Information security alarm method and device and electronic equipment
An information security and preset content technology, applied in the field of network information security, can solve problems such as inability to solve multiple data sources or multi-scenario comparison calculations, reduce the accuracy of information security detection, and undetectable alarm requirements, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
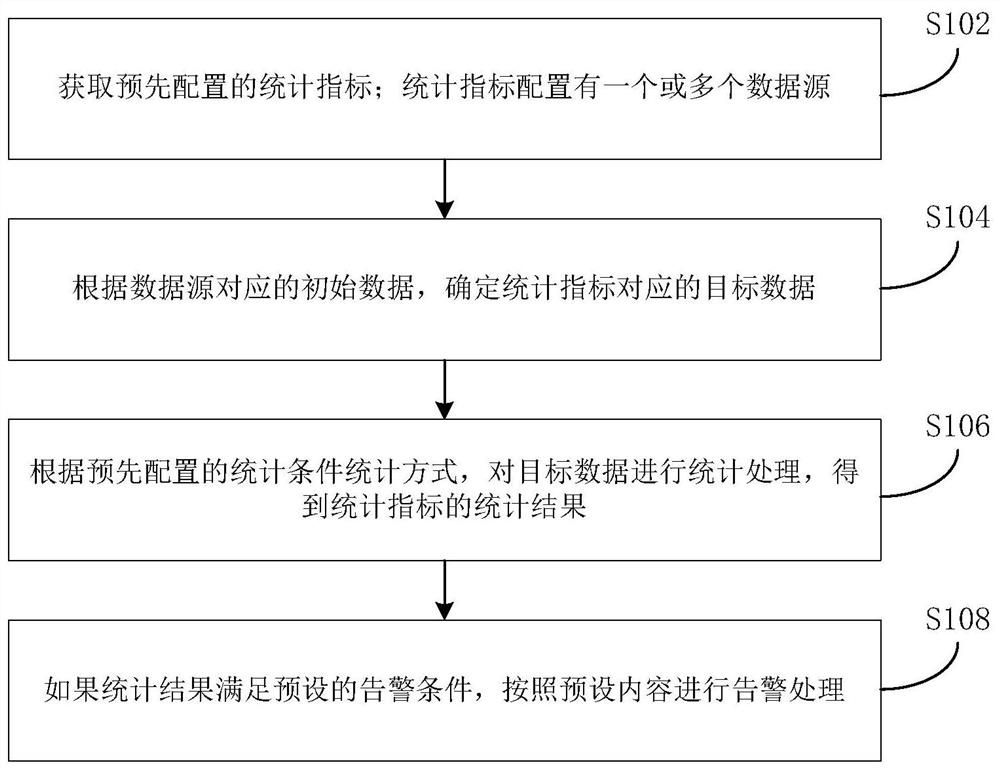
[0060] Step 205, if the target data comprises log data, log data corresponding statistically pre-configured, every predetermined time, log data within a specified time statistical processing, statistical results obtained statistical indicators; wherein data corresponding to the log comprising at least statistical methods: statistical polymerization, and a count of a statistical.
[0061] The above-described log data corresponding to statistically preconfigured, in advance according to the actual alarm needs provided, for example, if the alarm needs a period of time, the total number of infected data reaches 100 when the alarm, and the data to be infected is log data log data corresponding to statistical methods, the polymeric preconfigured or statistical counting statistics, the total number of virus data for the calculation. The designated time may be set to one minute, i.e., every one minute, for obtaining the target data for statistical processing, statistical indicators of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com