Identification method and device for junk short messages and storage medium
A technology of spam SMS and identification method, applied in the field of communication, can solve the problems affecting the accuracy of the identification system, calibration errors, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
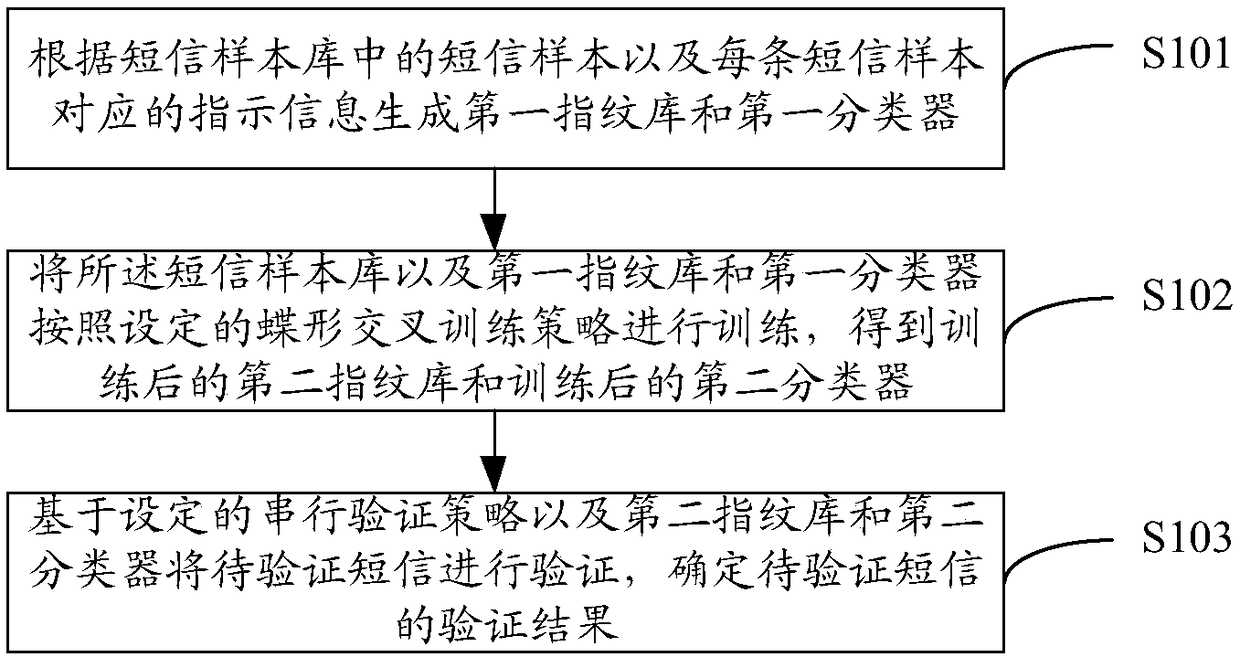
[0061] see figure 1 , which shows a method for identifying spam messages provided by an embodiment of the present invention, the method can be applied to a network device having a spam message identification function or a requirement for identifying spam messages, and the method may include:
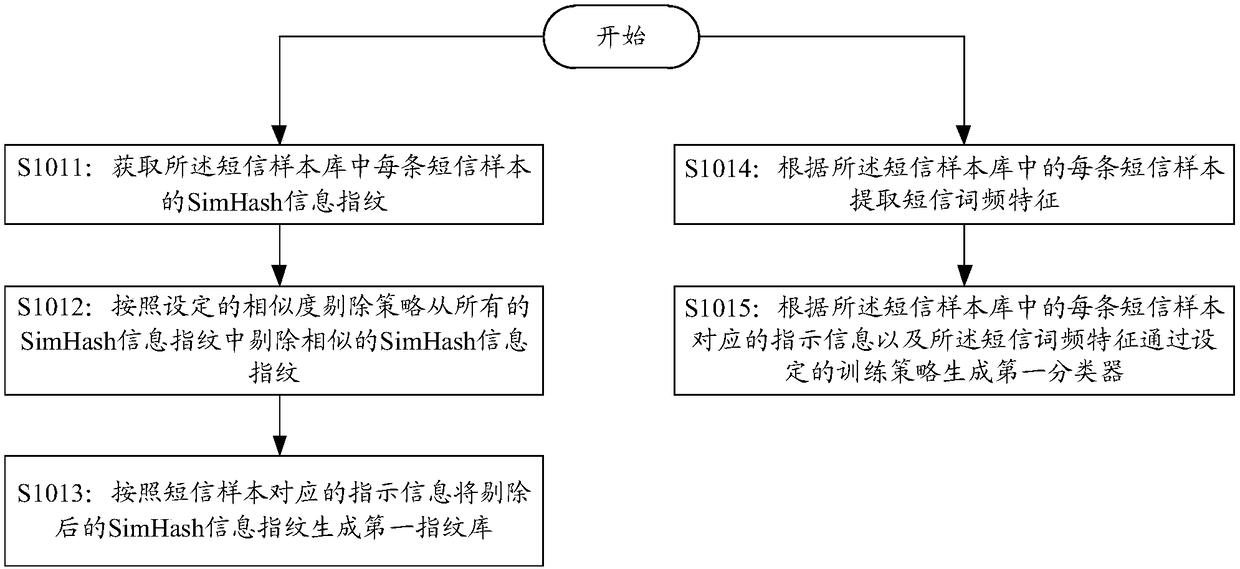
[0062] S101: Generate a first fingerprint database and a first classifier according to the short message samples in the short message sample database and the instruction information corresponding to each short message sample;
[0063] Wherein, the indication information is used to indicate whether the short message sample is a spam short message;
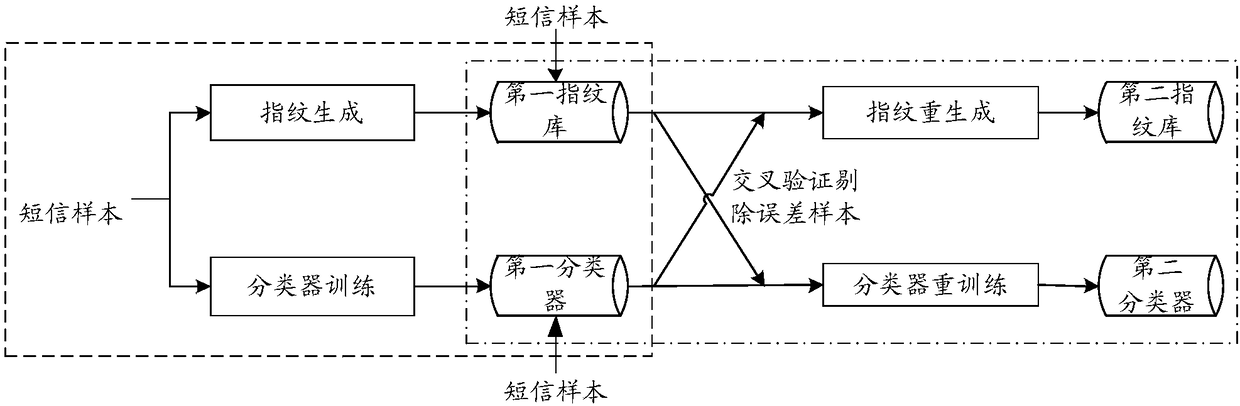
[0064] S102: Train the SMS sample library, the first fingerprint library and the first classifier according to the set butterfly cross-training strategy to obtain the trained second fingerprint library and the trained second classifier;
[0065] S103: Verify the short message to be verified based on the set serial verification strategy, the s...
Embodiment 2
[0123] Based on the same technical idea of the foregoing embodiments, see Figure 8 , which shows a schematic structural diagram of a device 80 provided by an embodiment of the present invention, the device 80 may include:
[0124] A memory 801 storing a junk message identification program;
[0125] The processor 802 is configured to execute the junk message identification program to perform the following operations:
[0126] Generate the first fingerprint library and the first classifier according to the short message samples in the short message sample library and the indication information corresponding to each short message sample; Wherein, the indication information is used to indicate whether the short message sample is a junk message;
[0127] The short message sample library, the first fingerprint library and the first classifier are trained according to the set butterfly cross training strategy to obtain the trained second fingerprint library and the trained second...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com