De-anonymization method and system by combining block chain and secret sharing
A technology of secret sharing and anonymization, which is applied in the field of combining blockchain and cryptography to achieve the effects of dynamic supervision, privacy protection, and deanonymization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
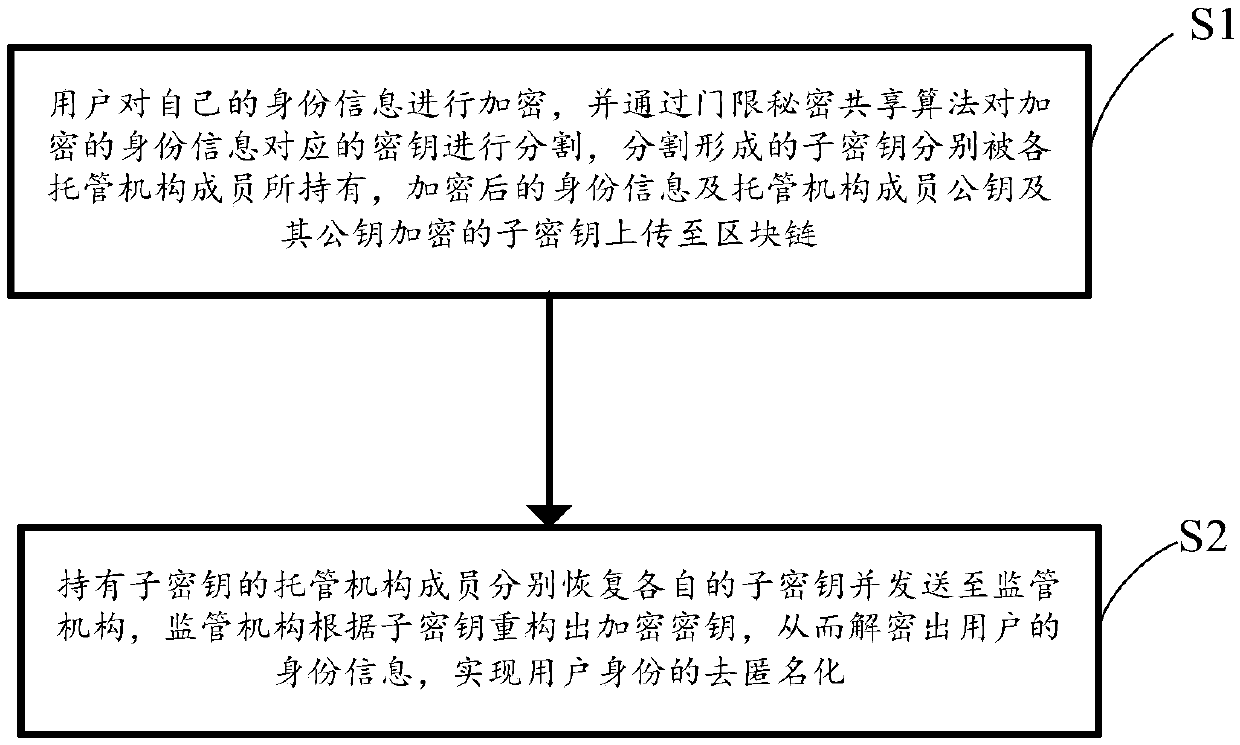
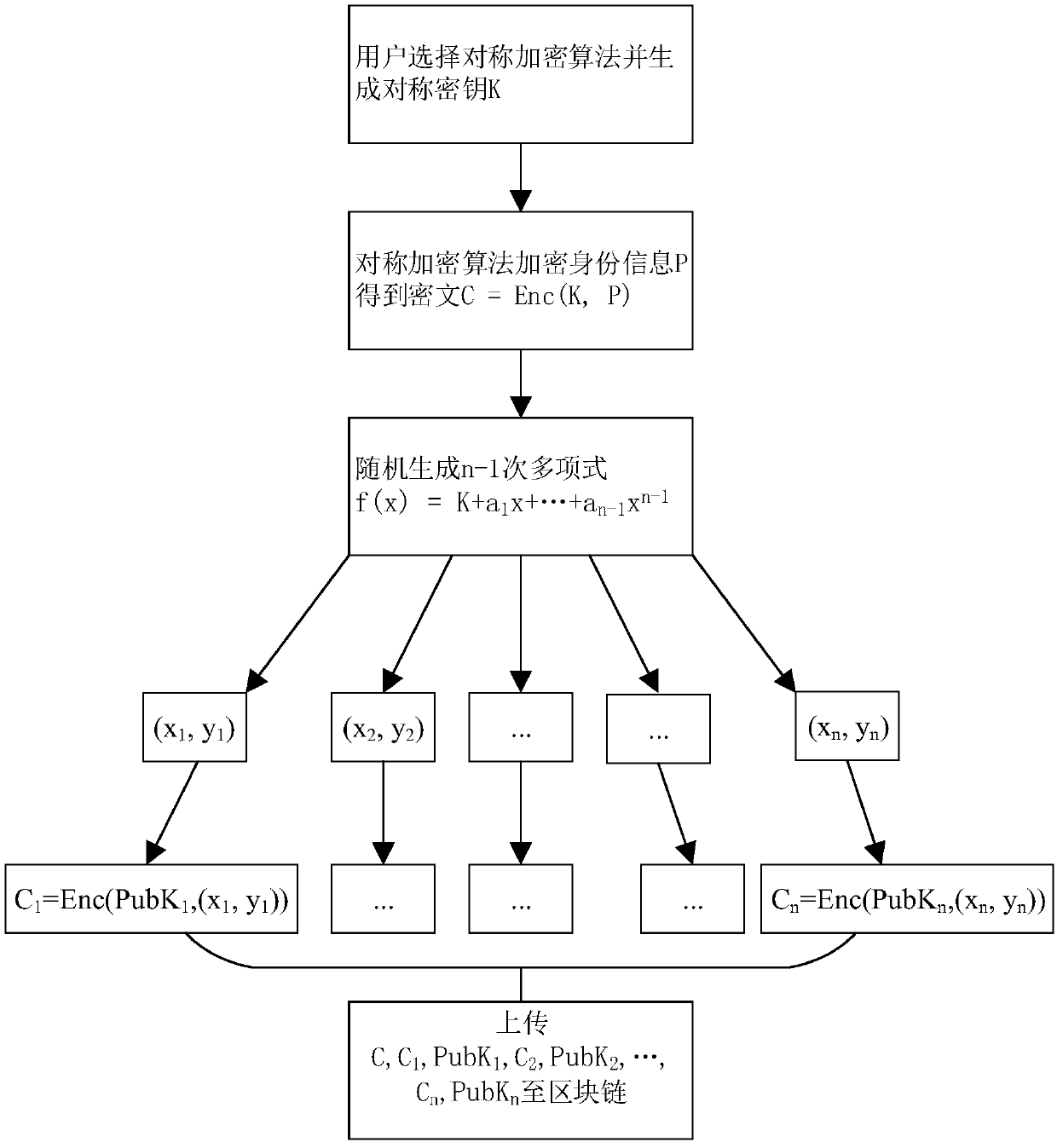
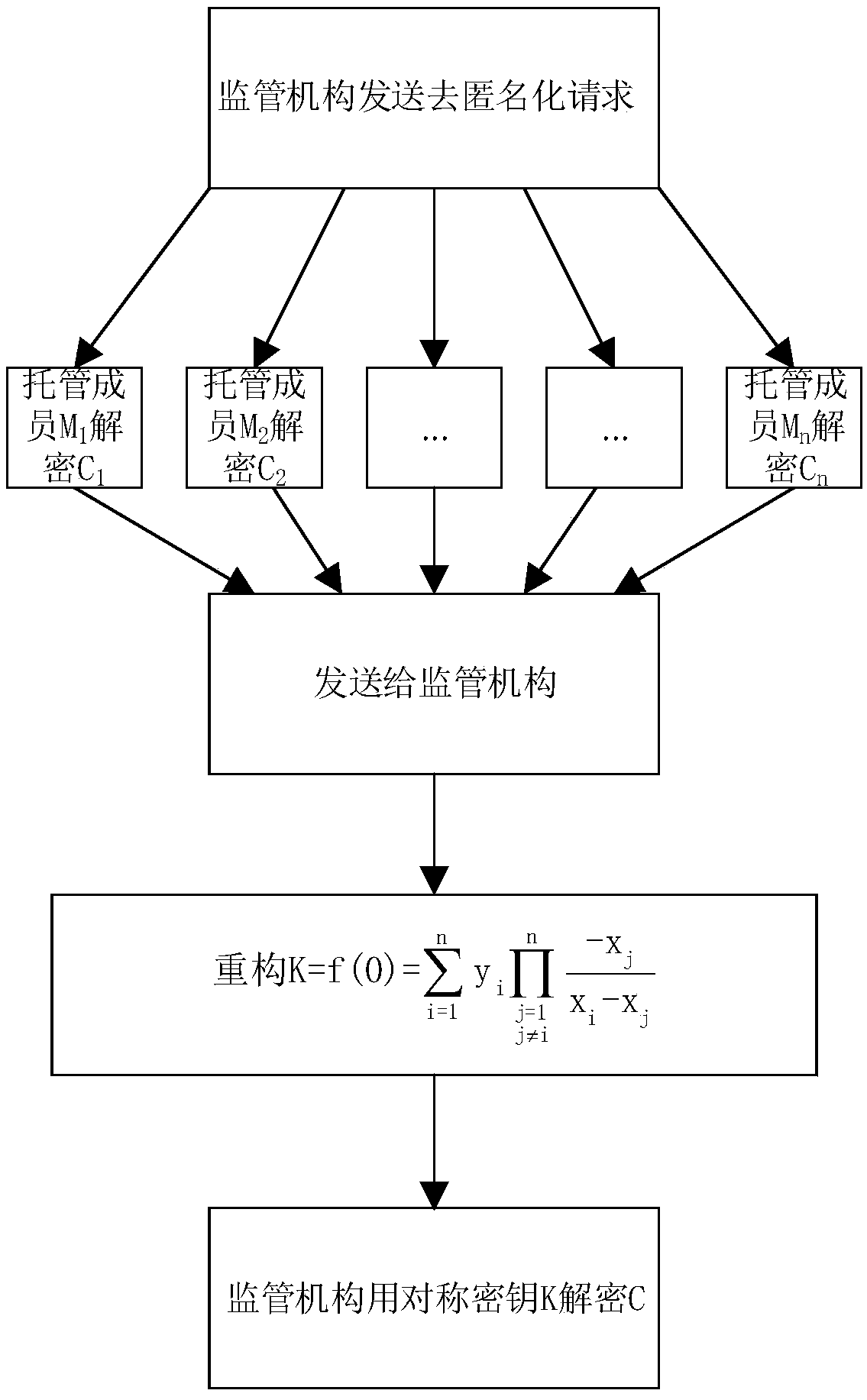
[0050] In order to enable those skilled in the art to better understand the technical solutions of the present invention, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0051]The basic scheme of a deanonymization method and system combining blockchain and secret sharing disclosed in the embodiment of the present invention is: the user generates a symmetric key locally and uses a symmetric encryption algorithm to encrypt his personal identity information and uploads it to the Blockchain to protect personal privacy; threshold secret sharing technology is used to realize the division of symmetric keys, and the divided encrypted sub-secrets are uploaded to the blockchain to realize the sharing of symmetric keys among members of the custodian organization; Under the joint action of the members of the institution, the symmetric key is recovered and the user identity information is decrypted to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com