Password verification method and system for preventing library collision attack, middleware and storage medium
A verification method and password technology, applied in middleware and storage media, password verification method to prevent credential stuffing attacks, system field, can solve problems such as low security index, and achieve the effect of reducing the risk of credential stuffing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
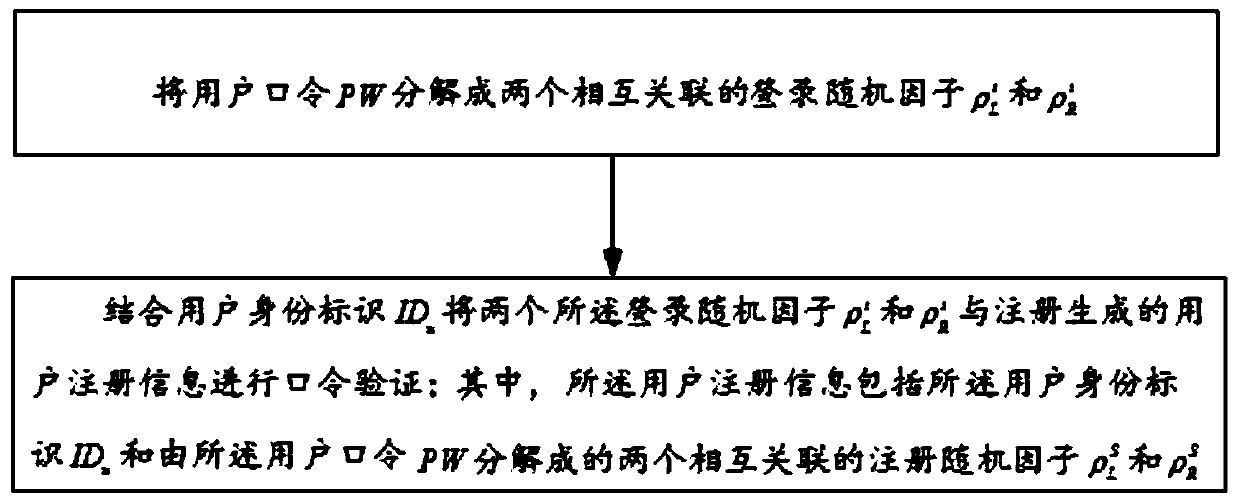
[0061] like figure 1 As shown, the password verification method for preventing credential stuffing attacks includes the following steps,
[0062] Decompose the user password PW into two interrelated login random factors and
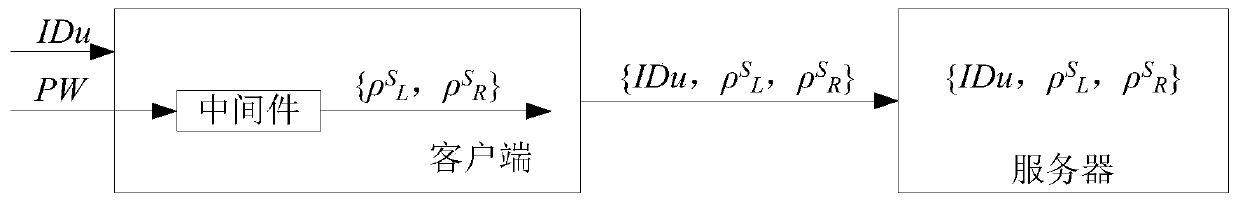
[0063] combined user ID u random factor of two said logins and Perform password verification with the user registration information generated by registration;
[0064] Wherein, the user registration information includes the user identity ID u and two interrelated registration random factors decomposed by the user password PW and
[0065] The basic design idea of the password verification method of the present invention is to decompose a password input by a user into two random factors, and perform password verification on the two random factors and the server. The risk of library attack can save the user from using different passwords to prevent the trouble of credential library attack. Therefore, this method is more convenient, practica...
Embodiment 2
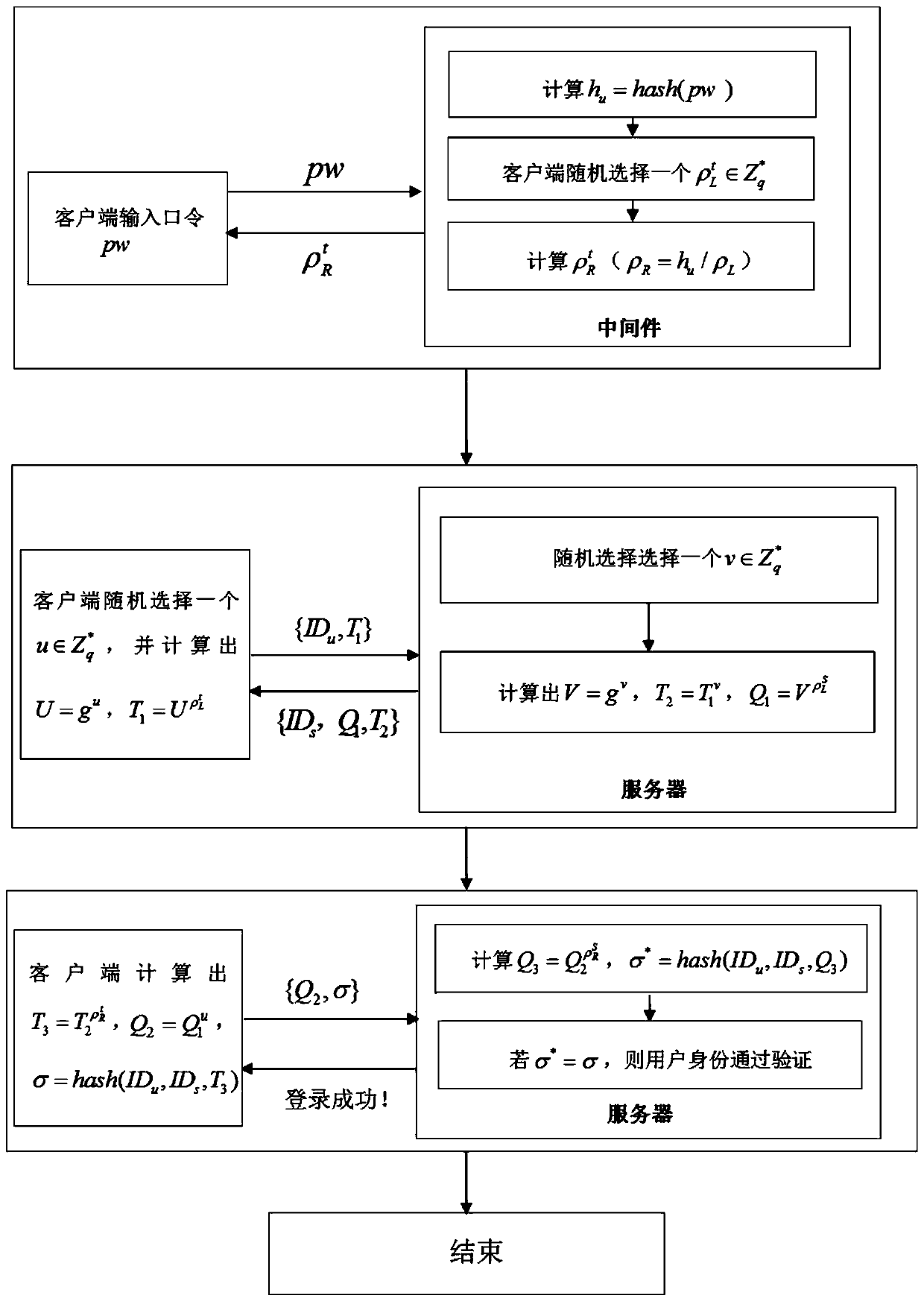
[0067] On the basis of the first embodiment above, registering and generating user registration information specifically includes the following steps, setting the user identity ID u and the user password PW, calculate the hash value h of the user password PW u ,
[0068] The group Z of integers modulo q q * Randomly select one of the registered random factors within use the formula calculates another of the enrollment random factors so that the user password PW is decomposed into two interrelated registration random factors and
[0069] is the user registration information.
Embodiment 3
[0071] On the basis of the above-mentioned embodiment 1 or embodiment 2, the user password PW is decomposed into two interrelated login random factors and Specifically include the following steps,
[0072] Calculate the hash value h of the user password PW u ,
[0073] The group of integers modulo q Randomly select one of the login random factors within use the formula Calculates another of said login random factors so that the user password PW is decomposed into two interrelated random factors of the login and
[0074] is based on modulo q in the group of integers The operation inside guarantees the non-infinity of the operation, and in addition is chosen randomly, so each calculated The results are not the same.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com