Memory leak analysis method and related device
A memory leak and analysis device technology, applied in the computer field, can solve problems such as memory leaks and occupancy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
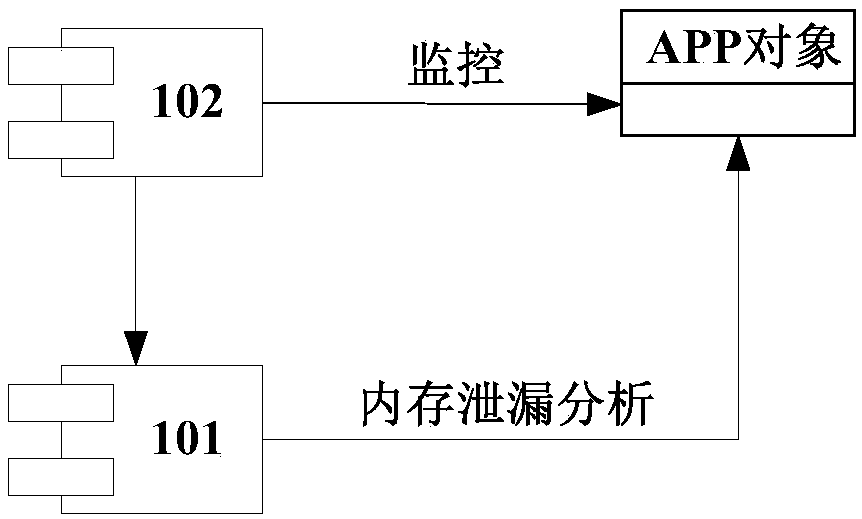
[0029] Generally, apps on mobile terminals may have memory leaks. Most memory leaks are caused by memory circular references. The memory leak analysis method and related devices (eg, memory leak analysis device, mobile terminal) provided by the present invention can perform memory leak analysis and locate objects with memory circular references.
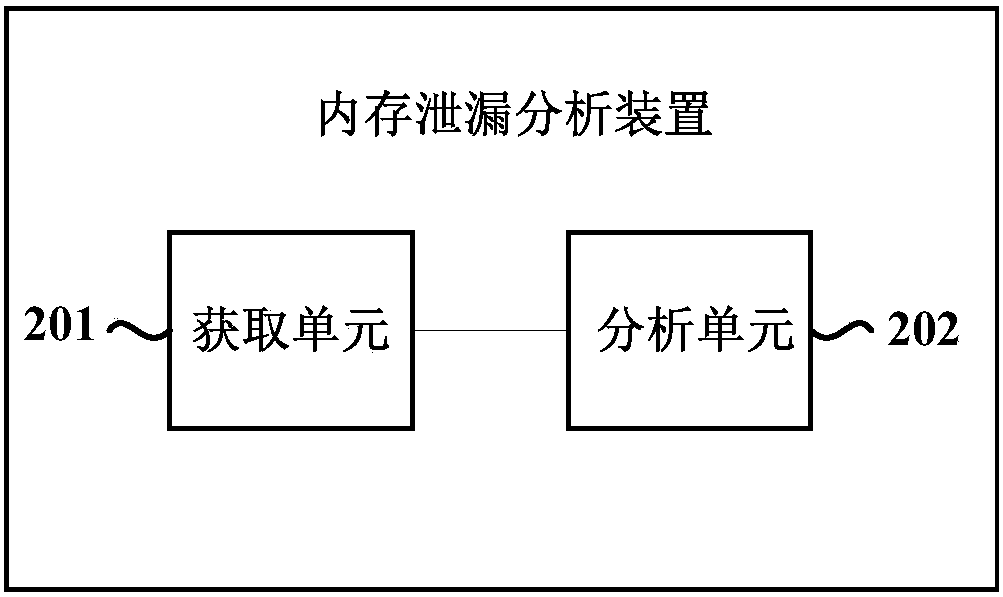
[0030] The memory leak analysis device can be applied in the mobile terminal in the form of software. When it exists in the form of software, the above-mentioned memory leak analysis device can be an independent APP, or can be used as a component of an APP or an operating system.
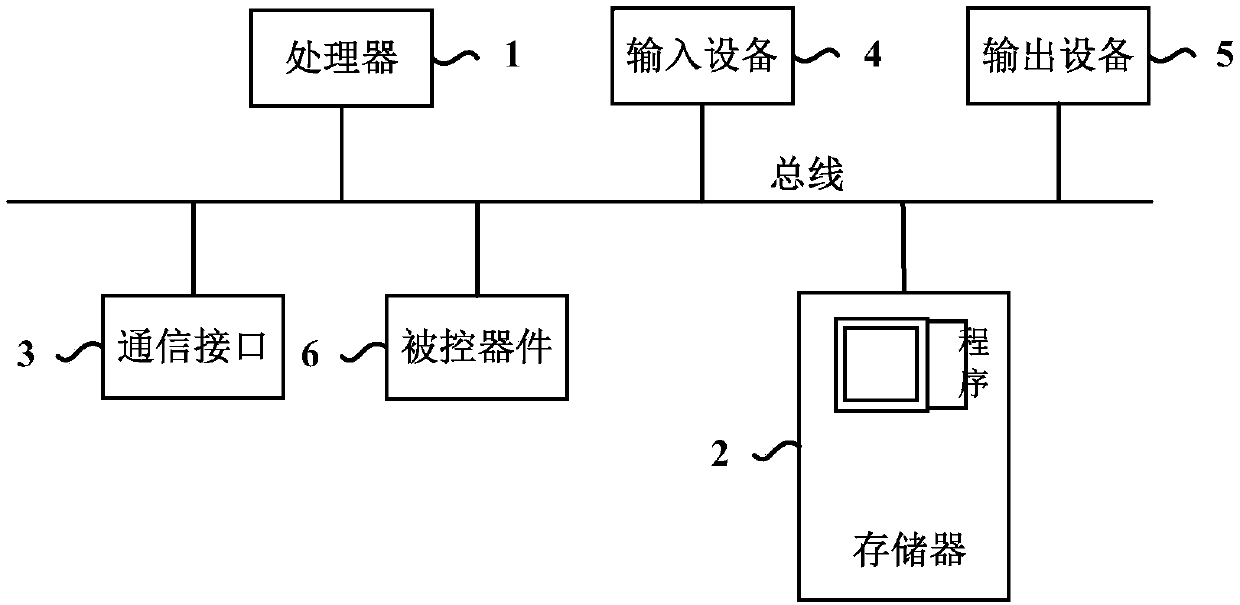
[0031] Alternatively, the above-mentioned memory leak analysis apparatus may be in the form of hardware as a component of the mobile terminal (for example, it may specifically be a controller / processor of the mobile terminal).
[0032] The above memory leak analysis method and related devices are applicable to the development and testing environment of mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com