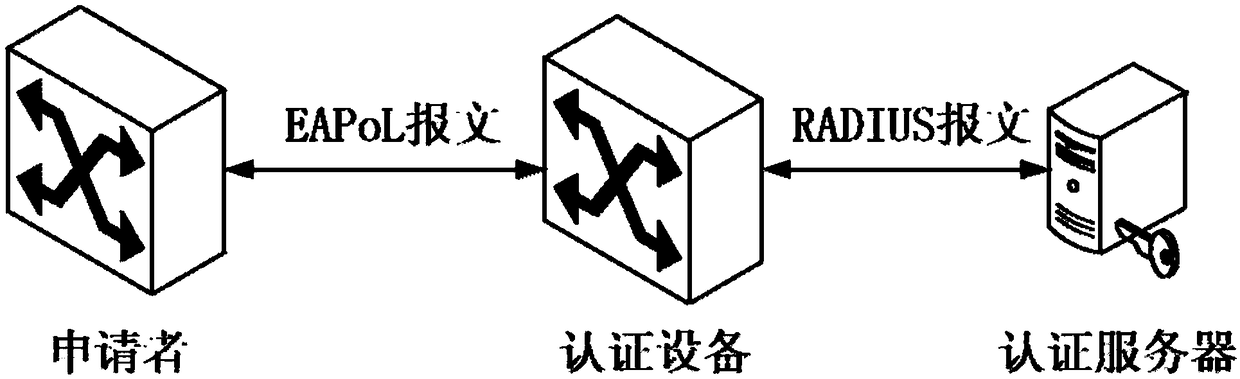
Port authentication method for authentication server, server, switch and storage medium
An authentication server and port authentication technology, which is applied in the field of servers, switches and storage media, and the port authentication method of authentication servers, and can solve problems such as potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
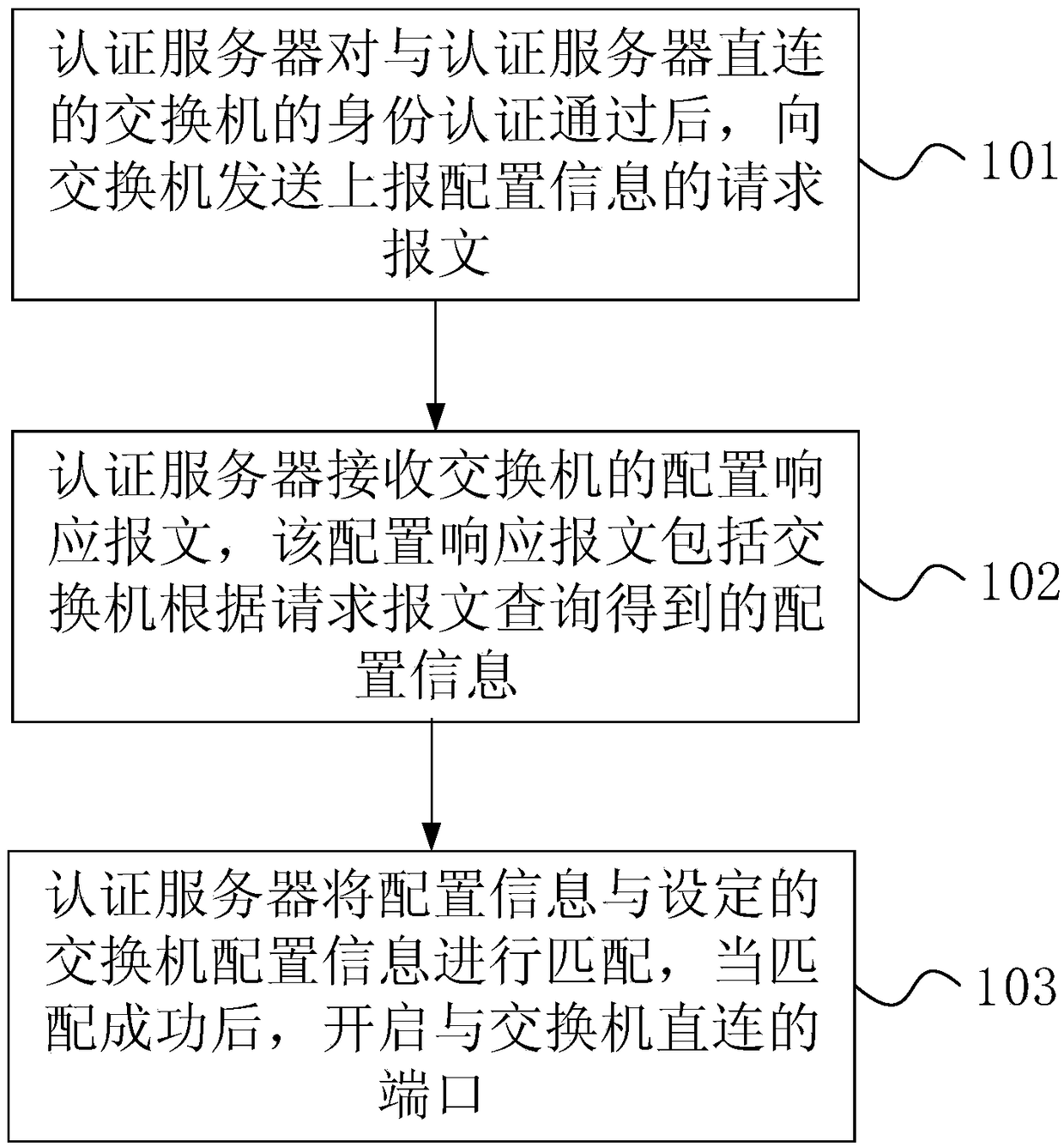
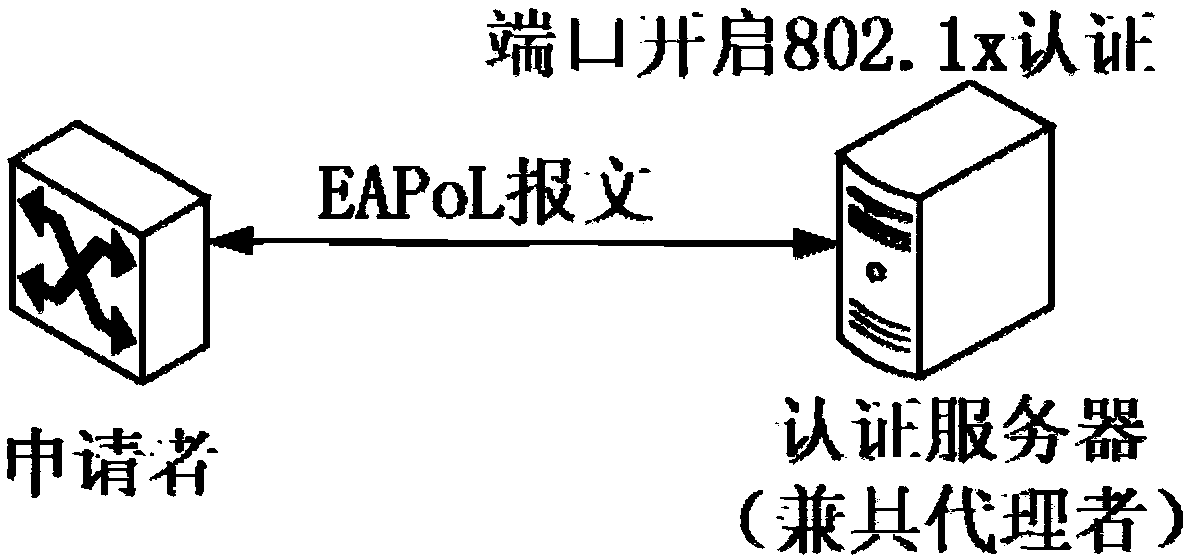
[0079] figure 2 It is a flow chart of the port authentication method of the authentication server provided in Embodiment 1 of the present invention, image 3 It is a schematic diagram of the network topology structure of the existing authentication server directly connected to the switch, such as image 3 As shown, if the switch is directly connected to the authentication server, the switch, as the applicant, requests the authentication server to open the port directly connected to the switch on the authentication server, and the authentication server also acts as an agent in this process. Once the authentication server passes its authentication, the switch as the applicant will be upgraded to an authentication device and provide an agent for other switches that need authentication. At this time, the network topology becomes figure 1 As shown in the structure, the switch is upgraded to figure 1 The second switch in acts as a proxy, and the other switches are equivalent to ...
Embodiment 2
[0100] Figure 4 A flowchart of a port authentication method for an authentication server provided in Embodiment 2 of the present invention, such as image 3 As shown in the figure, if the switch is directly connected to the authentication server, the switch, as an applicant, first requests the authentication server to open the port directly connected to the switch on the authentication server. The authentication server also acts as an agent in this process. Once the authentication server passes the authentication, the switch as the applicant is upgraded to an authentication device to provide an agent for other switches that need authentication. At this time, the network topology becomes figure 1 The structure shown, i.e. the switch is upgraded to figure 1 The second switch in as a proxy, the other switches are equivalent to figure 1 The first switch is the applicant, and the first switch, as the applicant, applies to the authentication server to join the network where the s...
Embodiment 3
[0108] Figure 5 It is a schematic diagram of the composition and structure of the network topology provided by the third embodiment of the present invention, refer to Figure 5 , According to the above network topology, a total of 4 authentication servers are used. In order to ensure the security of the network, the authentication server enables the port authentication function. The directly connected switches include 0-0, 1-0, 2-0, 3-0, These switches all need to initiate authentication to their directly connected authentication servers as applicants to open the ports directly connected to the authentication servers. If the authentication passes, switches 0-0, 1-0, 2-0, and 3-0 are upgraded to proxies. The switch or terminal connected to switches 0-0, 1-0, 2-0, and 3-0 can be used as a new applicant to request to join the network where the agent is located. If the authentication fails, it will cause any one connected to it. Switches cannot access the network, and terminals ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com