Method of deterministic garbage collection
a garbage collection and deterministic technology, applied in the field of digital computer programming, can solve problems such as memory leakage, dangling pointers, and unnecessary exhaustion of memory available for executing programs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
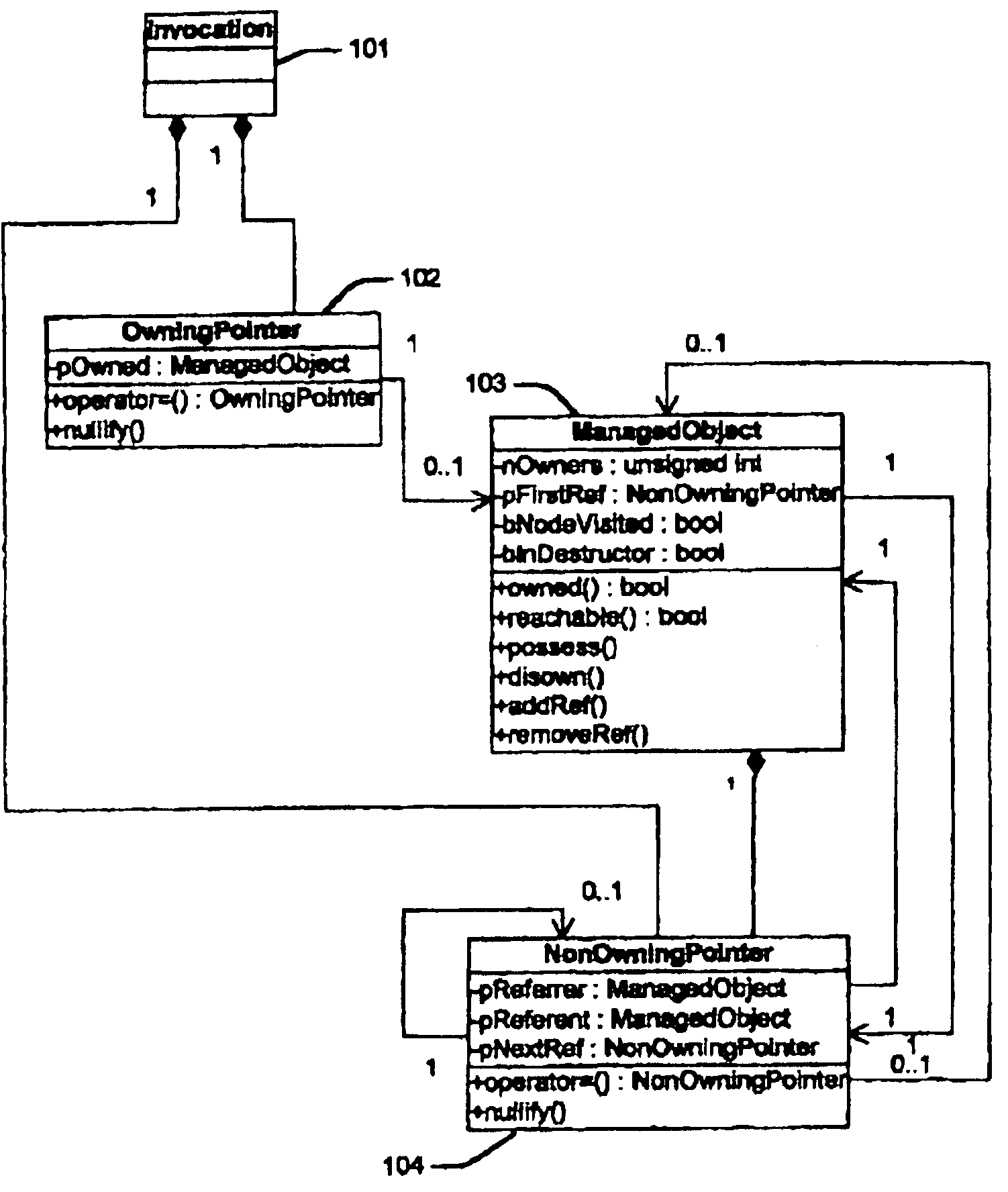
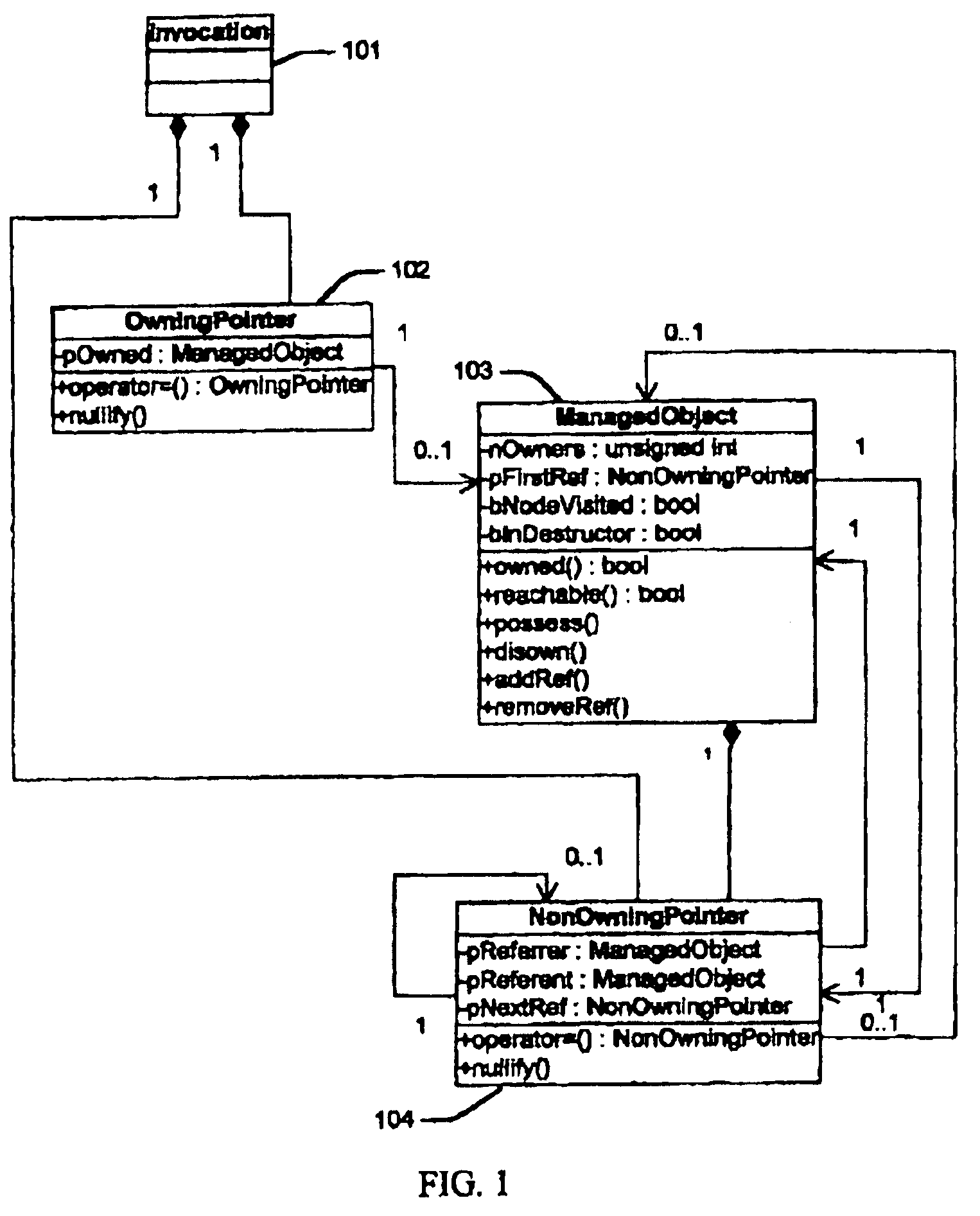
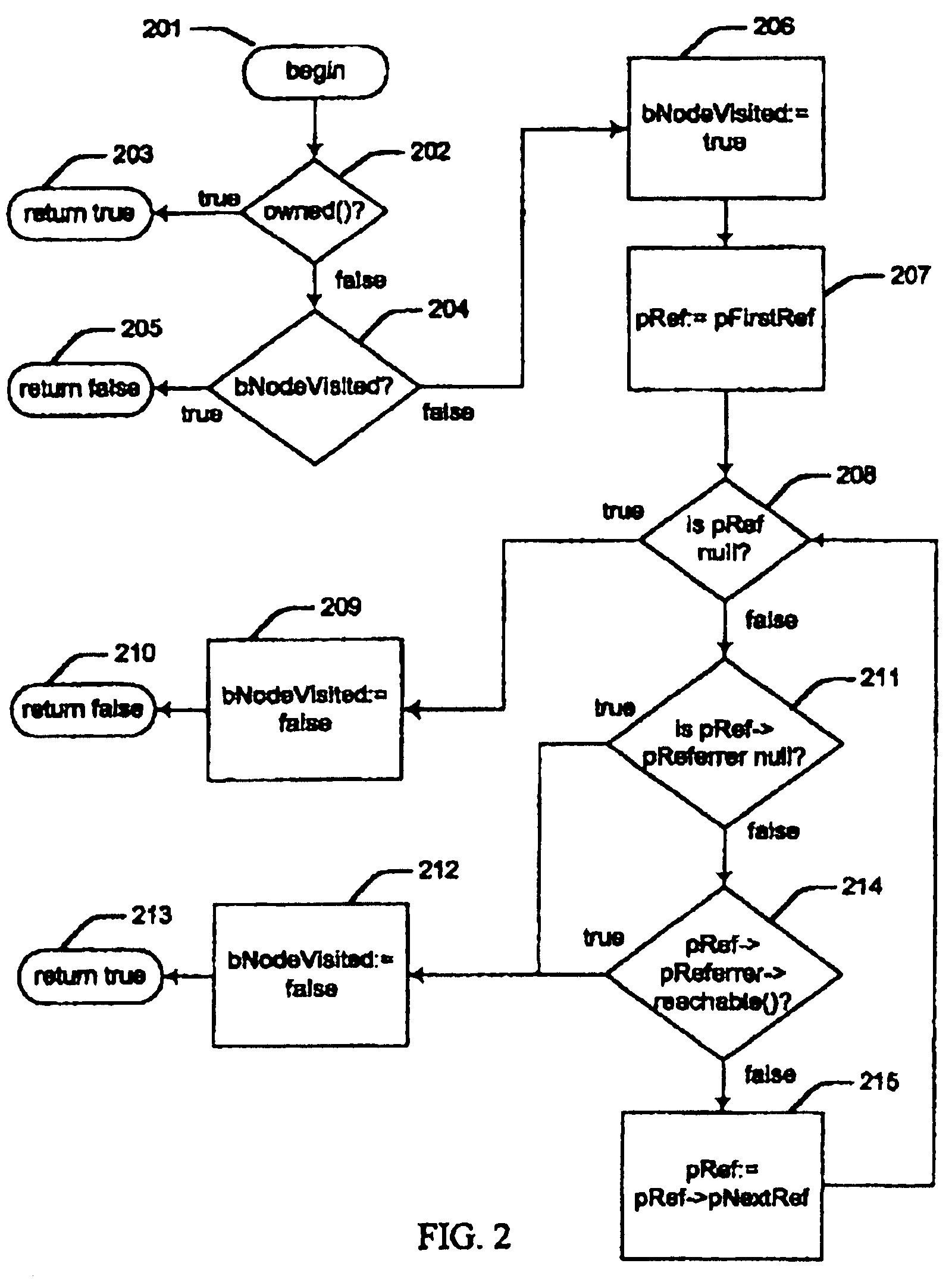
[0023]The present invention specifies an invocation, an owning pointer, a non-owning pointer, and a managed object. In the preferred embodiment, these are modeled using statements of an object-oriented programming language as classes with the names Invocation, OwningPointer, NonOwningPointer, and ManagedObject, respectively. FIG. 1 shows these classes using the graphical symbols of the Unified Modeling Language (UML), as defined by Rumbaugh, James, Ivar Jacobson, and Grady Booch, “The Unified Modeling Language Reference Manual,” Reading, Mass., Addison-Wesley, 1999, which is incorporated herein by reference.
[0024]An invocation is an invocation of a subroutine within a thread of a process of a system. An invocation ceases to exist when it is exited. An owning pointer is a pointer from an invocation to a managed object that establishes an ownership relationship between the invocation and the managed object. The owner of an owning pointer owns the managed object to which it points. A n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com