A program anomaly analysis method based on dynamic taint propagation
A technology of program exception and analysis method, which is applied in the field of network security, can solve problems such as staying on the surface, insufficient analysis depth, inability to deal with packing confusion, anti-debugging ability target software, etc., and achieve the effect of improving analysis efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
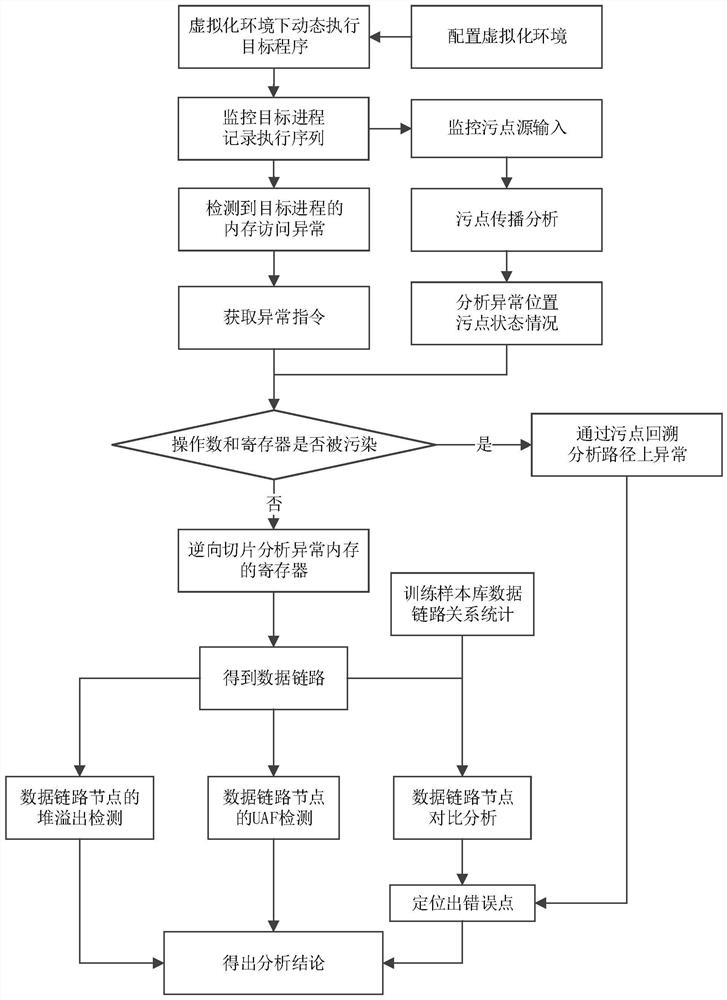
[0033] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in further detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
[0034] like figure 1 As shown, a program anomaly analysis method based on dynamic taint propagation, including steps:
[0035] 1. Configure the virtualization environment
[0036] The present invention adopts the dynamic virtualization technology. Firstly, it is necessary to install the virtual machine operating system for running the target program, install and deploy the target program in the virtual machine operating system, import the input data files that cause abnormalities, and configure the required software and hardware environment for operation. network environment and other conditions.
[0037] 2. Dynamically run the target program
[0038] The present invention adopts a dynamic analysis method, uses a virtu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com