Method, device, medium and device for detecting abnormal behavior access of world wide web
A technology for normal access and behavior, applied in the field of abnormal behavior access detection on the World Wide Web, it can solve the problems of heavy workload, slow speed, and difficult detection by Web scanners, and achieve the effect of improving speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
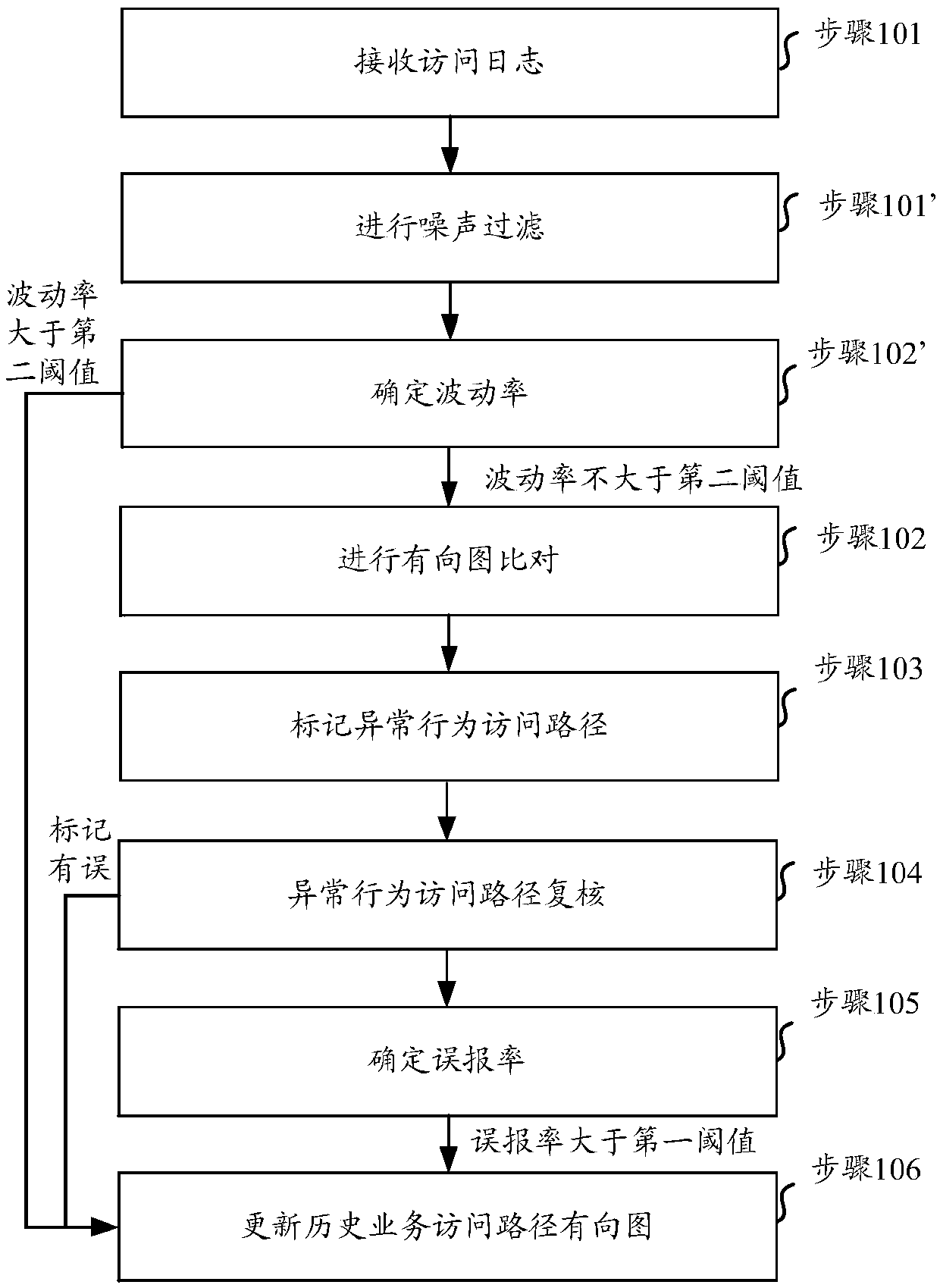
[0029] Such as figure 1 As shown, it is a flow chart of the steps of the method for detecting abnormal web behavior access provided by Embodiment 1 of the present invention. The method includes the following steps:
[0030] Step 101, receiving an access log.
[0031] In this step, access logs within a first set period of time, for example, one week, may be received. The access log can include the access status of each page in the website, such as access to Internet protocol (IP) address, access to uniform resource locator (URL), access to jump link relationship (referer), access to user agent (UA, User Agent) , access time, site domain name, request method, etc.
[0032] Step 102, performing directed graph comparison.
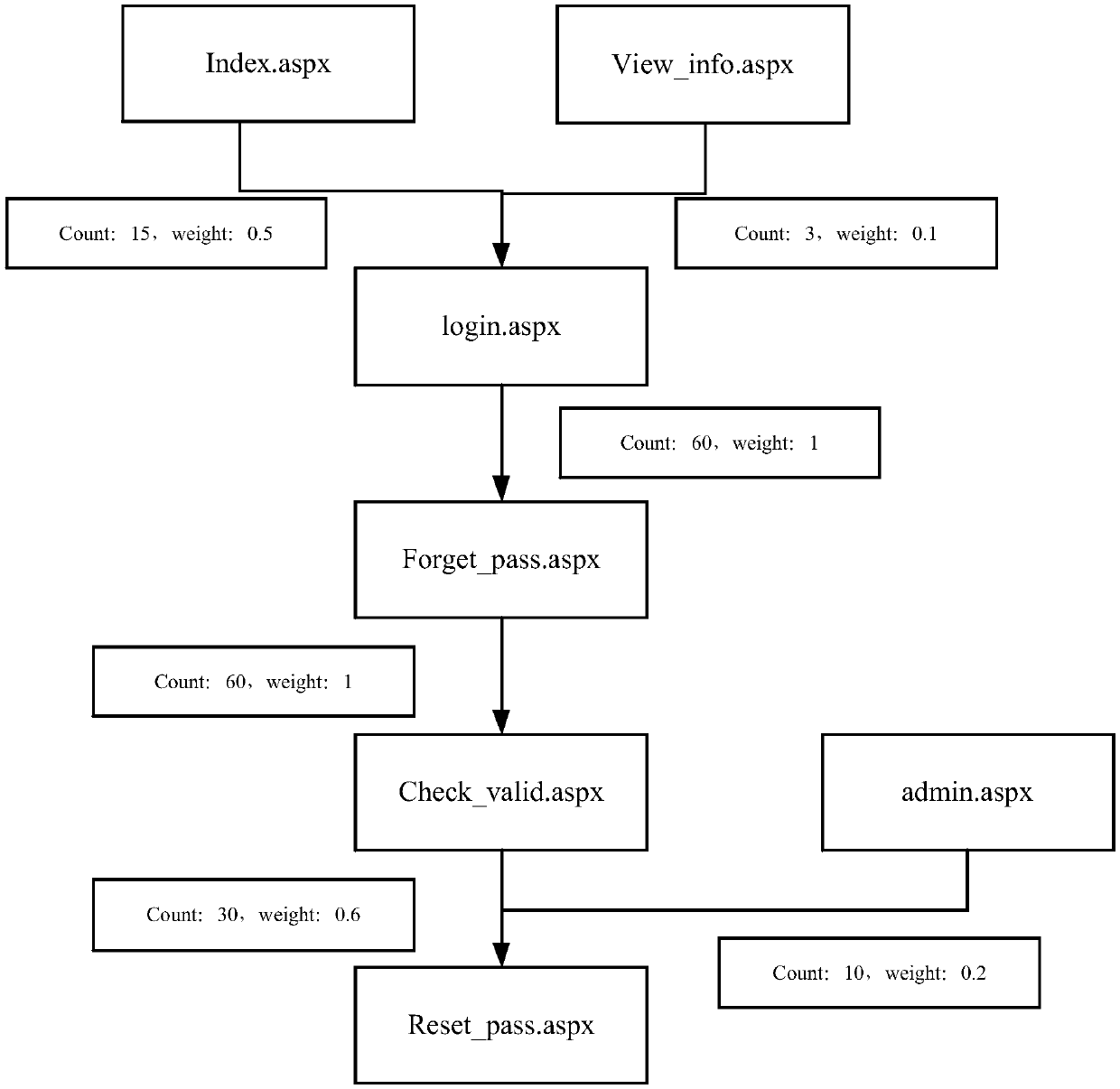
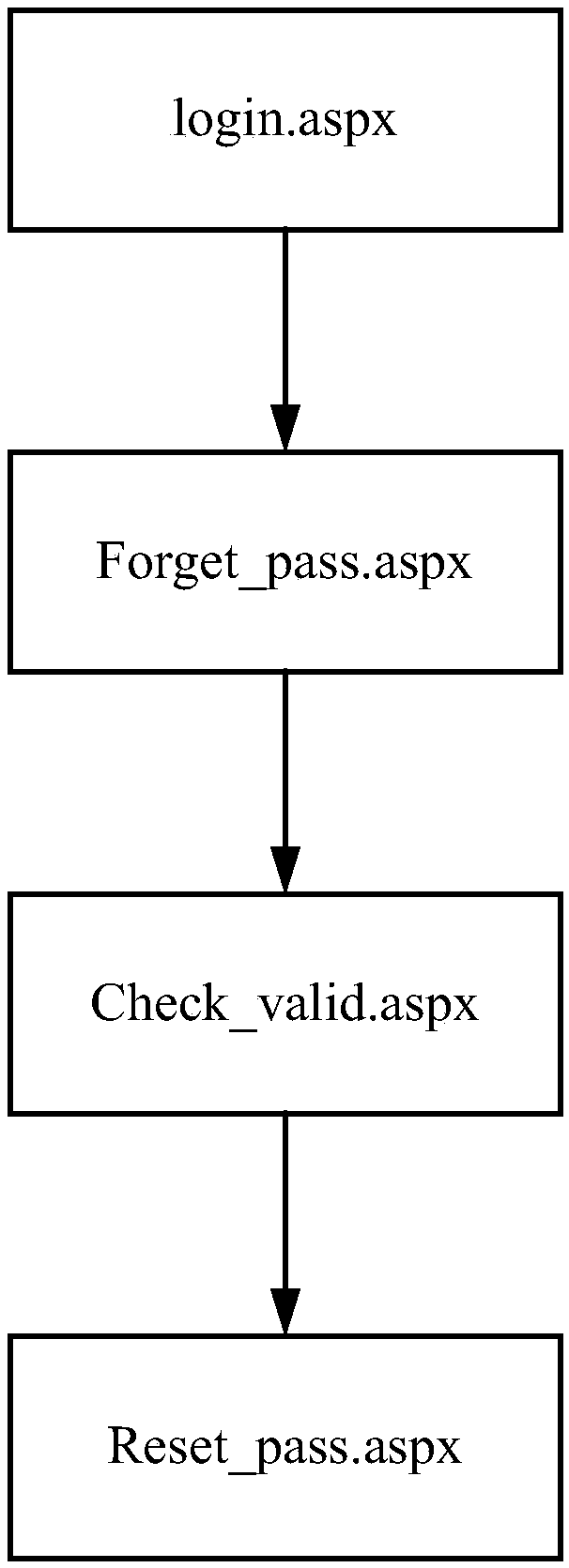
[0033] In this step, the same access path as the start page node of an access path in the temporary business directed graph, the end page node and the historical business backbone directed graph, can be determined as a normal access path; and determine the t...
Embodiment 2
[0144] Such as Image 6 As shown, it is a flow chart of the steps of the method for detecting abnormal behavior access on the World Wide Web provided by Embodiment 2 of the present invention. The method includes the following steps:
[0145] Step 201, receiving an access log.
[0146] In this step, access logs can be received in units of one day.
[0147] Step 202, judging whether the time threshold is reached.
[0148] It is judged whether the time span of the received access log reaches a time threshold, for example, 30 days. If yes, go to step 204; otherwise, go to step 203.
[0149] Step 203, determine or update the directed graph of historical service trunks.
[0150] In this step, the directed graph of historical service backbones may be determined or updated according to the received access logs. Specifically, the directed graph of historical business trunks may be stored in the database.
[0151] Step 204, determine volatility.
[0152] When the time span reache...
Embodiment 3
[0175] Such as Figure 7 As shown, it is a schematic structural diagram of a detection device for abnormal behavior access on the World Wide Web provided by Embodiment 3 of the present invention. The device can be applied to the server side. The device includes a receiving module 11, a detection module 12 and a marking module 13, wherein:
[0176] The receiving module 11 is used to obtain the access log and determine the temporary business directed graph;
[0177] The detection module 12 is used to determine the same access path as a normal access path between the destination page node and the starting page node of an access path in the historical business trunk directed graph in the temporary service directed graph; and, determine the temporary Whether the access paths starting from the same node in the business directed graph and the historical business backbone directed graph are the same;
[0178] The marking module 13 is configured to determine that the temporary access ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com