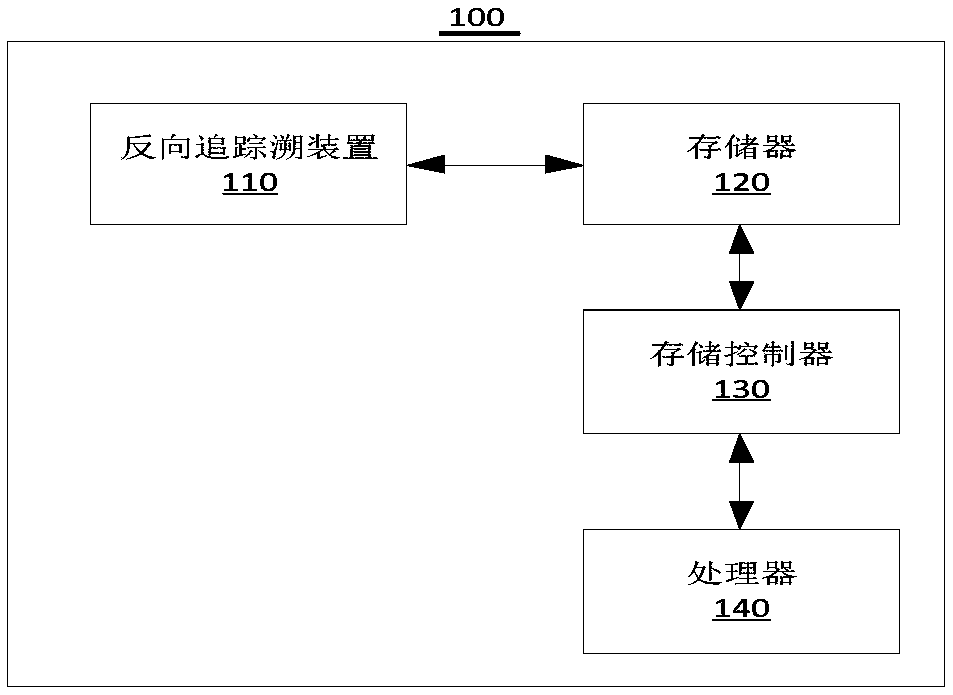
Reverse tracing method and device of proxy host
A technology of reverse tracking and proxy host, applied in the field of network security, can solve the problem of inability to trace the real IP address of attackers, improve the intrusion identification ability of network security protection equipment, etc., and achieve the effect of improving the identification ability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
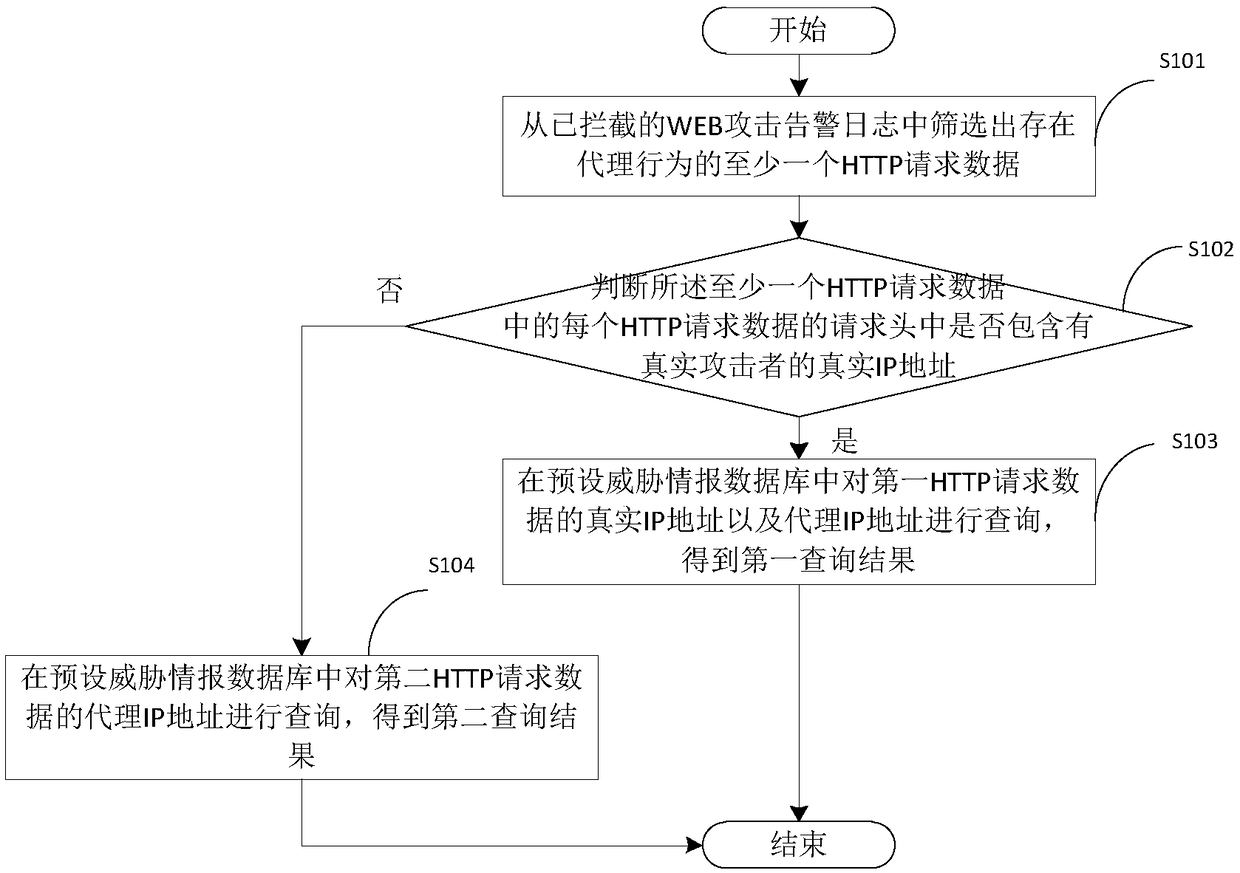
[0033] see figure 2 , which is a reverse tracing method applied to the proxy host of the above-mentioned electronic device 100 provided by the embodiment of the present invention, which will be combined below figure 2 Describe the steps involved.
[0034] Step S101: Filter out at least one HTTP request data with proxy behavior from the intercepted WEB attack alarm log.
[0035] Filter out at least one HTTP request data with proxy behavior from all WEB attack alarm logs intercepted by the network security protection device. As an implementation, you can combine image 3 The steps shown illustrate this process.
[0036] Step S201: Obtain the HTTP request data of each WEB attack alarm log from the intercepted WEB attack alarm log.
[0037] Obtain the HTTP request data of each WEB attack alarm log from all WEB attack alarm logs intercepted by the network security protection device, and further filter out WEB type WEB attack alarms from all the attack alarm logs intercepted b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com