A Two-way Authentication Method Based on Smart Card
A smart card and identity authentication technology, which is applied in the field of security identity recognition and communication, can solve problems such as low efficiency, information leakage, and long authentication time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0011] The present invention will be further described in detail below in conjunction with the accompanying drawings.
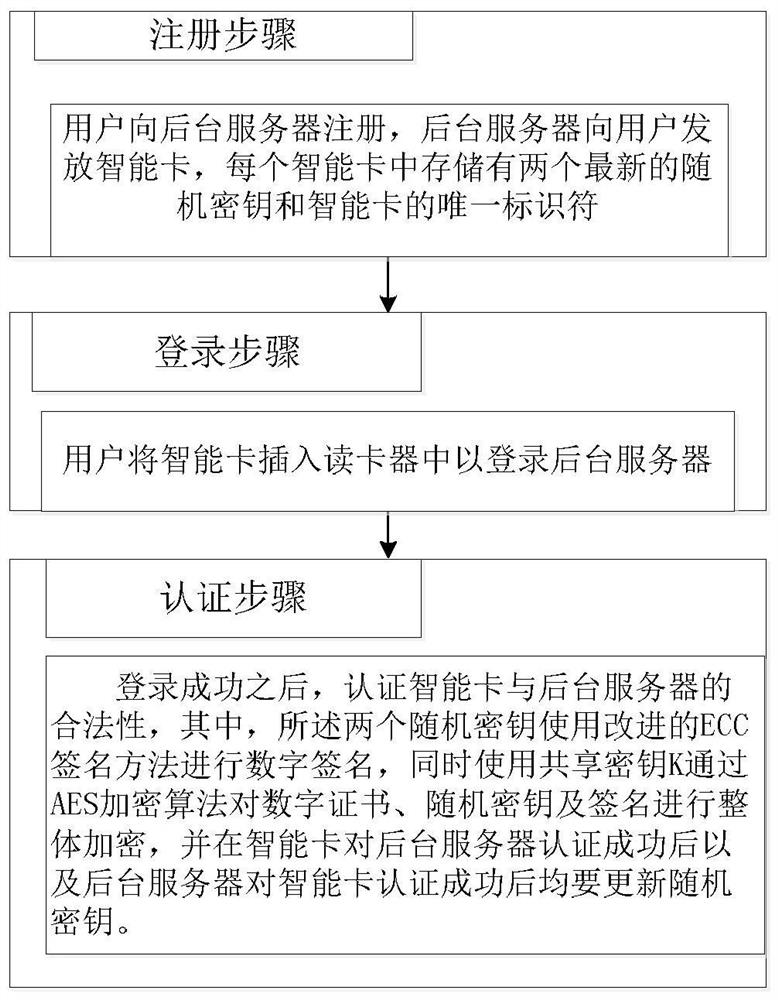
[0012] In one example, see figure 1 , which discloses a smart card-based identity authentication method, including a registration step, a login step and an authentication step, wherein,
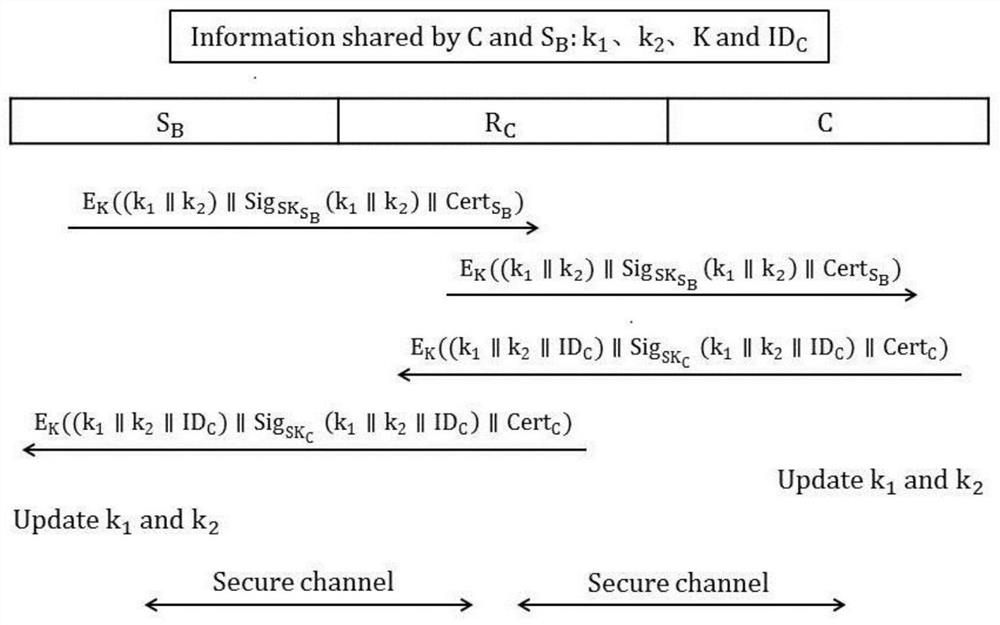
[0013] The registration step includes, the user submits to the background server S B Register, background server S B Issue smart cards C to users, and each smart card C stores two latest random keys k 1 , k 2 and the unique identifier ID of the smart card C ;
[0014] The login step consists of, the user inserts the smart card C into the card reader R C In order to log in to the background server S B ;
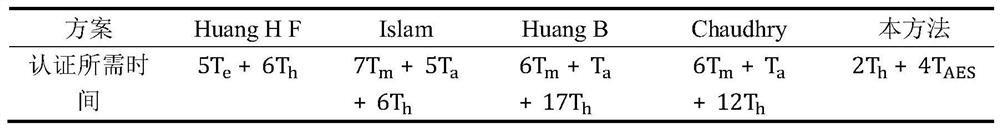
[0015] The authentication steps include, after successful login, authenticate the smart card C and the background server S B The validity of , where the two random keys k 1 , k 2 Use the improved ECC signature method for digital signature, and use the shared key K...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com