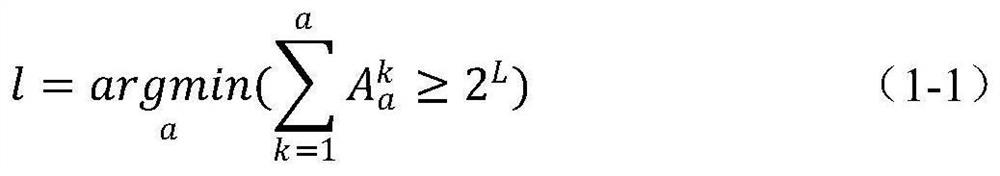Information hiding method based on forwarding mechanism of social software users' dynamic messages
A dynamic message and social software technology, applied in the field of information hiding, can solve the problem of no social network secret information transmission, etc., and achieve the effect of avoiding statistical anomalies and effective secret information transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] Below in conjunction with specific embodiment, further illustrate the present invention.
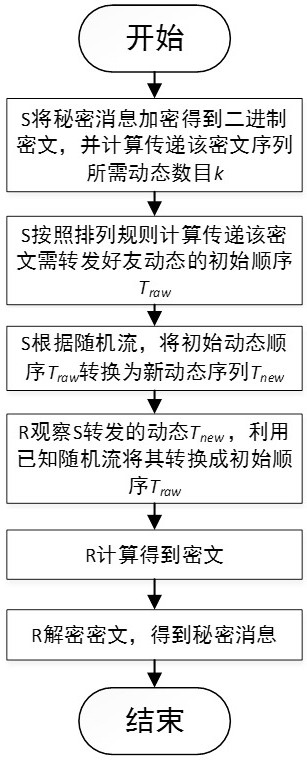
[0046] Message sender S:
[0047] Step 1: S calculates the dynamic number l required to transmit the L-bit binary ciphertext sequence m=[0, 0, 1, 1, 1, 0], the calculation formula is shown in (1-1), when L=6 , l=4.
[0048] Step 2: S calculates the forwarding order T of transmitting ciphertext m according to the arrangement rules agreed with R raw .
[0049] Specifically include the following sub-steps:
[0050] Step 2.1: S converts the ciphertext m into decimal d=14.
[0051] Step 2.2: S calculates that the transfer ciphertext m should be in T list ={t 1 , t 2 , t 3 , t 4} The number k selected in the order v in a permutation. According to the formulas (2-1) (2-2), when d=14, k=2 and v=10 are obtained, which means selecting the 10th type of permutations that can be formed by selecting 2 of the 4 dynamics.
[0052] Step 2.3: According to the arrangement rules agreed w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com