IP video tamper-proofing monitoring method and system
A tamper-proof, video technology, applied in the field of video processing, can solve problems such as inability to transmit effective monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
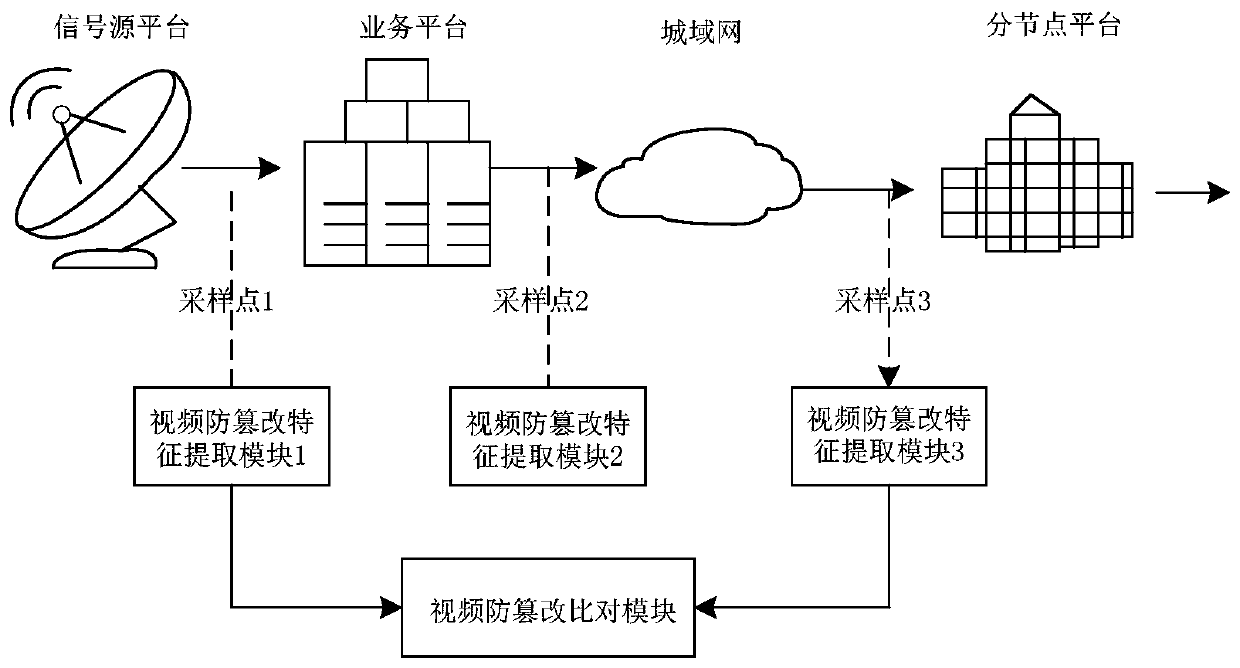
[0050] figure 1 It is a schematic diagram of an application scenario of an IP video anti-tampering monitoring system provided by Embodiment 1 of the present invention.
[0051]refer to figure 1 , the system includes a signal source platform, a service platform, a metropolitan area network and a sub-node platform; the system is not limited to the above-mentioned platforms, and other platforms can also be added for expansion.
[0052] The sampling point 1 is between the signal source platform and the service platform, the sampling point 2 is between the service platform and the MAN, and the sampling point 3 is between the MAN and the sub-node platform. Sampling point 1 corresponds to video anti-tampering feature extraction module 1, sampling point 2 corresponds to video anti-tampering feature extraction module 2, and sampling point 3 corresponds to video anti-tampering feature extraction module 3, and also includes a video anti-tampering comparison module.
[0053] The video a...
Embodiment 2
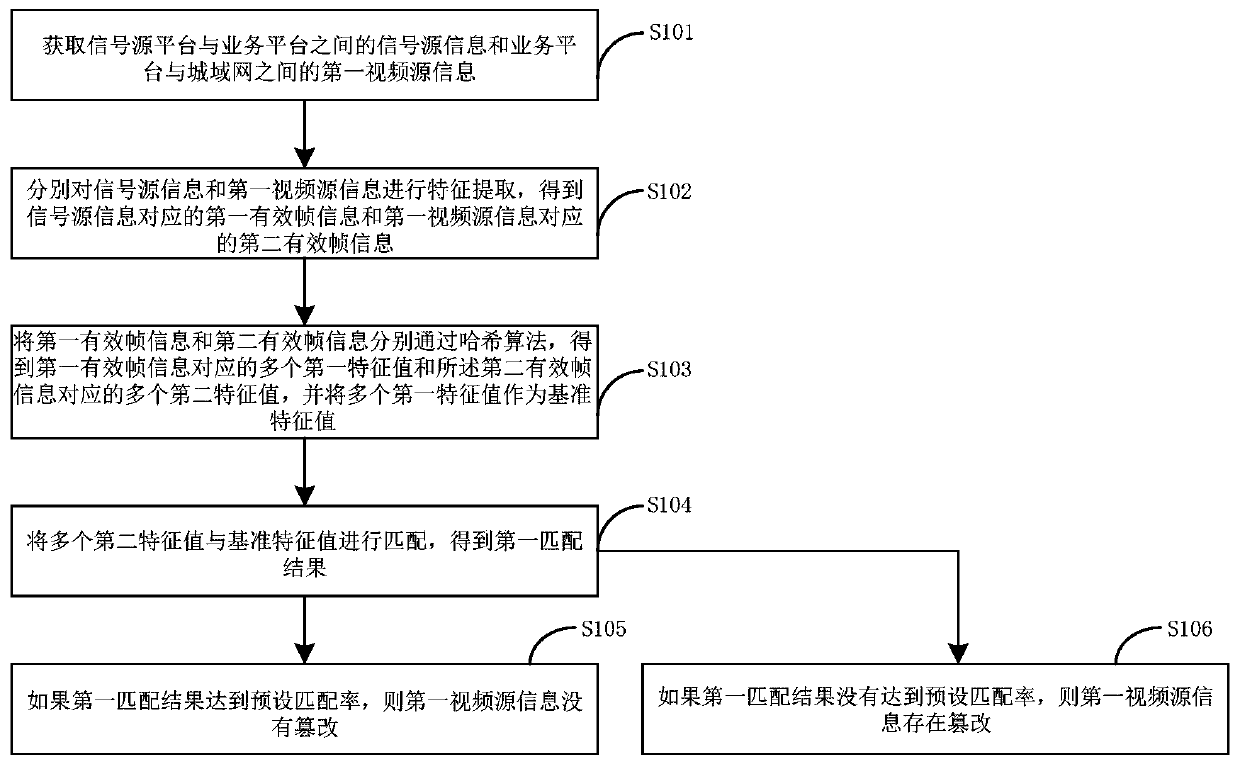
[0061] figure 2 It is a flowchart of an IP video anti-tampering monitoring method provided by Embodiment 2 of the present invention.
[0062] refer to figure 2 , the method includes the following steps:
[0063] Step S101, obtaining the signal source information between the signal source platform and the service platform and the first video source information between the service platform and the MAN;
[0064] Here, the signal source information between the signal source platform and the service platform and the first video source information between the service platform and the MAN are acquired through the monitoring probe.
[0065] Step S102, performing feature extraction on the signal source information and the first video source information respectively, to obtain the first valid frame information corresponding to the signal source information and the second valid frame information corresponding to the first video source information;
[0066] Step S103: Pass the first ...
Embodiment 3
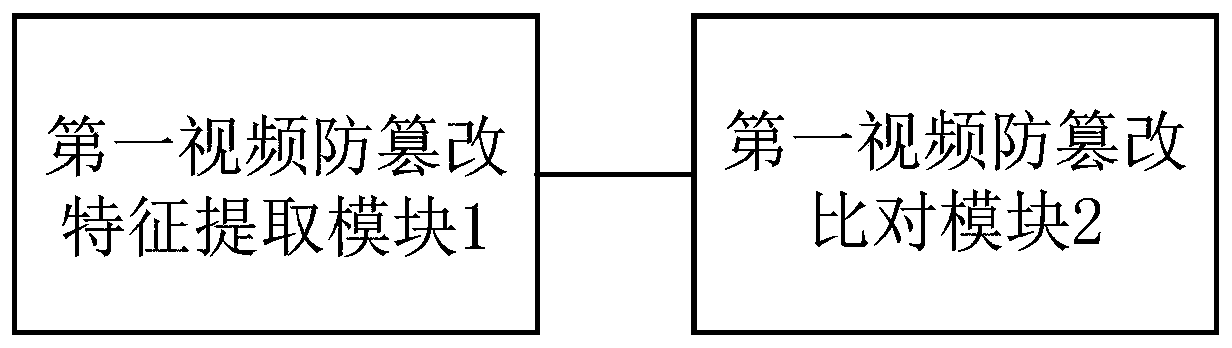
[0090] image 3 It is a schematic diagram of an IP video anti-tampering monitoring system provided by Embodiment 3 of the present invention.
[0091] refer to image 3 , the system supports simultaneous extraction of not less than 600 channels of video source information, including multiple IP (Internet Protocol, Internet Protocol) video streams such as standard definition video streams, high-definition video streams, and 4K video streams.
[0092] The system comprises: a first video anti-tampering feature extraction module 1 and a first video anti-tampering comparison module 2, the first video anti-tampering feature extraction module 1 is connected with the first video anti-tampering comparison module 2;
[0093] The first video anti-tampering feature extraction module 1 is used to obtain the signal source information between the signal source platform and the service platform and the first video source information between the service platform and the metropolitan area netwo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com