Abnormal user detection method and system based on ensemble learning
A technology integrating learning and detection algorithms, applied in the field of network security, can solve problems such as lack of pertinence in traditional methods, and achieve the effect of preventing information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
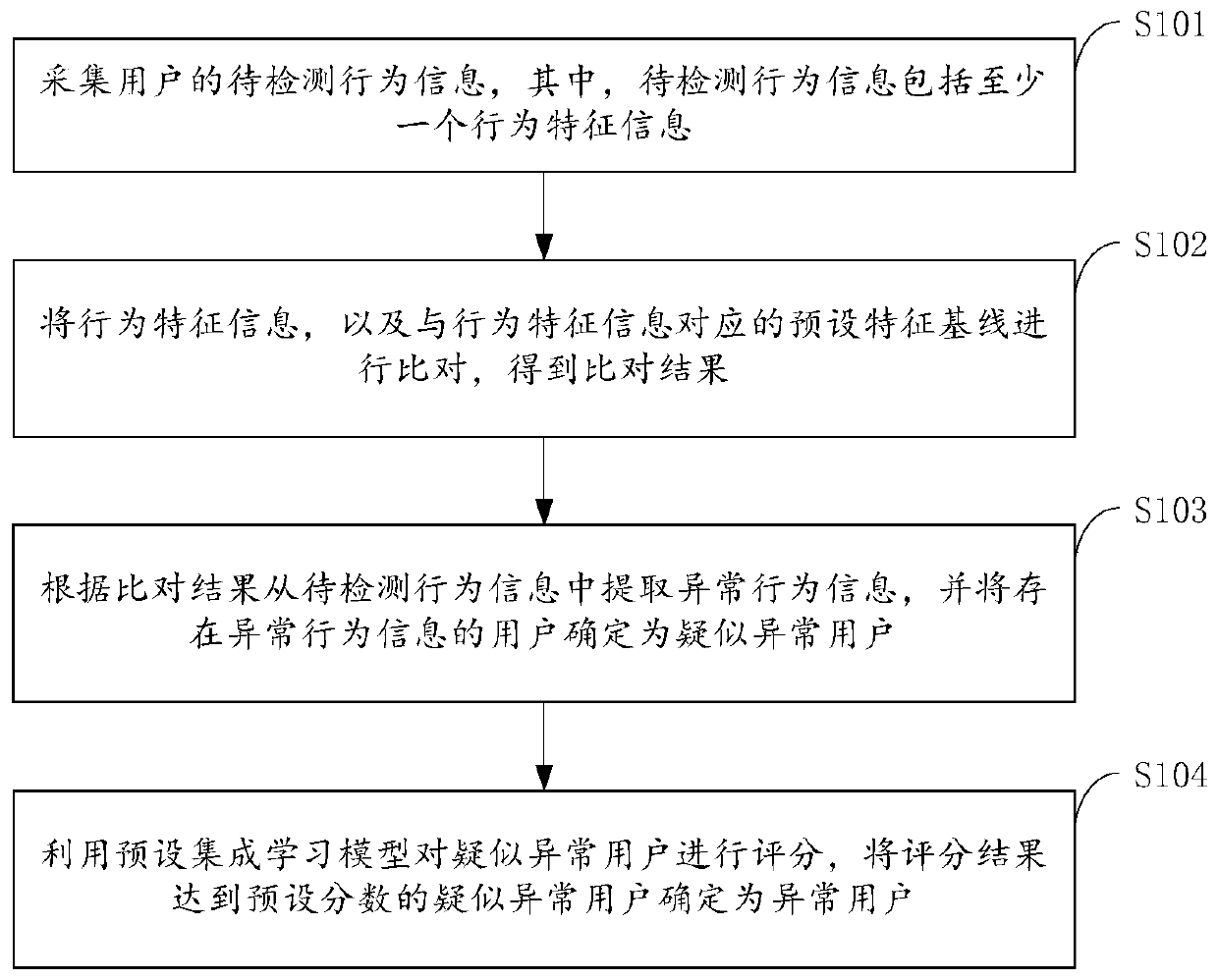
[0033] refer to figure 1 , the embodiment of the present invention provides a method for detecting abnormal users based on integrated learning, which may include the following steps:
[0034] Step S101 , collecting user behavior information to be detected, wherein the behavior information to be detected includes at least one behavior feature information.
[0035] In the embodiment of the present invention, the behavior information to be detected is the behavior information to be detected, and the behavior information can be classified into network behavior information and terminal behavior information according to classification. It should be noted that behavior information is provided by user behavior data sources. User behavior data sources include but are not limited to security logs, network traffic, threat intelligence, logs related to identity access, and access logs related to user scenarios. Among them, logs related to user scenarios include but are not limited to VP...
Embodiment 2
[0079] refer to Figure 6 , the embodiment of the present invention provides an abnormal user detection system based on integrated learning, which may include the following modules:
[0080] The first collection module 11 is used to collect the user's behavior information to be detected, wherein the behavior information to be detected includes at least one behavior characteristic information;
[0081] The comparison module 12 is used to compare the behavioral feature information and the preset feature baseline corresponding to the behavioral feature information to obtain a comparison result;
[0082] An extraction module 13, configured to extract abnormal behavior information from the behavior information to be detected according to the comparison result, and determine users with abnormal behavior information as suspected abnormal users;
[0083] The scoring module 14 is configured to use a preset integrated learning model to score suspected abnormal users, and determine susp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com