Attack detection method and device and electronic device
An attack detection and attacked technology, applied in electrical components, payment circuits, instruments, etc., can solve the problem of not being able to detect attacks and asset losses in a timely manner
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
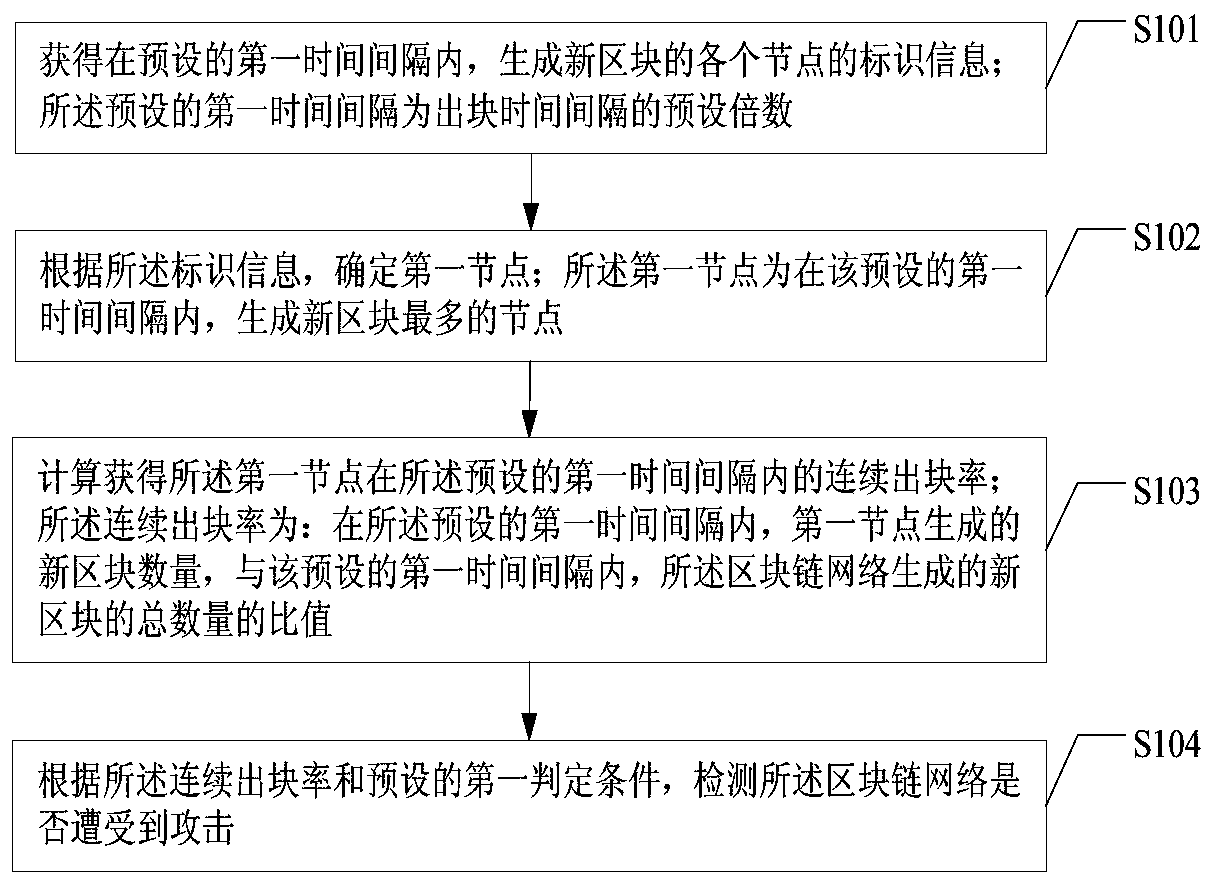
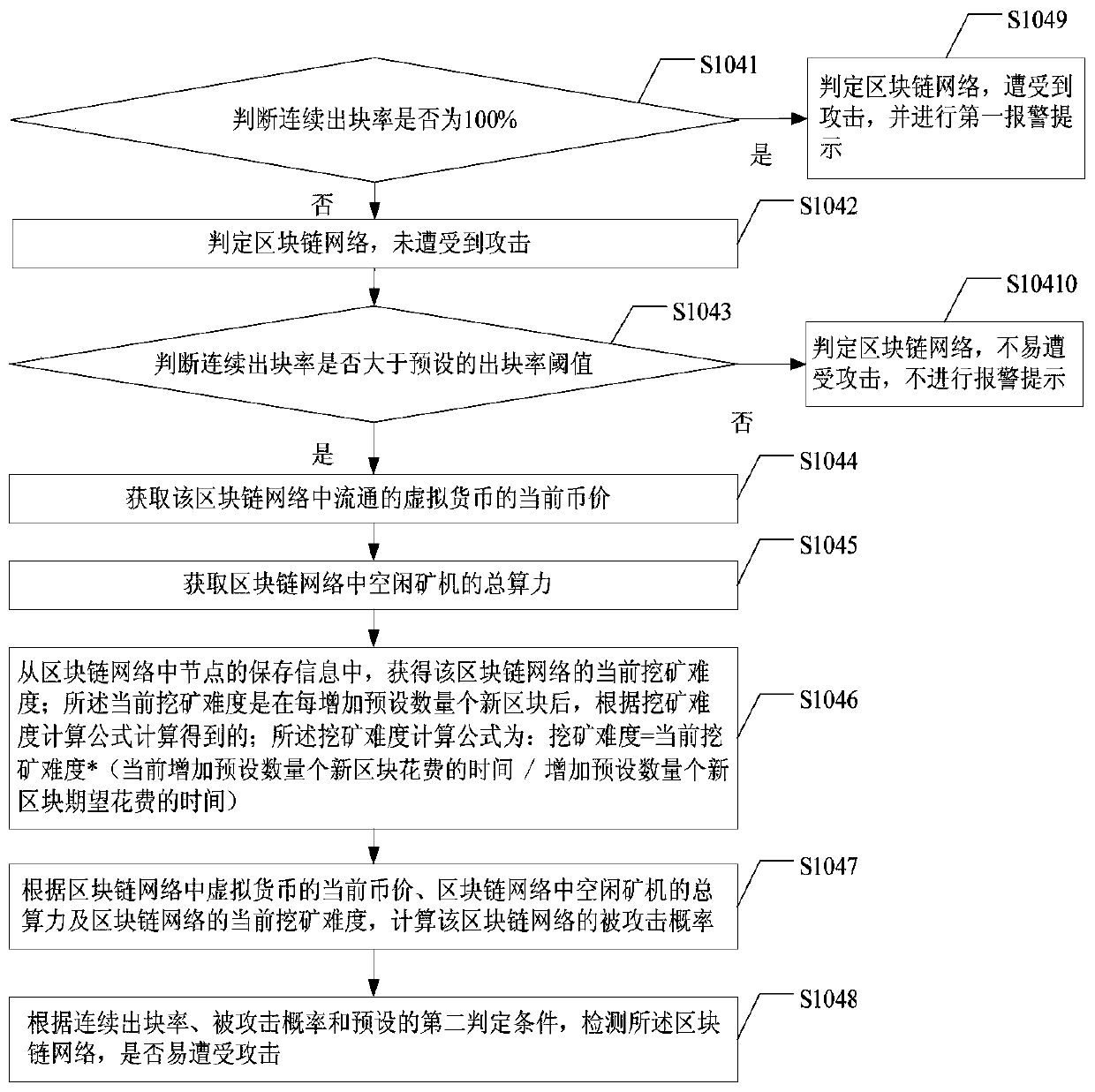
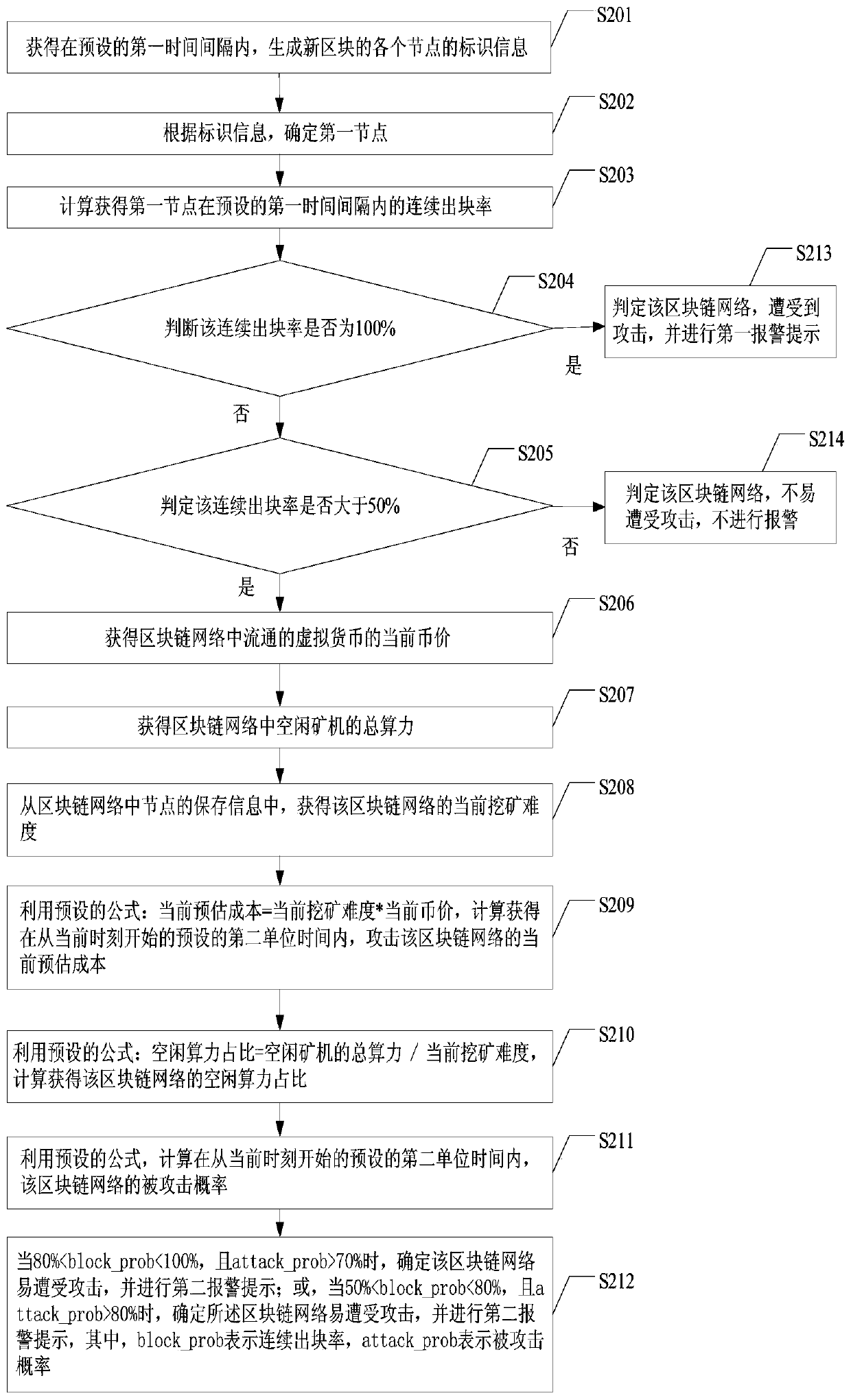
[0154] Example 1. Use the monitoring node to calculate the blockchain network. Within the preset first time interval of 50 minutes, the continuous block generation rate is 2 / 5, that is, the continuous block generation rate is 40%. The network has not suffered a 51% attack. Next, determine whether the blockchain network is vulnerable to 51% attacks. Since the continuous block generation rate is less than 50%, the blockchain network is not susceptible to 51% attacks and no alarm will be issued.
example 2
[0155] Example 2. Using the monitoring node to calculate the blockchain network, within the preset first time interval of 50 minutes, the continuous block generation rate is 3 / 5, that is, the continuous block generation rate is 60%; determine that the blockchain network The network has not suffered a 51% attack. Next, determine whether the blockchain network is vulnerable to 51% attacks. Among them, the block chain network's block generation time interval is 10 minutes, and the preset first time interval is 5 times the block generation time interval. Obtain the current currency price of the virtual currency circulating in the blockchain network, the total computing power of the idle mining machines in the blockchain network and the current mining difficulty of the blockchain network, which are used to calculate the attack of the blockchain network probability.
[0156] Since the first time interval is 50 minutes, it means that after every 50 minutes, the continuous block gen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com