A Data Security Monitoring System
A monitoring system and data security technology, applied in the field of network security, can solve the problems of accessible IP addresses and user name restrictions, and achieve the effect of ensuring data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
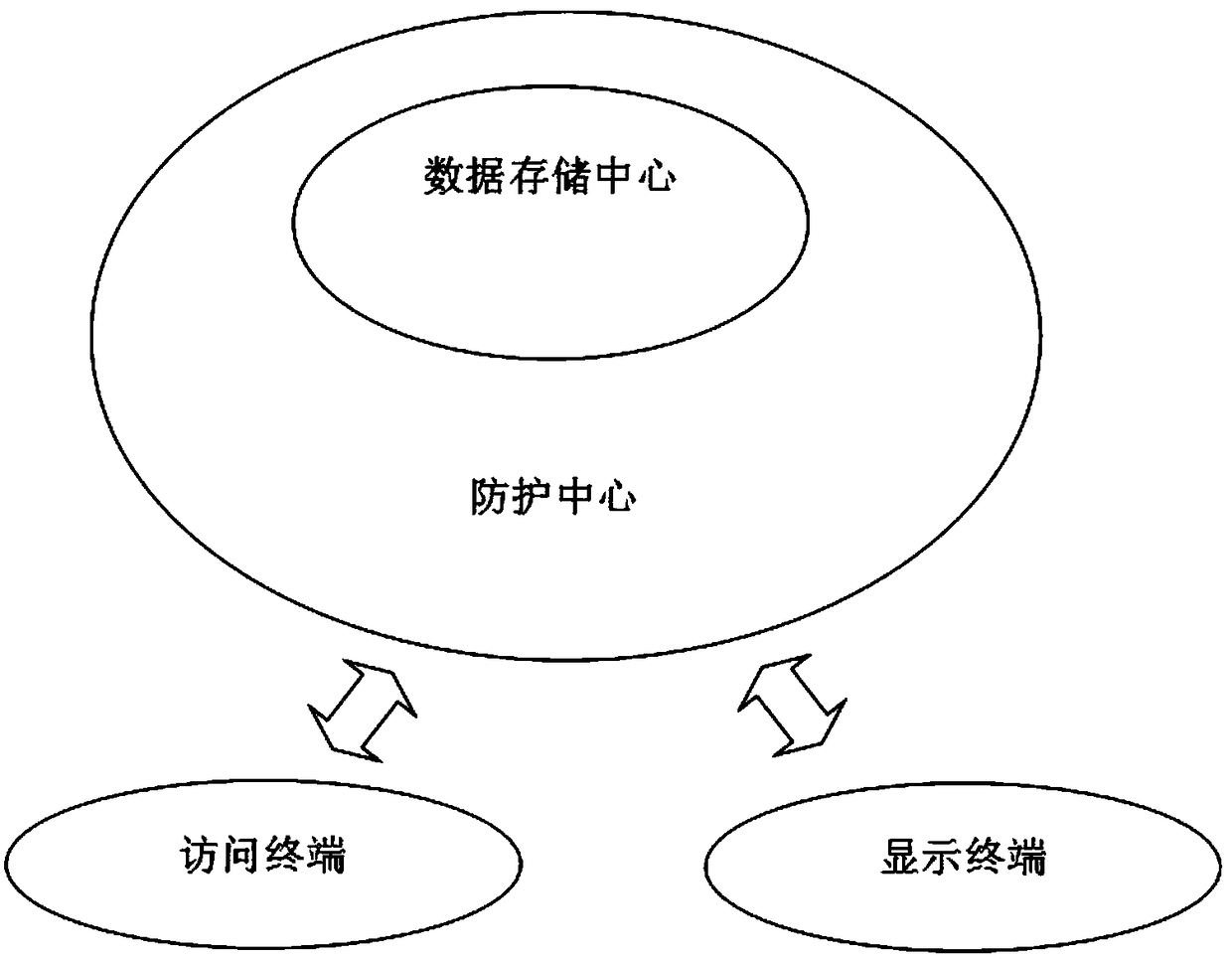
[0017] Such as figure 1 As shown, a data security monitoring system includes a data storage center, an access terminal, a protection center and a display terminal, the data storage center is used to store important data files; the protection center includes a protection database and an authentication terminal for The data storage center is protected to prevent illegal access from reading and writing data; the access terminal includes a request sending end for sending access request instructions during access; the display terminal is used for displaying data and interface frames.
[0018] It is worth noting that the protection database is used to store the IP range of the visitors and the username of the visitors, and the IP range of the visitors includes the red IP list and the black IP list.
[0019] In addition, the authentication terminal includes an IP verifier and an identity card issuing end, the IP verifying end is used to verify whether the visitor's IP meets the IP re...
Embodiment 2
[0021] Such as figure 1 As shown, a data security monitoring system includes a data storage center, an access terminal, a protection center and a display terminal, the data storage center is used to store important data files; the protection center includes a protection database and an authentication terminal for The data storage center is protected to prevent illegal access from reading and writing data; the access terminal includes a request sending end for sending access request instructions during access; the display terminal is used for displaying data and interface frames.
[0022] It is worth noting that the protection database is used to store the IP range of the visitors and the username of the visitors, and the IP range of the visitors includes the red IP list and the black IP list.
[0023] In this embodiment, the authentication terminal includes an IP verifier and an identity card issuer, the IP verifier is used to verify whether the visitor's IP meets the IP requi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com