Information encryption method, information decryption method, terminal and computer readable storage medium
A technology for information encryption and information decryption, which is applied in the field of decryption methods, terminals and computer-readable storage media, and information encryption, and can solve the problems of easy deciphering of encryption methods and low information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
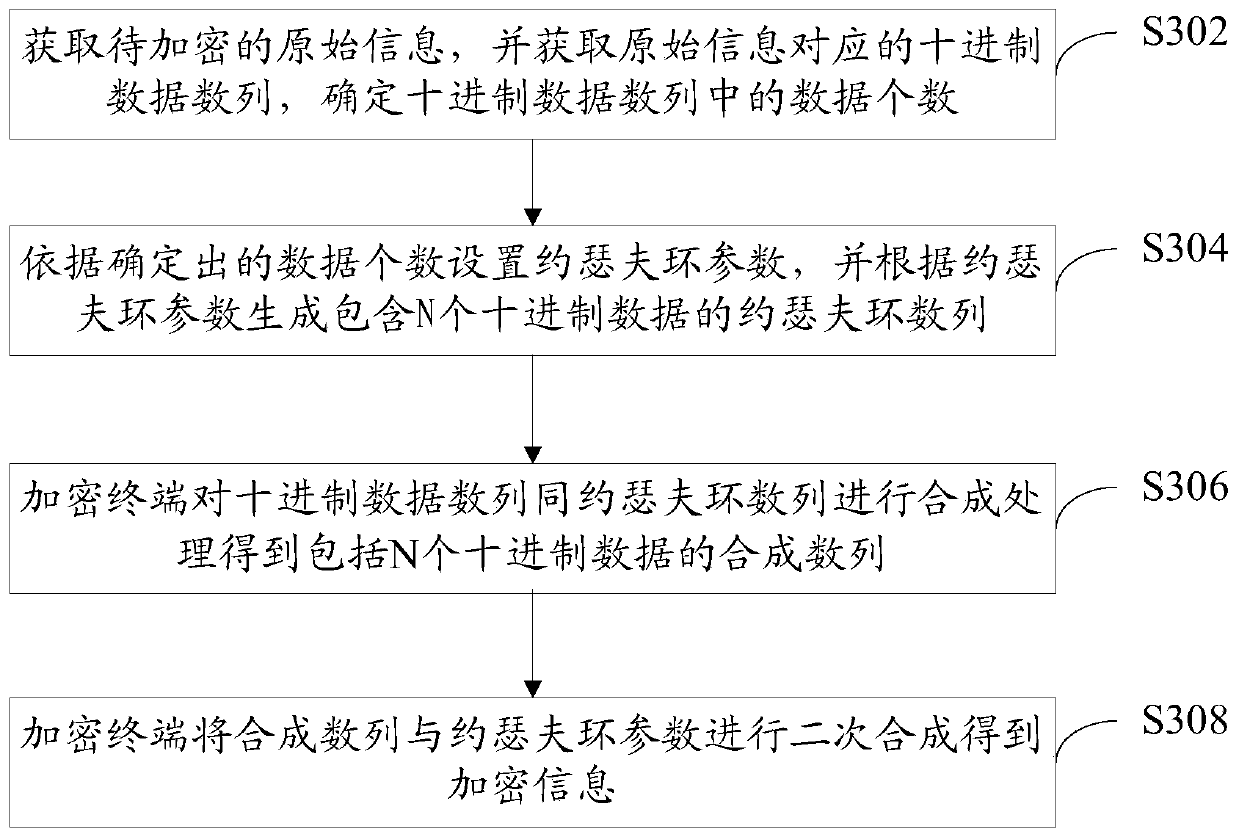
[0074] If the original information to be protected includes m data, according to the information encryption scheme provided in the related art, when the original information is encrypted, the processing for each of the m data is the same , for example, for the character string "I LOVE YOU", a typical encryption method in the related art is to add k to each value of the character string, for example, in one scheme, the value of k is 1 , then the ciphertext obtained after encryption is "J MPWFZPV", comparing the original information and the ciphertext, it is easy to see that since the processing of each data is exactly the same, the same data in the original information is also in the ciphertext identical. For this encryption scheme, the mapping relationship is simple. Once the ciphertext is intercepted, the risk of being deciphered is very high, which seriously threatens the user's information security. In order to solve this problem, this embodiment provides an information enc...
no. 2 example
[0101] This embodiment will provide an information decryption method corresponding to the information encryption method in the first embodiment, please refer to Figure 5 The flow chart of the information decryption method shown:
[0102] S502: The decryption terminal acquires the encrypted information to be decrypted.
[0103] It should be understood that the decryption terminal can receive the encrypted information through the network. For example, the mobile phone of user A and the mobile phone of user B perform encrypted communication. After the mobile phone of user A encrypts the original information to generate encrypted information, it is transmitted through the network. To the mobile phone of user B, in this case, the mobile phone of user B obtains the encrypted information from the network. Of course, those skilled in the art can understand that there are many other ways for the decryption terminal to obtain encrypted information, for example, copying encrypted infor...
no. 3 example
[0121] In order to make those skilled in the art more aware of the advantages and details of the information encryption method and information decryption method provided by the present invention, this embodiment will further illustrate the process background management method with examples: First, assume that the terminal in this embodiment for mobile phones, such as Figure 7As shown, the mobile phone 700 communicates with another tablet computer. It is assumed that the mobile phone 700 needs to transmit a file to the tablet computer. The information contained in the file is sensitive and requires high security protection. Therefore, the mobile phone 700 and the tablet computer are based on The information encryption and decryption scheme provided in the foregoing embodiments encrypts and transmits files to be transmitted. See Figure 8 Provided flow chart of interaction between mobile phone 700 and tablet computer:
[0122] S802: The mobile phone converts the obtained orig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com