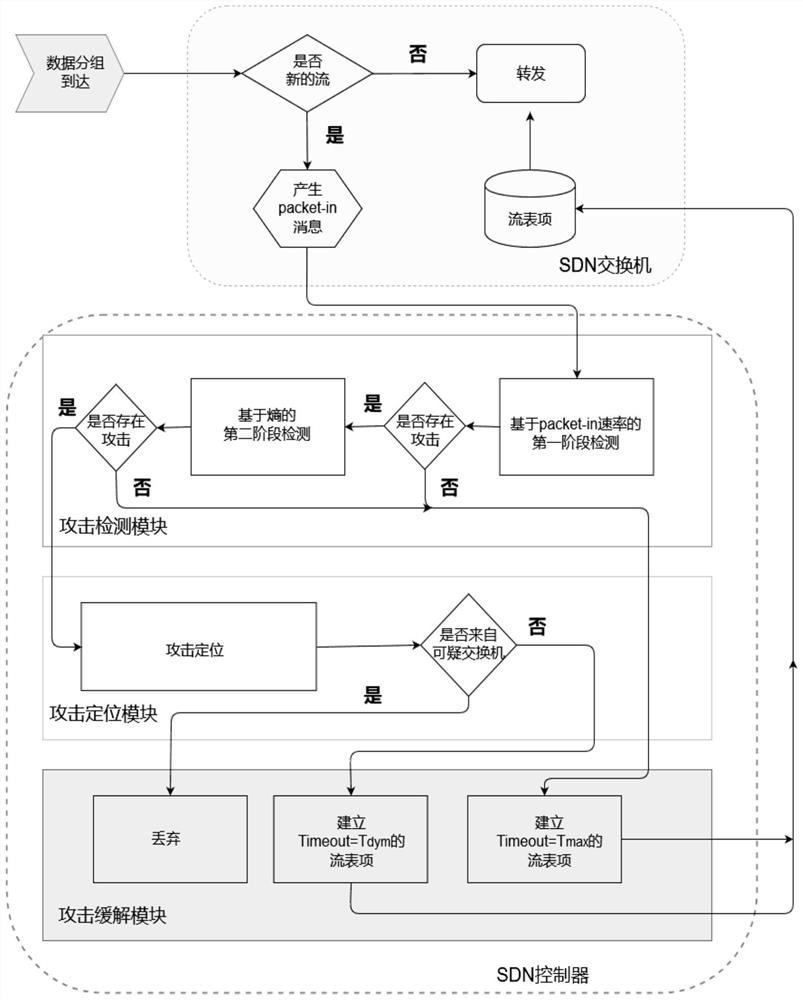
[0061] Such as figure 1 As shown, a DDoS attack defense method of an SDN controller, the implementation steps are as follows:
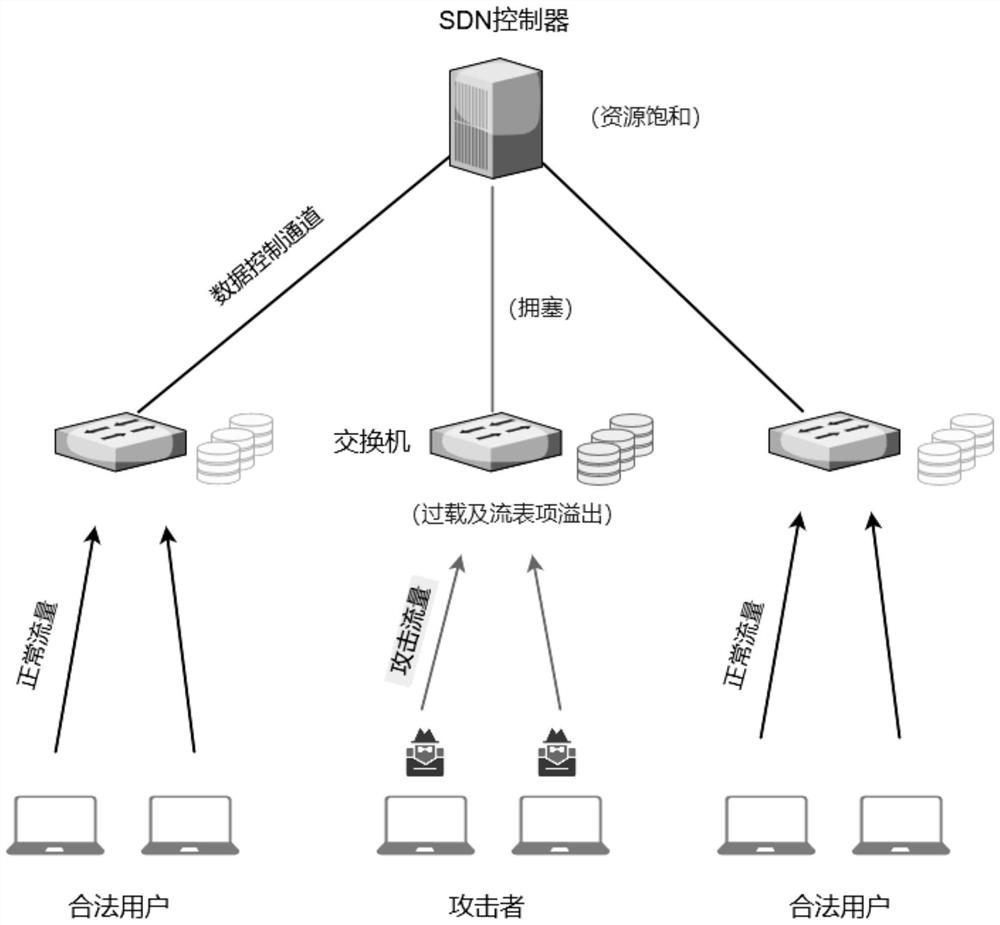
[0062] (S1) monitor the SDN network state in real time through the SDN controller, and obtain the Packet-in message arrival rate of the switch and the information entropy of the Packet-in message;
[0063] (S2) according to the Packet-in message arrival rate of described switch and the information entropy of Packet-in message, detect whether there is DDoS attack in current network state, if have, then enter step (S3), otherwise, then give described Packet-in The in message establishes the maximum flow entry Timeout=T max , and enter the step (S4), wherein, Timeout is the timeout value of the switch flow entry, which includes the following steps:
[0064] (a1) the window queue size W and the hash table C at the SDN controller end are emptied;
[0065] (a2) Add the Packet-in message i received by the SDN controller into the window queue, the size of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com