Content delivery network security detection method and system
A content distribution network and security detection technology, applied in the field of content distribution network security detection methods and systems, can solve the problems of network risk hysteresis and passivity, achieve accurate and reliable analysis results, improve security, and protect legitimate interests.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
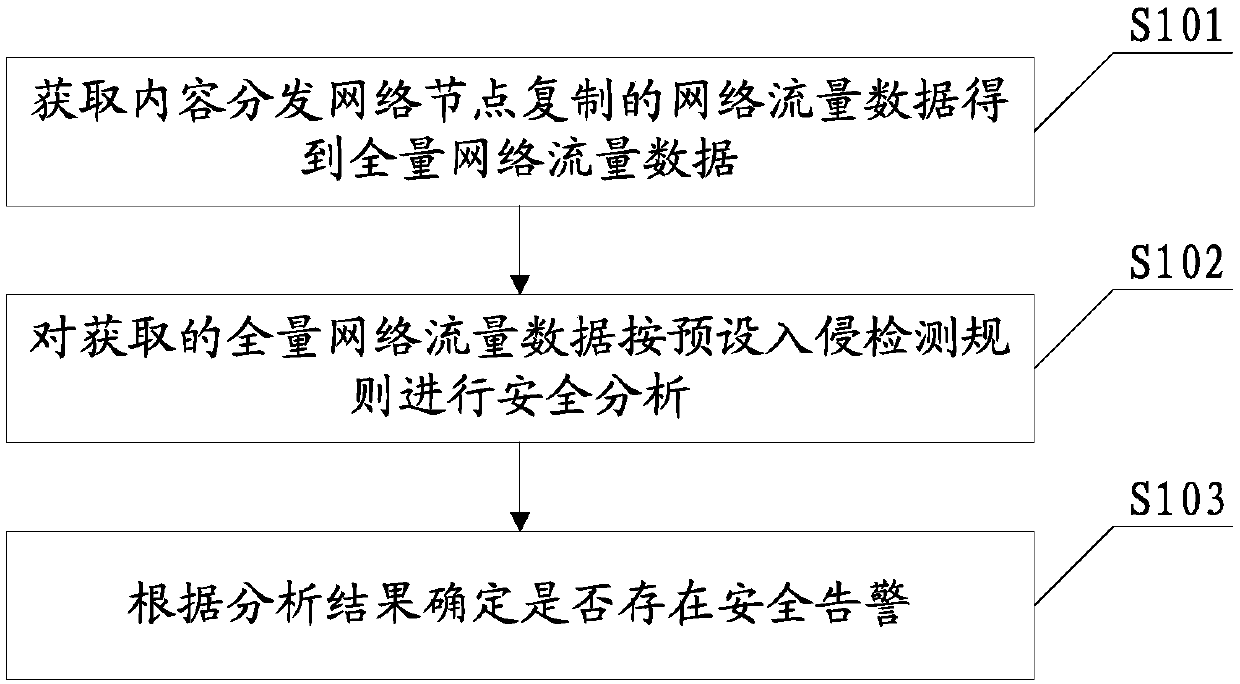
[0025] The content distribution network security detection method provided in this embodiment is applicable to a converged content distribution network. For the CDN (Content Delivery Network) node that needs to be detected, the CDN node needs to copy the traffic data forwarded by itself and send it to the node analysis device connected to the CDN node, so that the node analysis device can perform security analysis. In this embodiment, a node analysis device can be set up for each CDN node to be detected, so as to meet the timely and rapid analysis of a large amount of data. Of course, multiple CDN nodes can also share one node analysis device, which can be flexibly set according to specific needs. Specifically, on the node analysis device side, the content distribution network security detection method can be found in figure 1 shown, including:
[0026] S101: Obtain the network traffic data replicated by the CDN nodes to obtain the full amount of network traffic data.
[00...
Embodiment 2
[0066] This embodiment provides a content distribution network security detection system, see Figure 7 As shown, including a node analysis device 71 and a central server 72;
[0067] The node analysis device 72 is connected to the node of the content distribution network, and is used for obtaining the network flow data copied by the node of the content distribution network to obtain the full amount of network flow data, and for intruding the obtained network flow data according to the preset obtained from the central server The detection rules conduct security analysis, and determine whether there is a security alarm based on the analysis results.
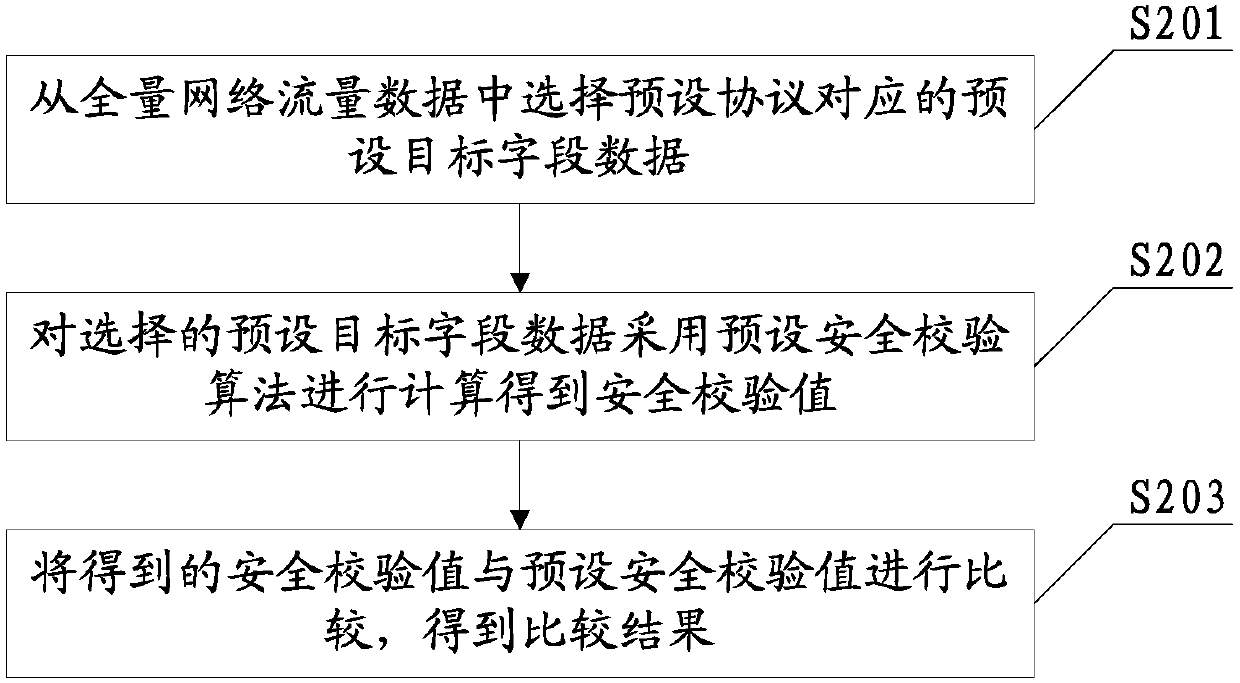
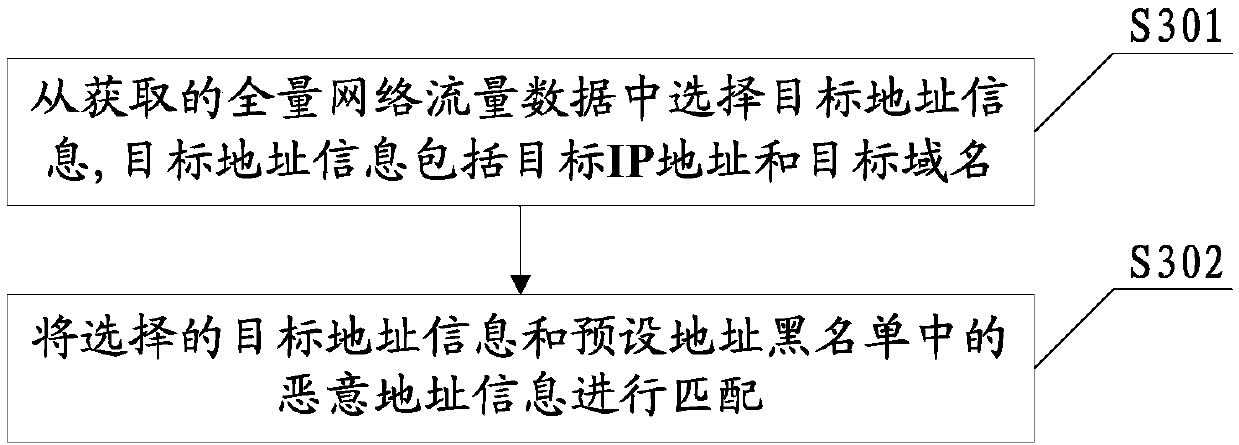
[0068] The preset protocol in this embodiment may be Hypertext Transfer Protocol (HyperText Transfer Protocol, http), HTTPS (Hyper Text Transfer Protocol over Secure Socket Layer) protocol, and the like. The target field data in this embodiment includes but not limited to IP address, text string, host name, email address, file na...
Embodiment 3
[0087] In order to better understand the present invention, this embodiment further describes the present invention in combination with a converged CDN system. see Figure 8 As shown, the node analysis device includes a flow collection module 81 and an intrusion detection module 82;
[0088] The traffic collection module 81 is deployed on the CDN node in a bypass, collects traffic data, stores it, generates information such as sessions and statistics, and transmits (periodically, or using other transmission rules) to the information collector module of the central analysis device.
[0089] Intrusion detection module 82: Deployed on the side of the traffic collection module to analyze traffic information in real time, and judge whether the traffic is a security threat according to the preset intrusion detection rules in the rule base.
[0090] Central analysis equipment includes:
[0091] The information collection module 83 is used to collect the log information from the CDN...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com