A LDOS Attack Detection Method Based on Queue Distribution
An attack detection and queuing technology, applied in the transmission system, electrical components, etc., can solve the problems of low average attack rate and difficult detection, and achieve the effect of safe and effective network defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0024] The LDoS attack detection method based on queue distribution provided by the invention comprises the following steps carried out in order:
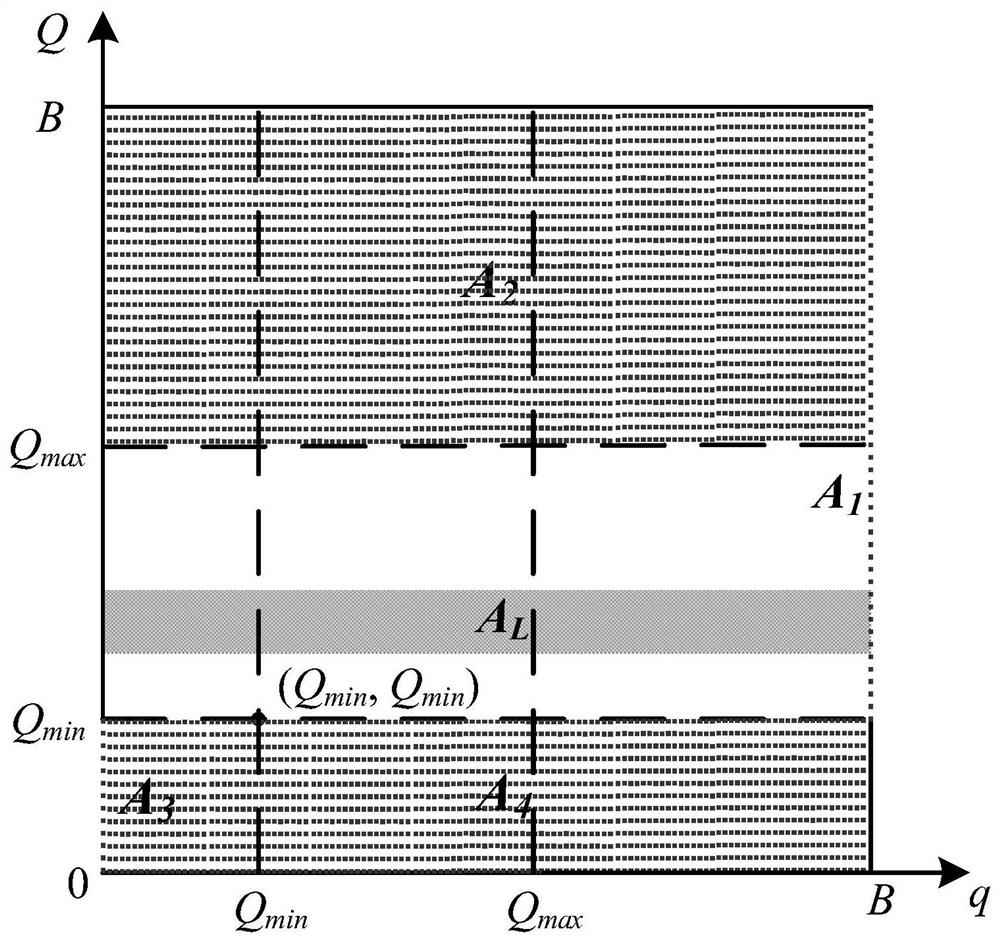
[0025] 1) First analyze the queue behavior under LDoS attack, infer the attack cycle, and establish a two-dimensional queue distribution model based on the analysis results;
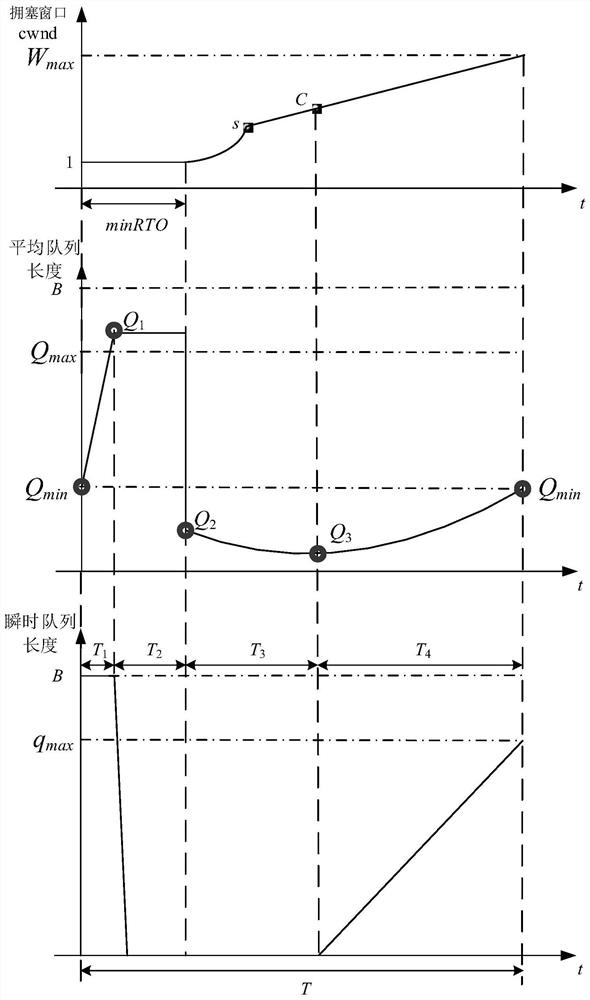
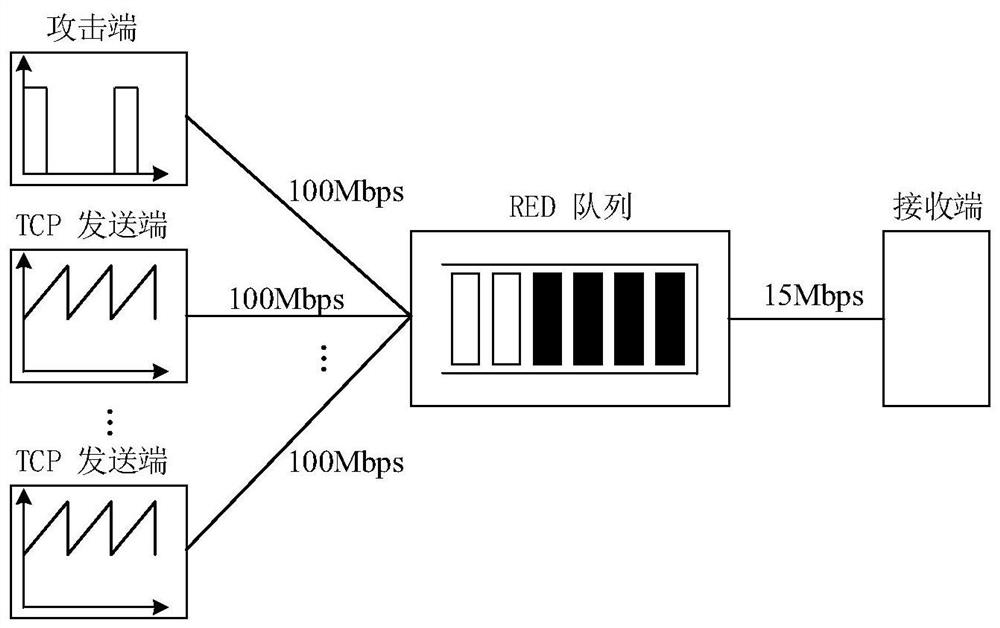
[0026] When analyzing the queue behavior under the LDoS attack, the present invention assumes that the window size of the TCP sender is not limited by the flow control window of the receiver, and the router buffer size is set to the bandwidth-delay product, then the RED queue behavior during the attack is as follows figure 1 shown. figure 1 The upper part of shows the TCP sender's congestion window over time, figure 1 The middle part of shows the average queue length over time, figure 1 The bottom half of , shows the inst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com