Illegal code identification method, system, device and storage medium
An illegal code and identification method technology, applied in the illegal code identification method, device, storage medium, and system field, can solve the problems of not being able to find unknown malicious code memory implantation and operation, and not being able to identify illegal codes, etc., to achieve strong protection, The effect of precise memory protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
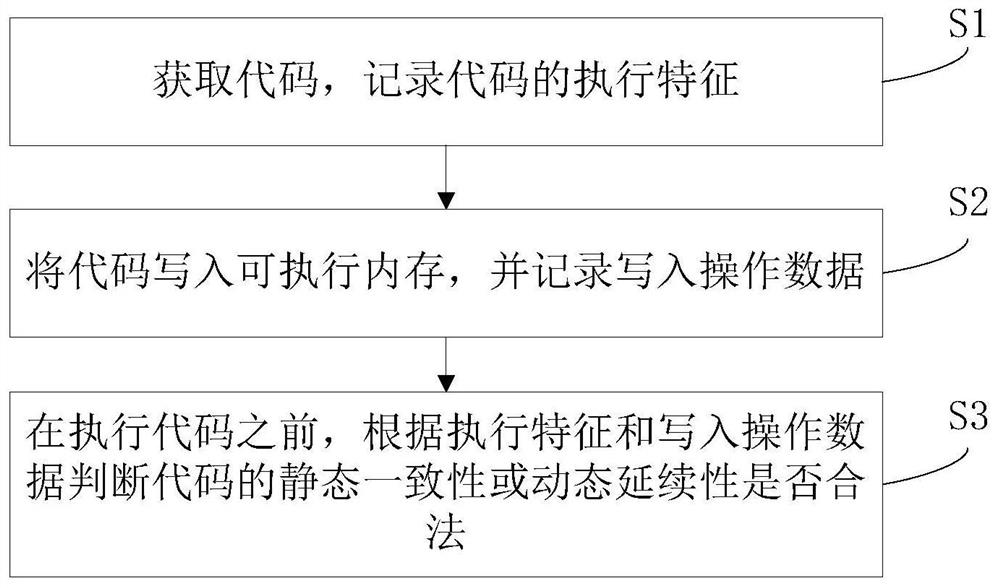
[0024] The principles and features of the present invention will be described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
[0025] At present, the main ways to prevent illegal codes include static scanning of disk files, process-based memory static scanning, patching, and firewall-based security policy protection. These security protection strategies are all implemented based on the known illegal code. For example, static scanning of disk files is the full-disk and directory scanning of common antivirus software. Process-based memory static scanning is common antivirus software scanning the memory of user processes and operating system processes. Firewall-based security policy protection is to protect some Protocols and ports are blocked.
[0026] That is to say, these network security protection measures can work only on the premis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com