Block chain based key storage, updating method, apparatus, apparatus and medium
A technology for key storage and key update, applied in the fields of equipment and media, blockchain-based key storage, device, and update method, can solve the problems of potential security risks and easy leakage of keys, so as to avoid potential security risks. , the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
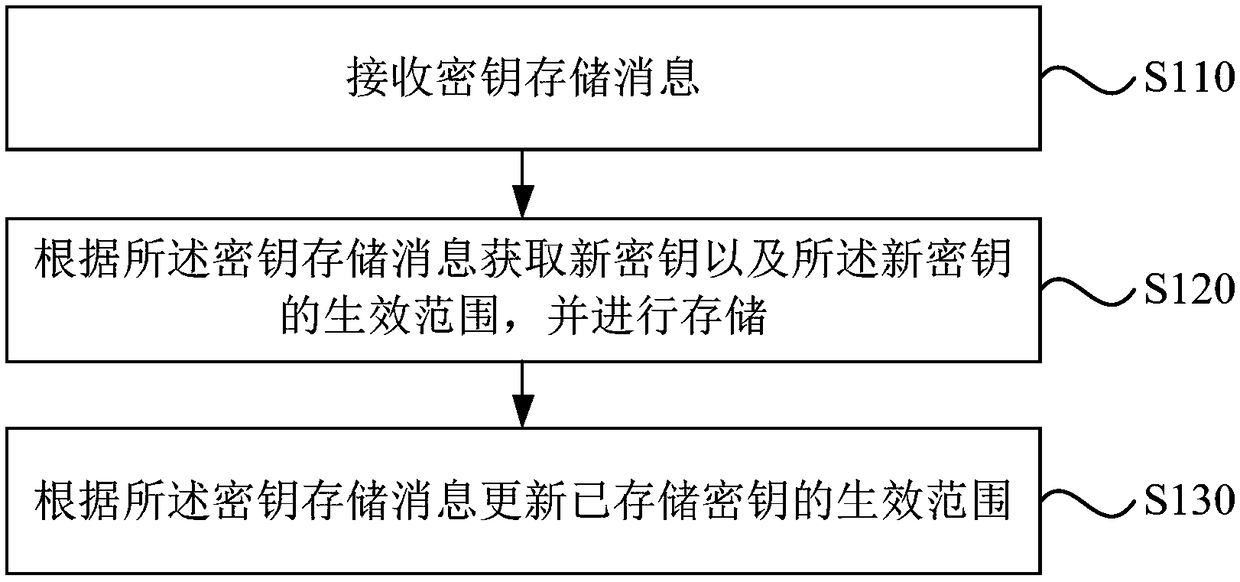
[0043] figure 1 It is a flow chart of a blockchain-based key storage method in Embodiment 1 of the present invention. The embodiment of the present invention is applicable to the case where an electronic device needs to be used as a central controllable device to control the blockchain network, and the key to be used is provided to the blockchain node for storage. It is implemented by a key storage device, which is implemented by software and / or hardware, and is specifically configured in an electronic device carrying a blockchain node. Of course, those skilled in the art should also understand that the keys to be stored are not limited to those provided by the central controllable device, but can also be keys that need to be used in any blockchain network, and the issuer of the key can be any blockchain node .
[0044] Such as figure 1 The blockchain-based key storage methods shown include:
[0045] S110. Receive a key storage message.
[0046] Wherein, the key storage m...
Embodiment 2
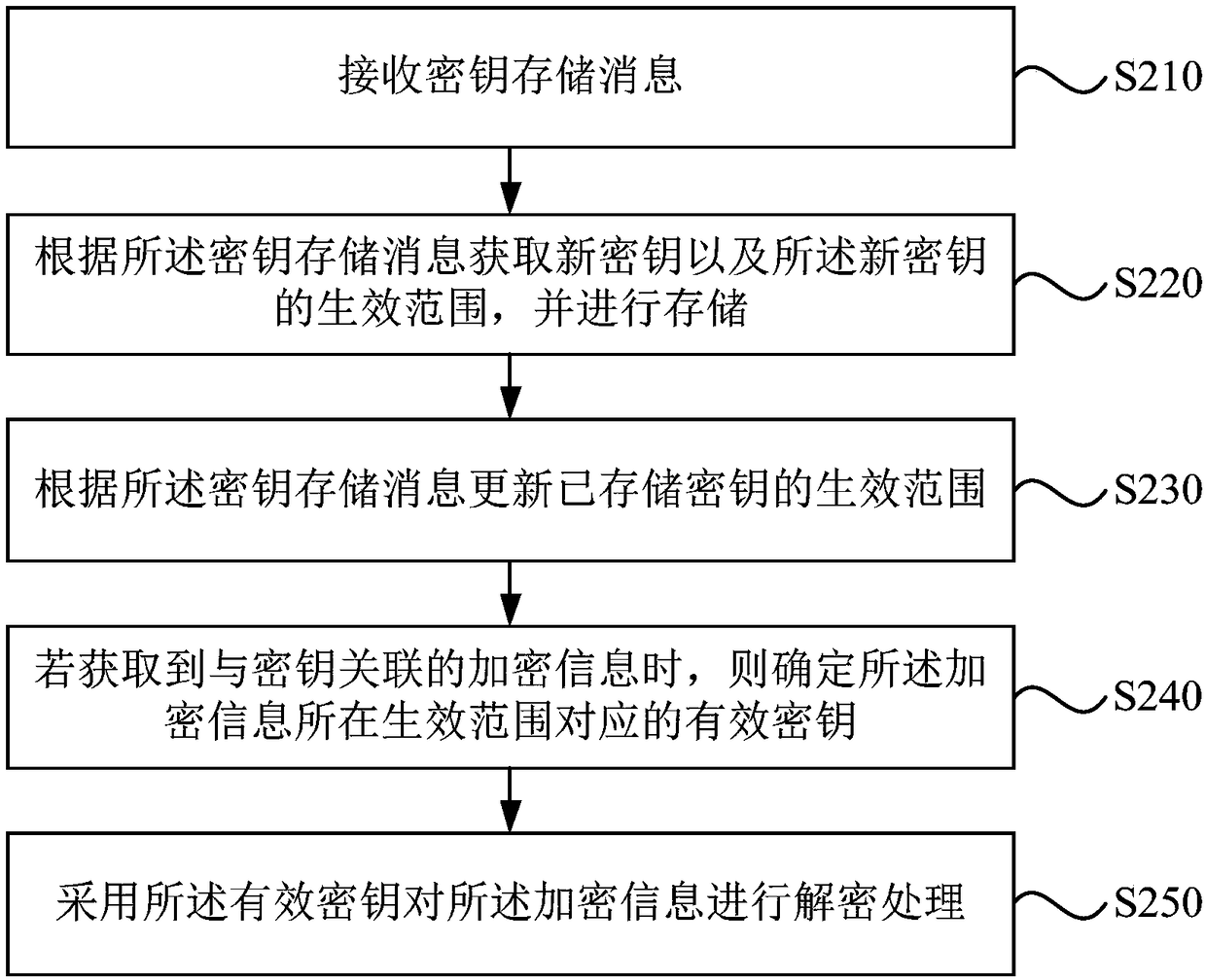
[0066] figure 2 It is a flow chart of a blockchain-based key storage method in Embodiment 2 of the present invention. The embodiments of the present invention perform additional optimization on the basis of the technical solutions of the foregoing embodiments.
[0067] Further, after the operation "acquire the new key and the effective range of the new key according to the key storage message, and store it", add "if the encrypted information associated with the key is obtained, determine the The effective key corresponding to the effective range of the encrypted information; use the effective key to decrypt the encrypted information", so as to interact with the device sending the encrypted information through the key.
[0068] Preferably, the device sending encrypted information is an electronic device carrying a blockchain network node.
[0069] Such as figure 2 A blockchain-based key storage method is shown, including:
[0070] S210. Receive a key storage message.
[...
Embodiment 3
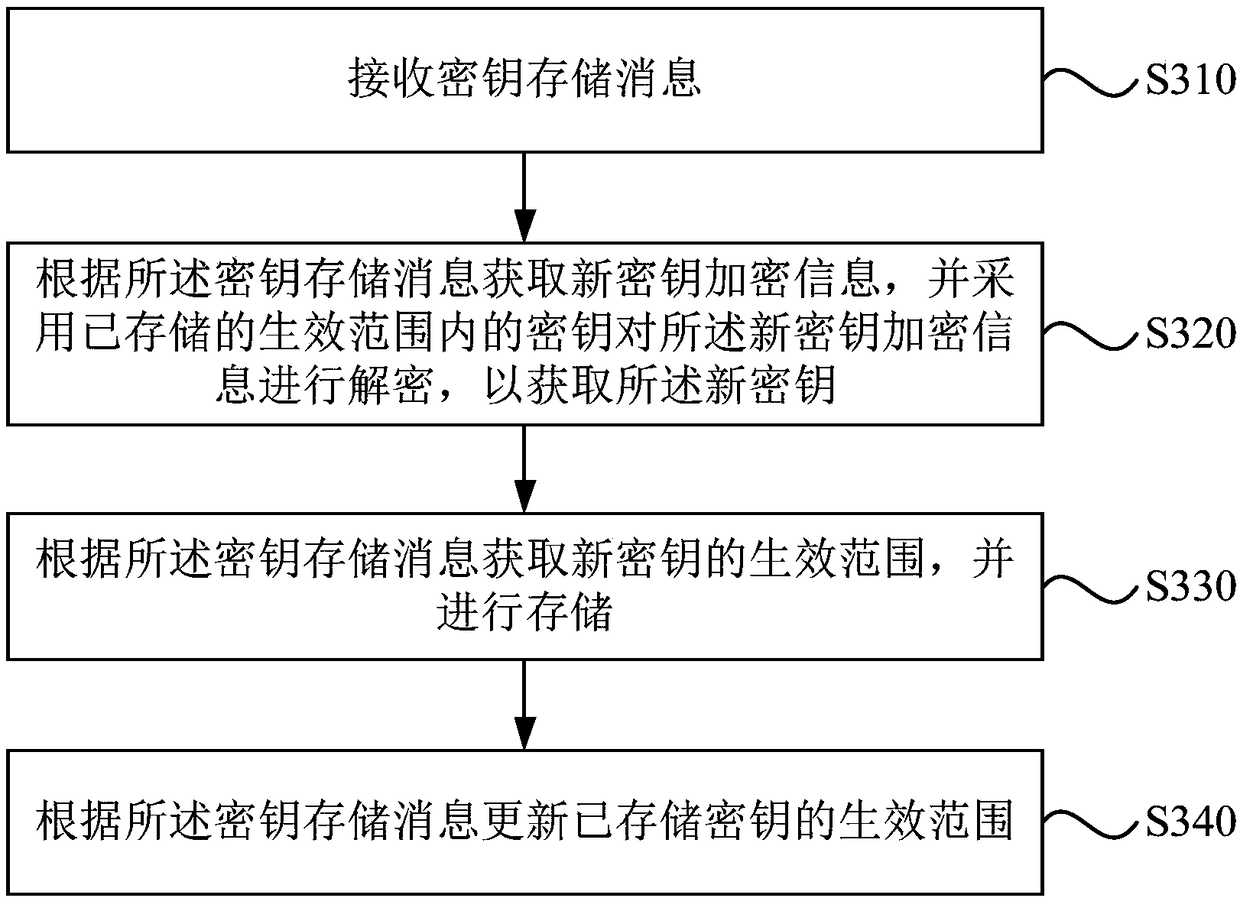
[0095] image 3 It is a flow chart of a blockchain-based key storage method in Embodiment 3 of the present invention. The embodiments of the present invention are optimized on the basis of the technical solutions of the foregoing embodiments.
[0096] Further, "obtain a new key according to the key storage message" is refined into "acquire the encryption information of the new key according to the key storage message, and use the stored key within the valid range to pair the new key Key encryption information is decrypted to obtain the new key", so as to enhance the security of the new key during transmission.
[0097] Such as image 3 The blockchain-based key storage methods shown include:
[0098] S310. Receive a key storage message.
[0099] In order to ensure the security of the new key distribution process, the central controllable device encrypts the key storage message including the new key with the historical key to generate a new key encrypted message; the new key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com