Fine-grained access control method and system based on strategy grammar
An access control, fine-grained technology, applied in the direction of instruments, electrical digital data processing, digital data protection, etc., to achieve the effect of wide coverage of requirements, flexible management, and reduce the risk of misoperation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
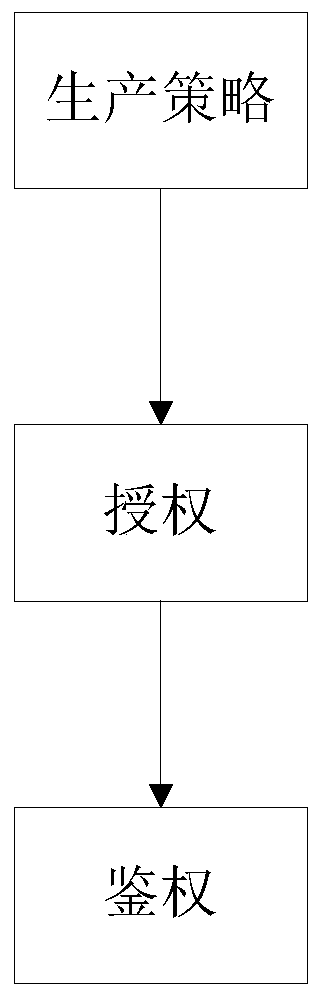
[0065] as attached figure 1 As shown, the fine-grained access control method based on policy syntax of the present invention, the steps of the method are as follows:
[0066] S1. Production strategy: Inspur cloud account strategy is preset for access control in public scenarios; for example, the main account needs to have access rights to the resources under its own account, and the sub-accounts have access rights to the resources it belongs to. Users can customize and create the required policies according to their needs; the specific steps are as follows:
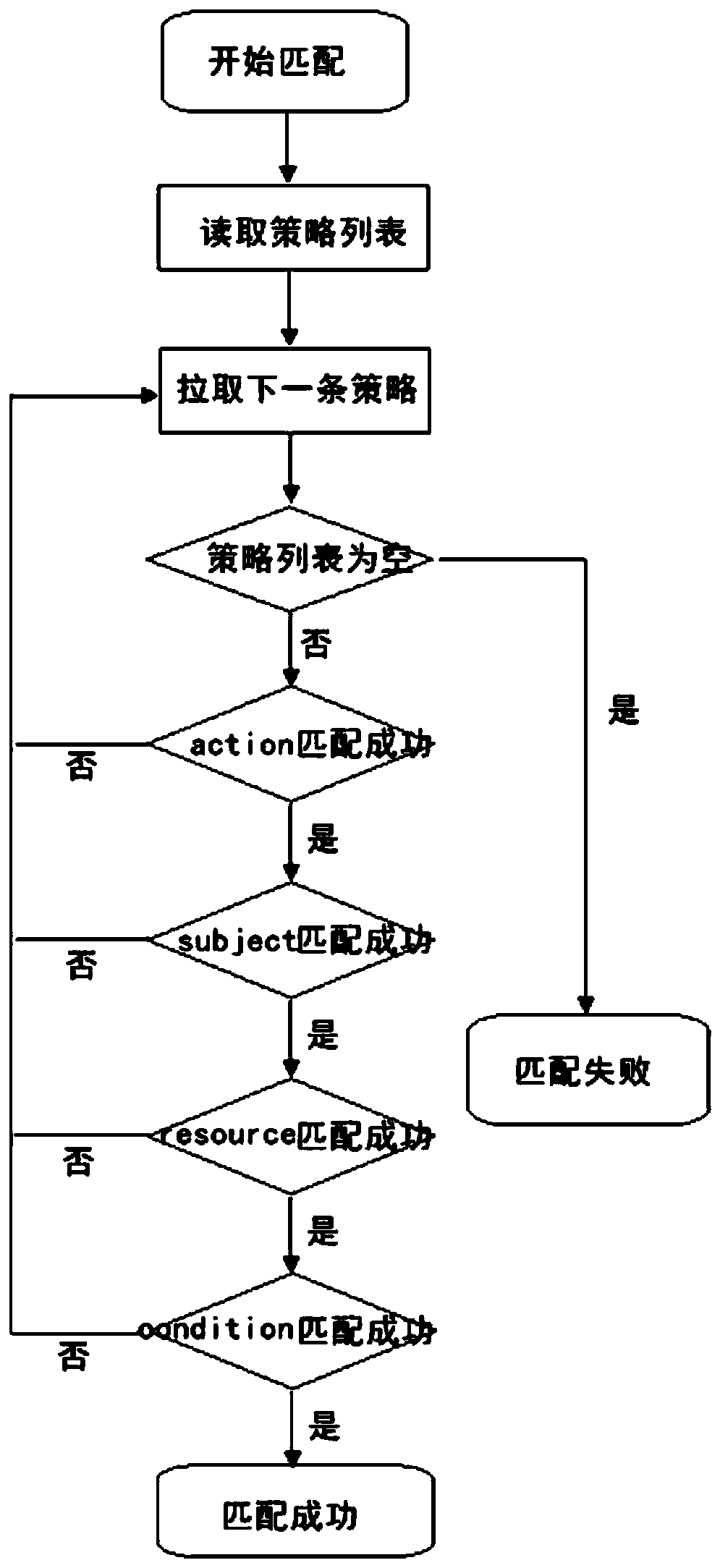
[0067] S101. The created strategy includes resource (referring to resources in cloud services, including information such as services, regions, accounts, etc., which can be specific to resource instance granularity), action (specific operations on resources or resource instances) or condition (custom data filtering Conditions, more precise authorization); among them, resource represents one or a kind of resource, and sup...
Embodiment 2
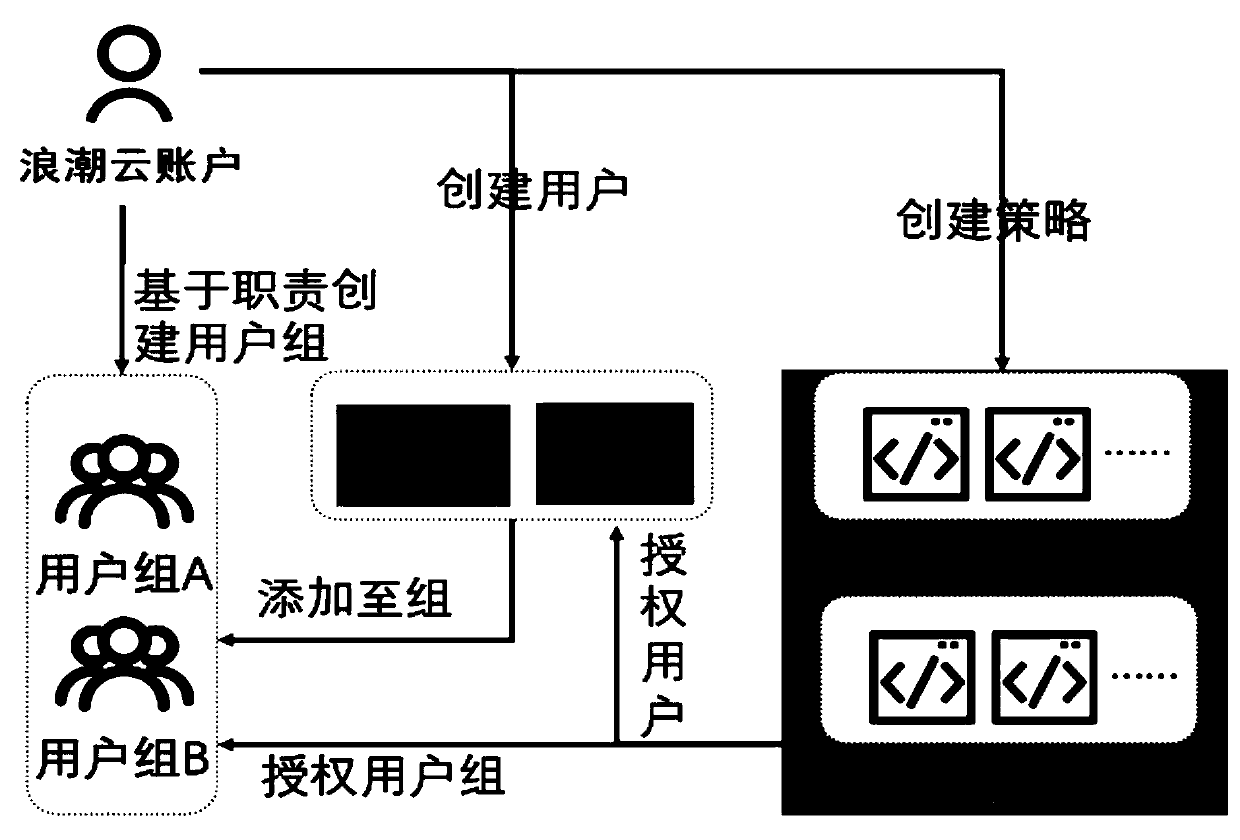
[0092] The policy syntax-based fine-grained access control system of the present invention includes:
[0093] Inspur cloud account is used to create users and user groups, specify policies according to conditions, and then authorize the policies to sub-users and user groups, so that all users under the user tools and user groups have the functional permissions specified by the policies;
[0094] The strategy production module is used for users to customize and create the required strategies according to their needs;
[0095] The authorization module is used to bind the created policy to the entity. The entity is a user or user group, which abandons the concept of role and makes the process of access control more direct and efficient;
[0096] The authentication module is configured to assemble authentication request information according to the user request after receiving the user request. The authentication module adopts the authentication component ladon.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com