An Efficient Metadata Management Method in Encrypted Data Deduplication System
A technology for deduplication and management methods, applied in the field of data storage, can solve the problems of key metadata that cannot be encrypted, metadata that can only be reduced by zero blocks, and key metadata that cannot be compressed, so as to reduce storage overhead. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
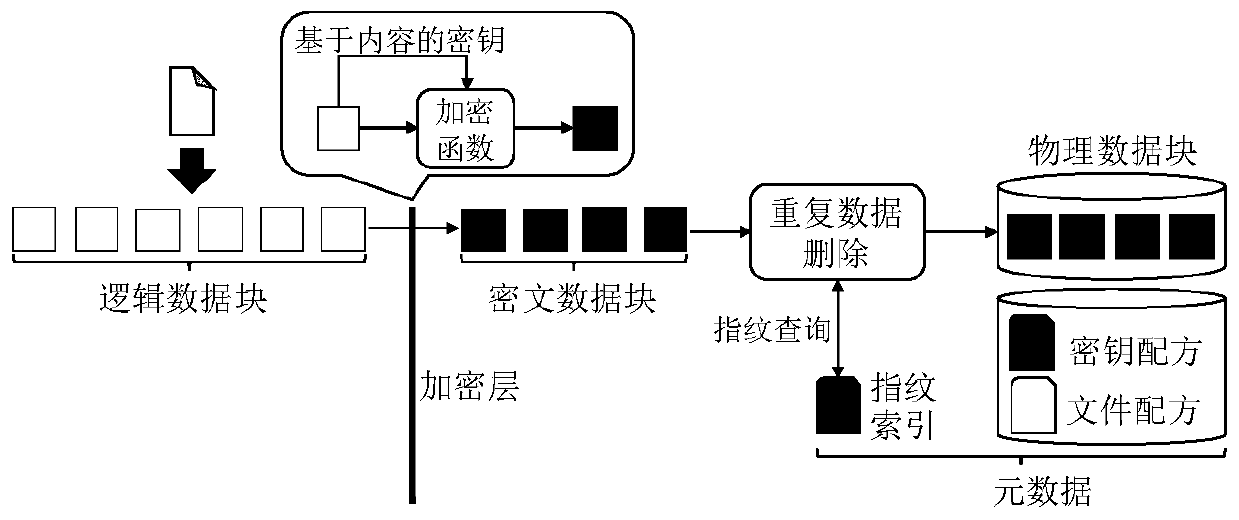
[0076] The CDStore system (for details, please refer to the document "M.Li, C.Qin, and P.P.C.Lee. CDStore: Towardreliable, secure, and cost-efficient cloud storage via convergent dispersal. InProc. of USENIX ATC, 2015") supports encrypted duplicate data Deleted multi-cloud storage system. The CDStore system client encodes logical data blocks into n ciphertexts through the deduplication-aware secret sharing algorithm (deduplication-aware secret sharing), and stores them in n cloud storage servers respectively; each server can perform data deduplication based on the received ciphertexts To save storage space; when downloading, the client downloads ciphertext from at least k servers, and recovers the corresponding plaintext data block after decoding.
[0077] The CDStore system itself does not support an efficient metadata management mechanism. In this embodiment, the method of the present invention is implemented based on the CDStore system to form a Metadedup system, and the p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com