Method and device to produce secure hash value
一种安全散列、散列函数的技术,应用在安全通信装置、带移位寄存器/存储器的加密装置、仪器等方向,能够解决安全漏洞等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
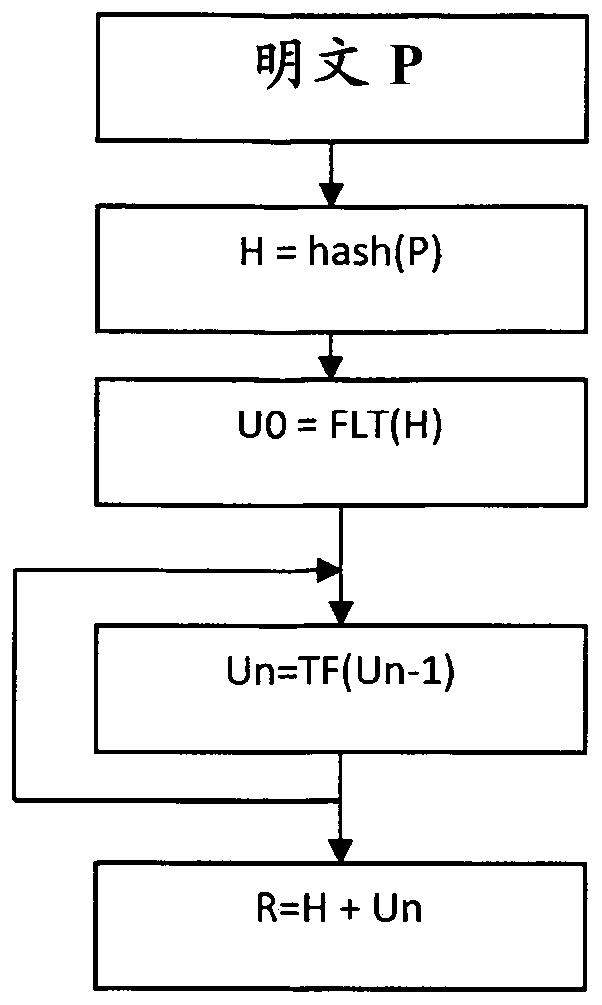
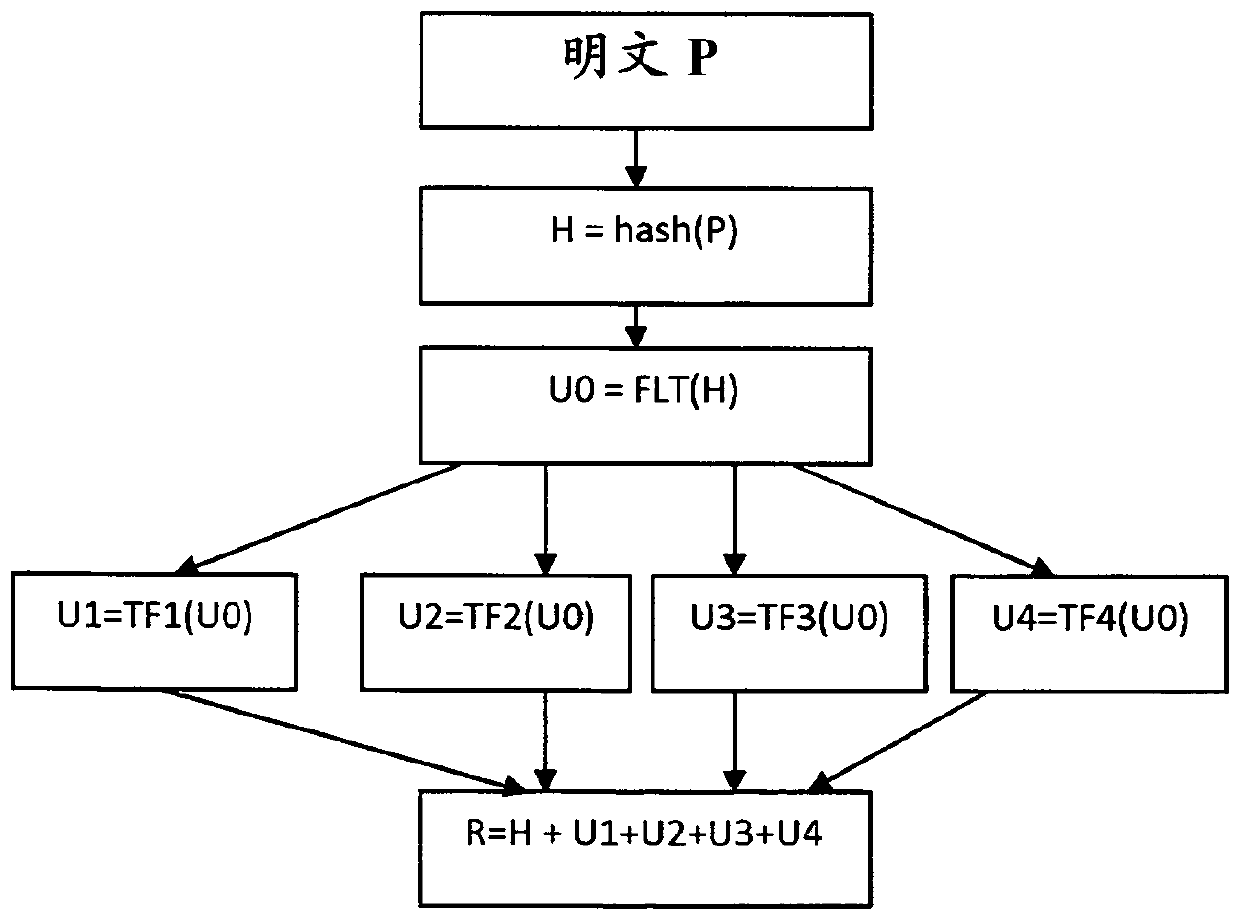
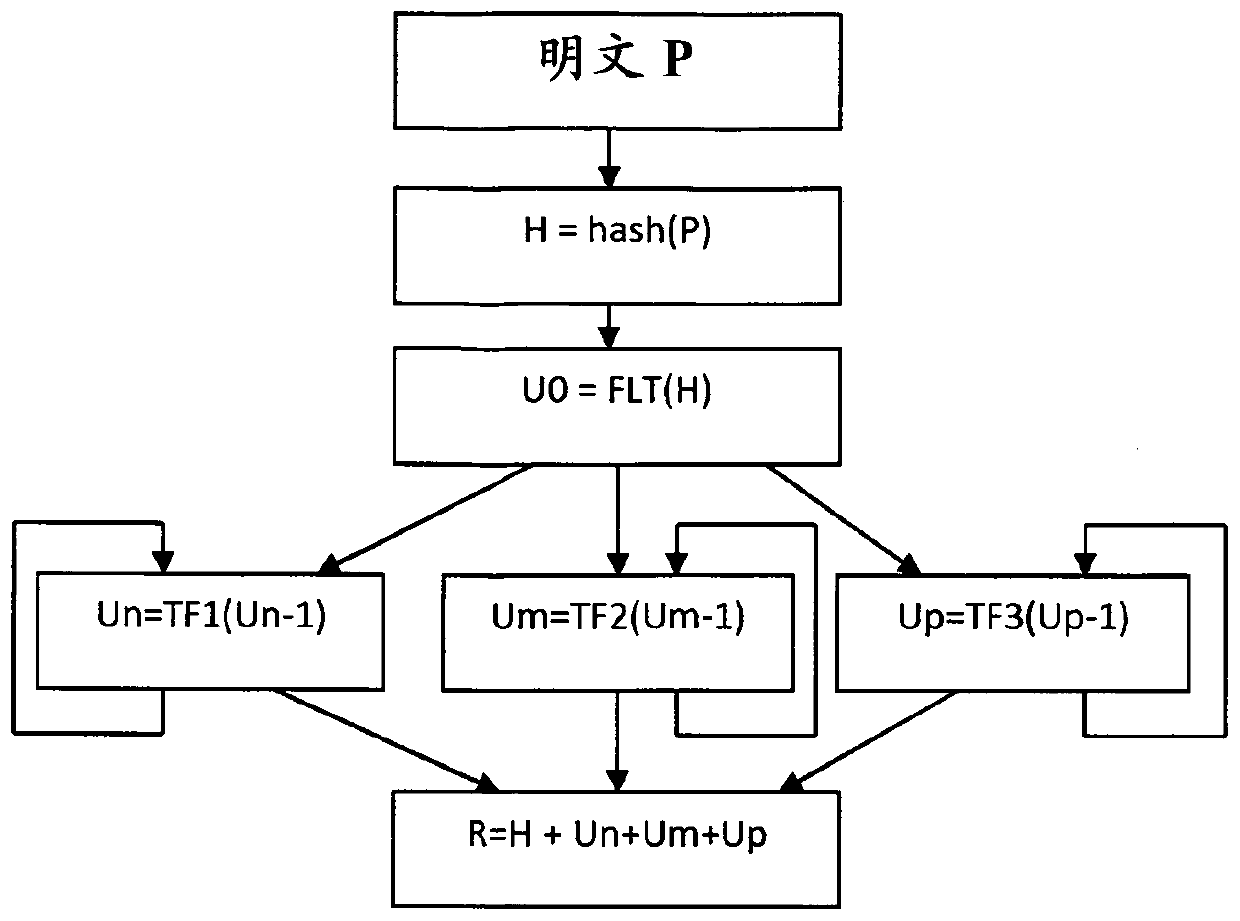
[0020] according to figure 1 , illustrating the steps of a method of generating a secure hash. An input message or plaintext P is input into a hashing module to generate a conventional hash value H. Known hashing algorithms are eg MD4, SHA-1 to SHA-256. Where the algorithm uses a seed, the seed is introduced into the module to produce the hash value H.
[0021] The next step is to convert the binary representation of the hash value H into a floating point number U0. The publication IEEE754-2008 gives an example describing how to represent an integer into a floating point representation. The IEEE 754 standard specifies binary 23 as having:
[0022] Sign bit: 1 bit, exponent width: 8 bits, significand precision: 24 bits
[0023] The double-precision floating-point format is a computer number format that occupies 8 bytes (64 bits) in computer memory and expresses a wide dynamic range of values by using floating point. The double-precision floating-point format usually ref...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com