Data encryption and decryption method, device and system
A data encryption and data technology, applied in the field of Internet technology applications, can solve problems such as complex computing and large workload, and achieve the effect of protecting data privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
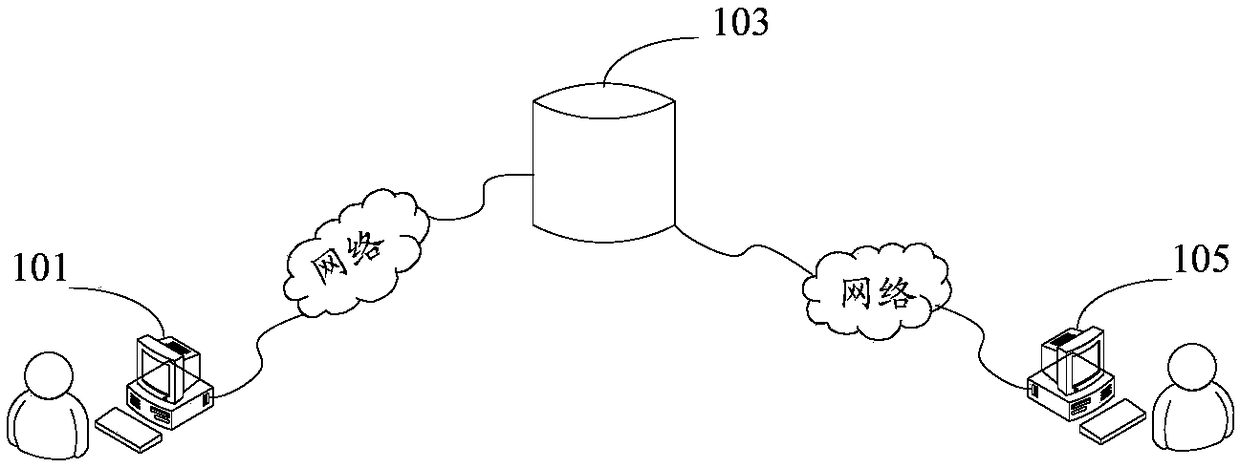
[0051] According to the embodiment of this application, a system embodiment of data encryption and decryption is provided. It should be noted that this embodiment can be applied to various blockchain application scenarios, including but not limited to payment, transfer, Stocks, securities, real estate, insurance, insurance, medical care, supply chain management and other industries.
[0052] With the development of Internet technology, electronic transactions such as online payment, transfer, and shopping have become more and more popular. Electronic transactions on the traditional Internet require the help of a trusted third-party credit institution to process electronic payment information, which is subject to the credibility of the third-party credit institution. Based on the principle of cryptography, the blockchain enables the two parties to pay directly without the participation of a third-party intermediary, ensuring the security of electronic transactions.
[0053] Th...
Embodiment 2
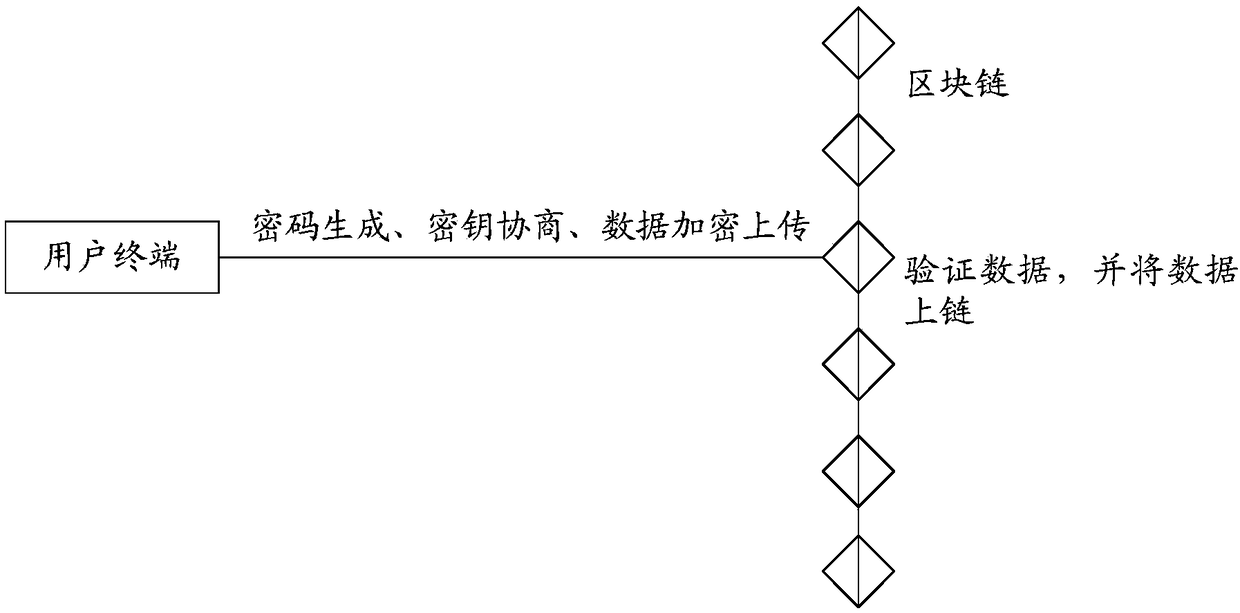
[0097] According to the embodiment of this application, an embodiment of a data encryption method is also provided. The data encryption method provided by this embodiment can be applied to the data encryption and decryption system provided by Embodiment 1 of this application, including but not limited to this The application scenario described in Example 1 of the application. It should be noted that the steps shown in the flowcharts of the accompanying drawings may be performed in a computer system, such as a set of computer-executable instructions, and that although a logical order is shown in the flowcharts, in some cases, The steps shown or described may be performed in an order different than here.
[0098] Since anyone can participate in the blockchain network, each device can be used as a node, and each node is allowed to obtain a complete copy of the database. Therefore, all data information on the blockchain is public. In order to protect the privacy and security of u...
Embodiment 3
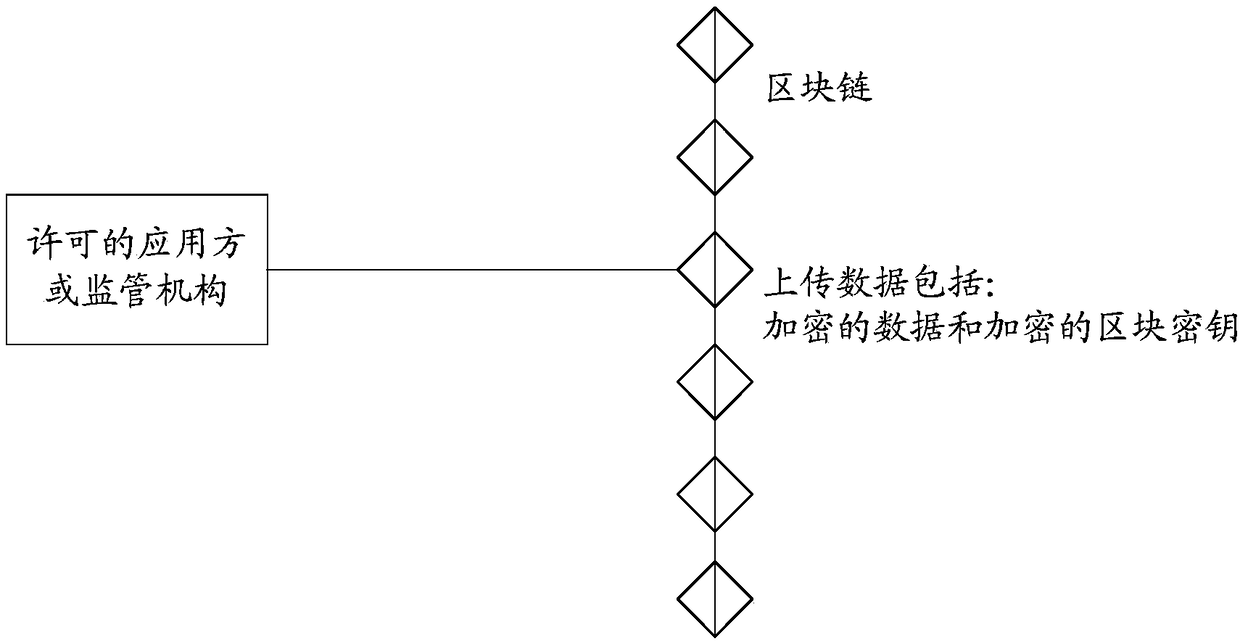
[0152] According to the embodiment of this application, an embodiment of a data decryption method is also provided. The data decryption method provided by this embodiment can be applied to the data encryption and decryption system provided by Embodiment 1 of this application, including but not limited to this The application scenario described in Example 1 of the application. As an optional embodiment, it can be used to decrypt the encrypted data obtained by the data encryption method in Embodiment 2. It should be noted that the steps shown in the flow chart of the accompanying drawings can be implemented in a computer such as a group of Instructions are executed in a computer system and, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
[0153] This application provides Figure 9 A method of data decryption is shown, Figure 9 is a flow chart of a data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com