Intelligent door lock identity authentication method and system, readable storage medium and mobile terminal
A smart door lock and identity authentication technology, which is applied in the field of communication security, can solve the problems of users' production and life troubles, easy to be monitored by hackers, threats to users' work or living safety, etc., and achieve the effect of improving security and preventing identity information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] It should be understood that the specific embodiments described here are only used to explain the present invention, but not to limit the present invention.
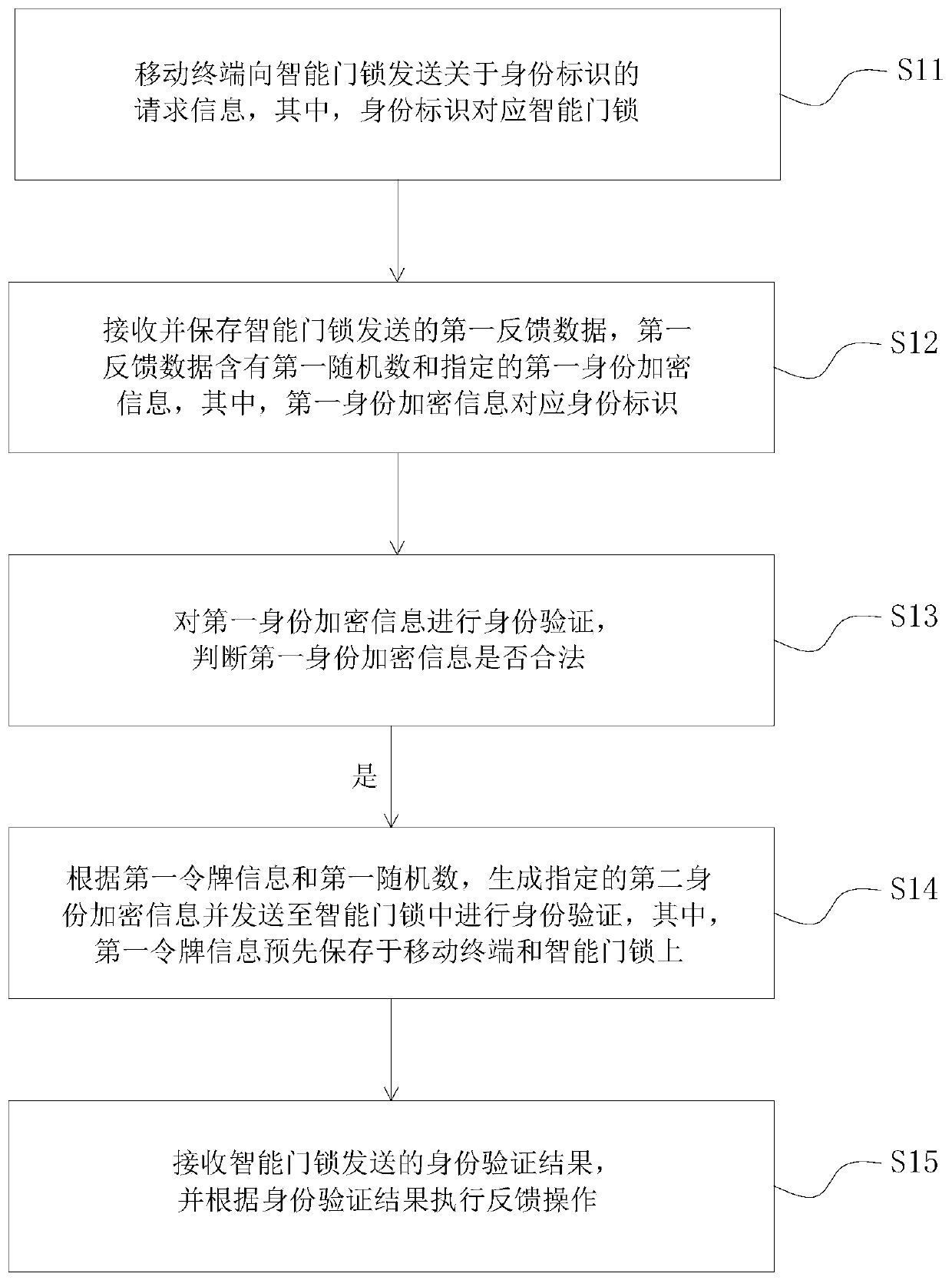
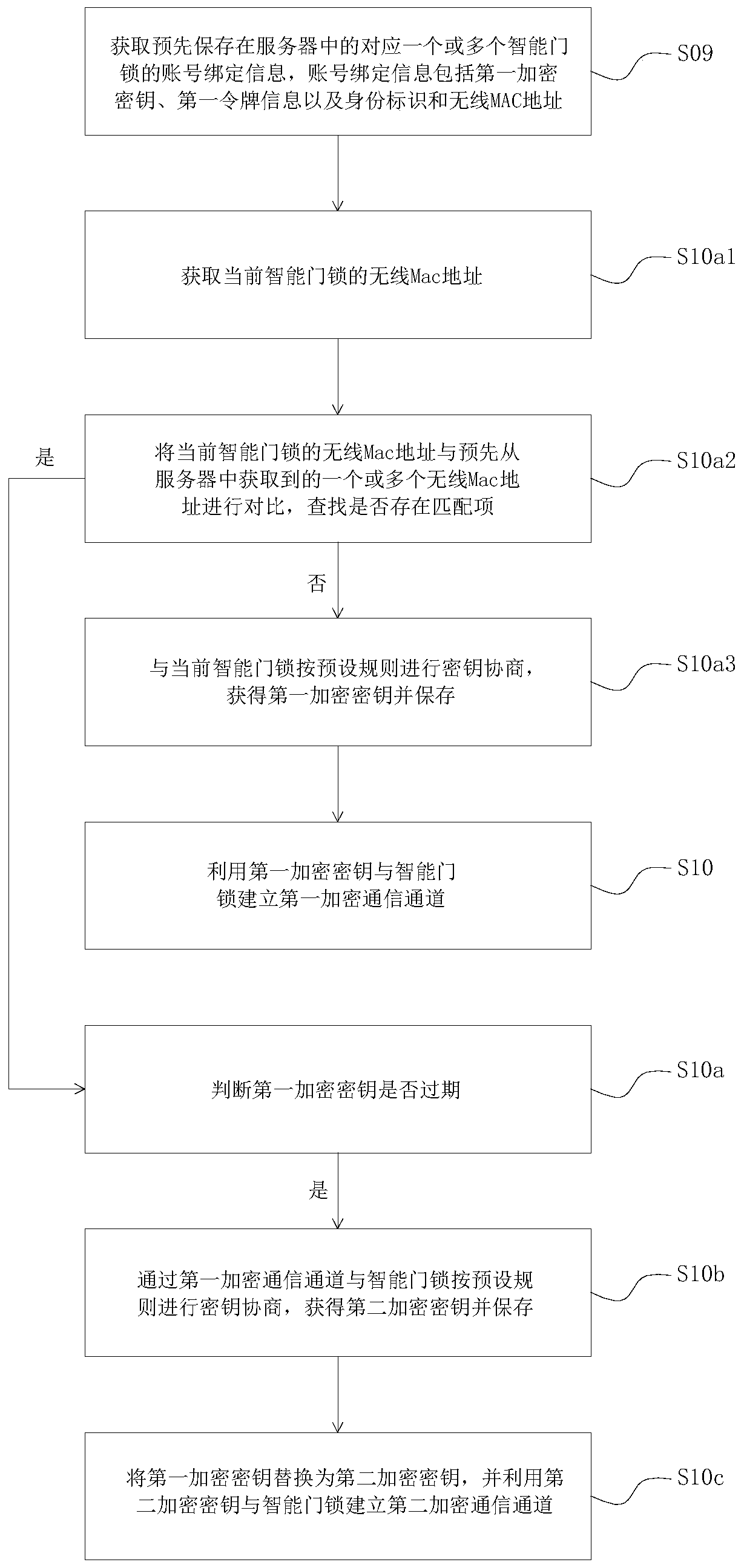
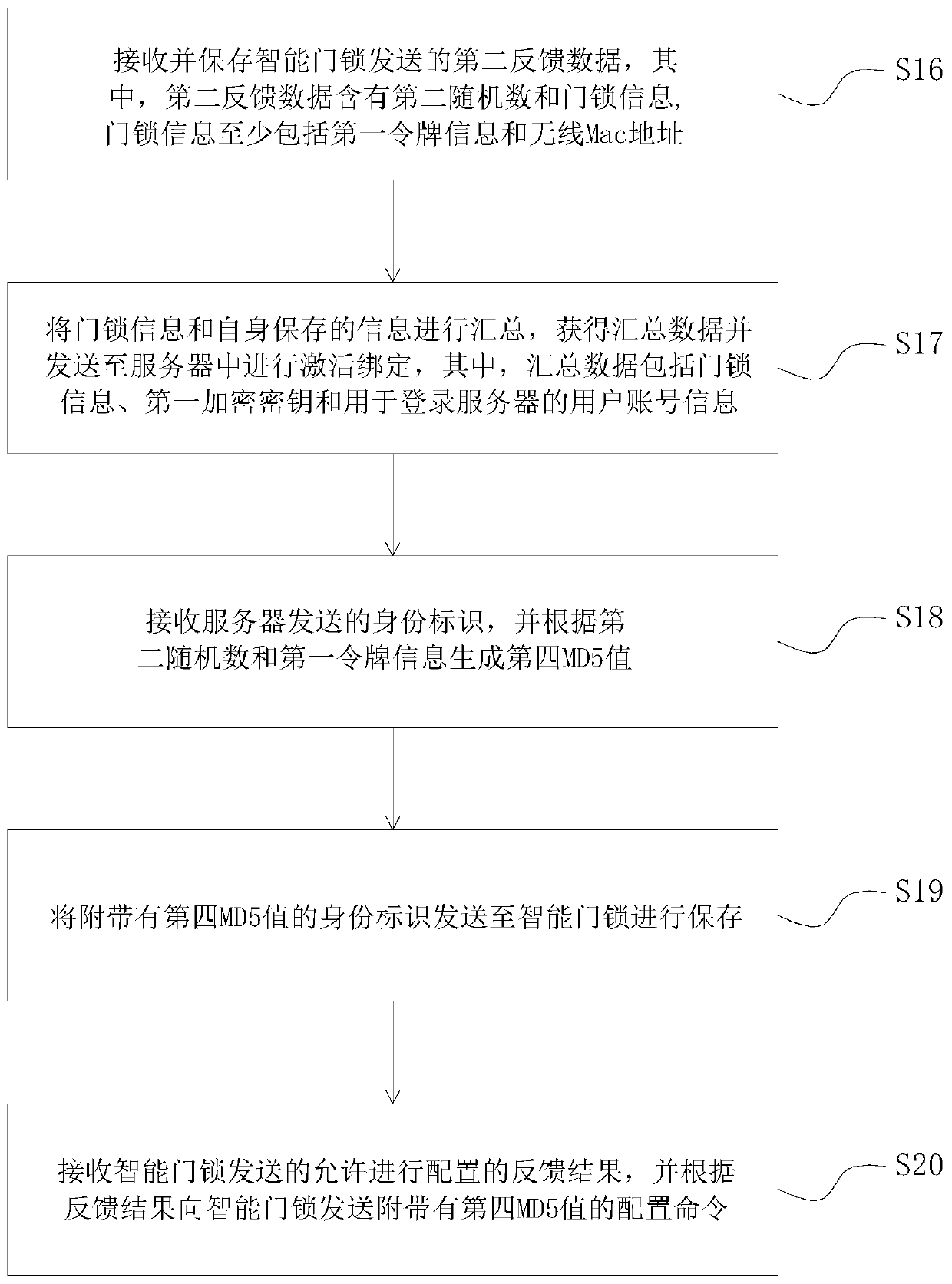
[0063] Reference figure 1 The present invention proposes a smart door lock identity authentication method. The smart door lock is in communication connection with a mobile terminal, and the mobile terminal is in communication connection with a server. The method includes the following steps:
[0064] S11: The mobile terminal sends request information about the identity identifier to the smart door lock, where the identity identifier corresponds to the smart door lock;
[0065] S12. Receive and save the first feedback data sent by the smart door lock, where the first feedback data contains a first random number and designated first identity encryption information, where the first identity encryption information corresponds to an identity identifier;
[0066] S13: Perform identity verification on the first identity encrypted...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com