Database storage security encryption method
A security encryption and database technology, applied in the field of database storage security encryption, can solve the problems of difficult transplantation and cumbersome operation, and achieve the effect of good portability and protection of sensitive data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
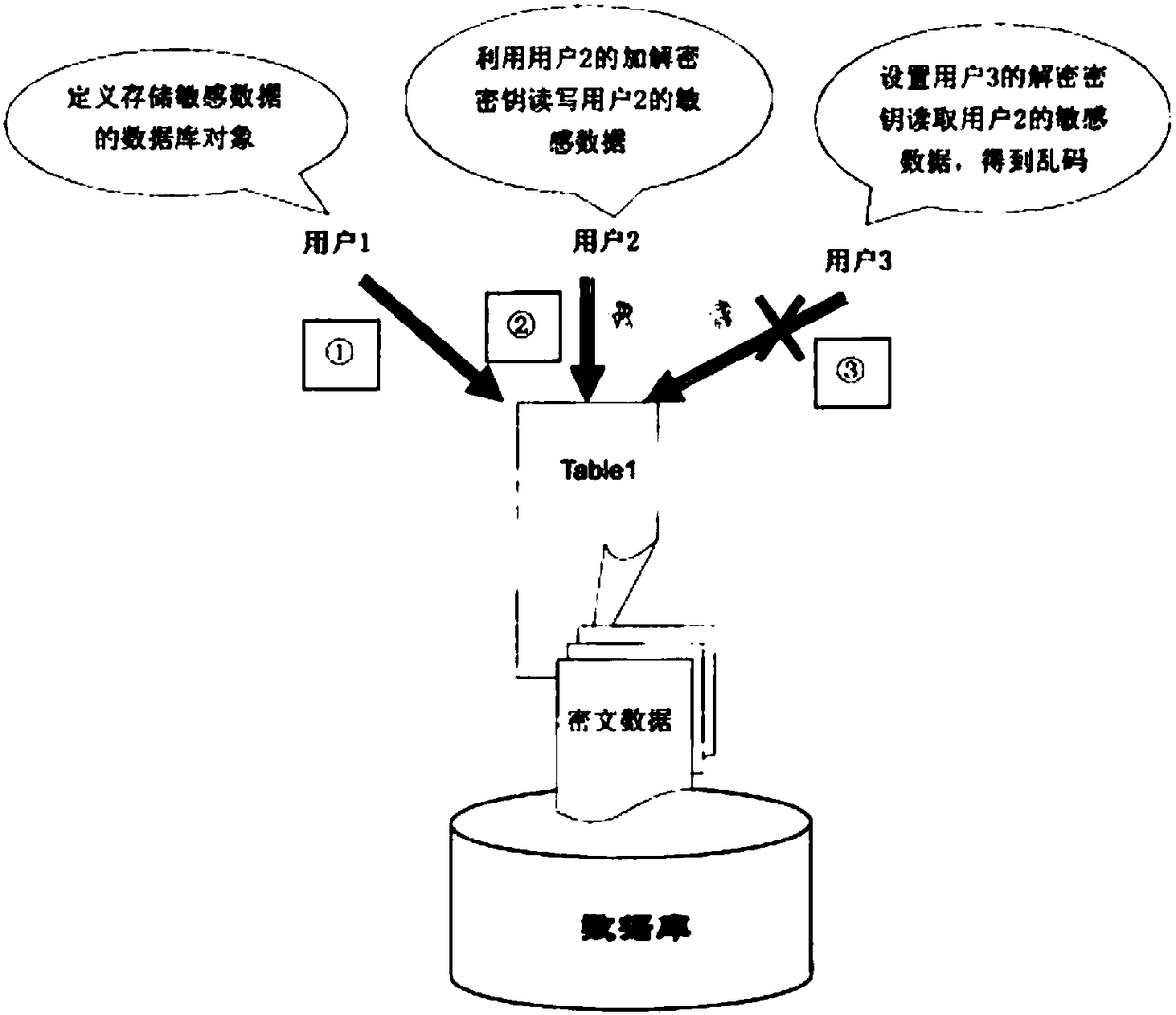
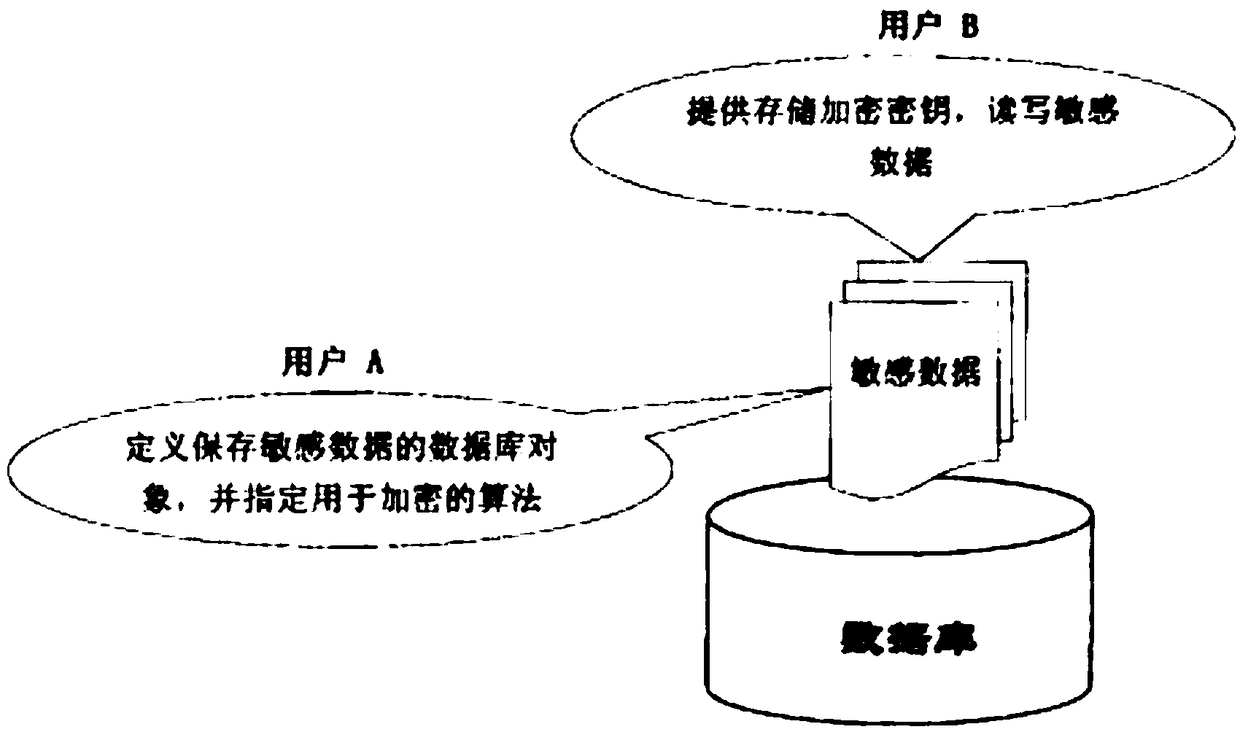
[0021] ①User 1 defines a table Table1 that stores sensitive data, and specifies the encryption algorithm used to encrypt the data in Table1 when defining Table1;
[0022] ②User 2 logs in to the database, and uses his own key to perform operations such as insertion and query on Table1. In the process of insertion and query, the database management system automatically invokes the encryption algorithm of Table1 and uses the key of user 2 to complete the encryption and decryption process;
[0023] ③ After user 3 logs in to the database, he wants to view the data inserted by user 2 in table Table1.
[0024] When the data is uploaded, the system cannot correct the data inserted by user 2 because it does not know the decryption key of user 2.
[0025] Decryption, so that the sensitive data of user 2 cannot be obtained. Similarly, user 2 does not know the solution of user 3
[0026] When encrypting the key, it is also impossible to view the sensitive data stored in Table 1 by User...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com